
EDITOR'S PICK
Dec 24, 2021
How to balance access to corporate resources with minimum user friction and maximum confidence in protecting your environment.
Designing user access for corporate applications is a trade-off between security and accessibility. This article explores balancing access to corporate resources with minimum user friction and maximum confidence in protecting your environment.
The Role of Zero Trust Network Access
Arguably, you can boil down the security of enterprise resources to the following three things:
- How careful employees and contractors are with their credentials
- How vulnerable applications and infrastructure are to attack
- How capable security teams are to detecting unauthorized access
By redesigning the way access is provided to corporate applications, you can reduce the risks around credential handling and infrastructure vulnerabilities, giving your information security team a better chance to defend the enterprise against attack. Implementing zero trust network access (ZTNA) is the optimal solution to eliminate infrastructure vulnerabilities because it brokers connections between authorized users and specific apps—no matter where they are.
A passwordless authentication environment makes credentials much more challenging to steal by reducing or eliminating the use of passwords. When combined with ZTNA, you create an invisible application ecosystem with zero attack surface that your users can access seamlessly and securely with little chance of credential theft.
Building a ZTNA
Building ZTNA reduces the enterprise's attack surface at a high level while continuously verifying systems and users entitled to use the systems.
Reducing the attack surface
A ZTNA service connected to an identity provider authenticates and authorizes requestors. Traffic between the user and the application is proxied—with no direct network access—and allowed only after successful authentication and authorization. There is no direct connection to the resource from the users or any other service or device.
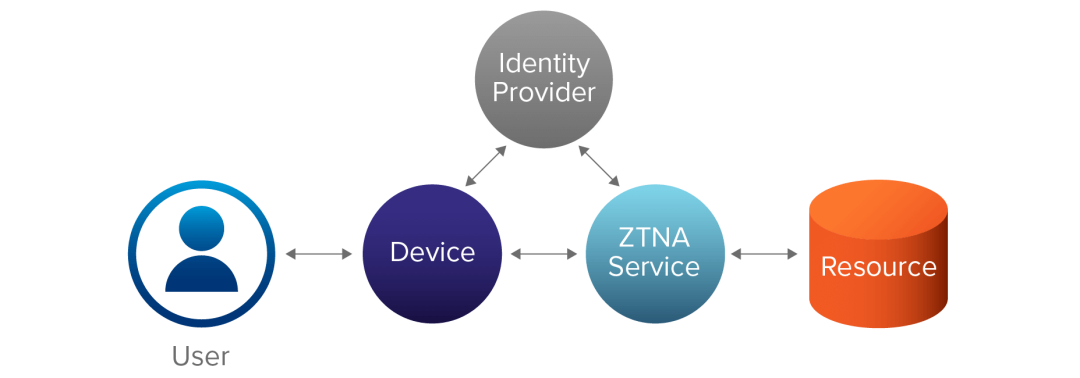
Continuous trust evaluation
Continuous trust evaluation is a key method to build trust in the ZTNA model. Continuous trust enforces an identity-based trust model so the system can analyze the context environment of access, identify the abnormal behavior of access requests, and apply policy to allow or block access on a real-time basis.
Contextual access
As each system is continuously verified, ZTNA can introduce contextual access. Contextual factors can include the location, such as the originating country or network; device type, such as corporate or personal; sensitivity of the data, public or confidential; or evidence of malware or tampering, which should trigger access restrictions.
Passwordless Authentication
Let's focus on the steps required to create a seamless application experience for the user while protecting their device with passwordless authentication.
Why Passwordless?
Many cybersecurity breaches occur through phishing attacks or malware stealing user credentials from a system. Passwordless in the context of this article is user-based authentication using either out-of-band methods or through a key or certificate that is bound to a device. A passwordless environment has no passwords that can be phished, and credentials are stored in a secure hardware module on managed devices or negotiated with a portable out-of-band device, making authentication tokens very hard to steal.
Multifactor versus passwordless authentication
Multifactor authentication (MFA) requires the user to provide two or more authentication methods to gain access. But user-based MFA by itself has limitations as it does not use context to ensure secure and appropriate access, like taking into account the device's security posture. Without this context, security teams have used short authentication session times to caution against stolen authentication tokens, creating friction in the user experience.
A seamless, passwordless environment with ZTNA is different. The user's device is the central authentication mechanism, and the user unlocks the device to gain access to applications. Though authentication sessions are still short, session renewals happen seamlessly and silently. ZTNA relies on the integrity of the user devices to perform the authentication, so manage the device with security controls to ensure that it is free of malware and not subject to any unauthorized use.
Users can also perform passwordless authentication without a managed device, using out-of-band (OOB) or one-time-password (OTP) authentication methods with a smartphone app or physical token. ZTNA might restrict some access in this case because of the reduced level of confidence with the access. For example, sensitive financial records might only be visible from a managed device. (This is an example of contextual access.) Even after authentication, sessions on unmanaged devices should time out after a limited period.
How many factors of authentication?
The number of authentication "factors" in a passwordless environment depends heavily on implementation decisions and the OOB devices' standards. NIST Special Publication 800-63B provides in-depth guidance on OOB and OTP devices and general implementation of digital identity services.
For example, you can replace old-fashioned, manual 2FA with seamless passwordless authentication that has two factors also: something you have (a managed device) and something you are (biometrics) or something you know (your pin). By adding specific OOB authentication requirements to a sensitive application, you suddenly have four factors of authentication.
Trade-offs
Increasing the convenience of access generally increases risk. Conversely, increasing security generally degrades the user experience. In a combined passwordless and ZTNA environment, you can enhance corporate resources' security and the user experience with appropriate protections and controls.
Protection targets
Ensuring the security of the environment requires multiple layers of protection, including:
- Physical protection: If an attacker gains access to an unlocked passwordless device, all bets are off. It's advisable to put controls in place to protect unattended machines if an attacker gains physical access. These controls can include pre-boot PINs, automatic device locks, and other policies that prevent or delay unauthorized use. Report stolen machines swiftly so their access can be disabled.
- Credential protection: Modern Microsoft Windows, Apple, and smartphones store user credentials in a secure hardware module. The device's operating system retrieves those credentials to access the application through the identity provider. A defense-in-depth strategy is essential to protect the device from misuse, keep it malware-free, and ensure that it remains trustworthy. Skimping on recommended controls when implementing ZTNA and passwordless environments will reduce security.
A passwordless application access architecture includes controls at seven different levels: the secure hardware module, device login controls, operating system controls, endpoint detection and response, network transport controls, application controls, and identity provider controls. These controls help secure user credentials and the environment.
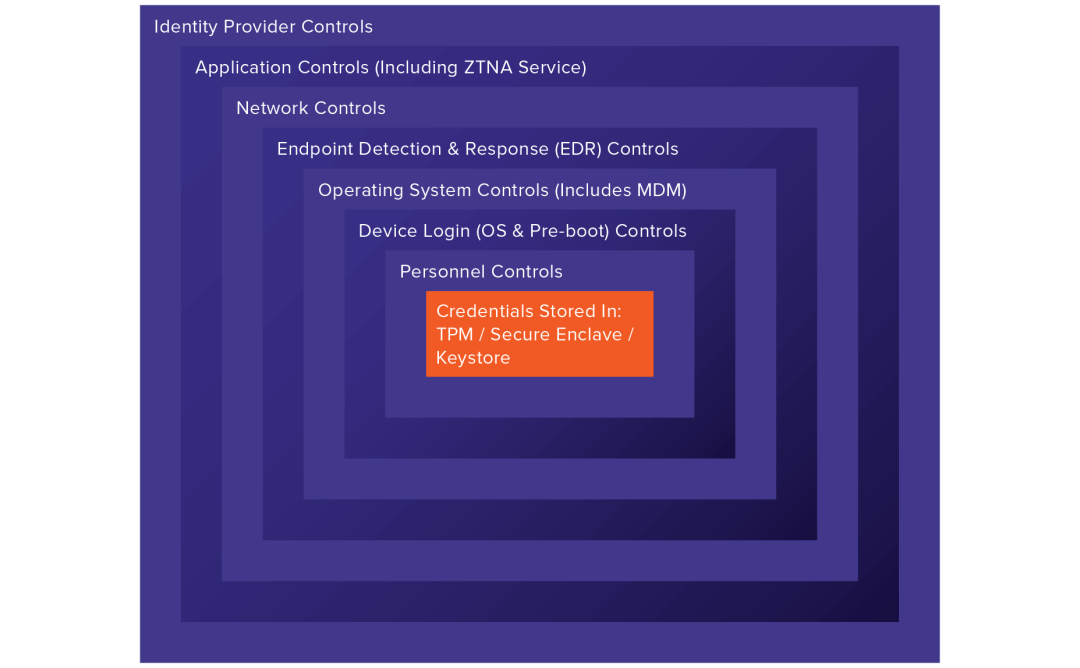
In conclusion, there are trade-offs between security and ease of use in a solution based on ZTNA; the key is an application access design for a frictionless yet secure user experience. In part two, I'll cover each security control needed in ZTNA to enable a balanced passwordless user experience.
What to read next
The passwordless future has arrived, here are your options
The importance of ERP in your zero trust strategy
It's time to revisit your BYOD strategy
Recommended
