
Sep 2, 2022
Zero trust means a lot of different things to different people. Those who stick to the principles and understand what it is and what it is not can radically simplify their information technology and cybersecurity.
Zero trust means a lot of different things to different people. Those who stick to the principles and understand what it is and what it is not can radically simplify their information technology and cybersecurity. They experience it firsthand as a change in architecture, mindset, and culture.
But when it is applied piecemeal and as point solutions without regard for the core tenets, it can leave organizations confused and further behind with an aging corporate network covered with Band-Aid fixes unable to free itself from the architecture of the past three decades: hub-and-spoke networks protected with castle-and-moat security designs.
Given the opportunity to separate fact from fiction, a team of executive technologists recently authored the ultimate reference for the Zscaler approach centered on seven elements covering verification, control, and enforcement for transactions. In one seamless movement, the elements solve the problem at the root of all enterprise data breaches by disrupting the workflow of an attacker:
- Locate a target network
- Compromise it by exploiting a weak link
- Move laterally using shared network context
- Exfiltrate the most valuable data
In this way, the seven elements are the sine qua non of any successful zero trust architecture.
The elements
The challenges caused by legacy network and security architectures are pervasive, long-standing, and require a rethinking of how connectivity is granted in the modern world. This is where zero trust architecture must be leveraged–an architecture where no user or application is trusted by default. Zero trust is based on least-privileged access, which ensures that trust is only granted once identity and context are verified, and policy checks are enforced.
NIST defines the underlying principle of a zero trust architecture as “no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned).” It’s an overhaul of the old proverb “Never trust. Always verify.”
This approach treats all network communications as hostile, where communications between users and workloads or among workloads themselves are blocked until validated by identity-based policies. This ensures that inappropriate access and lateral movement are prevented. This validation carries across any network environment, where the network location of an entity is no longer a factor and not reliant on rigid network segmentation.
To fully understand zero trust architecture, it’s useful to break it down into individual building blocks (or elements) that are executed before any connection is established. These elements ensure that all enterprise services–user/devices, IoT/OT devices, and workloads–are subject to the same set of controls when requesting access to assets.
There are seven essential elements of zero trust architecture, grouped into three categories.

Within these three categories are the following elements.
In order to verify identity and context, we must ask:
1. Who is connecting? – This first element verifies the identity of the user/device, IoT/OT device, or workload through integrations with third-party identity providers (IdPs) as part of an enterprise identity access management (IAM).
2. What is the access context? – This element validates the context of the connection requester, looking at attributes such as the role, responsibility, location, and others
3. Where is the connection going? – This element confirms that the verified identity has the rights and required context to access the requested application or resource.
To control content and access, we must first:
4. Assess risk – This element leverages AI to dynamically compute a risk score for the user/device, IoT/OT device, or workload based on multiple factors.
5. Prevent compromise – This element utilizes inline decryption and deep content inspection to identify and block malicious content.
6. Prevent data loss – This element also uses decryption and deep content inspection to identify sensitive data and prevent its exfiltration.
Then and only then can we:
7. Enforce policy – This element uses the outputs of previous elements to determine what action to take, ultimately resulting in a conditional allow or conditional block.
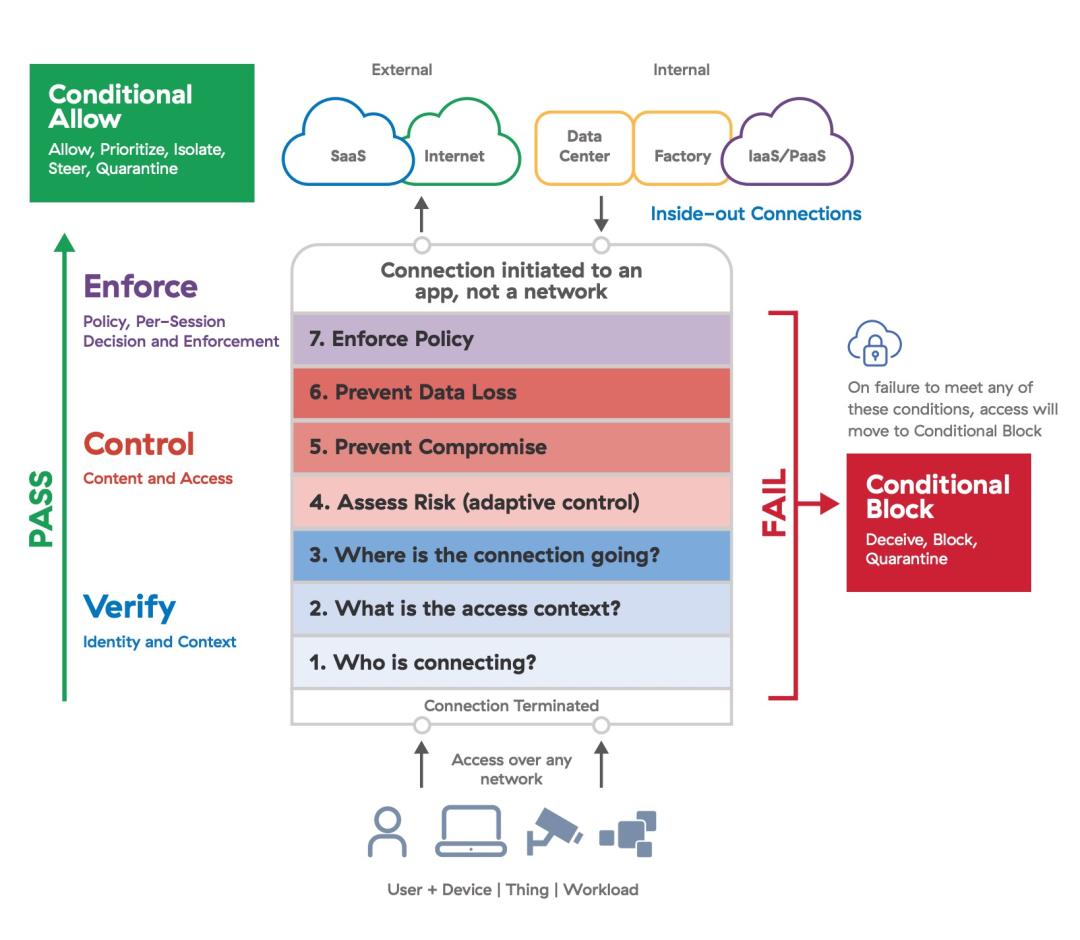
Note that all seven elements may not be used for all policies or types of traffic. For certain applications, such as VoIP, the choice may be to not inspect the content. Each element in this process feeds into the next, creating a dynamic decision tree that is utilized for each user/device, IoT/OT device, or workload-to-resource request. Every connection must evaluate identity, profile, user risk, site risk, posture, and content as criteria for deciding whether to grant access conditionally or to block conditionally.
Finally, remember that none of the elements above can come at the expense of the user experience. Zero trust architecture must therefore be able to monitor performance and diagnose experience issues to ensure that these seven elements do not put an undue burden on the user.
Download the complete Seven Elements of Highly Successful Zero Trust Architecture eBook and stay tuned for more installments of our accompanying commentary
Recommended
