
CISO Monthly Roundup, August 2023: Deep analysis of Ducktail, Statc Stealer, JanelaRAT, Agniane Stealer, insights on SEC cybersecurity policies, and NetScaler security advisories
Sep 5, 2023
The August CISO Monthly Roundup features ThreatLabz research on DuckTail, Static Stealer, JanelaRAT, and more.
The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on other cyber-related subjects. Over the past month, ThreatLabz deconstructed Ducktail operations, analyzed Statc Stealer, JanelaRAT, Agniane Stealer, provided insights on SEC cybersecurity policies, and issued NetScaler security advisories.
A deep dive into DuckTail
In May, Zscaler ThreatLabz began an intensive three-month analysis that gave us valuable insight and critical information about DuckTail’s operational framework. We have documented an extensive analysis of DuckTail’s intrusion techniques, compromise tactics, post-compromise procedures, and activities in the underground economy. Many of these insights have not been previously documented, but are now available to help others understand their targets and strategic motives.
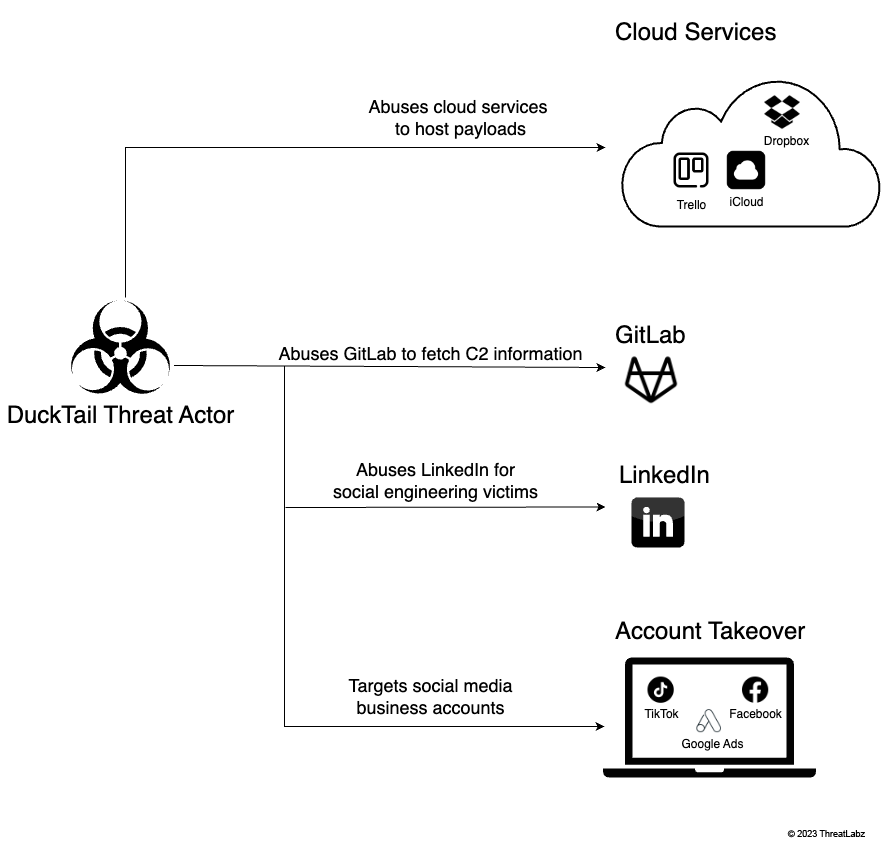
Our team discovered DuckTail threat actors primarily use social engineering to target users working in digital marketing and advertising so they can gain access to business accounts. They often create fake job postings on LinkedIn as a lure, then send applicants malware disguised as interview-related material. Once threat actors gain access to these accounts, they abuse security features to lock out victims. The group uses Telegram to perform C2 communications. Compromised accounts are sold on a Vietnamese underground market.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Studying Statc Stealer
The Zscaler ThreatLabz team has recently uncovered Statc Stealer, an information-stealing malware that specifically targets Windows-powered devices. It spreads via a malicious Google advertisement that infects computers when clicked. Statc infiltrates systems, steals sensitive data, and employs sophisticated evasion techniques to avoid detection. In our detailed analysis, we unveil the malware’s distribution methods and evasion strategies to provide crucial insights for safeguarding against this threat.
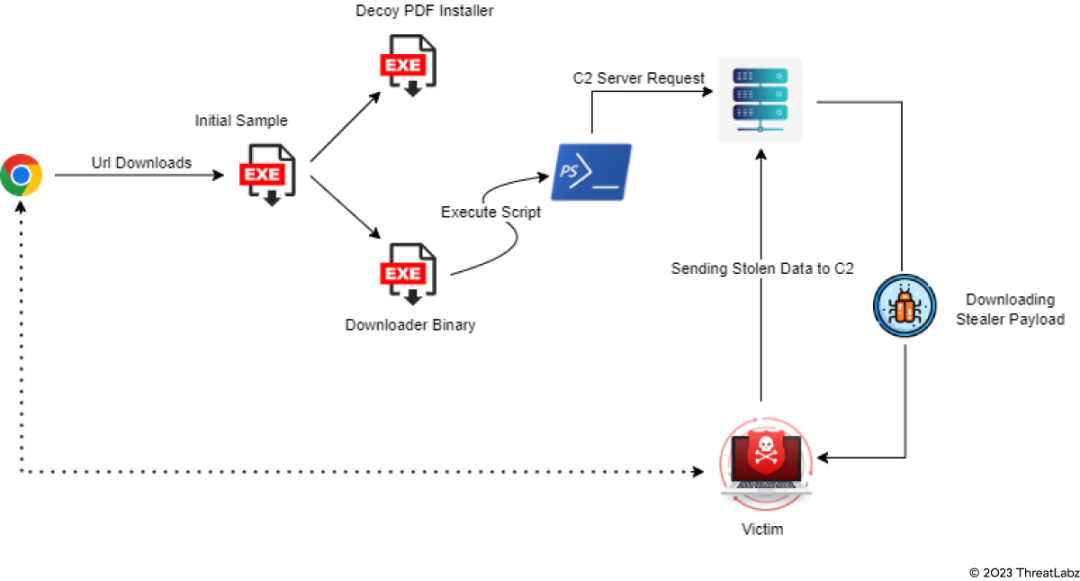
Statc Stealer exhibits a wide variety of stealing capabilities. It captures sensitive data and passwords from multiple browsers, cryptocurrency wallets, and messaging apps. The malware uses techniques such as filename checks and encryption to evade analysis and detection. Statc Stealer’s ability to exploit various apps for data theft highlights the importance of implementing comprehensive security measures.
Zscaler Zero Trust Exchange Coverage: Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Analyzing JanelaRAT
ThreatLabz recently discovered a Portuguese-speaking threat group targeting financial and crypto data in Latin American organizations. The adversaries are using a heavily modified variant of BX RAT, so we’re calling their current malware JanelaRAT. In its bid to steal data, JanelaRAT employs several tactics, techniques, and procedures (TTPs) such as DLL side-loading, dynamic C2 infrastructure, and a multi-stage attack.
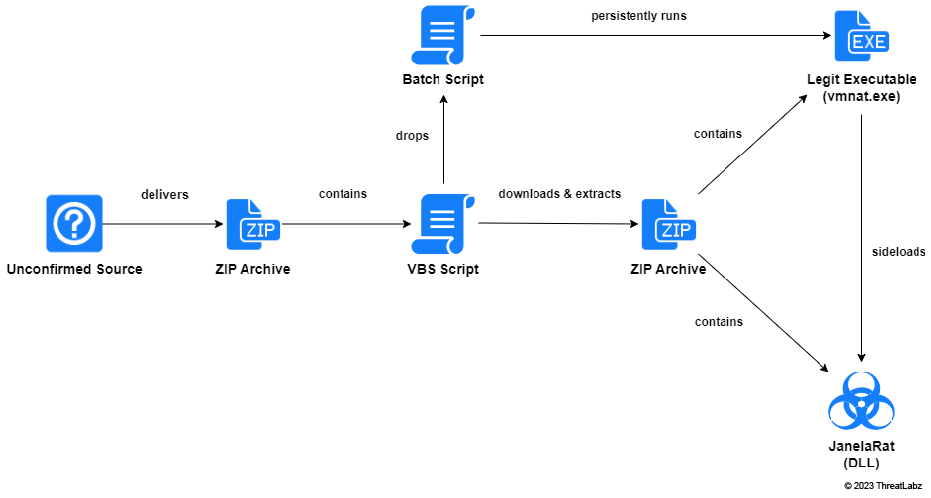
JanelaRAT can capture Windows title strings to steal relevant financial and banking data. It uses dynamic socket configuration that allows it to rotate C2 domains daily. It also performs DLL side-loading techniques using legitimate processes (like VMWare and Microsoft) to evade endpoint detection.
Read more about JanelaRat here
Zscaler Zero Trust Exchange Coverage: Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection.
Agniane Stealer: The dark web’s crypto threat
Agniane Stealer, a service sold on the dark web, steals sensitive information like credentials, session details, and crypto wallet data. We believe Agniane Stealer belongs to the Malware-as-a-Service (MaaS) platform Cinoshi Project, as the two share similar code structures. During our investigation we discovered a Telegram channel sharing updates and pricing information for this malware.
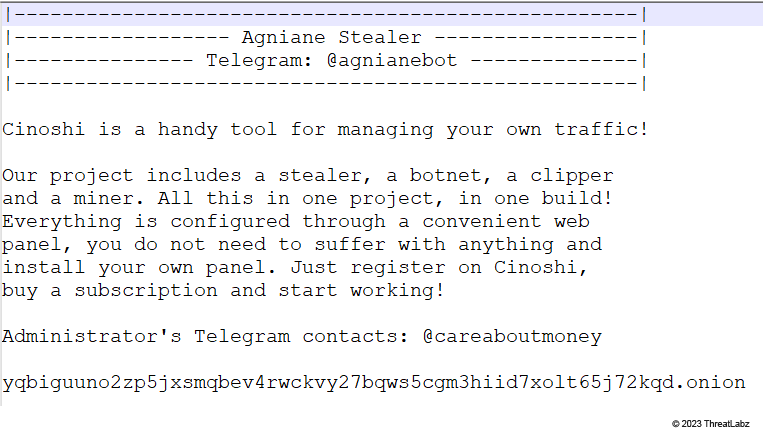
Agniane Stealer exfiltrates data from web browsers, Telegram sessions, Discord tokens, Steam, WinSCP, Filezilla sessions, crypto extensions, and crypto wallets. In its quest to remain undetected, Agniane Stealer looks for various types of security analysis software like malware sandboxes, emulators, and VirtualBox. It also leverages WMI to obtain CPU information, GPU details, and identify installed antivirus software. Agniane Stealer transfers stolen information to its command-and-control (C&C) servers and then removes its subfolder from the compromised machine.
Read our full analysis of Agniane Stealer
Zscaler Zero Trust Exchange Coverage: Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
The impact of the SEC’s new cybersecurity policies - CISO perspective
The U.S. Securities and Exchange Commission’s (SEC) new cybersecurity policies, introduced in July 2023, demand public companies promptly report significant cyber incidents and share details about their cybersecurity strategies. These new regulations aim to enhance transparency and cyber accountability by fostering informed stakeholders and encouraging robust risk management.
- These rules enforce swift reporting within four business days through Form 8-K, with exceptions for limited delays due to national security.
- The definition of a cybersecurity incident is expanded to include related unauthorized events for more comprehensive reporting.
- From December 15, 2023, annual Form 10-K reports must include information on cybersecurity risk management, strategy, and governance, although board members’ expertise disclosure is optional.
- Compliance deadlines vary by company size and disclosure type.
Security Advisory: Remote Code Execution Vulnerability (CVE-2023-3519)
Citrix issued a security advisory highlighting a critical vulnerability (CVE2023-3519) with a CVSS score of 9.8 on July 18. This vulnerability affects NetScaler ADC and NetScaler Gateway, and presents a risk of Remote Code Execution (RCE). The vulnerability has gained considerable attention due to reports of its use in active zero-day attacks. When successfully exploited, attackers can install web shells on crucial infrastructure.

The exploitation of CVE-2023-3519 involves triggering a stack buffer overflow through a specially crafted HTTP GET request, potentially leading to arbitrary code execution with “root” privileges. The attack chain includes uploading a file with a web shell and exploiting privilege escalation mechanisms to access Active Directory credentials.
The advisory also highlights other vulnerabilities:
- CVE-2023-3466 - A reflected Cross-Site Scripting (XSS) flaw that requires accessing an attacker-controlled link while on the NetScaler’s IP (NSIP).
- CVE-2023-3467 - A Privilege Escalation vulnerability needing authenticated access to NSIP or SNIP, with management interface access.
Users are advised to upgrade affected applications. Countermeasures, including network-segmentation controls, have thwarted attempts to exploit the vulnerability. ThreatLabz has also deployed specific protections against these vulnerabilities to Zscaler customers.
Zscaler Zero Trust Exchange Coverage: Advanced Threat Protection, App Protection, SSL Inspection.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
Crawl, walk, and run your way to more effective CASB policy creation
Recommended
