
Oct 20, 2022
Element #6 of the Seven Elements of Highly Successful Zero Trust Architecture focuses on preventing the exfiltration of sensitive data.
Editor’s note: Element #6 of the Seven Elements of Highly Successful Zero Trust Architecture focuses on preventing the exfiltration of sensitive data.
The ability to inspect traffic destined for the internet, SaaS, or internal applications is important for identifying and preventing the loss of sensitive data.
As part of the Control phase, enterprises must consider what data leaves the organization. SSL/TLS inspection at scale ensures that attacks against an enterprise are stopped, and this same inspection can also be applied for data egress controls.
As outlined in Element 5, over 80% percent of web traffic is encrypted, including common tools used by both enterprise and private users such as the file-sharing services Dropbox and Google Drive, or collaboration tools like Microsoft 365 and Google Chat. If this traffic is completely encrypted, enterprises are powerless to understand what’s being sent to these environments. This means businesses are unable to protect against both inbound malicious payloads and illicitly outbound intellectual property.
However, concerns are not limited solely to users. As the 2020 SolarWinds breach showed, enterprises not monitoring server data sent outbound to the open internet are unlikely to be able to stop the exfiltration of sensitive data, e.g., via a supply chain attack.
It is therefore critical that once SSL/TLS interception is enabled, an enterprise deploys the necessary inline controls to protect against information and intellectual property leakage. Traffic inspection allows enterprises to identify not only what intellectual property is being accidentally shared but also enables greater identification and protection against ransomware attacks.
Zscaler’s 2022 Ransomware Report documented a substantial increase in attackers now exfiltrating data as part of double extortion attacks. Attackers are now asking for ransoms not only to decrypt enterprise systems but are also increasingly stealing intellectual property only to ransom it back to the same company.
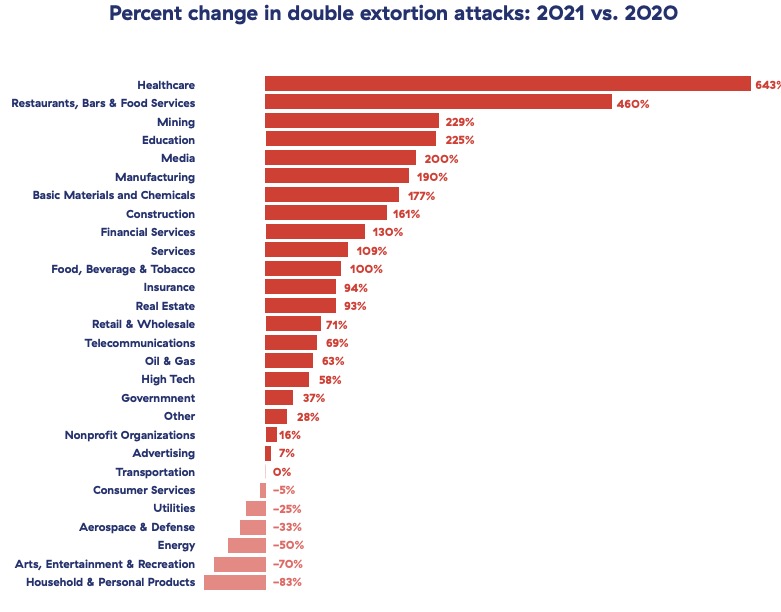
Again we arrive at the problem of determining the correct balance between inspection and privacy. This review must be understood in terms of enterprise risk.
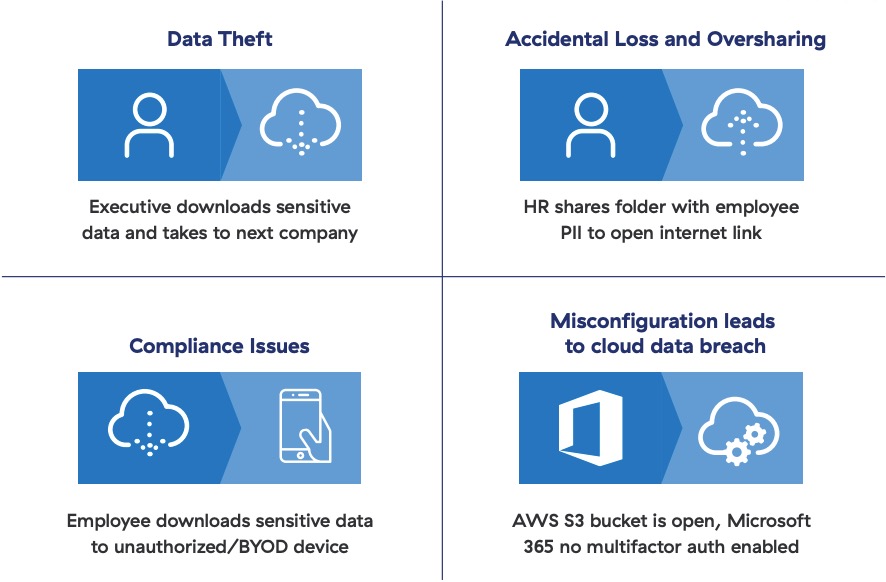
Technology and architecture considerations
Widespread adoption of cloud applications means organizations’ sensitive data is widely distributed. The top two enterprise data exfiltration channels are cloud desktop and personal email applications. Adequate protection technologies should deliver complete contextual visibility and enforcement capabilities when rogue users upload sensitive data to personal cloud desktops. They should also stop data exfiltration on personal and unsanctioned webmail services like Gmail and Outlook.
Protection starts with blocking access to unauthorized users. This is the simplest protection policy. Consider two examples:
- For users and devices - Implementing controls against destinations that contradict corporate policy, such as webmail services.
- For IoT/OT devices and workloads - Restricting workload or OT services to communications with relevant services such as patching solutions, or preventing a workload’s access to unnecessary services such as YouTube.
The protection outlined in Element 3 must be able to seamlessly create sets of common apps that relate to a singular service–for example, Microsoft 365 is a set of separate applications that can be addressed as a group or individually. These protection solutions must also be able to differentiate between personal and professional applications and cloud services and apply sets of rule definitions appropriately. As an example, a CEO should be able to upload financial reports to a corporate SharePoint file store, but unable to upload the same files to a personal file-sharing service.
Enterprise resource protection must also include the ability to view resources that may be out-of-band, which entails scanning the APIs of SaaS providers to protect data at rest, or inline, which requires the scanning of data in motion.
Inspection and subsequent protection policy application must happen at scale, wherever the user is located. It cannot be centralized in a data center or destination cloud if it’s to pass through at scale.
Upon decryption, protection policies must deliver appropriate controls based on the identity and app access permissions verified in Elements 1, 2, and 4. This protection policy includes two key areas, data in motion and data at rest.
- Data in motion (inline controls) – Information passing from the initiator to a destination application must be reviewed to ensure it does not contain sensitive corporate information. With inline inspection, enterprises can prevent data from being uploaded to unsanctioned apps, being downloaded to unauthorized devices, and malicious content from being downloaded or uploaded.
- Data at rest (out-of-band controls, independent of SSL/TLS inspection) – Data stored in cloud services must also be assessed to mitigate corporate information leakage. This should be queried via APIs to identify. Cloud access security broker (CASB) solutions offer these out-of-band controls for granular access based on a rich set of cloud app definitions, file type controls, and risk attributes.
Note: Any file store that leverages file-level encryption like AES would be visible to an out-of-band API as an encrypted file only. There is no visibility within the contents of the file.
Both of these functions must rely on protection solutions including:
- File type control - Define acceptable files for enterprise access
- Cloud app control - Determine which cloud apps are allowed and which are not
- Machine learning-enabled DLP - Improve the accuracy of sensitive data departure detection
- Exact data match - Index structured data (for example, your specific credit cards versus a 16-digit number that algorithmically could be a credit card, etc.) to help reduce false positives
- Optical character recognition - Block sensitive data found in images or screenshots
- Indexed document matching - Protect high-value documents containing sensitive information like intellectual property
These protection solutions empower enterprises to break an attacker’s kill chain, as outlined in the white paper Transforming Cybersecurity Response with Zscaler using the MITRE ATT&CK Framework.
Zero trust progress report
In assessing what information should be protected for each session, the control section identifies anything that may be unnecessarily exposed, then exercises the appropriate controls.
Download the Seven Elements of Highly Successful Zero Trust Architecture eBook and stay tuned for more installments of our accompanying commentary.
Recommended

