
TOP STORY
Dec 12, 2024
In the latest CISO Monthly Roundup, Zscaler CSO Deepen Desai provides cyber predictions for 2025, examines Raspberry Robin obfuscation techniques, and recaps his World Economic Forum visit.
The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on cyber-related subjects. In this edition, we provide predictions for the year ahead in cyber, examine obfuscation techniques used by Raspberry Robin malware, and recap my experience at the World Economic Forum.
Predictions for 2025
1. AI-powered social engineering will reach new highs
In 2025, GenAI will fuel voice phishing (vishing) attacks. With the proliferation of GenAI-based tooling, initial access broker groups will increasingly leverage AI-generated voices in combination with traditional channels. This will make it harder for victims to identify fraudulent communication as cybercriminals adopt local accents and dialects to enhance their credibility and success rates. The top three AI-powered social engineering attacks in 2025 will result in identity compromise, ransomware, and data exfiltration.
Figure 1: Zscaler CEO Jay Chaudhry describes an impersonation attempt against him to Fox Business.
We don’t need to go outside of Zscaler’s walls to find examples of such an attack. In 2023, a hacking group used AI technology to impersonate Zscaler CEO Jay Chaudhry in order to fool a company employee.
2. Fortifying GenAI security will continue to be a business imperative
As global organizations increasingly adopt generative AI applications, both first-party and third-party, securing these systems will continue to be a top priority. Generative AI applications introduced unique threat models, including risks of accidental data leakage as well as adversarial attacks aimed at poisoning AI application outputs.
In 2025, organizations will continue to focus on implementing effective security controls to protect AI models and sensitive data pools, and ensure the integrity of AI-generated content.
3. Businesses will face an increase in insider threat vectors
Threat actor groups are bypassing enterprise cybersecurity measures by planting malicious insiders as employees or contractors, or by compromising companies involved in mergers and acquisitions. Once inside, they use legitimate credentials and access to do real damage if the business is using legacy firewalls and VPNs.
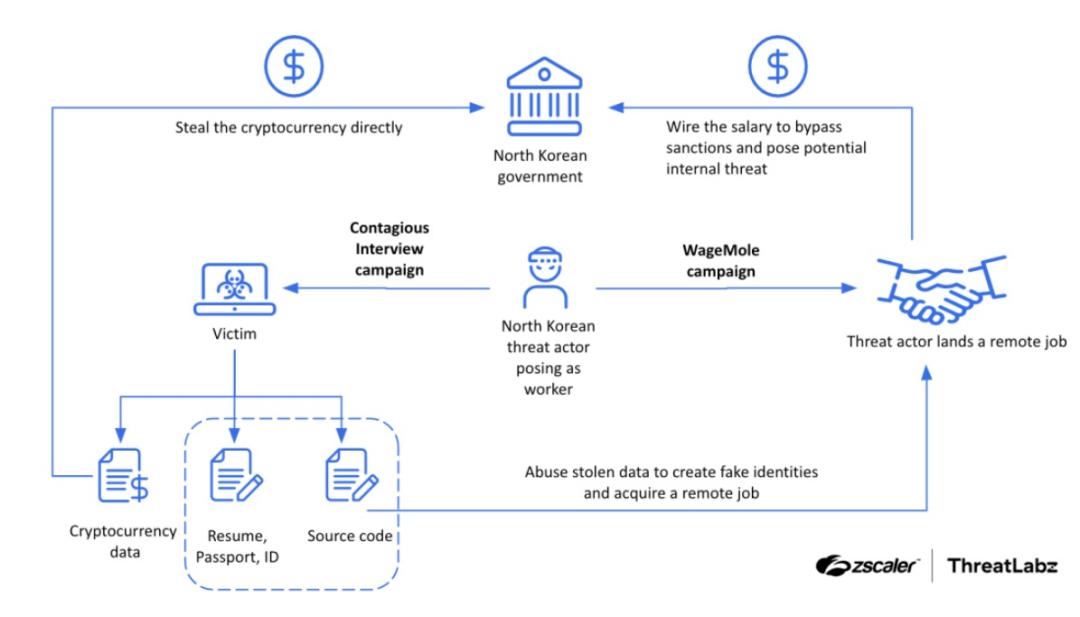
Figure 2: How North Korean threat actors carry out employment schemes.
As ThreatLabz documented late this year, North Korean threat actors were experimenting with Contagious Interview and WageMole campaigns to procure remote employment opportunities in Western countries. Through increasingly sophisticated means, these groups were able to increase their chances of success in stealing sensitive data and evading economic sanctions.
4. Regulation without harmonization may result in a weaker cybersecurity defense
Countries worldwide are introducing new regulations for cybersecurity and emerging technologies like AI and data privacy. Without harmonized regulations, the cybersecurity posture of organizations will suffer as resources are diverted towards compliance controls rather than meaningful risk reduction activity.
AI no doubt rises to the level of being a nation-state concern; there are fears regarding its impact on election integrity, disinformation capabilities, and potential to enable discriminatory tactics in areas like law enforcement. But, without adequate coordination, national and international organizations risk forcing emphasis on compliance over risk reduction in data security – as well as stifling innovation – when it comes to AI use.
5. Expect a rise in Adversary-in-the-Middle phishing attacks that evade multifactor authentication
Over the past year, a concerning trend has emerged where adversaries successfully circumvent enterprise multi-factor authentication (MFA) through Adversary-in-the-Middle (AiTM) proxy-based phishing attacks. In the coming year, we expect phishing kits to increasingly include sophisticated AiTM techniques, localized phishing content, and target fingerprinting—of course, enabled by AI. These advancements will allow attackers to conduct high-volume phishing campaigns aimed at evading MFA protections at enterprise scale. Organizations must prioritize adopting a stronger form of MFA (FIDO2 compliant) with zero trust architecture.
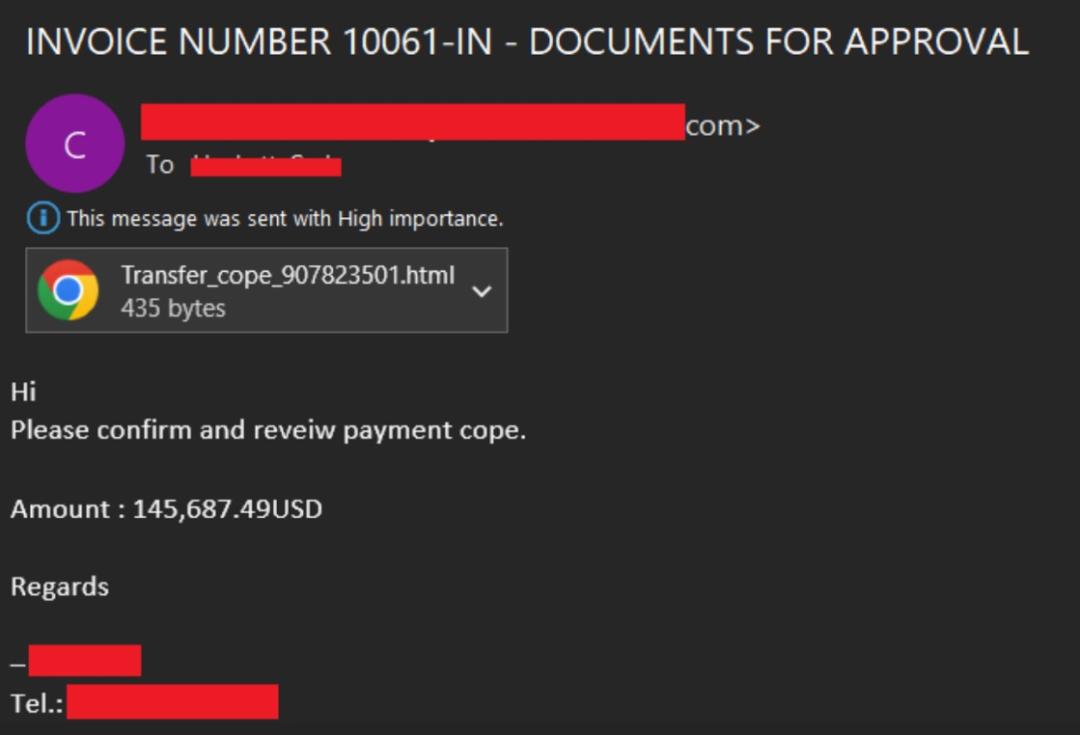
Figure 3: An example Adversary-in-the-Middle (AiTM) proxy-based phishing attack.
As the Zscaler ThreatLabz team documented this year, AiTM proxy kits today are able to closely mimic legitimate web pages, making them difficult for cybersecurity teams to identify. Threat actors distributing these proxy kits favor imitating widely trusted brands such as Microsoft and Gmail.
6. Rise in encryption-less, non-business disruptive ransomware attacks
Ransomware threat actors groups are increasingly targeting businesses without causing major disruptions by using encryption-less ransomware attacks, staying below the radar of media and law enforcement. These groups steal large volumes of data demanding ransom and see themselves as providing a valuable service to the companies by identifying their cyber vulnerabilities. This strategy allows them to exploit weaknesses while maintaining a low profile – a tactic that worked for Dark Angels and their historic ransomware payout.

Figure 4: The Dark Angels ransomware group received a historic payout in 2024.
As I discussed with the Information Security Media Group at Black Hat last year, this tactic is increasingly favored by cybercriminals looking to fly under the radar of law enforcement operations looking to disrupt groups like those behind the infamous SmokeLoader. As international cooperation continues to attempt to disrupt organized cybercrime, expect ransomware actors to place a premium on escaping the notice of security teams.
Peeling Back Raspberry Robin's Obfuscation Layers
Raspberry Robin, first identified in 2021, is a downloader malware primarily spread via infected USB devices. Raspberry Robin is notable for its use of binary obfuscation techniques, anti-analysis measures, and privilege escalation exploits. These methods help the malware evade detection.
The figure below shows a high-level view of Raspberry Robin’s multi-layered framework.

Figure 5: A high-level diagram of the multi-layered architecture of Raspberry Robin.
ThreatLabz published a technical analysis that explores the mechanics of Raspberry Robin’s techniques for obfuscation, propagation, and stealthy network communication.
Obfuscation
Raspberry Robin employs several obfuscation techniques designed to hinder analysis and detection. The malware utilizes control flow flattening to disrupt the local flow of its code, making it harder to analyze by reversing or tracing through the program’s execution. It also n incorporates Mixed Boolean-Arithmetic (MBA) obfuscation, which integrates both arithmetic and logical operations to further complicate reverse engineering.
To bypass security tools and sandboxes, Raspberry Robin includes anti-analysis mechanisms that detect these environments and deploy decoy payloads, creating misleading indicators for researchers. The malware also exploits privilege escalation vulnerabilities, granting it higher-level system access to maintain persistence and avoid detection. These layered obfuscation strategies allow the malware to evade automated and manual detection. For more details Raspberry Robin’s obfuscation, propagation, and communication tactics, visit our comprehensive technical analysis.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
World Economic Forum Annual Cybersecurity Summit 2024
I had the privilege of attending and speaking at the World Economic Forum (WEF) Annual Cybersecurity meeting in Geneva in November. This was my first time attending this annual meeting and the WEF team did an amazing job of including several critical cyber topics on the agenda. I was particularly impressed by the representation as well as interaction from several notable Global CXOs, global law enforcement agencies, regulators and ministers.

Figure 6: 2024 WEF Annual Cybersecurity Meeting Talk - CISOs in 2030: Flourishing Leaders or Endangered Species? [From left to right: Grant Bourzikas, CSO, Cloudflare; Yusuf Ezzy, CISO, Pacific Gas and Electric Company; ; Debbie Janeczek, CSO, Swift; Stefan A. Deutscher, Partner & Director, Cyber Security & IT Infrastructure, Boston Consulting Group; Deepen Desai, CSO, Zscaler; James Dolph, CISO, Guidewire Software; Joe Sullivan, CEO, Joe Sullivan Security]
Summarizing top 5 key points from various insightful discussions that I was part of:
- Securing generative AI (including Agentic AI) remains a top priority for most global CXOs. Experienced CISOs shared their insights on treating generative AI applications like any other enterprise application, rather than creating separate programs for them. Key areas of focus included security assessments, threat modeling, TLS inspection, and Data Loss Prevention controls.
- As adversaries increasingly target software supply chains, including contractors, software supply chain security remains a top priority for global CXOs. In addition to strengthening third-party risk management programs, implementing a zero trust architecture with segmentation for your crown jewels, including CI/CD environments and in-line inspection for threats and data leakage, becomes critical to defend against software supply chain attacks.
- Organizations must prioritize IT and cyber resiliency for all critical service providers with clear guidelines for consumers and vendors. Configuring and testing your Business continuity plans / disaster recovery (BCP/DR) maturity for all critical service providers is of utmost importance. Your vendor platforms must support native BCP/DR configuration, test, and audit functionality. Many CXOs have already scheduled BCP/DR focused tabletop exercises.
- Another focus area was the need for harmonization of controls across several global new and upcoming cybersecurity regulations, including those covering emerging technologies like generative AI. Cybercriminals are actively exploiting lapses in regulatory requirements as a means of extortion. Collaboration between industry and regulators will be key to meaningful risk reduction for global organizations.
- Quantum computing will give rise to a new dimension of threats that global CXO need to start planning and securing against over the next decade. We are already seeing cyberattacks where nation-state threat actors are stealing encrypted TLS sessions with the intent of breaking the encryption and decrypting it in future, especially if the underlying cryptography is not quantum safe, a standard still not widely adopted.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
Recommended
