
Aug 14, 2023
In a rare public report, the intelligence-sharing cooperative known as "Five Eyes" called the cyber industry's attention to the most exploited CVEs in 2022. Noticeably absent? Headline-grabbing zero days.
“Five Eyes” refers to an intelligence-sharing alliance between the US, UK, Canada, Australia, and New Zealand. This alliance, forged after WW2 to further the interests of English-speaking democracies, operated in secret for decades before coming to the public’s attention in 2005. Today, they continue their work behind a veil of secrecy, which makes their release of a report titled 2022 Top Routinely Exploited Vulnerabilities noteworthy. What does the collective intelligence of the Five Eyes nations have to say about the cyberattacks of last year?
Zero day vulnerabilities aren’t the greatest risk
The top takeaway from the report is that, “malicious cyber actors exploited older software vulnerabilities more frequently than recently disclosed vulnerabilities and targeted unpatched, internet-facing systems.” It seems attackers are more focused on the issues you should have patched for the last two years than today’s headline-grabbing vulnerability. The report is based on their analysis of 42 of the most routinely exploited CVEs observed in 2022. The following chart shows which year each commonly exploited CVE was disclosed.
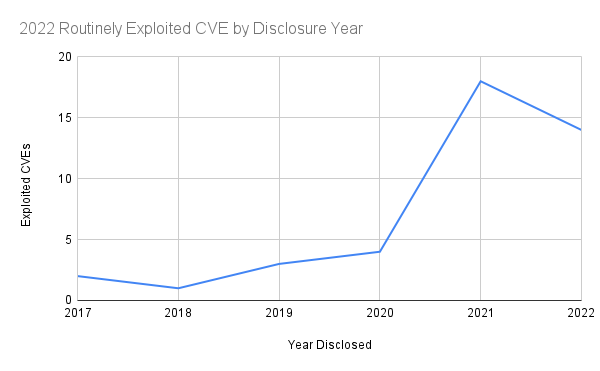
A cursory glance might convince you that vulnerabilities announced in 2021 are only slightly more troublesome than those from 2022. While technically correct, this view overlooks a larger problem that could cost your company dearly. Consider what the picture looks like if you follow a reactive strategy focused on addressing anything in the current news cycle.
In this hypothetical case, a CISO assumes duties in 2022 and focuses on patching each routinely exploited vulnerability as it is disclosed. Perhaps they assume their predecessors followed the same strategy, or they are simply unconcerned with old security issues. How would the security of their environment stack up against the most commonly employed attack strategies?
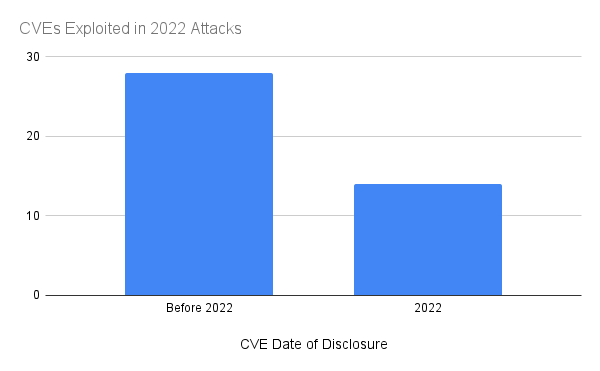
If our imaginary CISO patched every commonly exploited CVE disclosed in 2022, they would have successfully addressed 33% of the problem. However, they’ve ignored two-thirds of the vulnerabilities attackers are routinely exploiting. This is a broad generalization, of course. Every enterprise is not exposed to all commonly exploited CVEs. Each organization has its own unique blend of IT infrastructure and cloud services. Yet, this thought exercise demonstrates why it is imperative for security professionals to resist recency bias when weighing cyber risks. An enterprise patching strategy that focuses on reacting to the current news cycle overlooks 66% of the danger.
Time translates to increased risk
Why are older vulnerabilities more dangerous than new ones? Consider the various security factors that come into play as a vulnerability ages. A zero day vulnerability is something very few people know about, which limits the probability of it affecting your organization immediately. It is like a gun with one bullet - extremely dangerous to whomever is in the crosshairs but less threatening once fired.
Suppose a hostile nation-state or an elite team of threat actors has an incredible zero day vulnerability socked away for a rainy day. They have one shot at maximizing the impact of its exploitation. Once threat researchers catch on, it’s only a matter of time before the vulnerability is patched. Why would a serious threat group burn a zero day on anything less than a top-tier global company or government organization? You should certainly respond to these vulnerabilities by patching them as soon as possible. However, the odds that your company will be the chosen target of a zero day is unlikely. It is important to make sure the panic surrounding these attacks doesn’t overshadow greater (and more probable) cyber risks.
As a vulnerability ages, more people, including threat actors, become aware of its potential uses and capabilities. It takes time for threat actors to integrate new vulnerabilities into their adversarial tools. Finding unpatched organizations susceptible to a vulnerability and formulating campaign strategies also takes time, but it allows for more effective, efficient, and widespread attacks. Older vulnerabilities are more likely to be incorporated into a threat group’s toolkit, and used by a larger group of malicious actors. Exploiting a zero day is something usually performed by a small group of experts. However, as more people examine and discuss the vulnerability, the bar for launching similar attacks is lowered.
This lowering of the bar is particularly evident when researchers post proof-of-concept code to demonstrate a successful exploitation. Once a vulnerability is well documented and code for exploiting it is readily available, the hardest work has been done. Anyone who knows how to scan an environment for vulnerabilities and execute pre-written code poses a serious cyber risk to your organization.
Patch early, patch often
When I said Five Eyes operates in secrecy, it was a bit of an understatement. Gough Whitlam, former Prime Minister of Australia, was not aware of its existence until 1973, seventeen years after his nation became a member. Most people today are probably unaware of the secret intelligence alliance that has united the anglosphere for over sixty years. However, it’s no secret that patching and updating your environment in 2023 is the right move. Responding to the flaws in today’s news feed is not enough; the most exploited vulnerabilities are in the rearview.
The 2022 Top Routinely Exploited Vulnerabilities report offers four pages of mitigations for those looking for guidance on securing their environment from these risks. If that seems too heavy of a lift, you can still make progress by following the standard security advice, “patch early, patch often.”
What to read next
Shift left, save resources: DevSecOps and the CI/CD pipeline
Unnatural selection: Why cybercriminals are turning to encryption-less ransomware
Recommended
