
CXO Monthly Roundup, September 2025: Cisco Firewall and VPN vulnerabilities, Shai-Hulud NPM worm emerges, APT37's Rust backdoor, SmokeLoader's additional variant, and COLDRIVER's latest campaign, and new discoveries from ThreatLabz
Oct 10, 2025
Highlights from the Zscaler ThreatLabz team's September 2025 research.
The CXO Monthly Roundup provides the latest Zscaler ThreatLabz research, alongside insights into other cyber-related subjects that matter to technology executives. This September roundup highlights Cisco Firewall and VPN vulnerabilities, the emergence of the Shai-Hulud NPM worm, APT37's use of a Rust backdoor, new SmokeLoader variants, COLDRIVER's latest campaign, and other key discoveries from ThreatLabz, including malware families like YiBackdoor and kkRAT.
Cisco Firewall and VPN Zero Day Attacks: CVE-2025-20333 and CVE-2025-20362
On September 25, 2025, Cisco issued a security advisory addressing three zero-day flaws (CVE-2025-20333, CVE-2025-20362, and CVE-2025-20363) impacting the VPN web server of Cisco Secure Firewall Adaptive Security Appliance (ASA) and Cisco Secure Firewall Threat Defense (FTD) software, exploited since May 2025 in a campaign linked to China-based UAT4356/Storm-1849. The vulnerabilities, targeting HTTP(S) services, involve URL path-normalization and heap buffer overflow issues, with two requiring no authentication. On another important note, Cybersecurity & Infrastructure Security Agency (CISA) instructed federal agencies to immediately verify and disconnect impacted devices from their networks.
I want to state that these flaws do not impact Zscaler’s environments, as we do not use Cisco ASA devices.
ThreatLabz has put together the following attack chain, depicting what the infection process might look like when a threat actor exploits these vulnerabilities.
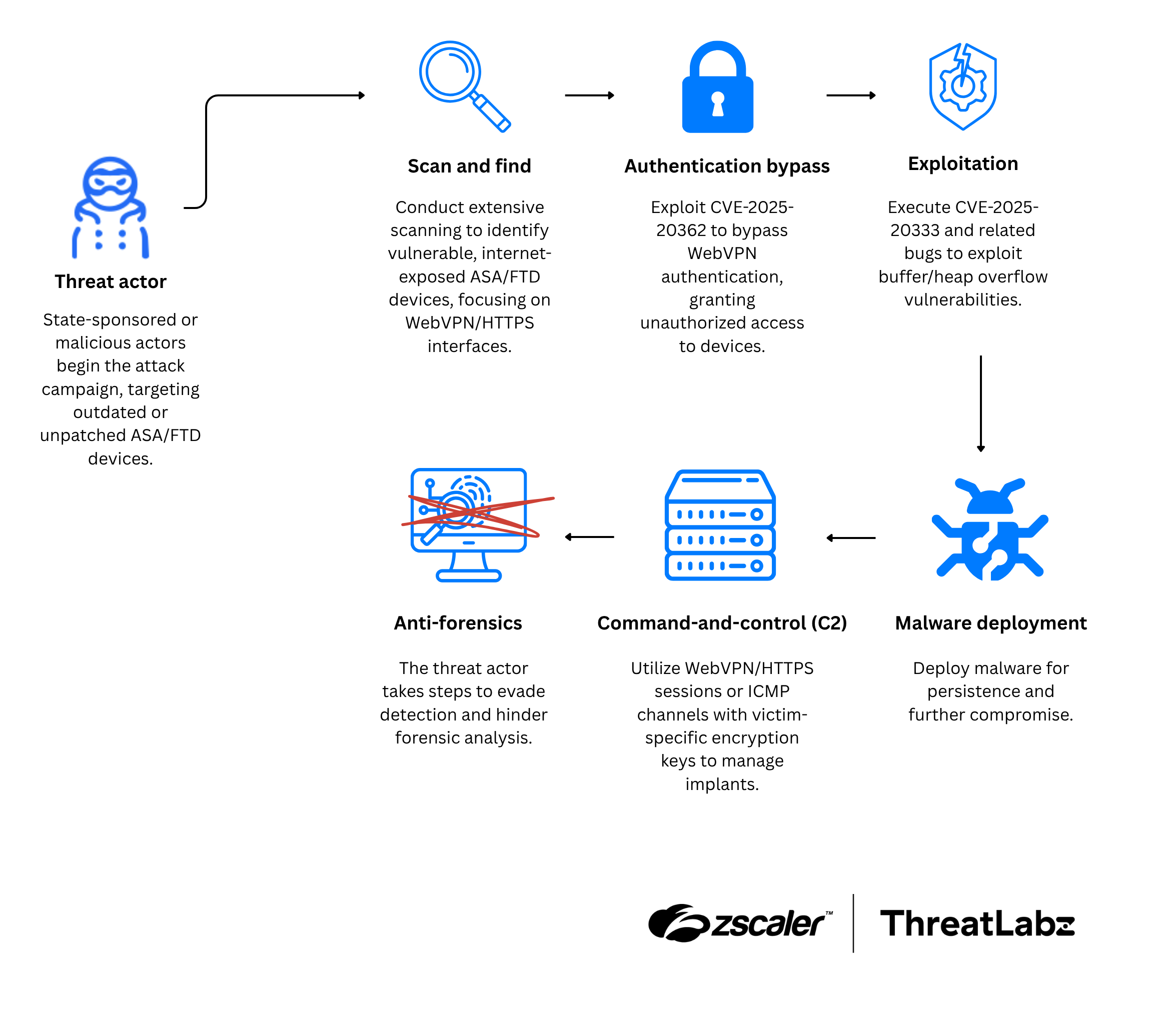
Figure 1: Diagram depicting the attack chain associated with Cisco ASA devices.
It is critical for organizations to prioritize implementing Zero Trust architecture, as we will continue to see large-scale exploitation attempts on these internet-exposed legacy devices (VPNs & Firewalls).
Mitigating Risks from the Shai-Hulud NPM Worm
On September 15, 2025, ReversingLabs researchers identified a self-replicating worm named “Shai-Hulud” within the npm open-source registry. This worm spreads autonomously by compromising maintainer accounts and injecting malicious code into public and private packages. Between September 14 and 18, over 200 npm packages and more than 500 versions were infected. Each compromised package further propagates the Shai-Hulud worm, creating a chain reaction throughout the npm ecosystem.
Affected Versions
Notable examples of compromised packages and their versions include:
- @ctrl/tinycolor - Versions 4.1.1 and 4.1.2
- @crowdstrike/* - Multiple versions of packages
For additional recommendations on safeguarding against threats like these, visit Mitigating Risks from the Shai-Hulud NPM Worm.
The supply chain attacks stemming from compromised open-source packages are even more critical in the world of AI coding agents, which are equally susceptible to downloading malicious packages and compromising the underlying systems without proper guardrails.
APT37 Targets Windows with Rust Backdoor and Python Loader
ThreatLabz published a technical analysis of recent campaigns where an advanced threat actor (APT) known as APT37 targeted South Korean individuals specializing in North Korea-related related fields, such as international affairs, political science, academia, and research. In this attack, APT37 utilizes a single command-and-control (C2) server to orchestrate all components of their malware arsenal, including a Rust-based backdoor that ThreatLabz dubbed Rustonotto (also known as CHILLYCHINO), a PowerShell-based malware known as Chinotto, and FadeStealer. These tools work collectively to establish persistence, execute commands, exfiltrate sensitive data, and enable covert surveillance through techniques like Process Doppelgänging and TxF-based code injection.
ThreatLabz reconstructed the APT37 infection chain that begins with an initial compromise via a Windows shortcut or a Windows help file, followed by Chinotto dropping FadeStealer through a sophisticated infection process. The attack chain is depicted in the figure below.
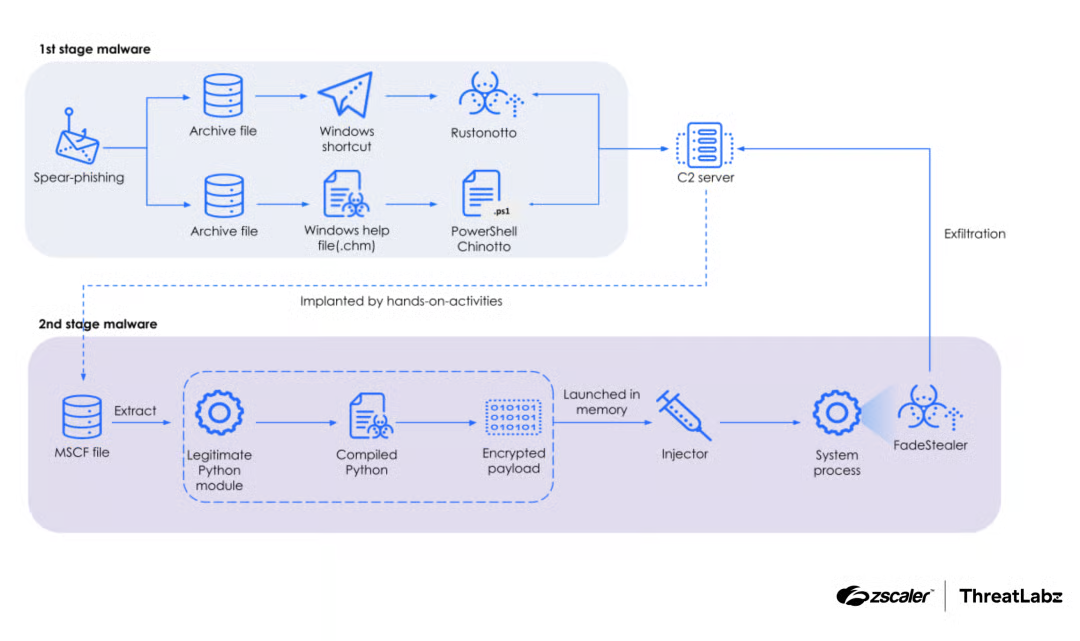
Figure 2: Full infection chain involving Chinotto, Rustonotto, and FadeStealer.
The technical analysis explores APT37's sophisticated tactics, including spear phishing, Compiled HTML Help (CHM) file delivery, and Transactional NTFS (TxF) for stealthy code injection. By incorporating new technologies alongside refined social engineering techniques, the group effectively exfiltrates sensitive information and conducts targeted surveillance on individuals of interest.
SmokeLoader Rises From the Ashes
In May 2024, Operation Endgame, an international collaboration between law enforcement and private industry (including Zscaler ThreatLabz), successfully dismantled numerous instances of SmokeLoader and remotely removed the malware from infected systems. These efforts significantly suppressed SmokeLoader activity following the takedown. Several months later, in July 2025, the author of SmokeLoader advertised a newer iteration of SmokeLoader on a cybercriminal forum. Shortly after, ThreatLabz discovered an additional variant featuring further updates.
The discovered SmokeLoader variants, version 2025 alpha and version 2025, introduce notable performance and detection evasion improvements. These updates address bugs affecting infected systems, optimize memory allocation, and implement advanced obfuscation techniques. Additionally, version 2025 includes significant modifications to its network protocol and detection checks, enhancing operational efficiency while maintaining backward compatibility with older versions.
The SmokeLoader bug fixes are detailed in the figure below.
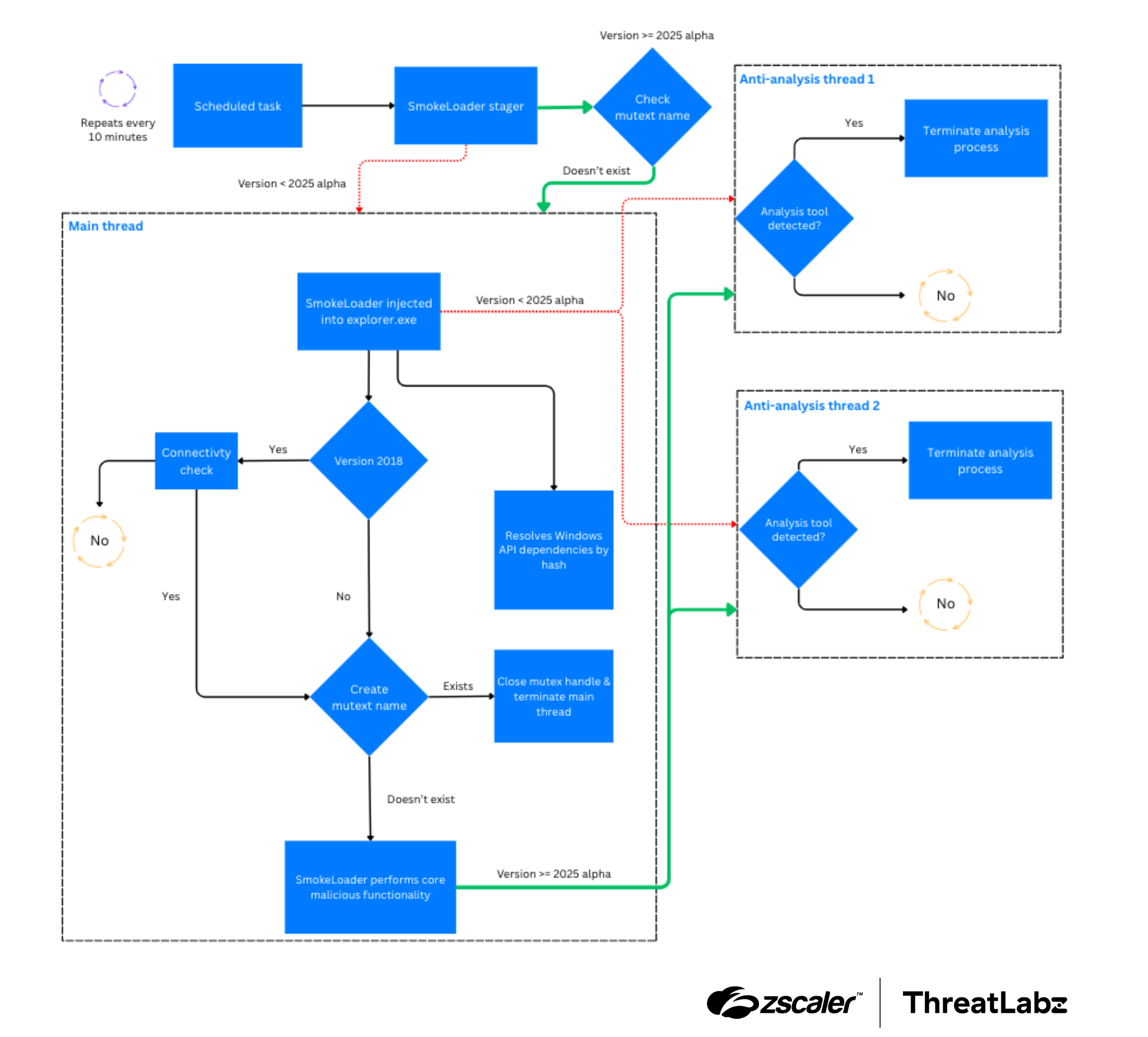
Figure 3: SmokeLoader execution process control flow comparison with versions before (red) and after (green) 2025 alpha.
COLDDRIVER APT Updates Arsenal with BAITSWITCH and SIMPLEFIX
ThreatLabz published a detailed analysis of a multi-stage ClickFix campaign likely linked to the Russia-based APT group COLDRIVER (also known as Star Blizzard, Callisto, or UNC4057). COLDRIVER, known for targeting NGOs, journalists, and human rights defenders in Russia and Western countries, extended their tactics with this campaign by introducing the ClickFix technique to deploy two new malware families: BAITSWITCH, a lightweight downloader, and SIMPLEFIX, a PowerShell-based backdoor. ThreatLabz observed COLDRIVER using server-side checks to selectively deliver malicious payloads based on user-agent and machine characteristics, emphasizing their sustained focus on civil society targets.
The figure below provides an overview of the multi-stage attack chain.
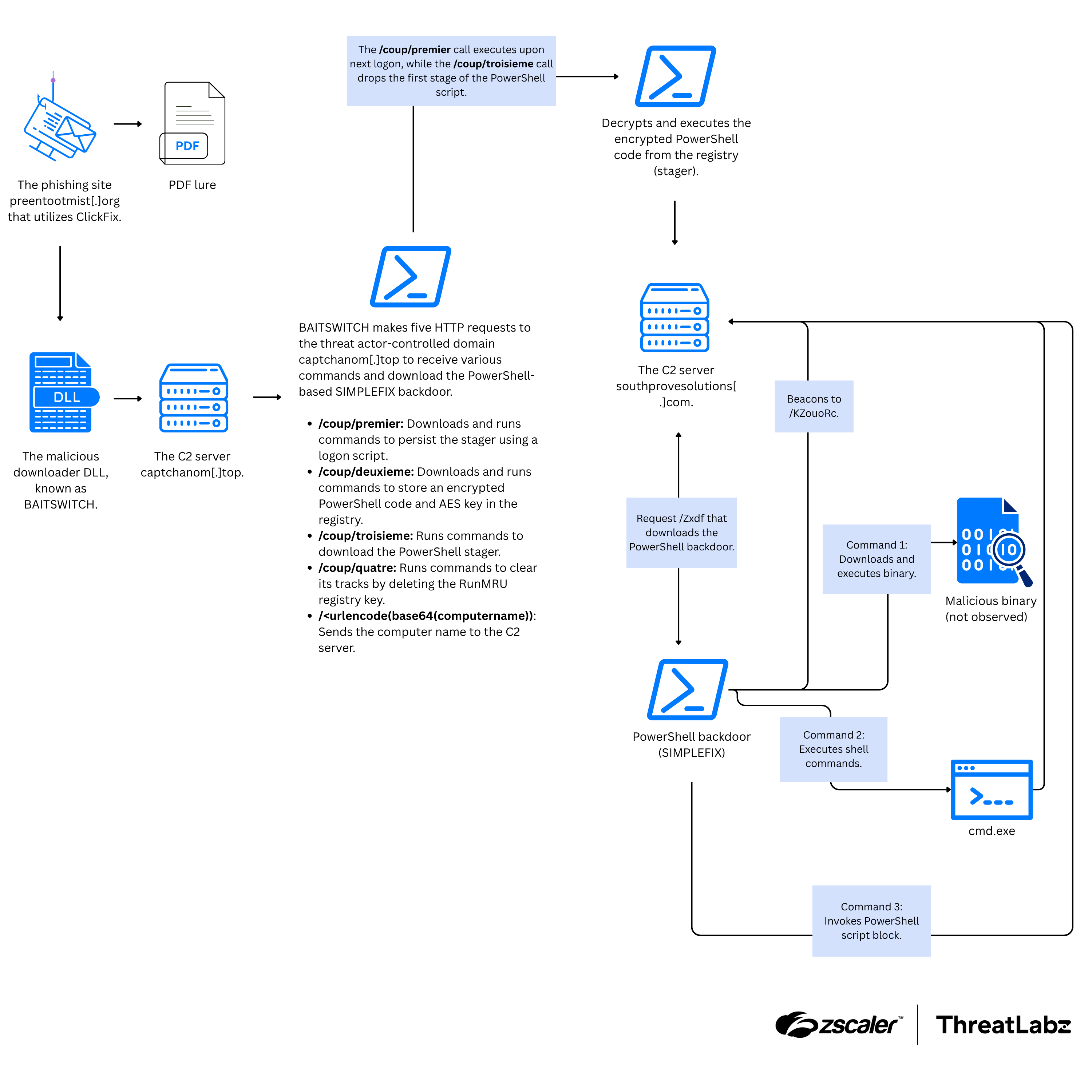
Figure 4: Multi-stage end-to-end ClickFix campaign attack chain leveraging BAITSWITCH to deliver SIMPLEFIX.
This campaign demonstrates that ClickFix-style attacks and lightweight malware remain effective tools for sophisticated threat actors. Technologies like Zscaler’s Advanced Threat Protection, Cloud Sandboxing, and Browser Isolation can help mitigate clipboard interactions and user actions on untrusted websites, providing an additional layer of defense against such attacks.
Original ThreatLabz Discoveries
The ThreatLabz research team announced the following discoveries in September:
- Zloader - Zloader 2.11.6.0 and 2.13.7.0 includes improvements to its DNS tunneling for C2 communications, support for WebSockets, and advanced anti-analysis methods.
- YiBackdoor malware family - With significant code overlaps with IcedID and Latrodectus, YiBackdoor’s capabilities include executing commands, collecting system information, capturing screenshots, and deploying plugins to expand functionality. The malware also employs techniques to evade sandbox detection and hinder analysis.
- saws and secmeasure PyPI packages and SilentSync - ThreatLabz researchers identified two malicious packages in the Python Package Index (PyPI) repository that distribute a Remote Access Trojan (RAT) we dubbed SilentSync. These packages employ typosquatting tactics and pose as legitimate government APIs associated with the Argentine government.
- kkRAT - A new malware campaign that targets Chinese-speaking users to deliver known RATs like ValleyRAT, and new RATs like kkRAT. kkRAT shares code similarities with Ghost RAT, a malware tool typically leveraged by China-based cybercriminals.
Recommended
