Summary:
- Zscaler and CrowdStrike announced a new device health integration
- Device health score will be used to automatically update ZPA access policies
- Joint customers of ZPA and CrowdStrike ZTA can leverage it
Adopting a zero trust model is highly sought after and much talked about—especially in the context of remote work. A majority of the workforce is now remote, accelerating security concerns for devices and connectivity.
Image: Microsoft
The world is evolving and embracing a combination of remote and on-premises workers, so security measures must also adapt to enable this new normal.
In order to obtain end-to-end security and protect data, it is imperative to understand device posture and user identity to enable secure access to applications. These components must be continuously assessed to identify attack risks and prevent expensive reactive measures.
Device posture is not a one-time consideration; it needs to be monitored on an ongoing basis, and this information must be passed along to the zero trust service responsible for providing secure access to applications.
Zero trust with Zscaler and CrowdStrike through endpoint posture assessment
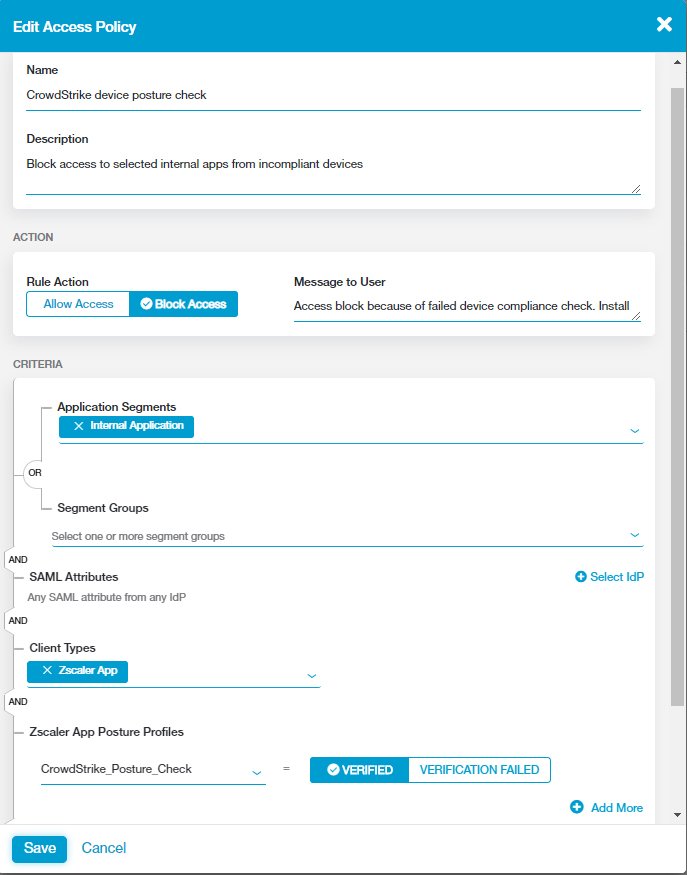
Zscaler and CrowdStrike have partnered to deliver secure access to applications by providing conditional access based on the user’s identity, location, and the posture of the device.
With the announcement of this new integration between ZPA and CrowdStrike Zero Trust Assessment, the Zscaler and CrowdStrike partnership has grown even deeper. CrowdStrike provides a health score for each device, and then surfaces it as a continuous stream of posture assessments. These scores provide ZPA with an enhanced understanding of device posture, allowing ZPA to leverage this information, auto-update policies, and decide whether to allow access to a private app or block the device from access.
What does this integration mean for customers?
Joint ZPA and CrowdStrike ZTA customers will be able to:
- Use device health metrics for a deeper understanding of the device posture
- Isolate devices to prevent malware propagation before they connect to apps
- Automate updates to access policies based on APIs from CrowdStrike to ZPA
- Ensure that only compliant devices gain access to sensitive data
- Increase visibility with stronger reporting and remediation
Through our conversations with customers, we know that zero trust is an important aspect of this journey, especially with helping your organization move beyond crisis mode with legacy software to a sustainable and modern, long-term solution.
True zero trust equates to having device and user identity awareness and the right policies enforced. This new integration is a huge step in that direction.
Learn more:
Video: Zscaler + CrowdStrike Demo
Customer Testimonial: Cushman & Wakefield
Kanishka Pandit is a product marketing manager for Zscaler Private Access






