
CXO Monthly Roundup, August 2025: Salesloft Drift Compromise, GenAI-Driven Phishing and increased usage of RMM tools for persistence, Python Supply Chain Vulnerability in PyPI, and Evolving Malware
Sep 15, 2025
Highlights from the Zscaler ThreatLabz team's August 2025 research.
The CXO Monthly Roundup provides the latest Zscaler ThreatLabz research, alongside insights into other cyber-related subjects that matter to technology executives. This August edition includes my insights into the Salesloft Drift compromise and highlights an AI-powered phishing campaign, a significant vulnerability discovered by ThreatLabz in the Python Package Index (PyPI), and updates to Anatsa and Raspberry Robin malware.
Commenting on the Salesloft Drift compromise
A threat actor compromised the Salesloft Drift application early this year and managed to steal OAuth tokens associated with the Drift customer’s technology integrations. Using these tokens, the actor gained unauthorized access to multiple SaaS platforms including Salesforce impacting several hundred organizations, including Zscaler.
I want to emphasize that the scope of the incident is confined to the Salesloft Drift application and does not involve access to any of Zscaler's products, services, or underlying systems and infrastructure. Following a thorough investigation, Zscaler determined that the credentials compromised granted only limited access to certain Salesforce information. Moreover, there is currently no evidence to suggest that the accessed information has been misused by the threat actor or any other party.
If your organization was impacted, here are some recommendations to mitigate exposure:
- Be wary of potential phishing attacks or social engineering attempts, which could leverage exposed contact details.
- Exercise caution regarding unsolicited communications, including emails, phone calls, or requests for sensitive information.
- Always verify the source of communication and never disclose passwords or financial data via unofficial channels.
- Remember that Zscaler Support will never request authentication or authorization details through unsolicited outreach, including phone calls or SMS.
At Zscaler, we take the security of our customers very seriously. Transparency and swift communication are core to our response strategy. For more information, please visit Salesloft Drift Supply Chain Incident: Key Details and Zscaler's Response.
Navigating GenAI’s double-edged impact
As I’ve mentioned in previous blogs, the proliferation of AI tools is a two-way street, presenting both opportunities and challenges for enterprises. The ThreatLabz team published a technical analysis of malicious phishing campaigns leveraging code-generating AI tools to target Brazilian citizens. These campaigns replicate official government websites, such as the Brazilian State Department of Traffic and the Ministry of Education where Brazilian citizens might seek driving licenses and job opportunities. The replicas are very convincing copies that, at a glance, look exactly like the authentic websites, as shown in the figure below.
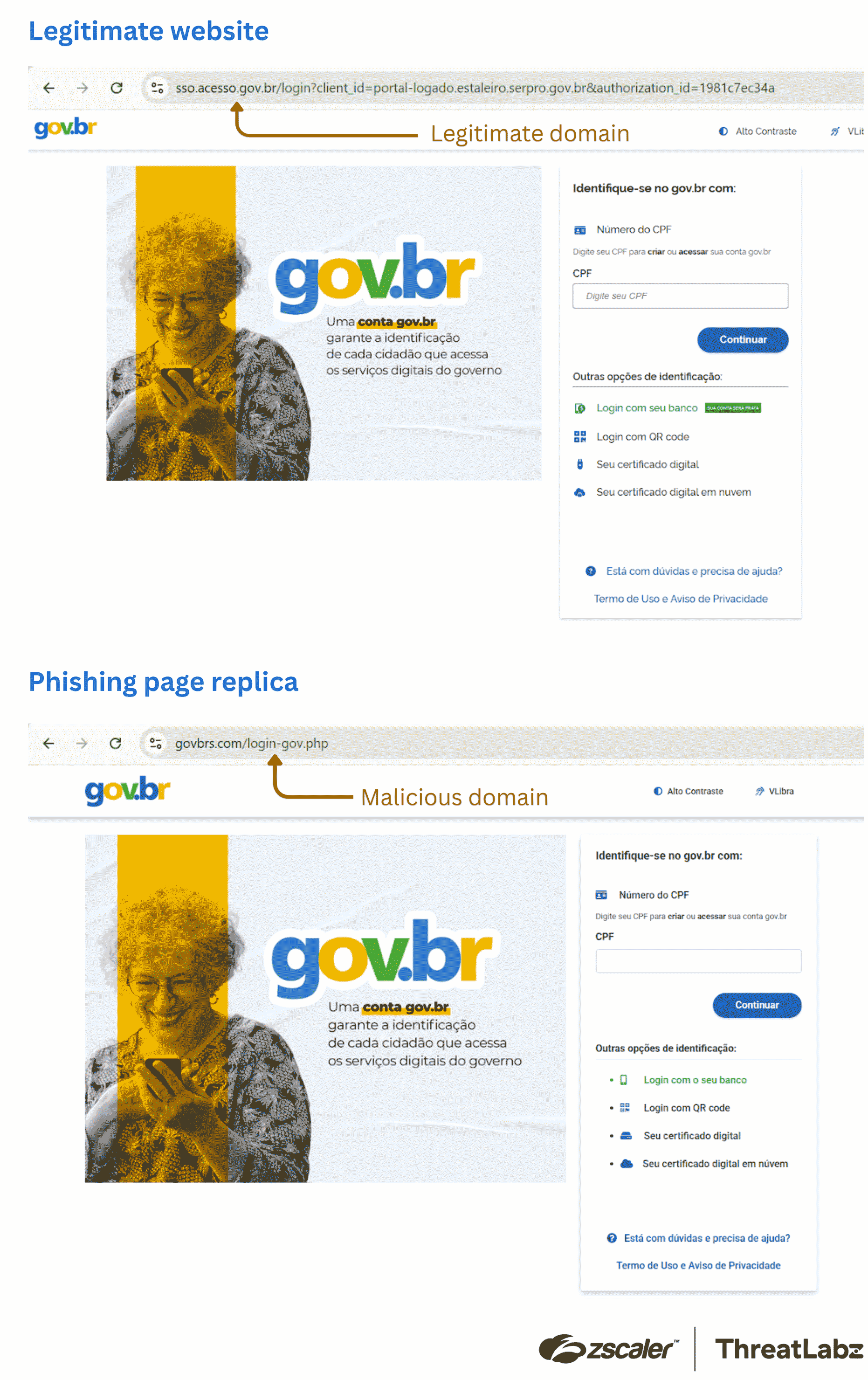
Figure 1: Side-by-side comparison of the legitimate and a phishing page associated with the Brazilian State Department of Traffic.
In addition, the threat actors behind this campaign used SEO poisoning techniques to ensure that their phishing replicas ranked highly and were easily accessible to users. The figure below depicts an example search with phishing pages shown as the first two results.
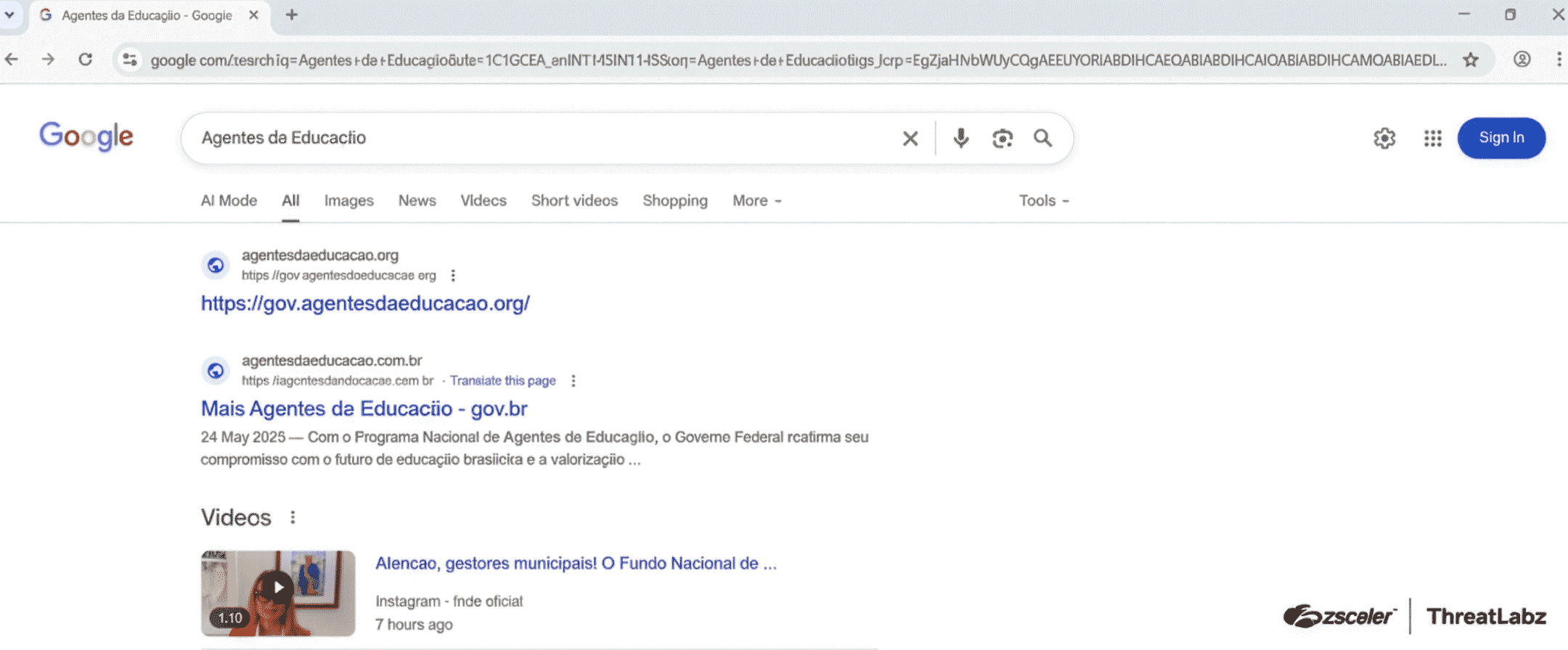
Figure 2: Threat actors use SEO poisoning techniques to boost their phishing pages in search results.
The campaign gradually gathers more sensitive information from victims as the flow progresses and uses backend APIs that look legitimate by sending responses. Eventually, the victims are tricked into paying the attacker directly through a payment platform popular in Brazil.
In addition to examining the campaign, the ThreatLabz team highlights some strong signs that the threat actor used AI-generated code, such as overly explanatory code comments meant to guide developers, non-functional interface elements recreated by the AI but ignored by the threat actor, and the frequent use of the TailwindCSS and FontAwesome CSS libraries. To learn more, visit GenAI Used For Phishing Websites Impersonating Brazil’s Government.
Active attacks leveraging multiple RMM tools to evade detection and maintain persistence
The Zscaler Threat Hunting team has identified multiple campaigns utilizing the RMM tools ITarian (also known as Comodo), PDQ, SimpleHelp, and Atera for remote access. Remote monitoring and management (RMM) tools continue to be a favorite choice for adversaries because they offer a veneer of legitimacy, as these solutions are often used by IT professionals for remote access, system monitoring, and managing machines without raising immediate alarms.
Adversaries are increasingly using the ‘Living-off-the-trusted-sites’ technique, where they abuse legitimate SaaS services to deliver these RMM tools, along with subsequent payloads such as information stealers or ransomware.
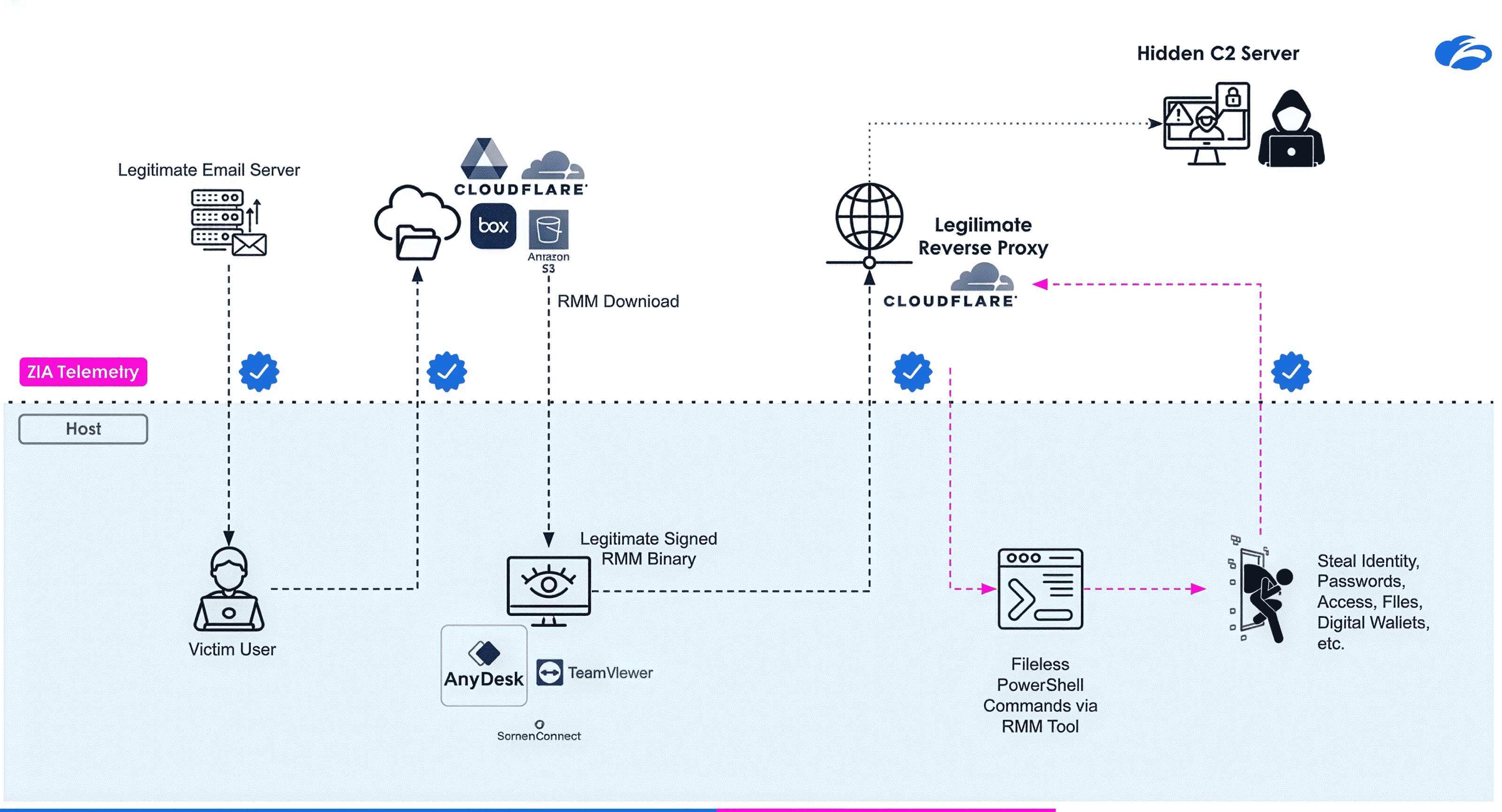
Figure 3: The attack chain illustrates how RMM tools are deployed to evade detection and establish persistence.
We have identified four common lure themes that have successfully led adversaries to download an RMM tool onto the target system:
- Fake browser update lures
- Meeting invitations
- Party invitations
- Fake government forms
Additionally, we have observed a trend in adversaries utilizing two RMM tools in quick succession, likely to establish multiple methods of persistent access.
ThreatLabz discovers potential supply chain vulnerability in PyPI
The ThreatLabz team regularly monitors for threats in the popular Python Package Index (PyPI), which contains open source libraries that are frequently used by many Python developers. On July 22, 2025, ThreatLabz discovered a suspicious Python package named termncolor, which at first glance appeared like a benign color utility but secretly introduced malicious behavior through its dependency, colorinal. The malware is capable of remote code execution (RCE), opening up the opportunity for threat actors to orchestrate supply chain attacks.
The colorinal dependency can deliver a multi-stage payload. Upon execution, colorinal loads a DLL file which decrypts and deploys two files: a legitimate-looking executable and another malicious DLL that gathers information from the victim’s system and sends it to the threat actor’s command-and-control (C2) server. The first stage of the attack involves AES-based payload decryption and staging directories. The second stage of the attack involves the malware collecting information and executing shellcode received from the C2 server. The figure below illustrates the potential attack chain connected to the PyPI package discovery.
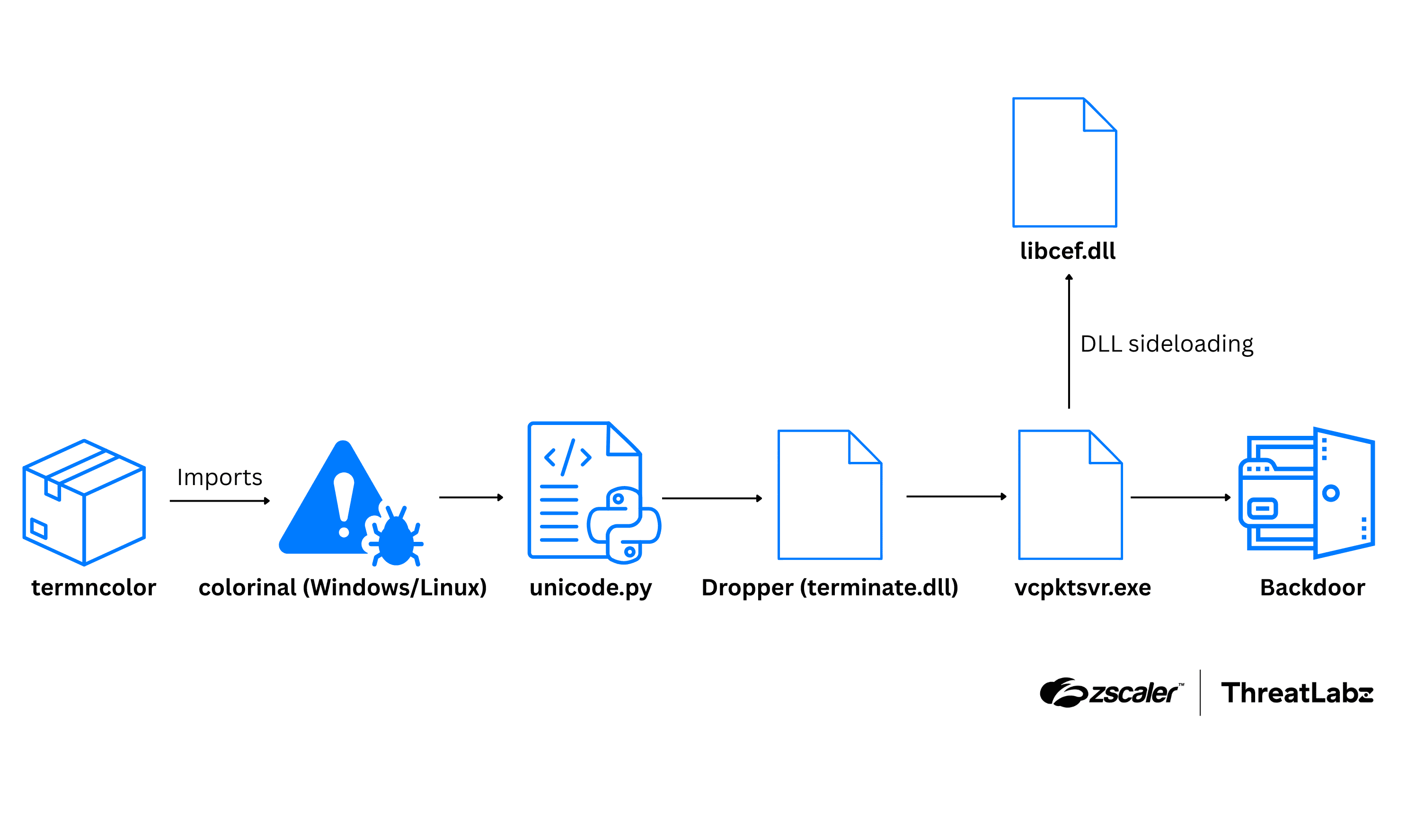
Figure 4: The attack chain illustrates how termncolor could import colorinal, which would trigger unicode.py to deploy a malicious DLL via sideloading.
The malware utilizes techniques such as DLL sideloading, API hashing for obfuscation, and setting up persistence by creating a registry entry under the Windows Run key. In addition, the malware hides in plain sight by mimicking Zulip network traffic (Zulip is a legitimate messaging platform). To impact as many platforms as possible, the malware includes a Linux variant. To learn more details about this supply chain risk, visit Supply Chain Risk in Python: Termncolor and Colorinal Explained.
Anatsa malware continues to evolve
The ThreatLabz team published blog post outlining many of Anatsa’s recent updates. Anatsa has been around since at least 2020 and is often leveraged by threat actors attempting to distribute malware in the Google Play Store.
Our blog post dives into Anatsa’s updates such as expanding its reach to new regions (Germany and South Korea), adding support for 150 more banking applications, and replacing the use of dynamic code loading for remote Dalvik Executable (DEX) payloads with direct payload installation. For the most part, Anatsa continues to operate as we have documented in the past. Anatsa uses a dropper technique, where the threat actors use a decoy application in the official Google Play Store that appears benign upon installation. Once installed, Anatsa silently downloads a malicious payload disguised as an update from its C2 server. This approach allows Anatsa to bypass Google Play Store detection mechanisms and successfully infect devices.
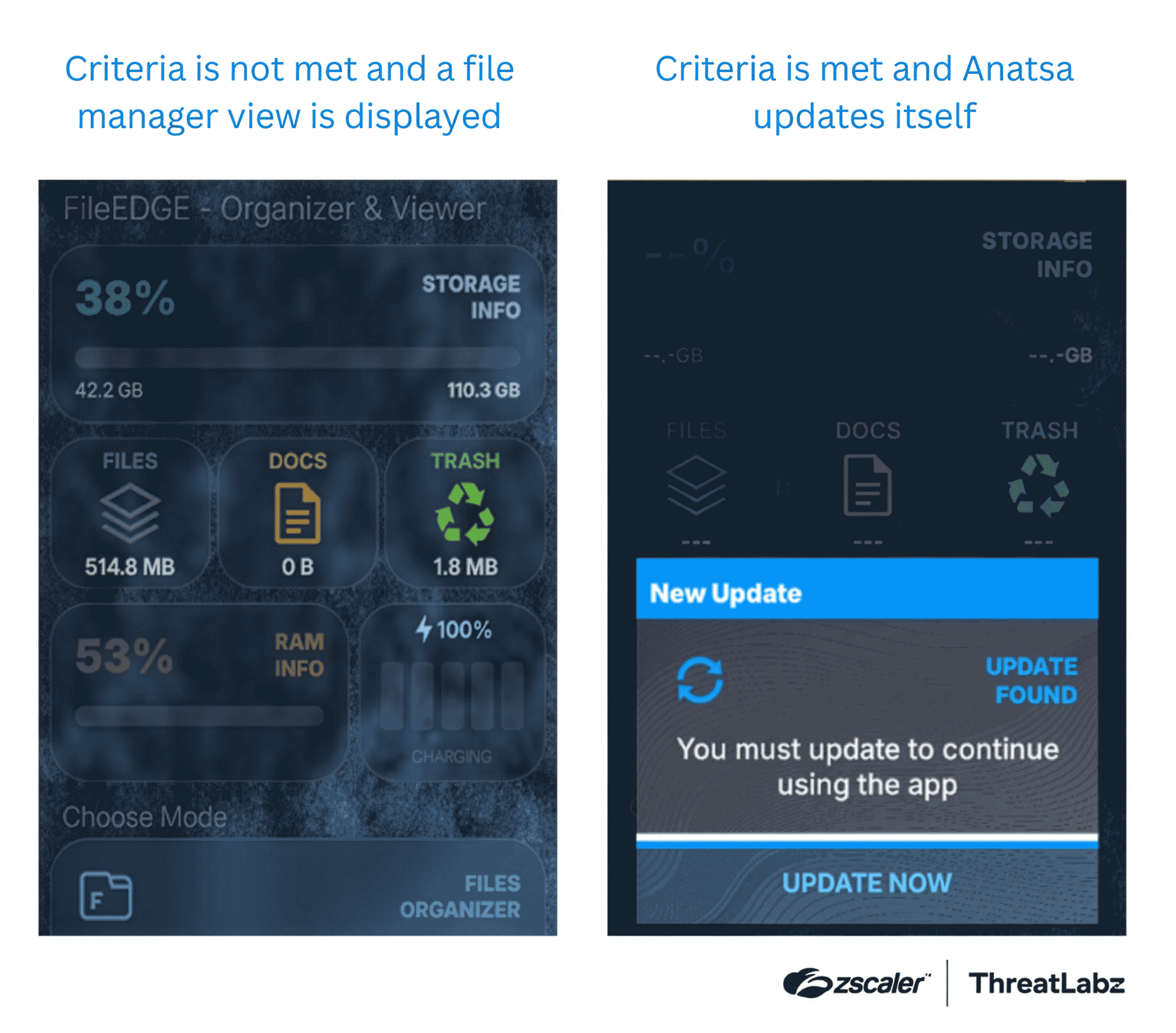
Figure 5: Example behavior of the Anatsa installer depending on the result of anti-analysis checks.
In addition to analyzing Anatsa’s recent updates, ThreatLabz identified and reported 77 malicious apps from various malware families to Google which collectively accounted for over 19 million installs. To learn more, visit Android Document Readers and Deception: Tracking the Latest Updates to Anatsa.
Tracking updates to Raspberry Robin
The ThreatLabz team published a technical analysis on Raspberry Robin’s most recent updates. Raspberry Robin, also known as Roshtyak, is a malware downloader first seen in 2021 that ThreatLabz has documented in the past. Raspberry Robin primarily spreads via infected USB devices, and its malware authors are consistently introducing and enhancing features.
In this case, the malware authors made changes to Raspberry Robin to improve its evasion capabilities. The malware now employs more complex obfuscation methods, such as adding initialization loops to functions, obfuscated stack pointers disrupting automated decompilation tools, and conditional statement obfuscation to complicate code analysis. Additionally, Raspberry Robin has transitioned from AES-CTR to ChaCha-20 for network encryption, embedding hardcoded keys while randomizing nonce and counter values per request. Its deliberate use of corrupted TOR onion domains to disguise C2 servers further complicates identifying indicators of compromise (IOCs). To learn more, visit Tracking Updates to Raspberry Robin.
Recommended
