
Oct 6, 2022
Element #4 of the Seven Elements of Highly Successful Zero Trust Architecture, assessing risk, is the first element to involve exercising control over content and access.
Editor’s note: Element #4 of the Seven Elements of Highly Successful Zero Trust Architecture, assessing risk, is the first element to involve exercising control over content and access.
In life, we’re all judged by the outcome of our last performance. The same goes for zero trust. The previous elements are only as good as the latest assessment. The solution must account for an enterprise’s tolerance for risk via a dynamic risk score.
Subsequent and ongoing risk assessments must be dynamically calculated from a set of signals to ensure the score is updated based on new developments. This risk then feeds into a decision engine to determine whether ongoing access should be granted.
True zero trust requires continuous evaluation of all values related to the authentication, inspection, and access determinations based on the destination service.
For example, identity verification must be continuously updated in the event the original authentication criteria are no longer met. Dynamic risk calculation is important for making risk-based access decisions throughout the life of a connection. A marked change in user/device posture or behavior can trigger an update on the access decision in near real-time based on updates to a risk score.
Technology and architecture considerations
Calculating risk dynamically requires varying inputs that cannot be consumed in a uniform manner. There must be mechanisms to regularly assess user/device profile values to confirm the status, change, updates, and ultimate risk of the initiating request.
Understanding user behavior is critical to distinguishing between risky and benign actions. This analysis learns patterns of normal behavior to then determine when behavior is anomalous. Analyzing these patterns and evaluating them against company policy leads to better access request determinations.
More simplistic methods of risk calculation focus on measuring rates of undesirable traffic or blocked access requests generated by a user.
Collection and collation of risk inputs also can’t be limited by an initiator’s location. While these methods give some indication of risk, they are neither truly dynamic nor based on a sufficiently broad set of input criteria. Additionally, calculating accurate risk scores isn’t workable as an add-on service.
Dynamic risk scoring must be a fundamental feature of a zero trust solution, able to scale with an enterprise’s ideas of acceptable risk. Values must be collected regardless of whether the initiator is connected at home, a coffee shop, in the office, or elsewhere. Zero trust solution providers must deliver global, highly-available, scalable, and network-agnostic solutions that offer consistent policy decisions and a seamless user experience while mitigating risk.

Just as behaviors vary among user identities, workloads must also be evaluated relative to their known and comparatively static activity; an SQL client should talk to an SQL server, but rarely if ever should it communicate with an unrecognized server.
Independent of the request initiator’s identity, the outcomes of these assessments are used to create a risk score, which is then sent to the application policy decision engine described in Element 7. It’s at this point where the decision of which action to take, based on the risk score calculated from user posture, device posture, and anomalous behavior is made. Customers must also decide on the frequency with which this determination must be made when risk scores are dynamically evaluated.
Third-party solutions can provide additional insight into user and workload risk assessments. Those garnered from EDR, SIEM, or SOAR services may add context for improved determinations.
Note: If the control assessment of Risk Score cannot be met, the access should default to a conditional block policy
Zero trust progress report
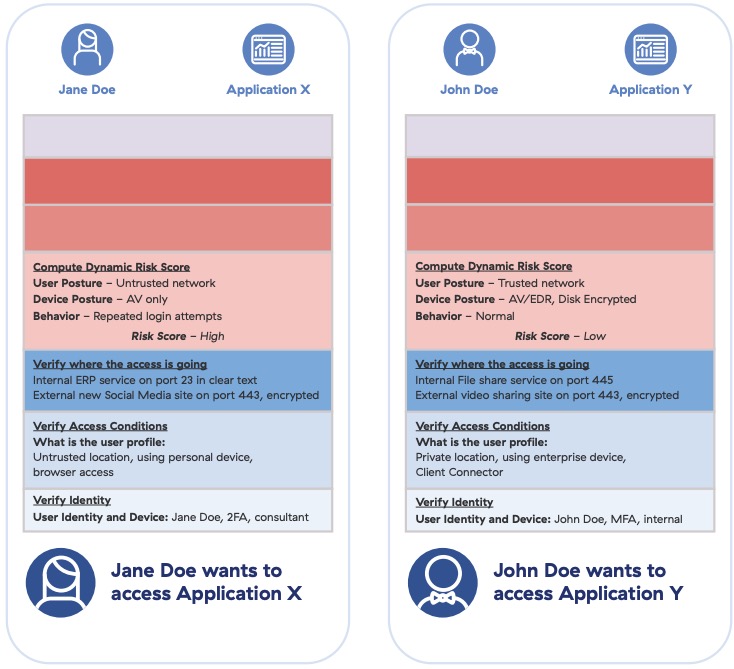
After a dynamic risk assessment, risk values are included with original identity outputs to round out the view of the requesting entities, John and Jane Doe. The zero trust process will consume this verified identity as part of its policy implementation.
Download the Seven Elements of Highly Successful Zero Trust Architecture eBook and stay tuned for more installments of our accompanying commentary.
Recommended

