
CISO Monthly Roundup, November 2022: World Cup-related threats, renewed attacks on the Indian government, holiday shopping scams, and malware in the Google Play Store
Dec 2, 2022
The November CISO Monthly Roundup explores World Cup-related threats, attacks targeting the Indian government, holiday season scams, and more.
The CISO Monthly Roundup provides the latest threat research from Deepen Desai and the ThreatLabz team, along with insights on other cyber-related subjects. In November, ThreatLabz uncovered several World Cup-related threats, new attacks on the Indian government, holiday skimming scams, and malware in the Google Play Store.
Surge of fake FIFA World Cup streaming sites
ThreatLabz is always watching for spikes in malicious activity tied to world news and events. As expected, the FIFA World Cup 2022 was promptly exploited by attackers using fake streaming sites to lure football fans. Our research uncovered a significant increase in newly registered domains related to the World Cup. Not all of these new sites are malicious, but a significant number are suspicious.
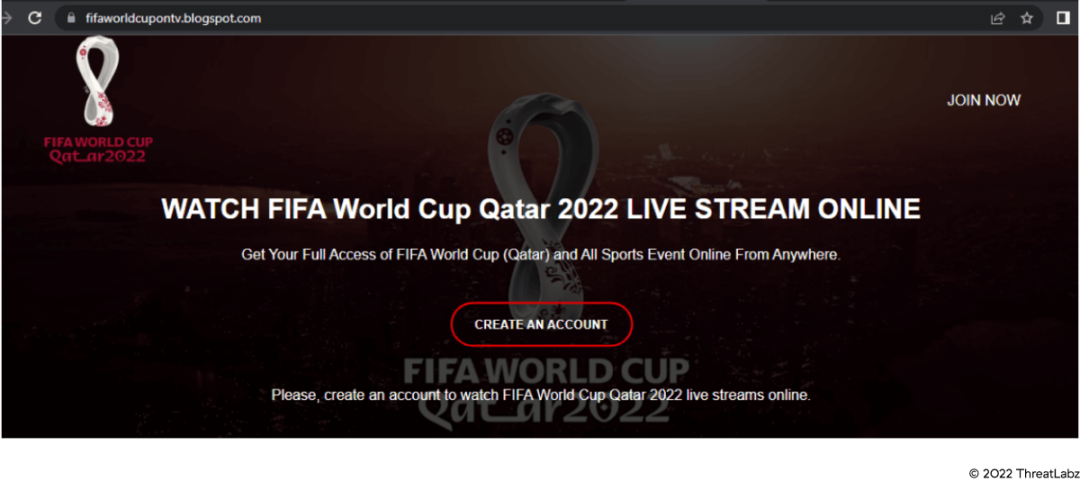
Some threat actors are using legitimate websites and portals to post malicious links. Other sites are running multiple related scams, offering World Cup tickets, airline tickets, themed lottery draws, and so on. In addition, malware families including SolarMarker have been seen using WorldCup related lures to deploy malicious MSI services. Attackers are also enticing unwary fans by offering malicious PDF files masquerading as cracked video copies of FIFA games.
Discover the many ways threat actors are exploiting the FIFA World Cup 2022
Zscaler Zero Trust Exchange Coverage: Advanced Threat Protection, SSL Inspection.
Transparent Tribe uses updated TTPs to attack Indian government
Transparent Tribe (aka APT-36) is a Pakistan-based threat group with a history of targeting users who work for the Indian government. Zscaler ThreatLabz has been monitoring APT-36 activity throughout 2022 and recently discovered them using new TTPs. Traditionally, the group has engaged in malvertising and credential phishing. Now, APT-36 is incorporating new distribution methods and tools.
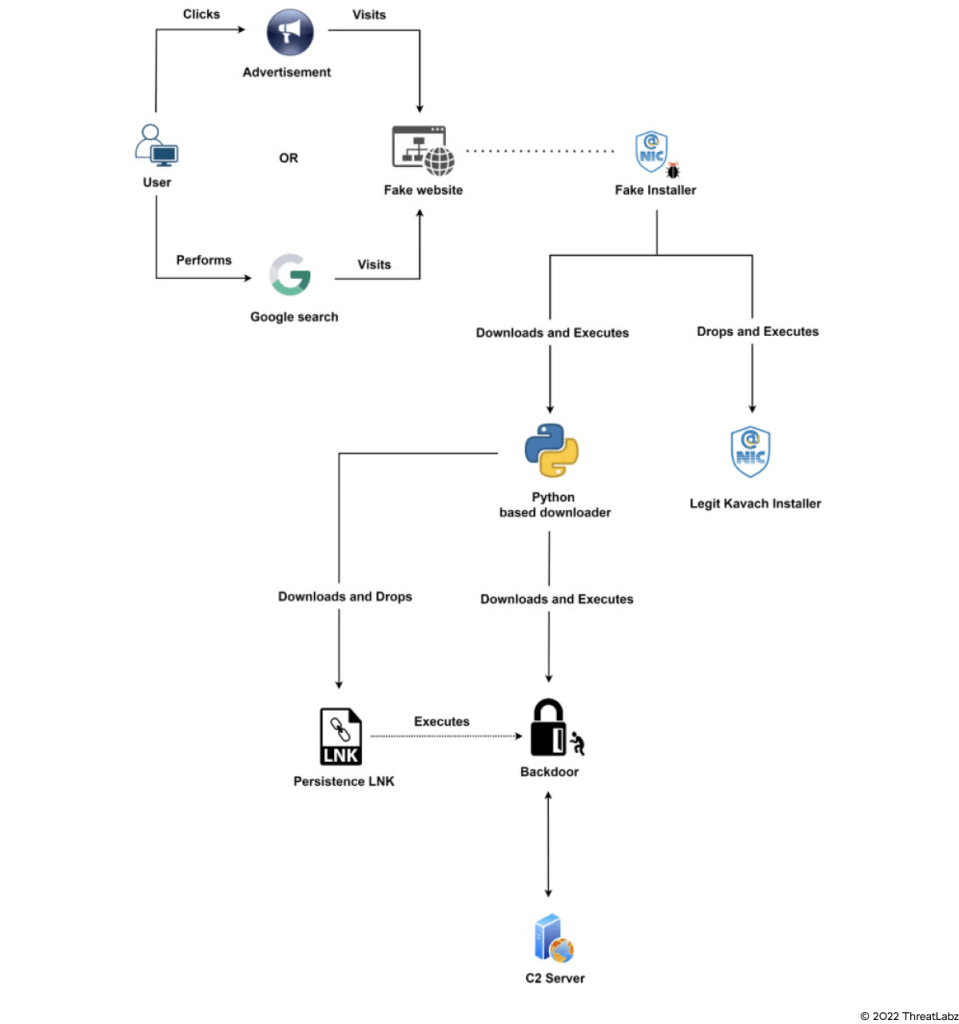
Transparent Tribe has registered multiple new domains to host web pages posing as legitimate download portals for the Kavach (authentication) app. They misused the paid search feature of the Google store to place their malicious domains near the top of Google search results for Indian users. APT-36 also unveiled LimePad, a new data exfiltration tool during its campaign. Many of the malicious binaries dropped by Transparent Tribe will only execute if the host machine is configured to Indian Standard Time (IST). The malicious binaries are often compiled with PyInstaller and hidden within VHDX archives.
Read an in-depth report of the current Transparent Tribe campaign
Zscaler Zero Trust Exchange Coverage: Advanced Threat Protection, SSL Inspection, Data Loss Prevention, Advanced Cloud Sandbox.
Holiday fraud alert: four emerging skimming attacks
Zscaler Threatlabz continuously monitors web threats, which include payment card skimming attacks. Over the past five months, we have observed an increase in these attacks against the Magento and PrestaShop ecommerce stores. For these campaigns, there is little or no documentation of the IOCs involved, and no current reports of them being discovered by other security vendors.
The affected stores are primarily located in the US, UK, Australia, and Canada. These skimming campaigns have a long shelf life, and have been able to keep their activities under the radar for months. New variants of these skimming campaigns are implementing JavaScript obfuscation, making them difficult to detect. As the US and other western nations enter their extended holiday season, it is likely these attacks will intensify.
Read the details of four recently revealed skimming attacks
Zscaler Zero Trust Exchange Coverage: Advanced Threat Protection, SSL Inspection, Data Loss Prevention.
Xenomorph banking trojan invades Google Play
ThreatLabz discovered the Xenomorph banking trojan embedded in an app called “Todo: Day manager”, on the Google Play Store. The app had over 1000 downloads, and is only one of over 50 malicious apps ThreatLabz has found in the store over the last three months. Xenomorph is designed to steal banking credentials from user’s devices. It intercepts SMS communications to steal passwords and circumvent MFA.
When the app is installed, the Xenomorph banking malware drops from GitHub as a fake Google Service application. It immediately asks users to enable access permissions. If the user agrees, the malware adds itself as a device admin and prevents other users from disabling the group account. This makes it impossible for users to manually uninstall Xenomorph from the phone.
Read detailed technical details on Xenomorph
https://www.zscaler.com/blogs/security-research/rise-banking-trojan-dropper-google-play-0
Zscaler Zero Trust Exchange Coverage: Advanced Threat Protection, SSL Inspection, Data Loss Prevention.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 6000+ customers securing over 240 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
Security Advisory for OpenSSL Vulnerabilities CVE-2022-3602 & CVE-2022-3786
2022 ThreatLabz State of Data Loss Report
New PHP Variant of Ducktail Infostealer Targeting Facebook Business Accounts
Recommended
