
CISO Monthly Roundup, May 2024: Operation Endgame, Anatsa malware, HijackLoader, and the Zscaler ThreatLabz 2024 VPN Risk Report
Jun 7, 2024
ThreatLabz research on Operation Endgame, Anatsa malware, and HijackLoader. The Zscaler ThreatLabz 2024 VPN Risk Report. Zenith Live 24.
The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on cyber-related subjects. Over the past month ThreatLabz assisted with Operation Endgame, analyzed an Anatsa campaign, examined HijackLoader updates, and released a VPN risk report.
Operation Endgame extinguishes Smoke
Smoke (a.k.a. SmokeLoader, Dofoil) is a malware that has been plaguing organizations since 2011. Threat actors typically use Smoke to deliver trojans, information stealers, and other second-stage malware payloads. Smoke also has deployable plugins that facilitate crypto-mining, credential harvesting, and web jacking. It can be bought as a crimeware kit, which has led to its popularity and longevity. Zscaler ThreatLabz technical analysis of Smoke supported an international law enforcement action called Operation Endgame.

Operation Endgame, the largest operation against botnets in history, dismantled Smoke’s infrastructure. In many cases, authorities were able to remotely uninstall Smoke from infected systems. While it is likely that Smoke will reappear in the future, this law enforcement operation will have a serious impact on the threat ecosystem. Zscaler looks forward to continuing our cybersecurity efforts with industry partners, regional CERTs, and law enforcement agencies.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Anatsa, analysis of an Android banking malware
ThreatLabz noticed an increase in instances of Anatsa (a.k.a. TeaBot) malware appearing in the Google Play Store. This malware is employing dropper applications (PDF readers, QR code scanners, etc) to trick users into installing its payload. Anatsa is a banking trojan that, once installed, will exfiltrate credentials and information from global financial applications. It does this by using overlay and accessibility techniques that allow it to discreetly intercept data.
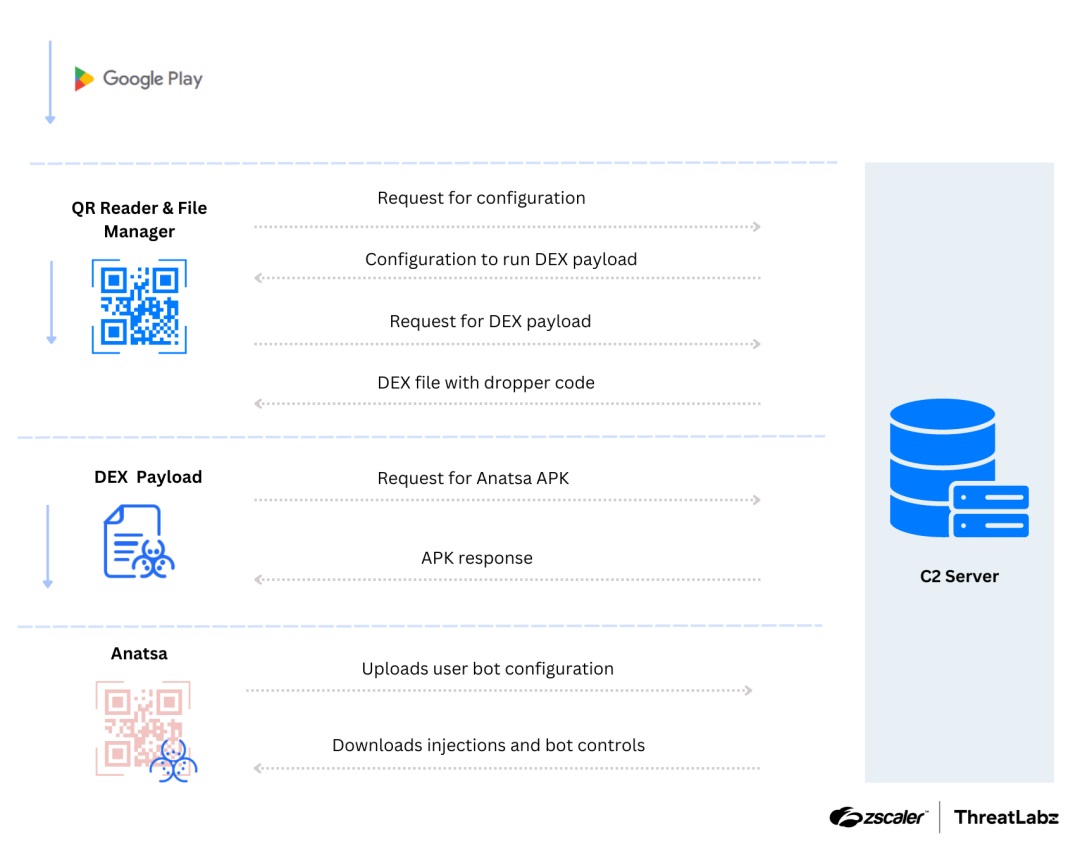
Once installed by an unsuspecting user, Anatsa contacts its C2 infrastructure to download the next stage payload and a configuration file. In one example, we observed the malware downloading a DEX file for the next stage payload and using reflection to invoke its code. Anatsa also analyzes the environment it is operating in and its host device. Once it determines it is in a vulnerable environment, the malware downloads a third and final payload from its C2 servers. Upon execution, Anatsa performs anti-analysis techniques (APK injection), payload decryption, device registration, and downloads a list of applications to search for on the host machine.
Read our full analysis of Anatsa
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
New modules for HijackLoader
HijackLoader is a modular malware loader first observed in the wild in 2023. It uses a variety of modules to perform code injection and payload execution. Its uncommon modular capabilities were explored in a previous ThreatLabz blog. Recently, we observed an updated version of HijackLoader that uses advanced evasion techniques. These included modules that add an exclusion for Windows Defender Antivirus, bypass User Account Control (UAC), and evade inline API hooking. We also observed Hijackloader using a PNG image to load the second stage of its attack.
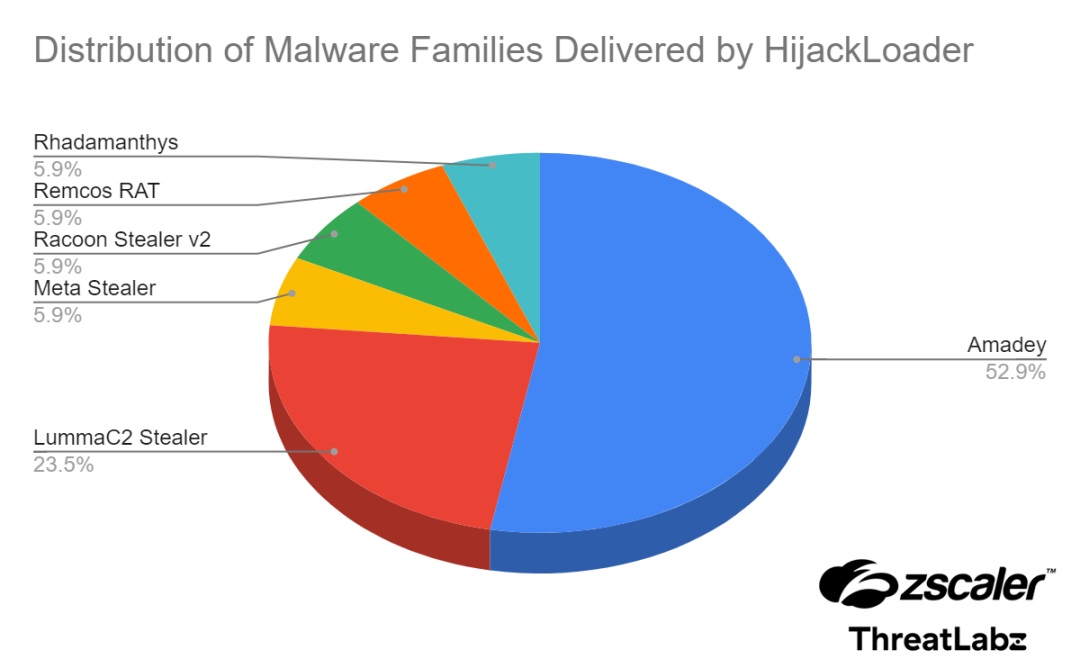
HijackLoader decrypts and decompresses its modules during the first stage of its attack. It establishes an internet connection and performs API resolutions looking for blocklisted processes on the system. It also downloads a PNG file containing multiple encrypted blobs. These blobs are decrypted to provide the data and modules required to load the second stage of the attack. The second stage of the attack focuses on anti-analysis, obfuscation, process hollowing, and executing x64 direct syscalls. During this stage HijackLoader will deploy one of multiple malware families.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Zscaler ThreatLabz 2024 VPN Risk Report
There have been a number of high-profile VPN cybersecurity vulnerabilities discovered and exploited over the past year. This is particularly concerning given the widespread adoption of VPN throughout the private and public sector. Notable examples of serious VPN vulnerabilities include:
- CVE-2023-46805 - Ivanti authentication bypass
- CVE-2024-21887 - Ivanti Connect Secure command injection
- CVE-2024-21893 - Ivanti server-side request forgery
- CVE-2024-3400 - Palo Alto GlobalProtect arbitrary file creation
The main problem with VPN technology is that this legacy technology grants overly broad network access. Once adversaries compromise a VPN connection they can move laterally through the environment causing great damage. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) at one point was directing federal agencies to disconnect affected devices in response to some of these recently discovered VPN vulnerabilities. This directive echoes Executive Order 14028, where the US Government mandated agencies to move away from VPNs and toward zero trust security.
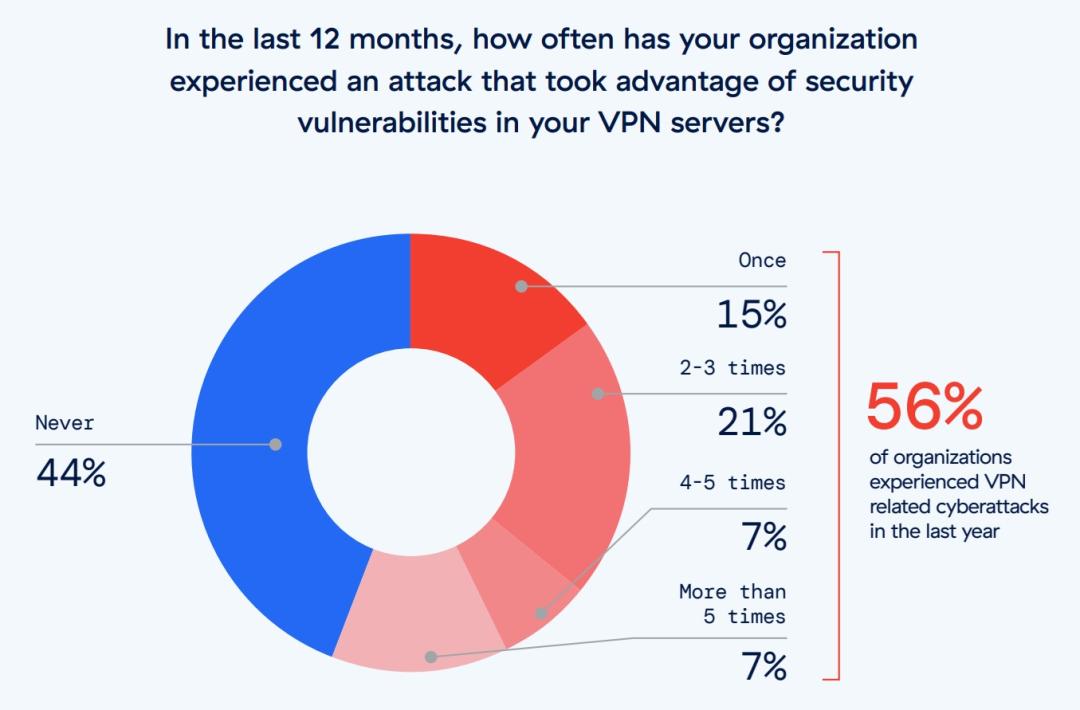
This report is based on the results of a comprehensive online survey of 647 IT and cybersecurity professionals from global organizations, conducted in April 2024, to identify the latest enterprise adoption trends, challenges, gaps, and solution preferences related to VPN risk.
By taking an in-depth look at the state of current enterprises and their exposure to VPN-related risks, we discovered some troubling statistics. For example, 56% of organizations suffered one or more VPN-related attacks in the past year, an 11% increase over the previous year. Threat actors who successfully breach VPN employ lateral movement in 53% of cases, broadening their impact on the environment. An overwhelming majority of the security professionals we surveyed (91%) are concerned about the risks VPN poses to their environment.
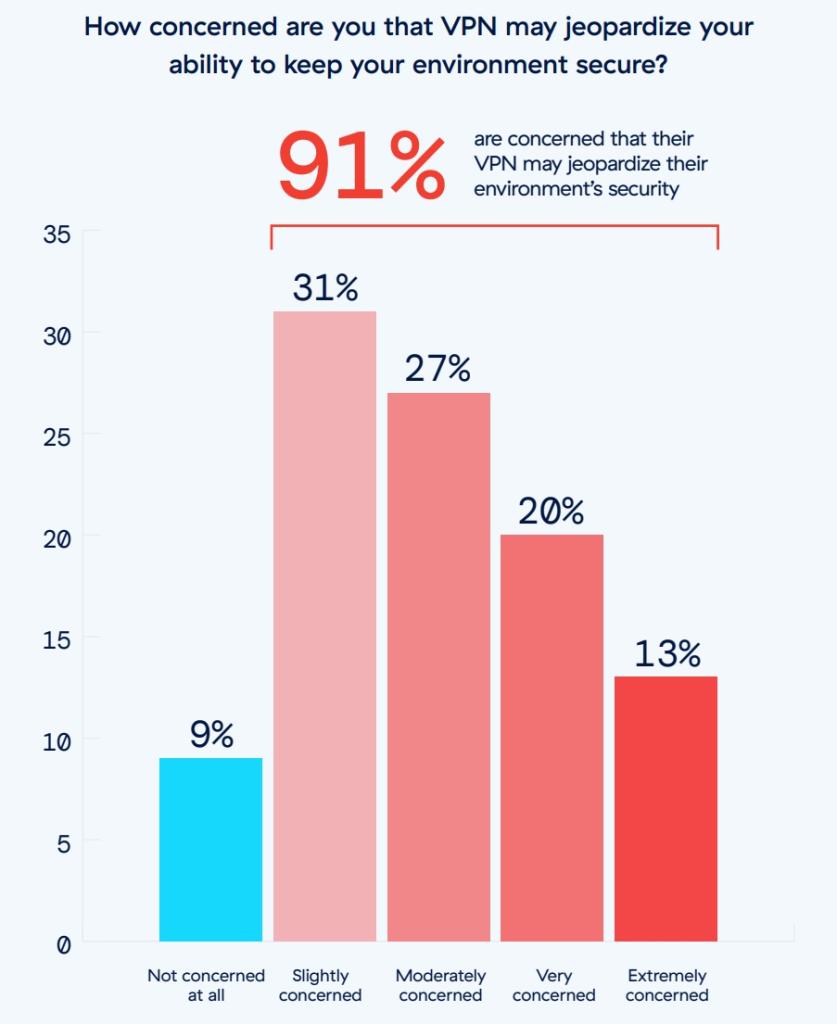
Our 2024 VPN Risk Report examines major security concerns, management challenges, user issues, third-party risks, and attack vectors. It also covers zero trust solutions which can effectively replace the role of VPNs while increasing your organization’s security posture.
Read the full 2024 VPN Risk Report
Zscaler Zero Trust Exchange Coverage - Replace inbound VPN with Zero Trust Architecture based solution like Zscaler Private Access.
Zenith Live 2024 in Las Vegas
Zscaler’s premier conference, Zenith Live, is happening on June 10-13 at the Bellagio Hotel in Las Vegas this year. Every year Zscaler brings together industry luminaries, executives, and technical professionals to discuss the latest developments in cybersecurity. Zenith Live features insightful keynotes, breakout sessions, hands-on training, and professional networking opportunities. This year, investigative reporter and cybersecurity journalist Brian Krebs will be giving a keynote about Unveiling the Secrets of Cybercriminals.

For those interested in attending my keynote, I will be speaking about Harnessing Zero Trust and AI to Outpace Cyberthreats on June 13 at 9:15 AM. There will also be presentations on zero trust and AI, comprehensive data protection, AI for risk management, cyberthreat protection, digital experience innovations, and more. For those in the EMEA region, Zenith Live '24 will happen on June 17-20 at The Hague, Netherlands, in the World Forum Convention Centre.
Zenith Live is a great opportunity for technical professionals and business leaders to exchange ideas, discover new insights, and share experiences. I hope to see you there.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
Settle your risk score with AI and your data fabric
Understanding board oversight of cybersecurity: Key findings from recent research
Analyzing social media exploitation at RSAC with CSO Deepen Desai
Recommended
