
CISO Monthly Roundup, March 2024: Zscaler ThreatLabz 2024 AI Security Report, Tweaks infostealer, Windows/Android RATs, and XZ Utils and ConnectWise vulnerabilities
Apr 8, 2024
CISO Monthly Roundup, March 2024: Zscaler ThreatLabz 2024 AI Security Report, Tweaks infostealer, Windows/Android RATs, and XZ Utils and ConnectWise vulnerabilities
The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with executive insights on other cyber-related subjects. This month we released the Zscaler ThreatLabz 2024 AI Security Report, investigated Tweaks infostealer, analyzed Windows/Android RATs, and reviewed vulnerabilities in ConnectWise and XZ Utils.
Zscaler ThreatLabz 2024 AI Security Report
ThreatLabz researchers analyzed how enterprises use AI/ML tools and observed trends across sectors and geographies in their 2024 AI Security Report. Our conclusions were drawn from the 18 billion AI transactions in the Zscaler Zero Trust Exchange occurring between April 2023 and January 2024. During this time we saw AI traffic increase nearly 600%. We also saw enterprises send over 569 terabytes of data to various AI tools from September 2023 to January 2024.
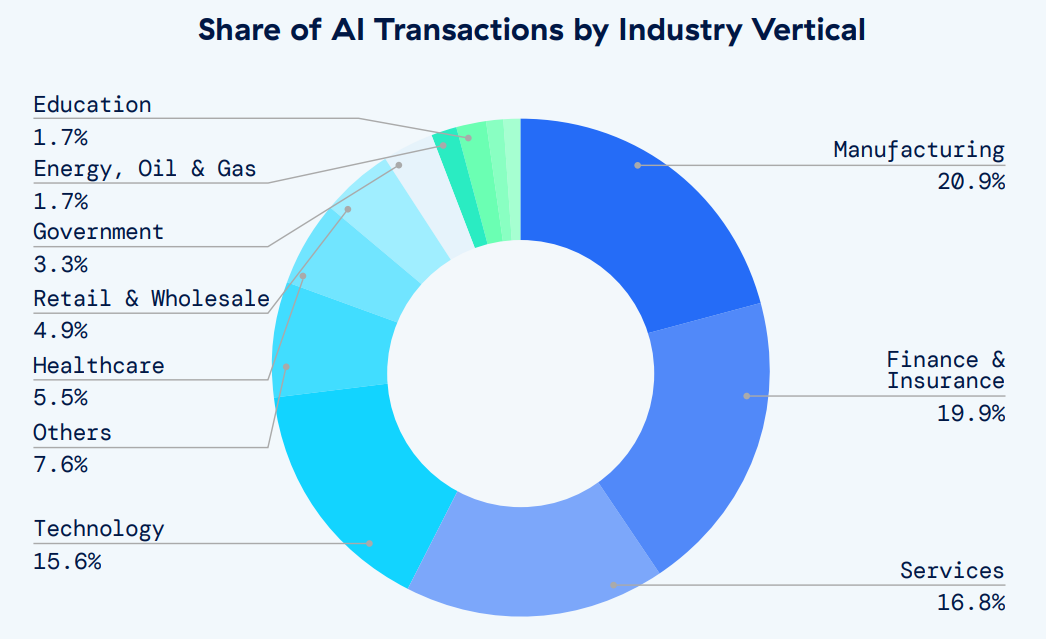
Some key findings in our report include:
- Enterprise AI/ML transactions increased from 521 million monthly in April 2023 to 3.1 billion monthly by January 2024.
- Manufacturing generates the most AI traffic, totaling 21% of all AI transactions in the Zscaler security cloud, followed by Finance and Insurance (20%) and Services (17%).
- The most popular AI/ML applications for enterprises by transaction volume are ChatGPT, Drift, OpenAI, Writer, and LivePerson.
- The top five countries generating the most enterprise AI transactions are the US, India, the UK, Australia, and Japan.
- Enterprises are blocking 18.5% of all AI/ML transactions—a 577% increase in blocked transactions over nine months
Top Generative AI Risks For Enterprises
Based on our comprehensive data and findings, these are the top generative AI priorities at the enterprise level to reduce risk:
- Protecting intellectual property and non-public information
- Data privacy and security risks of AI applications
- Data poisoning and data quality concerns: garbage in, garbage out
- Securing use of AI applications for productivity with guidelines and visibility
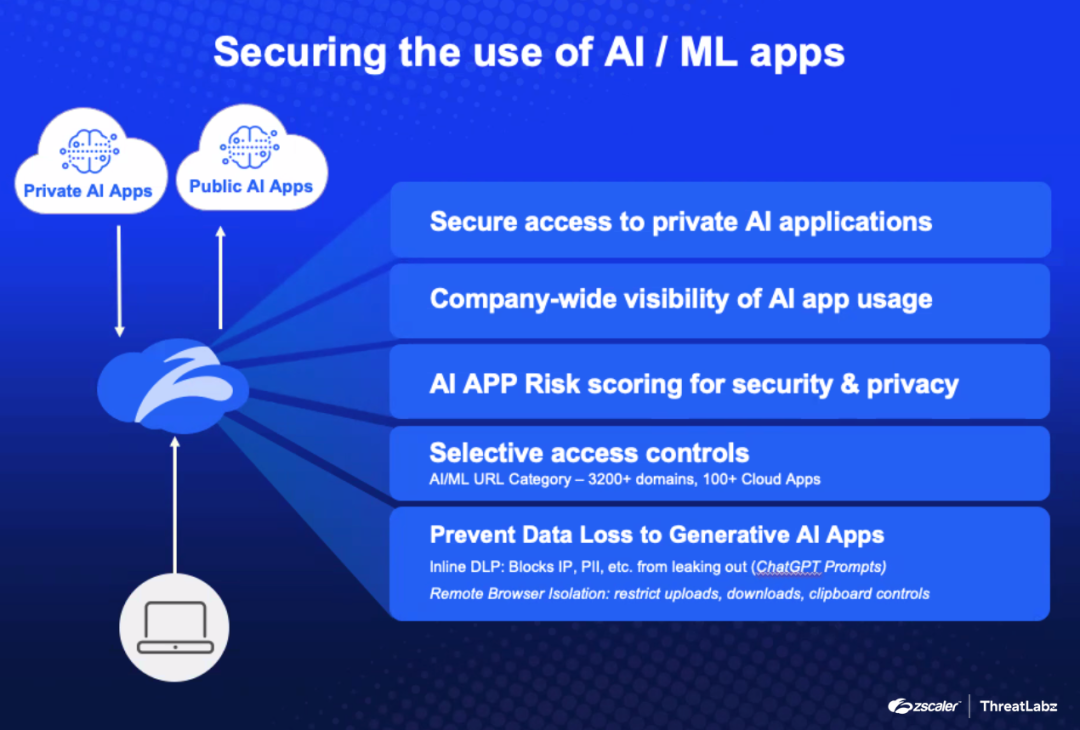
How Can Zscaler Help?
Zscaler products help secure the use of AI/ML apps in the following ways:
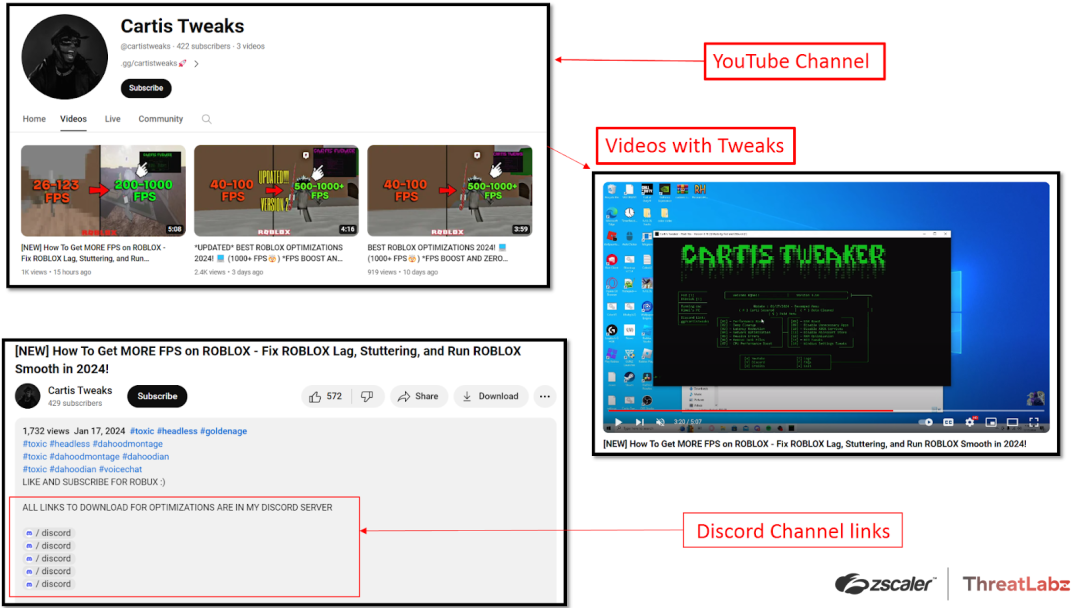
Tweaks Stealer Targets Roblox Users Through YouTube and Discord
Zscaler ThreatLabz has uncovered a new campaign distributing an infostealer called Tweaks, targeting Roblox users. Attackers exploit platforms like YouTube and Discord to distribute Tweaks malware, taking advantage of these legitimate platforms to evade detection by web filter block lists. Users are lured with FPS optimization packages, unaware that by downloading them they are infecting their systems with malware.
The figure below depicts description boxes of YouTube videos that contain links to the attacker's Discord groups, where users can download the malicious files.
The Tweaks malware steals sensitive data such as Wi-Fi profiles, passwords, UUIDs, usernames, user locations, IP addresses, system information, Roblox IDs, and in-game currency details. The stolen data is sent to the attacker-controlled server via Discord webhooks. Our blog highlights the risk posed by attackers leveraging popular platforms and the importance of exercising user caution when downloading applications from the internet.
Read more about Tweaks infostealer
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection, Browser Isolation, Data Loss Prevention.
Android and Windows RATs Distributed Via Zoom, Skype, Google and Meeting Lures
Zscaler ThreatLabz researchers discovered a threat actor deploying malware through fraudulent websites mimicking Skype, Google Meet, and Zoom. The adversary targets Android users with SpyNote RAT and Windows users with NjRAT and DCRat. The attacker employs shared web hosting to host all fake sites on a single IP address. These sites, written in Russian, utilize URLs resembling the legitimate platforms. The attack sequence involves users downloading malicious APK or BAT files, leading to the execution of Remote Access Trojans (RATs).
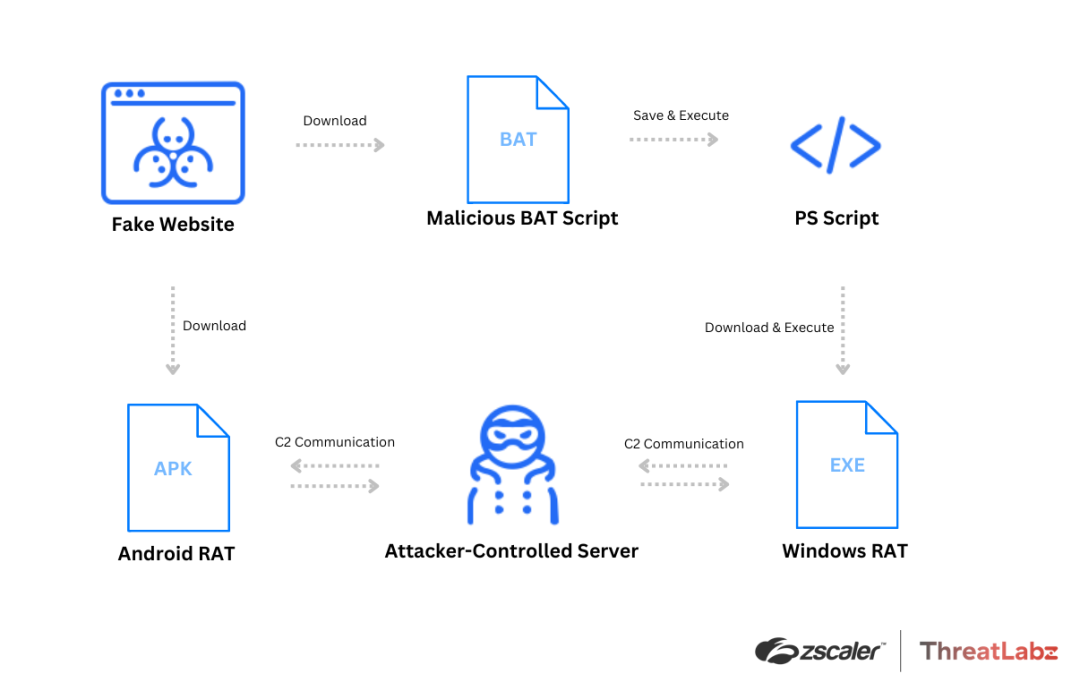
During our investigation the first fake site we discovered was join-skype[.]info. It is designed to deceive users into downloading a counterfeit Skype application. Another fake site, online-cloudmeeting[.]pro, imitates Google Meet and uses a subpath resembling a typical Google Meet joining link. The fake Zoom site, us06webzoomus[.]pro, features a subpath resembling a Zoom meeting ID. The Windows button on these sites triggers the download of BAT files, which subsequently downloads RAT payloads.
Additionally, the fake Google Meet and Zoom websites contain open directories with distinct Windows executable files named driver.exe and meet.exe, which are NjRAT.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection, Browser Isolation.
XZ Utils Vulnerability
A security incident involving XZ Utils was announced on March 29th. XZ Utils is a data compression package integrated into several major Linux distributions. A researcher discovered malicious code that could allow remote SSH access in versions 5.6.0 and 5.6.1 of this package. This discovery led to the vulnerability being assigned to CVE-2024-3094, and receiving a corresponding CVSS score of 10 (critical).
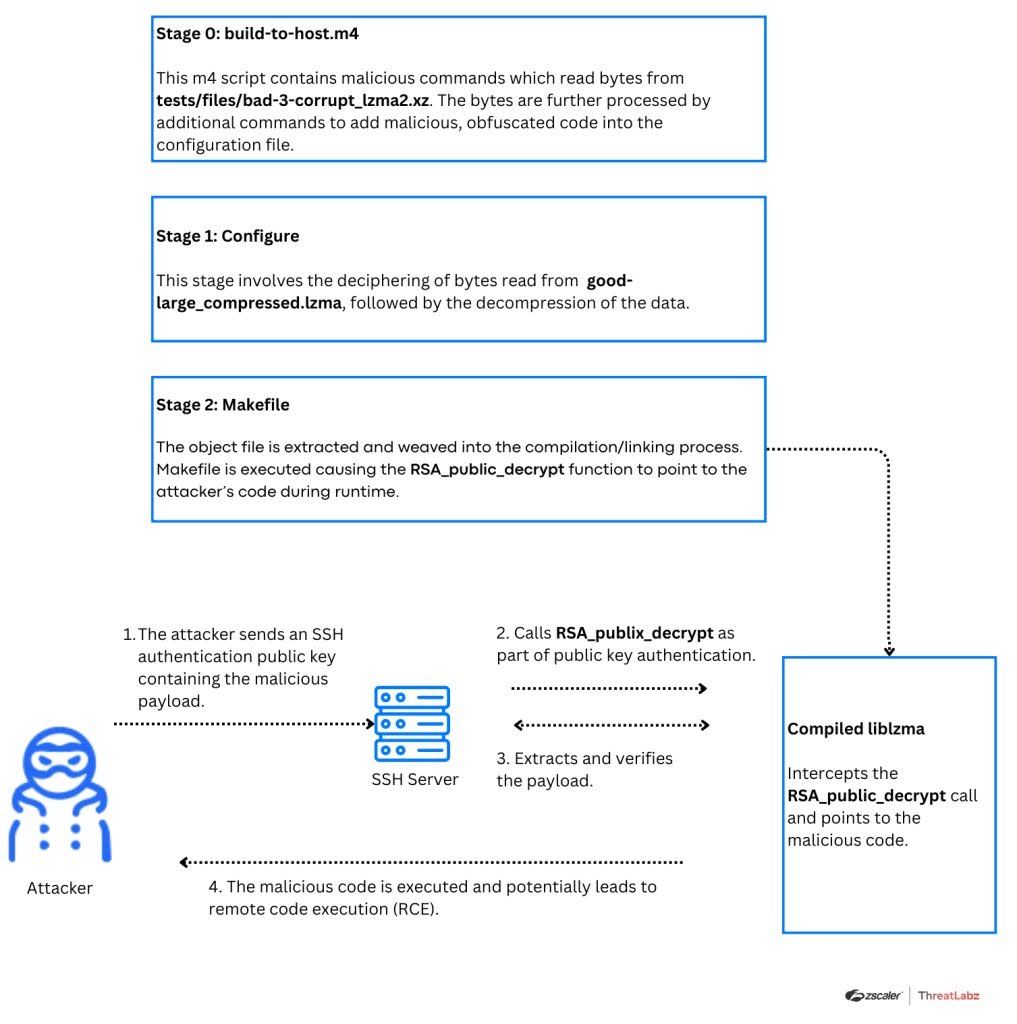
The goal of subverting XZ Utils is to allow attackers to inject code into an OpenSSH server (SSHD) running on the victim's machine. This will allow remote adversaries (who possess the private key) to send an arbitrary payload via SSH. The payload executes before the authentication step and can then issue commands on the victim’s machine. Read our blog for details on this vulnerability, how to detect it, and recommended security steps.
Details on XZ Utils vulnerability here
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection, Deception.
Multiple Vulnerabilities Found In ConnectWise ScreenConnect
ConnectWise ScreenConnect software has been found to have critical vulnerabilities, enabling attackers to bypass authentication and potentially achieve remote code execution. The vulnerabilities, CVE-2024-1709 and CVE-2024-1708, allow threat actors to exploit a path traversal flaw and upload malicious files. This can lead to compromising the affected ScreenConnect instances and acquiring unauthorized access to sensitive data.
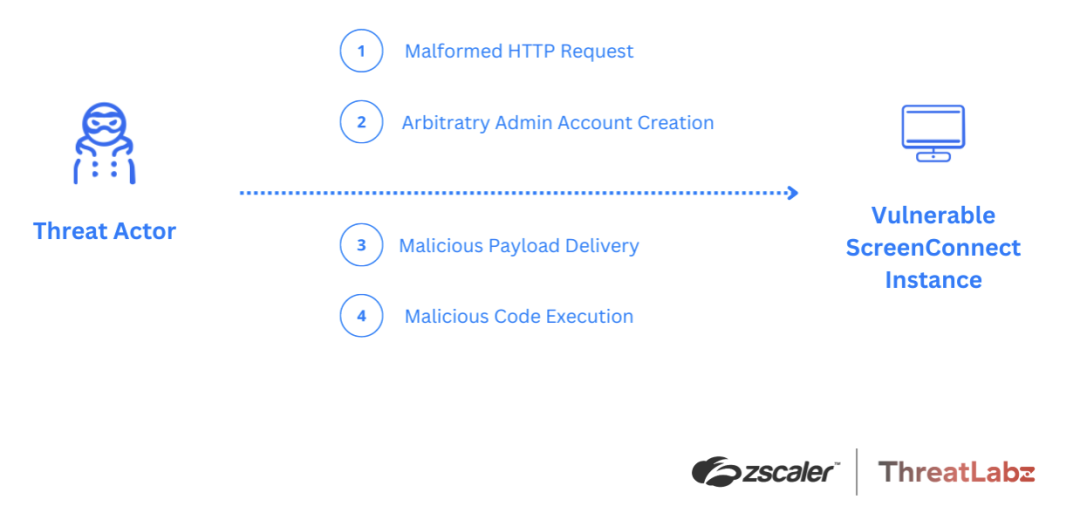
Zscaler ThreatLabz advises users to promptly update to the latest version of the software to mitigate these vulnerabilities. Our blog provides detailed technical analysis of the attack sequence and recommendations for safeguarding against these vulnerabilities.
More on the ConnectWise ScreenConnect vulnerability
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7700+ customers, securing over 390+ billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
CISOs, AI, and OT: A balancing act between innovation and protection
What it means to “fight AI with AI”
Five reasons why ransomware still reigns
Recommended
