
TOP STORY
CXO Monthly Roundup, April 2025: New Threatlabz reports, HijackLoader, Mustang Panda, and Langflow
May 14, 2025
Highlights from the Zscaler ThreatLabz team's April 2025 research.
The CXO Monthly Roundup (formerly the CISO Monthly Roundup) provides the latest threat research from the ThreatLabz team, along with insights on other cyber-related subjects that matter to technology executives. In April, ThreatLabz released two much-anticipated reports, one covering phishing and the other, VPN risk. The team published the inner workings of Mustang Panda, analyzed HijackLoader, and examined a critical remote code execution (RCE) vulnerability in Langflow, an open-source platform for composing AI-driven workflows.
Zscaler ThreatLabz 2025 Phishing Report
The Zscaler ThreatLabz 2025 Phishing Report dives into the latest phishing trends, including top phishing targets, real-world examples of AI-driven phishing attacks, and actionable best practices to defend against the next wave of AI-powered phishing threats. The ThreatLabz research team analyzed over 2 billion blocked phishing transactions captured across the Zscaler Zero Trust Exchange™ cloud security platform from January 2024 to December 2024.
Key findings on phishing attacks include:
- Phishing is down but is more targeted: Although global phishing volume dropped 20% in 2024, attackers are shifting strategies, focusing on high-impact campaigns targeting high-value targets to maximize their success rates.
- United States phishing declines but remains #1: The US remains a top target even though phishing in the US dropped 31.8% as a result of stronger email authentication protocols like DMARC and Google’s sender verification, which blocked 265 billion unauthenticated emails.
- Manufacturing is the most targeted industry: The manufacturing sector continues to be the most targeted industry despite large increases in other industries.
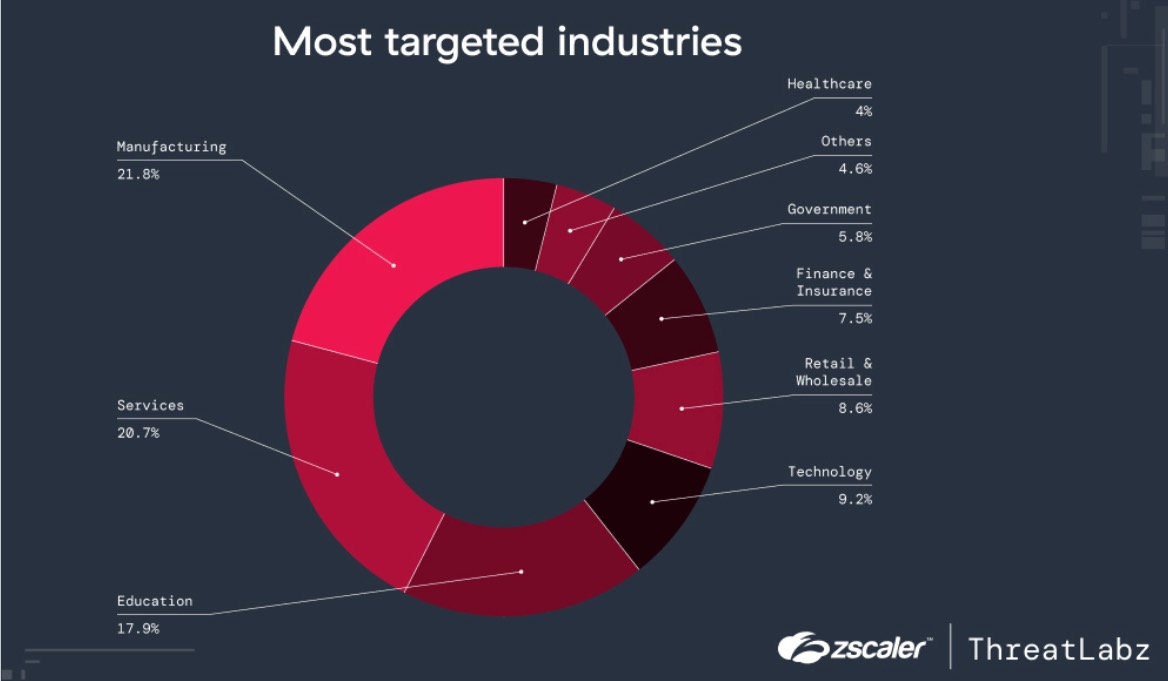
Figure 1: A graph showing the most targeted industries.
For more valuable insights, download your copy of the Zscaler ThreatLabz 2025 Phishing Report.
How Zscaler can protect your organization
Zscaler’s advanced phishing prevention combines inline AI-driven detection and features like browser isolation to eliminate risks from malicious phishing pages. Built on a Zero Trust Exchange framework, Zscaler neutralizes threats across the attack lifecycle, preventing initial compromise, blocking lateral movement, mitigating insider threats, and safeguarding data. By implementing Zscaler’s cutting-edge solutions and following security best practices, organizations can strengthen their defenses against phishing attacks and elevate their resilience into 2025 and beyond.
Zscaler ThreatLabz 2025 VPN Risk Report: The End of VPNs in a Zero Trust World
The Zscaler ThreatLabz 2025 VPN Risk Report with Cybersecurity Insiders surveyed 600+ IT and security professionals to explore the growing challenges of VPNs. It reveals a clear shift: 65% of organizations plan to replace VPNs within the year, and 96% favor a zero trust approach, with 81% actively implementing zero trust within 12 months.
As AI-driven threats evolve, attackers exploit internet-exposed VPNs with ease, leveraging automation to identify vulnerabilities and scan public IPs for weaknesses. This reality underscores the inherent risk: if your VPN is accessible, it’s vulnerable.
The report highlights how enterprises are addressing these challenges by adopting zero trust strategies to secure hybrid workforces and private applications. For the full findings and recommendations, download the Zscaler ThreatLabz 2025 VPN Risk Report today.
One key finding includes the rise of VPN CVEs from 2020-2025 represented below.
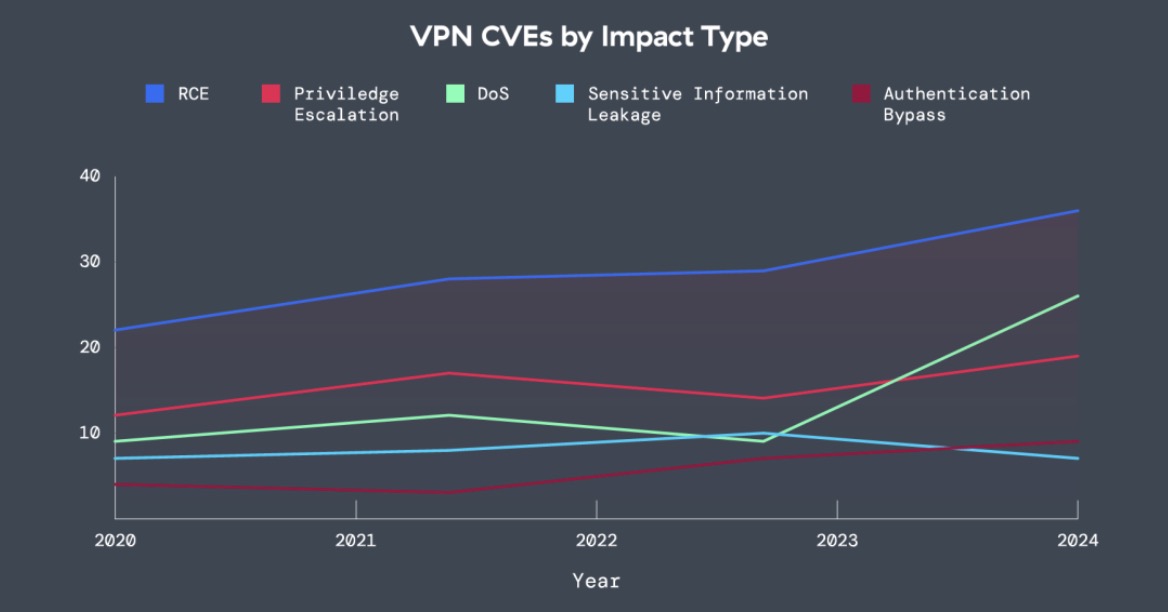
Figure 2: The impact type of VPN CVEs from 2020-2024, covering remote code execution (RCE), privilege escalation, DoS, sensitive information leakage, and authentication bypass.
Over the sample period, VPN CVEs grew by 82.5% (note that early 2025 data has been removed for this portion of the analysis). In the past year, roughly 60% of vulnerabilities were assigned a high or critical CVSS score. Moreover, ThreatLabz found that vulnerabilities enabling remote code execution (RCE) were the most prevalent kind, in terms of the impact or capabilities they can grant to attackers.
Mustang Panda
The team discovered new malicious activity linked to the China-sponsored espionage group Mustang Panda. Our research led us to multiple discoveries:
- A new tool we named StarProxy
- New ToneShell variants
- Two new keyloggers we named PAKLOG and CorKLOG
- A kernel-mode driver we named SplatCloak
In Part 1 of our Mustang Panda series, we explore StarProxy, a lateral movement and traffic proxying tool that establishes encrypted communication channels with command-and-control (C2) servers through malicious DLL sideloading. Packed inside RAR archives, StarProxy enables Mustang Panda to relay attacker traffic between compromised devices using custom XOR-based encryption and FakeTLS headers. This tool’s functionality includes TCP socket creation, two-way communication with target devices, and support for multiple protocols. This suggests threat actors use StarProxy as a post-compromise tool.
New ToneShell variants show updated functionality in areas such as seed generation for encryption keys, GUID file creation for client identification, and FakeTLS C2 communication protocols. These changes include varying methods of deriving GUIDs and rolling XOR encryption keys. FakeTLS headers are being altered to mimic TLSv1.3 traffic in newer versions, likely to evade network-level detection tools dependent on pattern recognition. As expected, the backdoors allow Mustang Panda to execute commands, transfer files, create reverse shells, and inject DLLs into victim processes. By leveraging DLL sideloading using signed binaries, ToneShell ensures stealth in its operations.
In Part 2 of our Mustang Panda series, we explain how Mustang Panda deploys two keyloggers, PAKLOG and CorKLOG, to monitor keystrokes and clipboard activity. PAKLOG obfuscates data locally, while CorKLOG adds encryption using RC4 and achieves persistence through services or scheduled tasks. Both exploit DLL sideloading with signed binaries to evade detection. SplatCloak, a kernel-mode driver we also discovered, disables EDR routines for Windows Defender and Kaspersky by targeting process, thread, and image creation notifications. Delivered via a dropper tool, it uses advanced obfuscation to evade analysis and removes traces post-installation.
These tools share technical overlaps with Mustang Panda’s prior activity, such as DLL sideloading and RC4 encryption, and align with Mustang Panda’s historic targeting of entities in Myanmar and NGOs, reinforcing attribution.
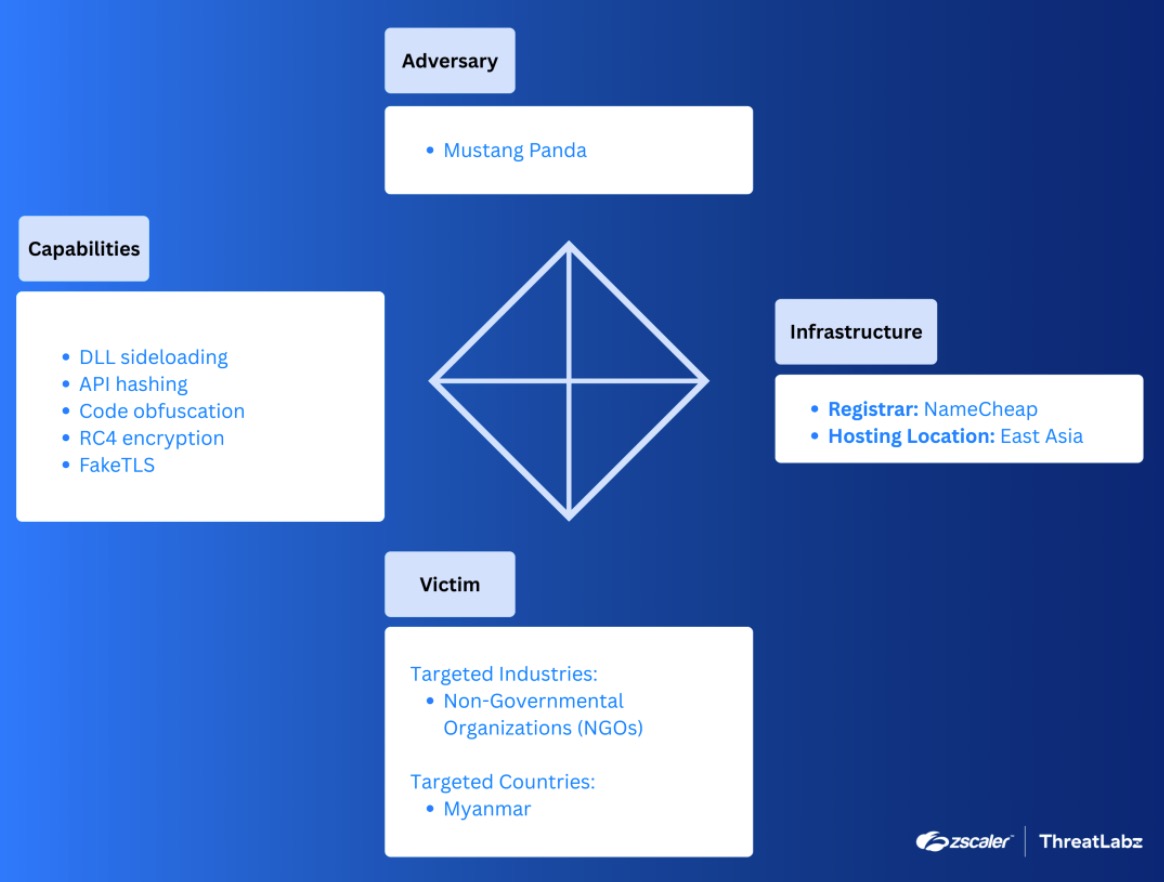
Figure 3: Diamond model highlighting TTP overlap with past Mustang Panda activity.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection), Zscaler Private Access, Deception
HijackLoader
Zscaler ThreatLabz has published a new technical analysis on HijackLoader, a modular malware loader first discovered in 2023. Building on previous analyses that explored its architecture and modules for code execution and injection, this latest research delves into recent updates. The highlighted features include call stack spoofing, anti-virtual machine detection, and persistence mechanisms using scheduled tasks.
One notable addition is call stack spoofing, which is a method to manipulate stack frames by replacing legitimate return addresses with forged ones. By navigating the stack through the base pointer register (EBP) and patching return addresses with randomized values from legitimate DLLs, HijackLoader conceals the origin of its API and system calls. This tactic is used extensively across various modules, such as modCreateProcess and modTask. Call stack spoofing is complemented by Heaven’s Gate, a technique that facilitates easy transitions between 32-bit and 64-bit code execution to facilitate direct system calls while bypassing user-mode hooks.
Another significant enhancement is HijackLoader’s anti-virtual machine detection module, known as ANTIVM. By exploiting common virtualization identification techniques, like hypervisor detection and physical memory analysis, HijackLoader identifies sandbox environments used for malware analysis and exits if conditions are met.
To learn more about HijackLoader’s other new features, visit Analyzing New HijackLoader Evasion Tactics.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection, Advanced Cloud Firewall).
Critical Vulnerability In The Wild: CVE-2025-3248 Remote Code Execution Vulnerability in Langflow
CVE-2025-3248 is a critical remote code execution (RCE) vulnerability in Langflow, an open-source platform for composing AI-driven workflows. The issue lies in the /api/v1/validate/code endpoint, which improperly uses Python’s exec()function on user-supplied code without authentication or sandboxing. Attackers can exploit this flaw to execute arbitrary commands on the server, enabling actions such as writing files, executing system commands, or deploying web shells.
- Severity: Assigned a CVSS score of 9.8 (critical).
- Affected Versions: All versions of Langflow prior to 1.3.0.
- Recommendations:
- Immediately upgrade Langflow to version 1.3.0 or later, where authentication is required for the vulnerable endpoint.
- Use a Zero Trust Network Access (ZTNA) solution, such as Zscaler Private Access™, to limit exposure.
- Use secure input validation and avoid exec() with untrusted code. Add sandboxing mechanisms if custom validation is required.
- Set up detection mechanisms to flag anomalous requests to validation endpoints and unexpected server connections.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its more than 9,000 customers, securing over 500 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
Recommended
