
CXO Monthly Roundup, November 2025: React2Shell, insights into how Zscaler Deception fights AI-driven threats, vulnerabilities uncovered by ThreatLabz, and Water Gamayun APT attack analysis
Dec 12, 2025
Highlights from the Zscaler ThreatLabz team's November 2025 research.
The CXO Monthly Roundup provides the latest Zscaler ThreatLabz research and critical updates, featuring coverage of the React2Shell vulnerability, insights into how Zscaler Deception fights AI-driven threats, key discoveries from Zscaler threat analysis, a detailed examination of a Water Gamayun APT attack, and the latest threat intelligence on DanaBot and TransferLoader.
React2Shell (CVE-2025-55182) vulnerability
We will begin by examining an urgent and critical security issue with a wide attack surface: React2Shell. On December 3, 2025, CVE-2025-55182 was publicly disclosed, revealing a severe vulnerability that allows attackers to execute remote code on affected servers. Given that React Server Components (RSC) are widely implemented across industries and sectors, the implications of this flaw are far-reaching. In fact, within the first two hours of its disclosure, over 4,100 exploitation attempts were recorded.
How it works
CVE-2025-55182 (aka React2Shell) exploits the Flight protocol used in RSC and can be triggered by a malicious HTTP POST request.
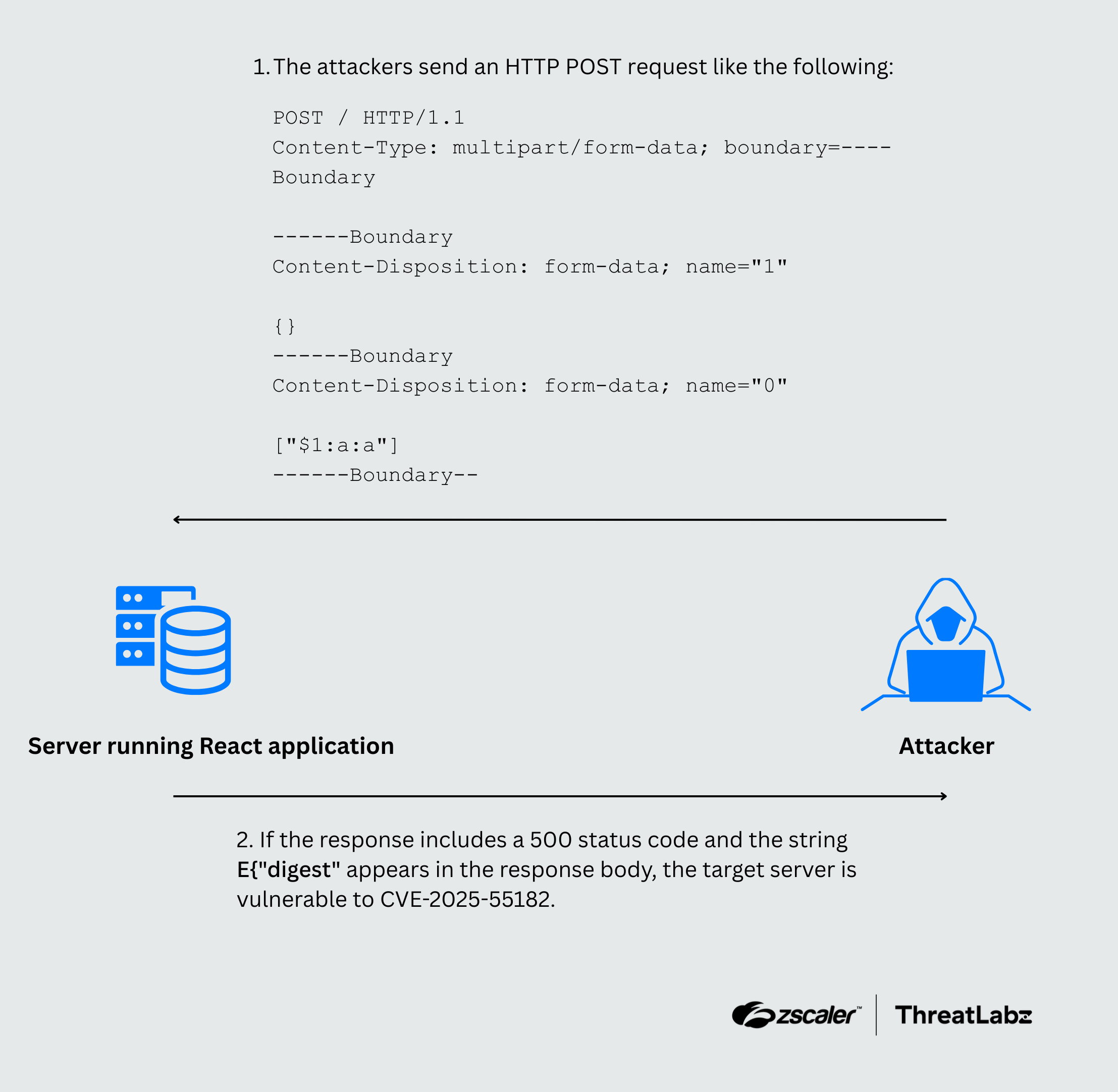
Figure 1: Diagram illustrating the attack flow for CVE-2025-55182.
Recommendation
ThreatLabz recommends that administrators of applications built on React and Next.js follow these recommendations.
Zscaler protects customers
Zscaler customers using Zscaler Deception technology observed exploitation attempts within their perimeter-facing decoy applications, which enabled them to take immediate and proactive measures to mitigate this threat.
Zscaler Zero Trust Exchange Coverage – Advanced Threat Protection, Zscaler Deception
How Zscaler Deception fights AI-driven threats
Recently, Anthropic published an analysis of the first AI-powered cyber espionage campaign which was allegedly led by a China-based state-sponsored group. The threat group utilized an infrastructure composed of about 80% to 90% AI-powered programs. Agentic AI was used for reconnaissance, exploit validation, credential harvesting, lateral movement, data analysis, and exfiltration. Human oversight was limited to escalation steps.
The table below highlights the key differences between a human and an AI-powered adversary.
My takeaway is that the methods reported by Anthropic were not entirely new; however, AI does help “super charge” simple scripts and steps that were once limited by human operation.
Regardless of whether an organization is facing a human or AI attacker, the most effective security strategy remains the same: implement a Zero Trust everywhere strategy with integrated Deception technology. When combined, Zero Trust and Deception technology create a strong defense, preventing lateral movement utilizing techniques such as:
- Decoy login pages for attractive targets
- Honey-token accounts that seem to have high privileges
- Decoy machines like databases and file shares
- Decoy files with passwords and decoy credentials
To learn more about how Zscaler’s deception technology can help organizations defend against AI (and human) foes, visit Anthropic AI-Orchestrated Attack: The Detection Shift CISOs Can’t Ignore.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access, Zscaler Private Access, Zscaler Deception
Zscaler threat discoveries
CVE-2025-12058 - Vulnerability in Keras Models Allowing Arbitrary File Access and SSRF
During our AI/ML security research, Zscaler discovered CVE-2025-12058, a vulnerability in Keras (version 3.11.3 and earlier) that exposes AI environments to file access and network exploitation risks. The flaw allows arbitrary file access and server-side request forgery (SSRF) during the loading of malicious .keras model files. The vulnerability introduces serious risks such as local file access (e.g., SSH keys, credentials), cloud credential theft (via metadata endpoint abuse), and supply chain attacks through poisoned pre-trained models.
How it works
The StringLookup and IndexLookup preprocessing layers enable file paths or URLs in their vocabulary parameter, and serialized models can exploit this by accessing local files or external network resources even with safe_mode=True enabled.
Recommendation
Zscaler recommends leveraging its AI Security Posture Management (AISPM) solution, which offers real-time detection of AI threats. AISPM scans ML models for suspicious file paths, network references, and embedded payloads to prevent malicious models from infiltrating enterprise environments.
Zscaler Zero Trust Exchange Coverage – Zscaler AI SPM, Zscaler AI Guard
CVE-2025-50165 - Critical Flaw in Windows Graphics Component
As part of our ongoing efforts to protect customers, the ThreatLabz team discovered and reported CVE-2025-50165 to Microsoft in May 2025. Subsequently, Microsoft patched the issue and published the CVE in August. The ThreatLabz team recently published a technical analysis blog providing additional insights on this critical remote code execution (RCE) vulnerability.
How it works
The attack chain involves creating a JPEG that triggers an attack flow when the user opens the file. ThreatLabz performed extensive research and developed a Proof-of-Concept (PoC) to demonstrate the exploit. Our analysis confirmed that attackers could use techniques such as heap spraying and Return-Oriented Programming (ROP) to control the instruction pointer and ultimately execute malicious payloads.
Recommendation
Microsoft released a patch on August 12, 2025. ThreatLabz recommends updating your system immediately with the patched version.
Zscaler Zero Trust Exchange Coverage – Advanced Threat Protection, Zscaler Private Access
Zscaler identifies and examines a Water Gamayun APT attack
The Zscaler Threat Hunting team has published a technical analysis of a multi-stage attack attributed to the Russia-aligned APT group, Water Gamayun. This campaign combined zero-day exploitation, social engineering tactics, and advanced obfuscation methods to deliver hidden PowerShell payloads and malware loaders, which enabled the attackers to infiltrate enterprise networks and steal sensitive data. The specific malware involved in this case remains unclear; however, Water Gamayun is known for using tools such as EncryptHub, SilentPrism, DarkWisp, and Rhadamanthys.
The attack began with Bing search results leading victims to a compromised website, which redirected them to a fake domain hosting the malicious payload. The group exploited the MSC EvilTwin vulnerability (CVE-2025-26633) and used encoded PowerShell scripts along with obfuscation techniques to evade detection. Victims were tricked into opening password-protected archives, which displayed decoy documents while secretly deploying malicious payloads designed to establish persistence and potentially install backdoors or data-stealing software.
Zscaler Zero Trust Exchange Coverage – Advanced Threat Protection, Zscaler Cloud Sandbox, Zscaler Deception
Threat updates
- DanaBot returns with version 669: After a six-month hiatus following Operation Endgame, DanaBot malware has resurfaced with version 669. DanaBot is using new infrastructure and targeting cryptocurrency-related data.
- TransferLoader: The TransferLoader malware has resurfaced with updated samples.
Recommended
