
EDITOR'S PICK
Jul 11, 2022
Fears of a recession are rising. Will cybersecurity investment suffer as a result?
I was working for a utility company in 2008 when a bubble burst in the housing market and caused the economy to collapse. We were all asked to tighten our belts. I knew then that I had to reduce spending on software solutions rather than staff.
Today, a recession is commonly understood to entail two consecutive quarters of economic contraction. On the other hand, the National Bureau of Economic Research defines a recession more loosely as "a significant decline in economic activity that is spread across the economy and lasts more than a few months.”
Whichever definition you prefer, it’s fair to ask if we are either already in the midst of one or headed in that direction. Layoffs are currently hitting the tech sector hard, startups are tempering growth expectations due to the prospect of rising interest rates, and established enterprises are revising down plans to make new hires. Will investment in cybersecurity solutions and staff suffer as a result?
I recently spoke about the importance of executives delineating between discretionary and non-discretionary spending. I believe skilled cybersecurity workers clearly fall in the non-discretionary category for at least a few reasons.
First, when organizations begin laying off cyber professionals, it's an indication that the right hand doesn't know what the left hand is doing. One side of the organization is scrambling for talent to bolster its cyber defenses, while the other is looking for any opportunity to cut costs. When it comes to security staff, these efforts are at odds with one another. CISOs and CIOs are well aware that cyber threats are likely to grow over the near term, with many believing that new technology like 5G, smart devices, and AI-enabled threats will only increase an already broad attack surface.
Second, those who are cut during hard times won’t forget, and they won’t return during good times. Executives will only exacerbate their own cybersecurity skills shortages by laying off these workers. If it’s true that we are in the midst of a recession, it’s an unusual one in the sense that the demand for workers remains strong. In the cybersecurity industry alone, there are reportedly more than 2 million positions in need of filling. Organizations lucky enough to have snatched up talent to plug their own gaps should do their best to hold onto them for when the economy once again comes around.
Finally, shedding security staff sends the wrong message to markets, bad actors, and the general public. It can imply a lack of concern for customer privacy and a negative outlook for the future. Data breaches imperil users’ privacy and can impart lasting negative impressions. No one wants to be the next to make headlines for leaking sensitive customer data, but that’s the fate organizations court by neglecting cybersecurity spending.
If worse comes to worst
Imagine you are a CFO in dire enough straits to turn to your cybersecurity budget for cuts. You have the choice of slashing spending in one of three areas: hardware, software, or staff. And you’re gambling that the cost of spending in any proportion on these three areas is more expensive than the cost of a breach.
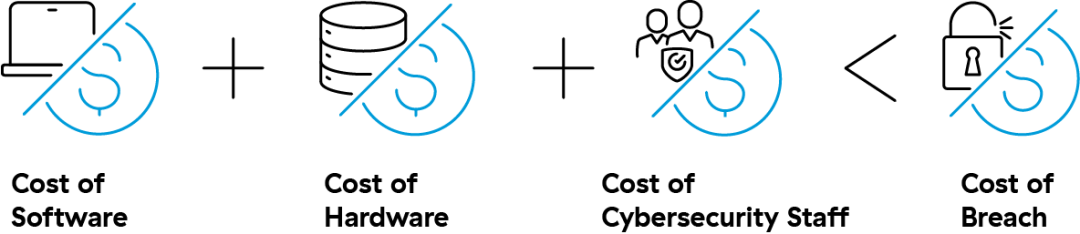
Admittedly, a business's tolerance for risk and the probability of an adverse cyber incident occurring are two factors that muddle this oversimplified equation. But I submit that now is not the time for organizations to roll the dice on remaining unscathed by cyberattacks in the absence of strong defenses.
By reducing spending in any one of the three areas, the odds of incurring a breach rise. And chances are, the costs associated with an adverse cyber incident are likely to be orders of magnitude higher than spending on hardware, software, and staff combined. This is especially true when organizations calculate reputational harm, the loss of customer trust, and sacrificed productivity among the potential damages.
It’s up to CISOs and CIOs to explain the knock-on effects of a potential breach and make a vivid case for prioritizing cybersecurity spending as essential to the health and wellbeing of the business. If there’s one area in which cybersecurity leadership is falling short in their service to top executives and board members, it is perhaps in adequately expressing these dangers.
A brief aside here: cybersecurity insurance is no substitute for spending on cyber defenses. It simply can never cover the losses sustained in an attack. Collateral damage like public image aside, any policy coming even close to doing so would cost organizations dearly in premiums. CIOs, CFOs, and board members should never rely on the fact that they've been told cyber insurance will protect them.
Before staff, cut trust
Typical IT teams are tasked with securing six attack vectors:
- Users
- Devices
- Datacenters
- Applications
- Networks
- Data
Protecting all these elements with legacy IT architecture is intensive, laborious, and complicated. It must be done 24/7/365 and requires significant training in a diverse set of disciplines. Doing all of it in the face of reduced investment becomes nearly impossible.
Keeping software patched, replacing aging hardware, and monitoring alerts from potentially dozens of consoles for a lineup of point solutions has the potential to exhaust understaffed and undersupported teams. This, in turn, exacerbates the shortage as dissatisfied employees leave the organization for one of the millions of other open IT positions mentioned earlier.
Network permissions once gave IT admins reassurance that, at any second in any day, they know where their data resides and who is allowed to access it. But that day has passed. Malicious actors can see what your staff can see. So today, we must be sure that only the right users with the right permissions on the right devices are even allowed to know the access exists in the first place.
Short of a guarantee, the best protection (which incidentally may also help reduce IT spending) is the adoption of zero trust principles. Using a zero trust exchange to shroud assets from the outside world eliminates the attack surface. Providing access after verifying – and only after verifying – a pre-determined set of policies is the key to securing users, applications, and networks.
Organizations that continue down the legacy path, cutting staff to survive at the expense of their own security, will find themselves riding the coattails of organizations that have invested in the future.
Recommended
