Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Latest Mustang Panda Arsenal: ToneShell and StarProxy | P1
Introduction
The Zscaler ThreatLabz team discovered new activity associated with Mustang Panda, originating from two machines from a targeted organization in Myanmar. This research led to the discovery of new ToneShell variants and several previously undocumented tools. Mustang Panda, a China-sponsored espionage group, traditionally targets government-related entities, military entities, minority groups, and non-governmental organizations (NGOs) primarily in countries located in East Asia, but they have also been known to target entities in Europe.
This blog post is the first in a two-part series that covers new variants of ToneShell and a new tool that we have named StarProxy, both found on Mustang Panda’s staging server. The second part of the blog explores two keyloggers and an EDR evasion driver, also hosted on the same staging server.
Key Takeaways
- ToneShell, a backdoor used by Mustang Panda, has been updated with changes to its FakeTLS command-and-control (C2) communication protocol as well as to the methods for creating and storing client identifiers.
- ThreatLabz discovered a new lateral movement tool used by Mustang Panda that we have named StarProxy, which leverages the FakeTLS protocol to proxy traffic and facilitate attacker communications.
- Mustang Panda remains active in targeting organizations and individuals in Myanmar.
- Mustang Panda employs DLL sideloading techniques, typically bundling malicious tools inside RAR archives paired with legitimate, signed binaries.
Technical Analysis
Mustang Panda packs their tools in archive files hosted on a staging server. All the tools detected by ThreatLabz utilized DLL sideloading to execute malicious payloads to evade endpoint detection products.
We will first examine new versions of a known Mustang Panda tool known as ToneShell. ToneShell is designed to download malicious payloads and execute attacker-specified commands on target machines.
ToneShell
ToneShell is one of Mustang Panda's most frequently used malware tools. Since the core functionality has already been publicly documented, this analysis focuses solely on the recent changes worth highlighting. This section examines three variants of ToneShell: Variants 1 and 3 were discovered on Mustang Panda’s staging server, while Variant 2 was identified through a third-party malware repository bundled in a ZIP file instead of a RAR file.
All three ToneShell variants were found in archive files, which include a legitimate executable (EXE) file and a DLL file (ToneShelll) which is sideloaded.
ToneShell Variant | Archive Filename | Executable Name | DLL Name |
|---|---|---|---|
1 |
|
|
|
2 |
|
|
|
3 |
|
|
|
Table 1: Example ToneShell variant filenames.
Seed generation
Random number generators are utilized in multiple sections of ToneShell’s code for two primary purposes:
- As a fallback mechanism to generate a 16-byte GUID if
CoCreateGuid()fails (as described in the following section). - To generate a rolling XOR key, which encrypts and decrypts data exchanged between the victim’s machine and the C2 server.
Each random number generator requires a seed, which ToneShell derives using various methods. These methods are listed in the table below.
Variant | Description |
|---|---|
Variant 1 | Derives the seed by calling |
Variant 2 | Derives the seed by calling |
Variant 3 | Derives the Unix epoch timestamp from the Windows FILETIME format using the code shown below. |
Table 2: ToneShell random number seed generation.
seed = (*(_QWORD *)&SystemTimeAsFileTime - 116444736000000000i64) / 10000000;
Creation of GUID file
Each ToneShell variant observed in-the-wild generates a GUID, or a value derived from the GUID, and writes it to a file on the filesystem. This GUID is used to uniquely identify the infected machine. Recent variants display subtle changes in how this file is created. The table below shows how the three different ToneShell variants create the GUID file.
Variant | Description |
|---|---|
Variant 1 |
|
Variant 2 |
|
Variant 3 |
|
Table 3: Shows how each ToneShell variant creates the GUID file.
struct GUIDFILE
{
DWORD total_length;
BYTE guid[16];
DWORD length_of_random_byte_array; // 64KB max size
BYTE random_byte_array[];
}
Rolling XOR key
ToneShell employs a rolling XOR key to encrypt and decrypt network traffic exchanged with its C2 server. This XOR key is generated using an LCG, seeded by values derived through methods previously described. The XOR key size varies across ToneShell variants, with Team T5 documenting sizes ranging from 0x20 to 0x200.
- Variant 1 uses a 0x100-byte XOR key
- Variant 2 uses a 0x100-byte XOR key
- Variant 3 uses a 0x200 byte XOR key
This aligns with Mustang Panda's tactic of rapidly iterating and modifying their tools, likely to evade detection.
FakeTLS header
FakeTLS headers are a key feature of ToneShell, which helps disguise the malware’s network activity. They are used to mimic the TLS protocol in network traffic exchanged between the infected machine and the C2 server.
Earlier ToneShell variants utilized the FakeTLS header with the bytes 0x17 0x03 0x03, corresponding to TLSv1.2. However, newer variants have introduced the FakeTLS header bytes 0x17 0x03 0x04, to spoof TLSv1.3. Interestingly, in Variant 2, the TLSv1.3 FakeTLS header was used for sending beacons, while the server continued responding with the older TLSv1.2 header.
This modification appears to be an attempt by the threat actor to evade network signature-based detection systems that rely on identifying specific FakeTLS header patterns.
C2 commands
ToneShell variants continue to utilize a custom TCP-based protocol. Compared to earlier versions, these newer variants focus primarily on executing payloads received from the C2, reflecting Mustang Panda's pattern of iterating their tools, likely to evade detection while adopting a more minimalist design for remote shells.
Variant 1 is a very minimal backdoor, which receives files and acts as a reverse shell. The table below shows the C2 commands supported by Variant 1.
Command Number | Description |
|---|---|
1 | Receives and processes the next command from the C2 server. |
2 | Creates an empty file at the C2-specified file path and stores the file handle. |
3 | Appends the bytes received to an open file handle (from Command 2). |
4 | Appends the bytes received to an open file handle (from Command 2), closes the file handle, and frees up the file path string in memory thereafter. |
5 | Creates a reverse shell (cmd.exe), redirecting both stdin and stdout. ToneShell keeps track of this subprocess using an ID received from the C2 server. A background thread is created to continually send the output from the subprocess back to the C2 server. |
6 | Finds the subprocess with the given ID and writes to its standard input. |
7 | Terminates the subprocess with the given ID. |
Table 4: C2 commands supported by Variant 1 of ToneShell.
Variant 2 specifically includes functionality to download DLLs from the C2 and execute them within victim processes through DLL injection. The table below shows the C2 commands supported by Variant 2.
Command Number | Description |
|---|---|
1 | Receives and processes the next command from the C2 server. |
2 | Pauses operation for 3 minutes. |
3 | Terminates the current process. |
4 | Retrieves the name of the infected machine. |
5 | Identifies usernames that are not built-in accounts. |
6 | Specifies the file path to create a new file (used in Command 8). |
7 | Defines the size of the file to be downloaded (used in Command 8). |
8 | Creates and writes a DLL file likely used in conjunction with Command 10. |
9 | Updates the configuration for the executable path used in shellcode injection (Command 10). Defaults to |
10 | This command creates a child process using the victim executable path specified by command 9. Command 10 also supports an option via a parameter to perform token impersonation when creating the process. ToneShell then decodes shellcode that is hardcoded into the malware with randomized padding bytes, and specific arguments, including |
Table 5: C2 commands supported by Variant 2 of ToneShell.
ToneShell Variant 3 includes functionality to download files and create a subprocess that redirects standard input (stdin), standard output (stdout), and standard error (stderr) streams to the C2 server. The table below shows the C2 commands supported by Variant 3.
Command Number | Description |
|---|---|
3 | Creates an empty file at the C2-specified file path and stores the file handle. |
4 | Opens an existing file at the C2-specified file path, moves to the end of the file, and stores the file handle. |
5 | Appends bytes received from the C2 to an open file handle (from Command 3). |
6 | Deletes the file used in commands 3, 4, or 5. |
7 | Executes a subprocess using the command-line received from the C2, redirecting the stdin, stderr, and stdout subprocess. |
8 | Transfers bytes received from the C2 to the stdin subprocess and reads its output. |
9 | Retrieves the output of the subprocess. |
10 | Terminates the subprocess and closes all associated handles. |
Table 6: C2 commands supported by Variant 3 of ToneShell.
StarProxy
ThreatLabz uncovered a new lateral movement tool associated with Mustang Panda’s operations, which we named StarProxy. This tool was found within a RAR archive hosted on the group’s staging server with the name client.rar. The archive contains two files: a legitimate, signed binary (IsoBurner.exe) and a malicious DLL (StarBurn.dll), which is the StarProxy tool. The StarProxy DLL is sideloaded when the IsoBurner.exe file is executed.
Once active, StarProxy allows attackers to proxy traffic between infected devices and their C2 servers. StarProxy achieves this by utilizing TCP sockets to communicate with the C2 server via the FakeTLS protocol, encrypting all exchanged data with a custom XOR-based encryption algorithm. Additionally, the tool uses command-line arguments to specify the IP address and port for communication, enabling attackers to relay data through compromised machines. The figure below illustrates how StarProxy proxies traffic.
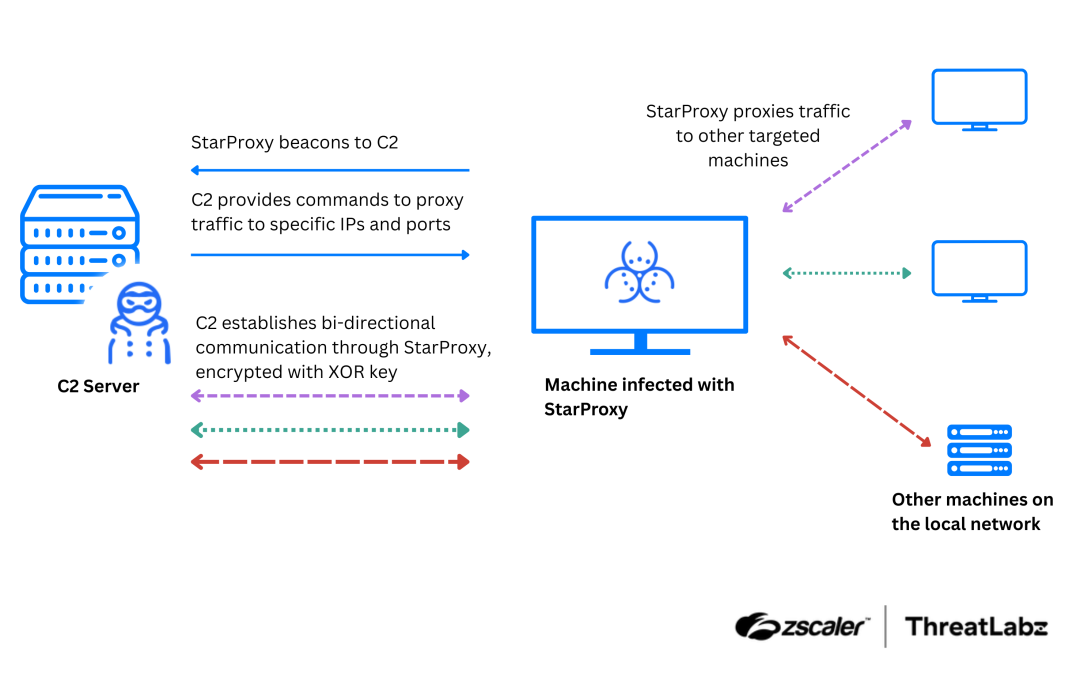
Figure 1: High-level diagram of StarProxy activity.
Given the features of the malware, and the use of command-line arguments, Mustang Panda likely uses StarProxy as a post-compromise tool to access systems that are not reachable directly over the Internet.
Initialization
The StarProxy DLL contains a malicious export function named StarBurn_UpStartEx, which expects two command-line arguments: a C2 IP address and a port number. Upon execution, the DLL attempts to connect to the specified C2 IP address. If the connection fails, StarProxy will keep retrying until it succeeds, waiting for one second in between attempts.
Beaconing
Once a connection to the C2 server is successfully established, StarProxy beacons to the C2 to receive commands. If the C2 server signals that there are no commands, StarProxy waits for one second before beaconing again. If the C2 server signals that there are further commands to execute, StarProxy makes additional requests to the C2 server to retrieve the commands and execute them.
Packet encryption and decryption
All messages exchanged between the client and the C2 server are encrypted using two hardcoded 0x100-byte XOR keys. Details of the XOR keys and the encryption algorithm are available on the ThreatLabz GitHub page.
C2 protocol
Request Header
All messages sent by StarProxy to the C2 server are prefixed with a request header (SEND_HEADER), which includes the fields below.
struct SEND_HEADER
{
BYTE fake_tls_header[3]; // 0x17 0x03 0x03.
WORD message_size; // Size of data after the FakeTLS header.
DWORD zero; // Zero bytes (start of encrypted data with a hardcoded key).
WORD message_type; // C2 message type.
WORD buffer_size; // Buffer size specific to each message type.
}Response header
All messages sent by the C2 to StarProxy are prefixed with a response header (RECV_HEADER), which includes the fields below.
struct RECV_HEADER
{
BYTE fake_tls_header[3]; // 0x17 0x03 0x03.
WORD buffer_size; // Size of the message body (RECV_BODY).
}Notably, the FakeTLS header in these messages is designed to impersonate the TLSv1.2 protocol similar to the earlier ToneShell variants.
Response body (RECV_BODY)
The RECV_HEADER is followed by the RECV_BODY, which includes the command number and data specific to the corresponding command. The generic structure of the RECV_BODY is shown below.
struct RECV_BODY
{
DWORD unused1;
WORD command_number; // The ID of the command to be executed.
WORD unused2;
BYTE body[]; // Body data (variable length array).
}
Beacon message
As mentioned in the beaconing section above, StarProxy sends a beacon message (CMD_0_MESSAGE) at regular intervals to check for commands to be executed. The structure of the beacon message is shown in the table below.
struct BEACON_MESSAGE
{
SEND_HEADER send_header; // message_type = 0 to indicate beacon message.
DWORD hash_of_rand_arr; // The hash of a randomly generated array with variable length, computed using a custom hash algorithm.
DWORD size_of_rand_arr; // Number of bytes occupied by the random array. This is always a multiple of four.
BYTE rand_arr[]; // A variable-length random array, likely used to verify the correct decryption of messages from the client.
}StarProxy uses the following convoluted process to generate the array of random bytes:
- Calls
GetLocalTime()to retrieve aSystemTimestructure. - Adds up all members of the
SystemTimestructure to generate a seed. - The seed is used to initialize a pseudo-random number generator (PRNG) using
srand(). - Generates a random number between 1 and 16. This value will be the variable length (in bytes) of the array containing 32-bit integers.
- The array is filled with randomly generated 32-bit integers, which are then used to generate a 32-bit hash.
In response to the beacon message, StarProxy expects the following response format from the C2:
struct BEACON_MESSAGE_RESPONSE
{
RECV_HEADER recv_header; // Contains the FakeTLS header and message size.
DWORD unused;
DWORD has_command; // 0: command data present; any other value: no data present.
}
C2 command handler
The StarProxy client supports 5 command IDs (RECV_BODY.wCmdNum). The table below describes each command ID and its purpose.
Command ID | Description |
|---|---|
1 | Command 1 appears to be a ping command. |
2 | Command 2 also appears to be a ping command, implemented exactly as command 1. The purpose of this duplicated command is unclear. |
3 | Command 3 directs StarProxy to set up a TCP connection to a target IP or domain. Once the connection is established, StarProxy sends the newly created socket descriptor to the C2. StarProxy then sets up a background thread to receive data from the target and forward it back to the C2. |
4 | Forwards message to specified socket descriptor. |
5 | Closes the socket descriptor specified by the StarProxy C2 server. |
Table 7: Lists StarProxy commands.
The purpose of the duplicate command handlers 1 and 2 is not clear, but could suggest that StarProxy is still under development.
To Be Continued
In Part 1, we explored Mustang Panda’s modifications to ToneShell and a new lateral movement tool that we discovered called StarProxy that is likely used for post-compromise activities and lateral movement. In Part 2, we will explore two new keyloggers and an EDR evasion driver, also discovered on Mustang Panda’s staging server.
Zscaler Coverage
Zscaler’s multilayered cloud security platform detects indicators related to Mustang Panda at various levels with the following threat names:
Indicators Of Compromise (IOCs)
File indicators
MD5 Hash | SHA1 Hash | SHA256 Hash | Filename | Description |
|---|---|---|---|---|
233214d22659aa85f32bb705812a0b22 | fcc7095f6ddbffb7c2ca29188c45bbdf4c922c66 | ede116e8f652728773363f6808fa8bbd5af873398e4bb5393c210677fa96a654 | cf.rar | RAR archive hosted on attacker's server
|
b695a31ea90e61cc08da1837d836655a | 03272f764bc0f6d80a830c164a5357cd9179030e | a0f42337601429ffda00aa64b8e6102e2470b2388c132f96002f37d40f40d587 | libcef.dll | ToneShell DLL |
4fefc66a0f7e1b2ed8affc9c3ba66ec7 | 0d186cd1ecc525716ac08cbd5f59c58e44d08202 | 8fe76b434c9d57d5b82a786bcfac5aa3a75be88b19df5cd76e111af58c3c98c5 | mrender.exe | Legitimate signed binary
|
4572914d6fd4b50604b30c761736ef7d | 1afde3bfe7ff7a9a164c9e6a0de12f5f1ce50b9a | 91d8b31259d8602539fb6eaa0588d6521bf01299ccd8ed830abfe2ace7aea54d | client.rar | RAR archive hosted on the server
|
db26dbad33580489204320c9c5ea400b | 81dce30dfb85d8a110f384ab72f23081f20f500d | c1d24a5cb1d57a91cf4a717425bd0d46b4436d14d7f4744fa8dfbb22609f57a8 | IsoBurner.exe | Legitimate and signed binary
|
784bcd1f62b97589f479525d27f883cb | 70b286728cf006ae6da37d918d372b7cedd40855 | 63aa30c452e4dc0aa2324ce891da1acfa90ce85476d2dd7ab85ff448f913af5e | StarBurn.dll | Malicious DLL - StarProxy
|
3ed1b60aada8ec3fc0965976c542dda5 | da01214c5df3ee4a5a6b99414e4bb1fd88f6eb3e | 649b32f2db7d71cd083e9af4fae2fb3c086f5ed73eac622f427f7fa5d513c605 | zz.rar | RAR archive |
5788433d90e3297b32dfa009790490aa | 428c4da69023ec6ca7d253e5c643fd1c2689c55c | 69555f4d956fce11eac8fb6d7286c087d6acacf7971821ede1335e96a3c72736 | gpgconf.exe | Legitimate and signed binary |
1b388ef6594415421ef1b3cd9502fc7a | 092cd5ad641ce749c100c2ad045e4aabb9bb7e90 | cf1f057bc8cb25b2d6d0704cef0655ea4d41ea247c51984b25635bd23c8ae109 | libgcrypt-20.dll | ToneShell DLL |
9afdcf5369eca11d412870f7cb805da9 | 20b4624781bdc1f670942dc07bf673abd1c5e70f | 21e271bde14b62a1c982ea3aefc1c42a7f5b412126e920e7dd4200cbf14fe475 | libgpg-error-0.dll | N/A |
7c65d1e28fadf9b6d704b5c47016c05d | 67d777f491b89d052c709cec7762b91ab514d3e6 | a901fd9ef4044a872866ad9506cf3e17cbf58b93278ac3ca7e48820b3a228458 | Bandizip.exe | Legitimate and signed binary |
2012bf5de269d9acd0bfd7250ab46c68 | 337850d965dd9860162c2084d83d4113bac95593 | 88e1b73318ba2107c2e70a59064d51e4fecd37ab6175735e43abfa8657d2cd91 | ark.x64.dll | ToneShell DLL |
5936b135905bee8f038b9266362f22c7 | f435900ebbc8a46c3b0b273d48b2ac149a35b194 | a9b1289383ffe3ee2bd0df96ad6918b9a7e27819e4bc10c3922d8bbd61cbd959 | ru.zip | Zip archive |
d7ae078b2641b94c8042424a1387851b | 296c37ab1985c08bd3b194b129392c8d4d164399 | 005754ced6f73a197a4a21c58da39d5e3ee84e484640765dbda2475f4ba2d3bd | FastVD.exe | Legitimate and signed binary |
6164f397ff13c56310e94af235a9aa02 | b2544370e041c2b3d38e5b1c0a22b4eab2d70588 | 57e22a93fc31bd299871840864e82fa553e99501af7645102d07dceed2a8ef1a | LogMeIn.dll | ToneShell DLL |
ToneShell variants
The table below shows details about the three ToneShell variants identified by ThreatLabz.
Variant | Description |
|---|---|
Variant 1 | ITW Filename: libcef.dll MD5: b695a31ea90e61cc08da1837d836655a Compilation Time Stamp: Sun Dec 15 21:58:31 2024 |
Variant 2 | ITW Filename: LogMeIn.dll MD5: 6164f397ff13c56310e94af235a9aa02 Compilation Time Stamp: Tue Jan 14 02:42:26 2025 |
Variant 3 | ITW Filename: libgcrypt-20.dll MD5: 1b388ef6594415421ef1b3cd9502fc7a Compilation Time Stamp: Thu Jan 02 09:48:51 2025 |
Network indicators
Type | Indicator |
|---|---|
Staging server URL | 103.13.31[.]75/heugojhgriuhn78867jhkbjkdgfhuie78/jhegiokj7889seghjegh786jkhegfukj/ |
C2 domain | www.dest-working[.]com |
C2 domain | www.profile-keybord[.]com |
C2 IP address | 43.229.79[.]163 |
C2 IP address | 43.254.132[.]217 |
C2 IP address | 181.215.246[.]155 |
Host indicators
ToneShell GUID file paths
The following files are used to store the GUID or its derived values.
%temp%\cryption_event.iniC:\\ProgramData\\bcryptprimitive.appcore.tbiC:\Users\public\description.ini
Certificate details of the signed binaries
SHA256 Hash | Binary Name | Signer Name |
|---|---|---|
8fe76b434c9d57d5b82a786bcfac5aa3a75be88b19df5cd76e111af58c3c98c5 | mrender.exe | JUNYUN LIMITED |
c1d24a5cb1d57a91cf4a717425bd0d46b4436d14d7f4744fa8dfbb22609f57a8 | IsoBurner.exe | LSoft Technologies Inc |
69555f4d956fce11eac8fb6d7286c087d6acacf7971821ede1335e96a3c72736 | gpgconf.exe | g10 Code GmbH |
MITRE ATT&CK Framework
ID | Tactic | Description |
|---|---|---|
T1574.002 | Hijack Execution Flow: DLL Side-Loading | All the DLLs in this new toolset are sideloaded by legitimate and signed Windows binaries. |
TA0011 | Command and Control | StarProxy and ToneShell variants have command-and-control capabilities. |
T1573 | Encrypted Channel | StarProxy uses two 256-byte XOR keys to encrypt and decrypt network packets using a custom algorithm.
ToneShell variants use a randomly generated variable length (0x20 - 0x200 bytes) rolling XOR key to encrypt and decrypt network packets. |
T1090.001 | Proxy: Internal Proxy | StarProxy is equipped with capabilities to route traffic between systems within a compromised network. |
T1573.001 | Symmetric Cryptography | The XOR encryption algorithms employed by Mustang Panda's tools are based on symmetric cryptography. |
TA0005 | Defense evasion | Encrypted network packets exchanged between client and C2 server can be used to evade network security products. |
T1001.003 | Data Obfuscation: Protocol Impersonation | StarProxy and ToneShell variants use FakeTLS headers in network packets to impersonate various versions of TLS protocols and blend in with legitimate network traffic. |
T1027.007 | Obfuscated Files or Information: Dynamic API Resolution | ToneShell uses a modified DJB2 algorithm to resolve APIs. |
T1055.001 | Process Injection: Dynamic-link Library Injection | ToneShell uses DLL injection to execute payloads received from the C2 server. |
T1070.004 | Indicator Removal: File Deletion | ToneShell includes functionality to delete payload files received from the C2 server. |
T1134.002 | Access Token Manipulation: Create Process with Token | ToneShell includes functionality to create sub-processes with a specific user’s token. |
T1087 | Account Discovery | ToneShell includes functionality to retrieve a list of user accounts. |
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



