
EDITOR'S PICK
Aug 5, 2021
5G represents a melding of telco operator, enterprise, and cloud technologies to deliver amazing new experiences and flexibility. Zero trust simplifies the protection of 5G/Edge workloads and devices.
Fifth generation (5G) wireless networks will change the world, but I’ll forgive your skepticism given the years of hype, politics, and uneven roll out. Rest assured, analysts and forecasters agree that signs of a one-to-two-year 5G tipping point are everywhere.
Depending on your location, your mobile carrier, and your device, you might be seeing 5G high-band performance (you know, when SpeedTest.net tells you your 5G download speed is in excess of 1,000 Mbps while your pricey home fibre connection maxes out around 100 Mbps). Even when your provider is using mid-band or low-band 5G, you’re still seeing speeds as good or better than what most wired Internet provides.
Network operators are in a race to deploy high-speed, high-bandwidth 5G around the world as they push past 4G LTE technology to enable new and exciting use cases like immersive experiences. At the Tokyo Olympics, some lucky spectators watched swimming and other medal events through Microsoft HoloLens 2 goggles with low-latency in 5G-powered augmented reality.
On the enterprise side, the attractiveness of replacing wired and fiber networks with wireless 5G is growing as real-time, data-intensive applications, Industrial IoT, and other high-value use cases are accelerating adoption. Entire industries are bracing for change and opportunities that make use of a connected ecosystem spanning fixed broadband, mobile, and IoT infrastructure.
Unlike the previous 4G-LTE generation, the new 5G mobile standard gives enterprises deployment options and new ways to work with telcos and cloud providers. Private 5G and network slicing expand deployment options to suit specific scenarios, business requirements, use cases, and budgets. While 5G remains compatible with 3G and 4G standards, it represents a significant overhaul of telco architectures with new openness and access. That means an overhaul of both operator and Enterprise IT infrastructure, a rethink of business models, and a demand for greater cybersecurity and data governance.
Why is 5G so exciting?
The best way to understand the widespread appeal of 5G is to think of the three words that encapsulate how it will impact networks and applications: fast, live, and massive.
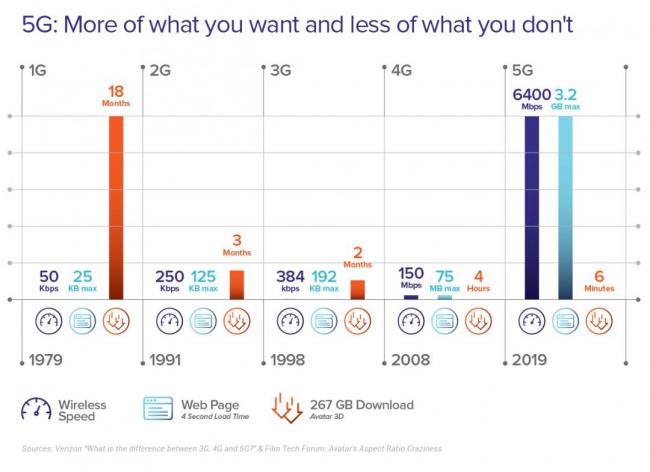
FAST: 5G uses a broad mix of radio bands that push more bits per second (bps) and A LOT more bits at the higher frequencies. That means 5G speeds of up to 10 Gbps, which is 10 to 100x faster compared to 4G-LTE, will make some of today’s web experiences feel like the days of dial-up. If we all expect a future with ubiquitous augmented and virtual realities then 5G performance is the new “must have.”
The chart below compares the speed, the size of a web page that can be loaded in four seconds, and the download time of a movie (Avatar 3D) by each wireless generation. The performance gains are exponential.
LIVE: As in 5G offers near real-time performance (also referred to as “low-latency”). Today, a packet of data can take 20 to 1,000 milliseconds (ms) to get from your laptop or smartphone to the cloud. 5G wants to cut that time down to a few milliseconds (ms) when the use-case demands it. Think about 4K video streaming to your personal 5G device. That means no more buffering, stuttering, freezing, or waiting for your video—no matter how many others are streaming video to their mobile devices around you. But 5G can’t cheat the speed of light. Packets take time to get from one place to another. Physical speed alone does not reduce latency.
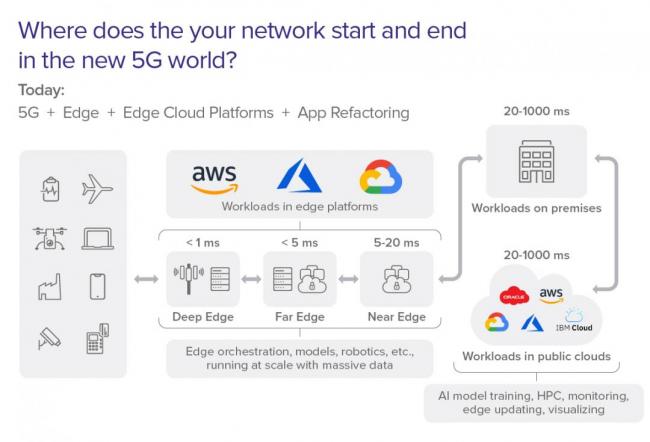
To achieve low-latency, compute resources need to live closer to end user devices. That means Edge Compute, and it comes in multiple flavors that depend on how fast you need to access it:
- FAR Edge (between 5 to 20 ms latency), which is farthest from the cloud and nearer to your device;
- NEAR Edge (20+ms latency) which is nearer to the cloud than your device; and,
- DEEP Edge that is less than 5 ms away from you
Which Edge you need depends on your use-case, latency-requirements, and budget. Not all use-cases need near real-time computer performance. A lot need “sort of real-time” where 20 ms or so is more than adequate.
MASSIVE: 5G is designed to be massively scalable in terms of attached devices. Upgraded radio access point hardware can support massive simultaneous connections and deliver staggering performance improvements like 1,000 times more bandwidth per unit area and 100 times more connected devices than 4G. That means connecting up to 1 million 5G devices per square kilometer. Consumer mobile devices, Enterprise devices, smart sensors, autonomous vehicles, drones, etc. all share the same 5G network, without seeing service degradation as the number of connected devices increases.
FAST, LIVE, MASSIVE: Taken together, they equal disruption across the tech industry and the Enterprise. Companies will be able to connect more closely and often with employees, customers, and partners than ever before.
Behind the scenes, there’s a global architectural refactoring and infrastructure upgrade as telcos move away from in-house, monolithic solutions towards massively scalable, cloud-first enterprise designs. Telecoms like T-Mobile, AT&T, and Verizon in the US, and cloud providers like Amazon, Microsoft, and Google are all looking to lay claim to a piece of the market, which is on track to reach USD 700 billion at a 70.83% CAGR from 2020-2025 according to Market Research Future (MRFR).
What’s the exciting upshot of all this? The confluence of 4G-LTE, cloud, and smart mobile devices disrupted industries like taxis, hotels, and physical music media by enabling companies like Uber, Lyft, AirBnB, VRBO, Spotify, and Pandora. 5G offers a greater confluence of technological permutations including edge computing, private 5G, artificial intelligence, augmented reality, virtual reality, Industry 4.0, robots, and autonomous vehicles. This is expected to lead to a virtual “Cambrian explosion” of new business models and new revenue streams disrupting established businesses in unexpected ways.
Key industries facing 5G transformation
One way to appreciate the transformative impact of 5G is to consider what the convergence of device, edge, and cloud means to those industries that are already digitally mature. The first stop, however, is to consider how endpoints look once 5G optimizes broadband, latency, and coverage. We’ll have immersive platforms for education, gaming, and entertainment. Smart production driven by information convergence, industrial automation, and flexible production. Mixed reality headsets and glasses will add a new level of experience with real-time, localized context (like the Tokyo Olympics example earlier) for training, maintenance, and learning. Let's take a look at a few industries with the greatest potential.
In healthcare, 5G can enable remote biosensor monitoring and telemedicine, which are key uses accelerated by the COVID-19 pandemic. Looking further down the path, in areas where surgeons are in short supply or where operations are time-sensitive, tele-surgery can step in once sub-five millisecond latency is widely available.
Manufacturing stands poised for extreme efficiency with the advent of industrial factory automation made possible by IoT and 5G. According to an Oracle survey, 73% of respondents agree that IoT will be revolutionized by 5G networks. Imagine eliminating cabling and other instruments from factories and processes by using devices that don’t need to be connected to power sources. Businesses can save up to 90% power costs with IoT/5G devices that have batteries that last up to a year. In fact, low-power 5G devices such as electrochemical agriculture sensors or remote/buried pipeline monitors can be equipped with batteries with a 10-year life.
Furthermore, lower-level technicians in the field can use mixed-reality goggles to connect back to the office so that higher skilled workers can help with troubleshooting一to troubleshoot slowly rotating wind turbine, for example.
Government and defense is a final example where 5G can be a positive disruptor. “In the DoD’s case, 5G networks will allow information to get to decision-makers more quickly to help facilitate the real-time decision-making key to managing future conflicts,” said Jeff Verrant, director of Nokia Corporation’s U.S. Defense and National Security earlier in 2021.
Border monitoring in the face of human migration regulation is another application under consideration, as noted by Daniel Kroese, Deputy Assistant Director at the Cybersecurity and Infrastructure Agency’s (CISA) National Risk Management Center: “We have to mature the use cases so that when 5G is implemented on the border with thermal imaging and autonomous vehicles, we understand the unique characteristics and aspects of those 5G deployments in terms of the spectrum, low latency considerations, and can make sure the promise of 5G is realized.”
Refactoring at the edge to support new business models and customer experiences
CXOs that have been around to see the evolution of the modern tech stack can trace the origins of edge computing back to large, centralized data centers and colocation facilities. These evolved to distributed facilities in large metros. With the advent of the cloud, organizations shifted workloads from on-prem to private clouds and managed service providers for essential tools like Microsoft 365 and Salesforce. But as I said earlier, you can’t cheat the speed of light. A data packet traveling at the speed of light from the West coast to the East coast of the United States will ALWAYS take 15 ms or longer to make that trip. It takes packets in most mixed fibre/copper networks much longer. Network latency persists as a challenge today because data round trips from users and devices to workloads could be 20 ms or longer (typically 50-100 ms) even when located in the same metro, which not only can degrade user experience but is unsuitable for the kinds of immersive, data-intensive, real-time experiences businesses want - but currently can’t have.
Edge computing brings high-performance workloads, storage, and network resources to users and devices with latencies of 20ms down to sub-millisecond, unlocking new use cases for enterprises and their customers. As a consequence, enterprises may need to refactor their apps to take advantage of all that 5G offers.
Enterprise apps in the 5G world include edge platforms from providers like AWS (Wavelength), MSFT (Edge Zones), Google (Anthos). Some workloads can remain on-prem and others in public clouds. Where and how you place workloads will depend on latency, availability, cost, and network slicing. The telco's role in all of this has yet to be determined, but expect more changes in the operator/public cloud partnership picture.
Network slicing, which is when you run multiple virtual networks on the same physical network infrastructure, is still in its infancy. Think of network slicing like SD-WAN on steroids, where each isolated slice can be designed for specific requirements requested by particular application and use-cases. The smartphone slice and the business/IoT slice are two main buckets, then these will splinter further to include a critical performance slice that supports uses like autonomous vehicles, and an IoT/OT slice for telemetry, logistics, and Industry 4.0. Once such network slices are fully deployed they can offer a variety of security configurations and unique SLAs. Even better, you can start up (and tear down) slices of different performance characteristics to suit your immediate business needs一much like you use the cloud to scale your operations up or down today. With 5G, you’re going to eventually be renting your networks much like you rent computing resources today.
5G and cybersecurity
“Wait, isn't 5G secure by design?” The answer is yes, but only where it was designed to be secure...and that means the actual 5G networks. The workloads that your business runs on top of 5G are not inherently secure like the network. Just like you need to secure your workloads running in public clouds today, you will need to secure your 5G/Edge workloads.
5G represents a melding of telco operator, enterprise, and cloud technologies to deliver amazing new experiences and flexibility. But that also means more data, more services, more devices, more operating systems, and more unfamiliarity for everyone. Mixing so much technology in one place creates an attack surface that is huge. That surface now includes machine-to-machine (i.e., Industrial Internet of Things), and Edge compute as the new preferred cyber attack target.
Security professionals, enterprise IT, and third-party IT contractors and suppliers lack knowledge and experience to protect 5G networks and apps, and have a steep learning curve ahead of them. The simpler we can make 5G end-to-end security, the better it will be. According to Zscaler VP of Emerging Technology, Nathan Howe, “When 5G and MECs eventually render traditional networks obsolete, cloud-based security will become an enabler of security for Industry 4.0 and end customers alike.”
Taking zero trust down to the deep edge
“5G makes modern approaches to application access and zero trust more important and will accelerate the recognition that we don’t need a corporate network any more,” said Lisa Lorenzin, Director of Transformation Strategy at Zscaler.
5G and zero trust are a match made in heaven. Zero trust simplifies the protection of 5G/Edge workloads and devices. Organizations who embrace zero trust will find embracing 5G, with all of its security challenges, a lot easier, a lot faster, and a lot safer. Zero trust is the architecture for comprehensive security monitoring, granular risk-based access controls, infrastructure-wide coordinated system security automation, and real-time protection of critical data assets in a dynamic threat environment. This is just the architecture you need to be successful with 5G before all the specifications are complete and all the potential security shortcomings are addressed more fully.
“I’m most excited about the exponential expansion of new devices and applications that will eventually come from 5G. However, this creates a broader attack surface, which is why we work with companies like Zscaler who have the best solutions in the industry to protect users in the 5G world,” says S. Jay Lawrence, General Manager of Technology Enablement, SuperMicro Computer Inc.
An ounce of preparation is worth a pound of cure
The time to 5G impact is closer than you think. There are currently about 100 million 5G subscribers globally, representing a growth trajectory that is three times faster than 4G. Disruption of established business models (think taxis and hotels) started to happen when the 4G subscriber base exceeded 25% of the previous subscriber base. 5G global subscriptions are expected to reach 25% of the 4G subscriber base in 1-2 years. To get ahead of the competition and prepare, CXOs and transformation leaders should consider how to answer the following questions as they formulate their plans and objectives for the next 12-24 months:
- How could 5G power new alternatives to my offerings today?
- Which of my offerings that are not unique to me could be displaced by competitor offerings that incorporate 5G-enabled experiences?
- How could competitors deploy 5G to compete more effectively against my offerings?
The answers to those questions will inform your 5G plan and the cybersecurity upgrades it is reliant upon.
Recommended:
Watch on the on-demand Zenith Live 2020 breakout “5G and Zero Trust for Maximum Security” on YouTube or by selecting “Day 1,” and then selecting “Network Professional” on the Zenith Live site.
Recommended
