
TOP STORY
CISO Monthly Roundup, December 2024: State of encrypted attacks, malware deep-dives, and more
Jan 16, 2025
In this CISO Monthly Roundup, we highlight key findings from our encrypted attacks research, analyze campaigns using RevC2 and Venom Loader, detail techniques used by NodeLoader and RiseLoader malware, and unpack a Google Chrome extension compromise.
The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on cyber-related subjects. In this edition, we highlight the key findings from our latest research into encrypted attacks, analyze two campaigns using RevC2 and Venom Loader, a boost in the sophistication of Zloader, detail the techniques used by NodeLoader and RiseLoader malware, and unpack a malicious Google Chrome extension campaign.
Zscaler ThreatLabz 2024 Encrypted Attacks Report
The Zscaler ThreatLabz 2024 Encrypted Attacks Report highlights a significant trend in the threat landscape: the increasing use of encrypted channels by cybercriminals to deliver malware. The report, which is based on a comprehensive analysis of 32.1 billion encrypted attacks blocked by Zscaler between October 2023 and September 2024, shows that 87.2% of all blocked threats were delivered over encrypted channels such as TLS/SSL. This represents a 10.3% year-over-year increase, indicating that threat actors are continuing to leverage encryption to bypass traditional security measures and evade detection.

Key findings include:
- Predominance of malware: Malware is the most prevalent type of encrypted threat, constituting 86.5% of all blocked attacks.
- Surge in specific threat types: Cryptomining/cryptojacking and cross-site scripting (XSS) threats saw increases of 122.9% and 110.2%, respectively, while phishing threats rose by 34.1%.
- Abuse of cloud services: Advanced persistent threat (APT) groups are increasingly abusing legitimate cloud services to blend in with normal traffic and evade detection.
- Targeted sectors and regions: The manufacturing industry was the most affected, with 13.5 billion attack attempts, and the United States and India were the top targeted countries with 11 billion and 5.4 billion attacks, respectively.
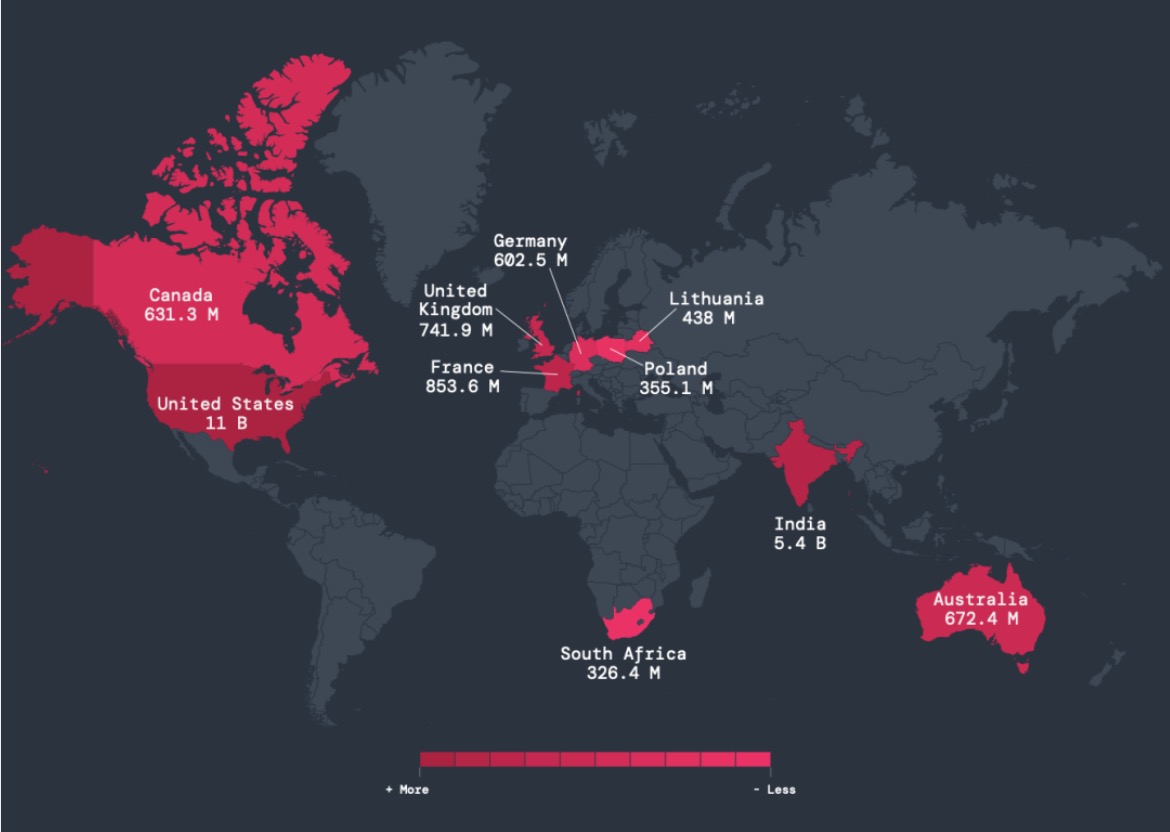
Figure 1: The countries that experienced the most encrypted attacks between October 2023 and September 2024 according to the Zscaler ThreatLabz 2024 Encrypted Attacks Report.
Defending against these types of attacks:
- Keep applications and services invisible to the internet to prevent encrypted threats from reaching critical systems.
- Reduce exposed workloads and eliminate unnecessary encrypted connections.
- Verify every connection with full TLS/SSL inspection to identify and block hidden threats.
- Use context-aware policies to limit user access to specific applications based on identity and context.
- Prevent lateral movement within the network by enforcing granular access controls.
- Inspect both outbound and inbound encrypted traffic to disrupt command-and-control (C2) communications.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
Unveiling RevC2 and Venom Loader
Zscaler ThreatLabz published a research blog on two campaigns using RevC2 and Venom Loader to deliver malware between August and October 2024. These two new malware families, which we named RevC2 and Venom Loader, were deployed through Venom Spider malware-as-service (MaaS) tools. RevC2, a backdoor malware, uses WebSockets for command-and-control (C2) communication and steals cookies and passwords, proxies network traffic, and executes remote code. Venom Loader, on the other hand, is a custom-built malware loader that encodes payloads using the victim’s computer name.
The first campaign we observed utilized an API documentation lure to deliver RevC2 through a VenomLNK file, as shown below.

Figure 2: Attack chain of the first campaign delivering RevC2 as the payload.
The second campaign, shown in the figure below, used a cryptocurrency transaction lure to deploy Venom Loader, which subsequently loaded the Retdoor backdoor. Retdoor provides remote code execution (RCE) capabilities, continuously communicating with its C2 server to execute commands.
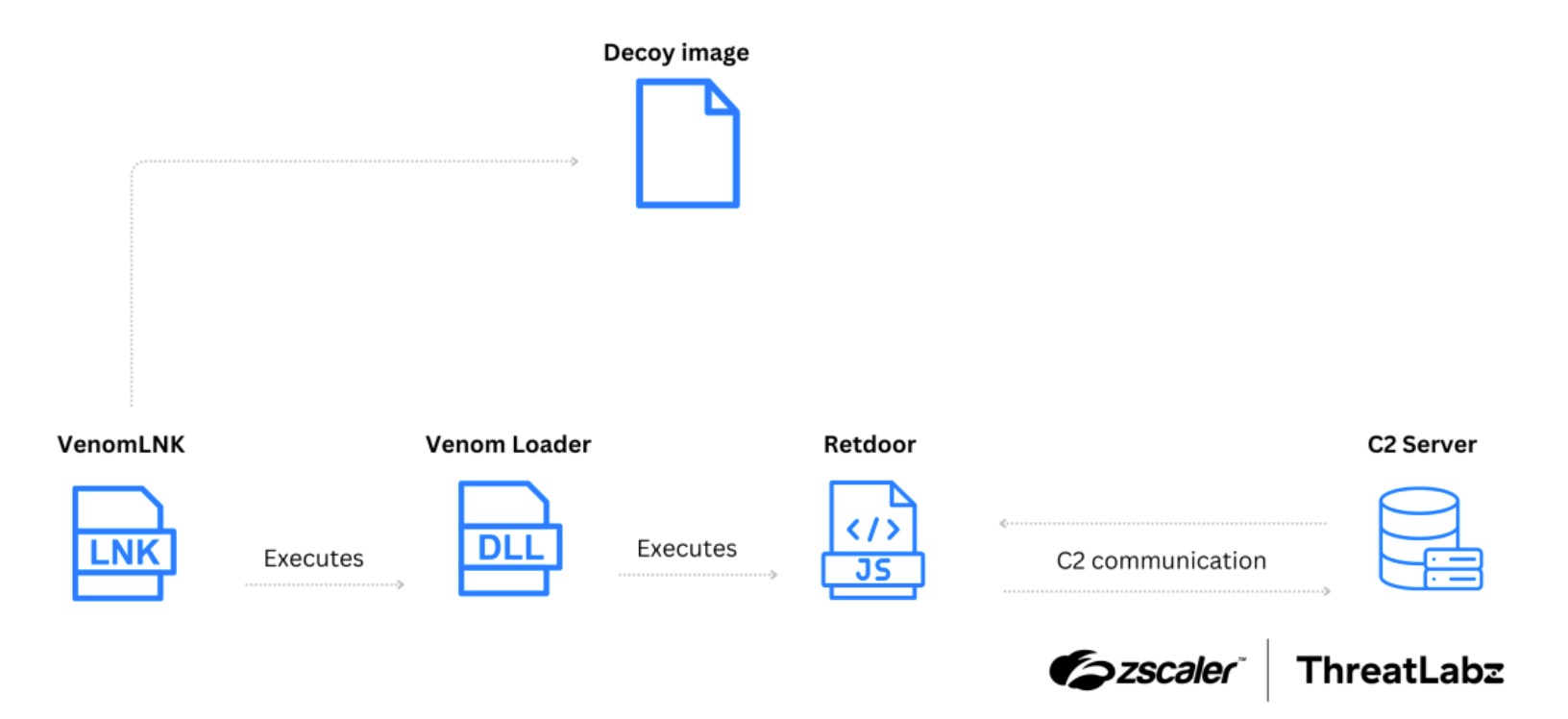
Figure 3: Attack chain of the second campaign delivering Retdoor as the payload.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
Inside Zloader’s Latest Trick: DNS Tunneling
Zscaler ThreatLabz released technical analysis of the latest version of Zloader, 2.9.4.0. Zloader, a modular Trojan based on the leaked Zeus source code, has evolved significantly since its emergence in 2015. Originally designed for banking fraud, it has been repurposed for initial access in corporate environments, facilitating ransomware deployment. Zloader 2.9.4.0 has introduced several features, including enhanced anti-analysis capabilities, an interactive shell for hands-on operations, and a sophisticated DNS tunneling protocol for command-and-control (C2) communications.
The distribution of Zloader has shifted towards more targeted attacks, often involving Remote Monitoring and Management (RMM) tools like AnyDesk, TeamViewer, and Microsoft Quick Assist. This version of Zloader employs a multi-stage infection chain, sometimes incorporating an additional payload known as GhostSocks to facilitate its deployment, as shown below.
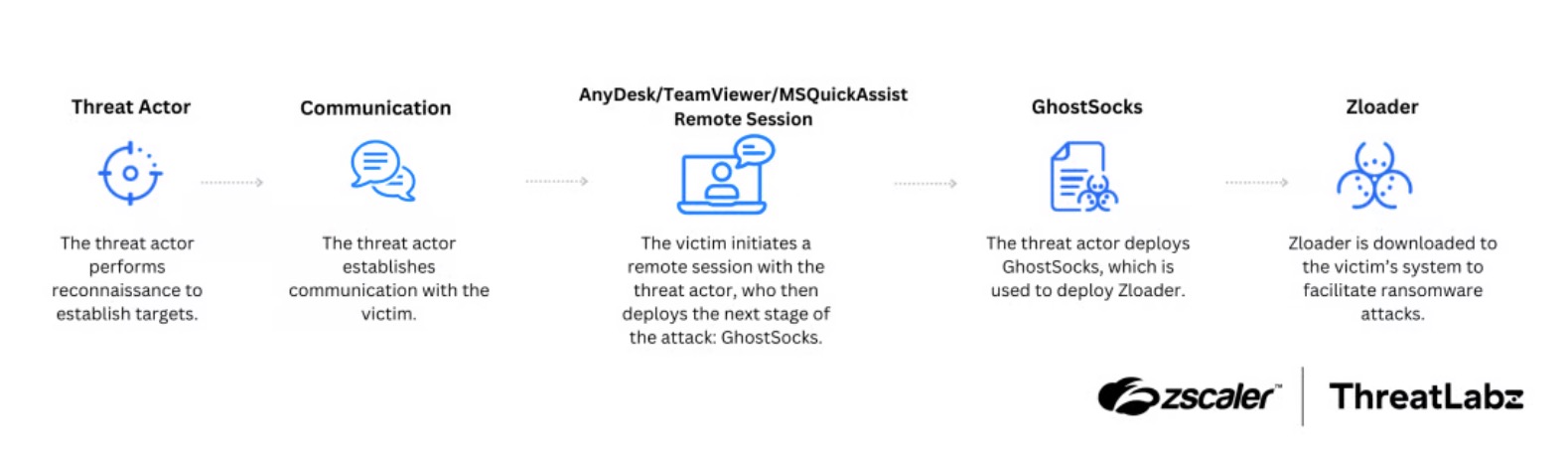
Figure 4: Example Zloader attack chain observed by ThreatLabz.
In addition, Zloader 2.9.4.0 has altered its configuration encryption, introduced a custom DNS tunnel protocol, and API resolution methods updated its anti-analysis checks. The updated process that Zloader uses to perform its anti-analysis environment check is shown in the figure below.

Figure 5: Example Zloader attack chain observed by ThreatLabz
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
NodeLoader Exposed: The Node.js Malware Evading Detection
Zscaler ThreatLabz documented a malware campaign we named NodeLoader that leverages Node.js applications for Windows to spread cryptocurrency miners and information stealers. This malware family, which utilizes Node.js compiled executables, employs social engineering and anti-evasion techniques to remain undetected. NodeLoader exploits the Node Package Manager (NPM) pkg module to create standalone Windows executable files, delivering second-stage payloads like XMRig, Lumma, and Phemedrone Stealer.
Attackers distribute NodeLoader via YouTube and Discord by embedding malicious links in video descriptions that lead to gaming websites. These sites prompt users to download a ZIP archive with the NodeLoader executable. Once run, NodeLoader uses privilege escalation, creates hidden directories, and downloads additional payloads using a PowerShell script. The attack chain is shown below.

Figure 6: High-level diagram for the NodeLoader attack chain.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection, DNS Security
Technical Analysis of RiseLoader
In October 2024, Zscaler ThreatLabz published a technical analysis on a new malware, which we named RiseLoader, that uses a network protocol similar to RisePro. Unlike RisePro, which steals information, RiseLoader downloads and runs additional malicious payloads. Due to the similarities and the discontinuation of RisePro's development in mid-2024, ThreatLabz suspects the same group behind RisePro and PrivateLoader is also behind RiseLoader. This malware uses a custom TCP-based binary protocol and has been seen deploying other malware like Vidar, Lumma Stealer, XMRig, and Socks5Systemz.
Our analysis dives deep into RiseLoader’s custom network communication protocol. RiseLoader collects and sends system and cryptocurrency information to the server. It processes downloaded payloads, creates a registry key as an infection marker, and terminates after completing its tasks. RiseLoader uses different message types like SEND_VICTIM_INFO for system info and PAYLOADS for executing tasks. The figure below shows a high-level view of RiseLoader’s network communication protocol.

Figure 7: RiseLoader’s custom network communication protocol.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
Addressing the Malicious Chrome Extension Campaign
On December 24, 2024, Cyberhaven's Chrome extension was compromised by a threat actor who used a phishing attack to gain access to a Cyberhaven employee's credentials, which were then used to publish a malicious version of the Cyberhaven Chrome extension. This incident was part of a broader attack campaign targeting Chrome extension developers. A list of affected extensions and their compromised versions can be found on Cyberhaven Incident.
Zscaler ThreatLabz analyzed several of the compromised extensions to examine the malicious scripts added by the threat actors and observed connections to known malicious Indicators of Compromise (IoCs).
Technical Details
We downloaded the Chrome Extension (CRX) archive for Reader Mode, one of the Chrome extensions that was compromised. The library folder of the bundle contains the infected script, as shown below.

Figure 8: Figure shows the lib folder containing the malicious script called safe-browsing.js.
The details of the malicious script along with the IoCs are shown below.

Figure 9: Detailed view of the malicious script, safe-browsing.js, along with IOCs.
Zscaler Coverage
Zscaler’s multilayered cloud security platform detects indicators related to this campaign at various levels as shown below.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
Recommended
