
Nov 22, 2023
Assisting your board in determining how susceptible your organization is to being breached requires conveying its cyber risk posture in terms intelligible to non-experts.
Boards cannot address a problem as complex as cybercrime if the scope of the problem is not well understood. Assisting your board in determining how susceptible your organization is to being breached should be aimed at determining its cyber risk posture. Cyber risk posture refers to an organization’s ability to protect itself from cyber threats and risks. Even the millions of dollars the board has authorized for cybersecurity do not mean that there is minimal risk.
To ascertain the cyber risk posture of your organization, a CXO should relate to the boards the answers to the following questions:
- What is our exposed cyberattack surface? Do we still use older and riskier network and security architectures? In essence, are we reachable, which means we are breachable? Specify that these questions also include physical assets, like operational technology (OT) or internet of things (IoT), such as manufacturing equipment or medical devices.
- Who might be interested in attacking our organization? This may include external and internal attackers.
- What policies, procedures, or controls have been put in place to prevent or mitigate an attack?
- What programs are in place if the company is breached? For example, can an internal team address breaches of internal or customer data?
- If breached, can attackers freely roam our network looking for sensitive data? How effective are the current security controls in preventing this free movement
- Where is our sensitive data being kept, and can attackers find it? This includes identifying what data is most valuable, where it is stored, who has access to it, and how it is being used.
- Can attackers steal our sensitive data? What is the impact to the organization's reputation, financial stability, and ability to deliver products or services if data theft occurs?
- How well do we monitor internal employees and third parties who have access to our critical data and assets? Is it possible for these individuals to move data and funds out of the organization?
- Are there any existing contractual arrangements with external resources to assess the extent of a breach and help remediate?
Advising on these questions is the most critical step in assessing cyber risk posture. Third-party audits and assessments can also help provide an independent lens into your organization's current state of affairs. These audits focus on evaluating risk from four perspectives:
- External Attack Surface - Measuring the vulnerabilities that exist and are publicly exposed, allowing attackers to discover and exploit data and technologies over the internet
- Compromise - Measuring the ability to infiltrate and share malicious content within an organization
- Lateral Propagation - Measuring the exposure of applications and data that occupy the same network that attackers can discover after a successful breach.
- Data Loss - Understanding what sensitive organizational data is at risk of being stolen and exploited and assessing the security of internal data-sharing practices
These four risk elements should be monitored and presented to boards in dashboard form that allows for full transparency of the status quo and trends over time.
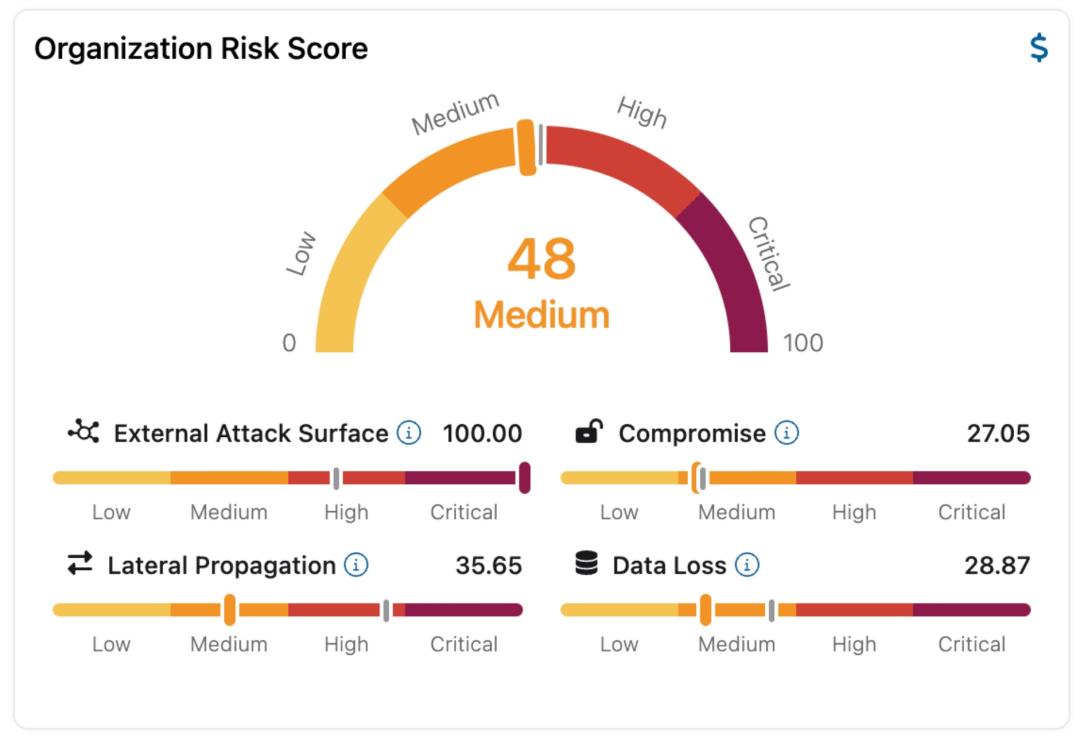
Once the assessment is done, board members should then establish goals and benchmark the organization's progress over time. Any critical negative change in the score for these four areas should be addressed as a high priority for management.
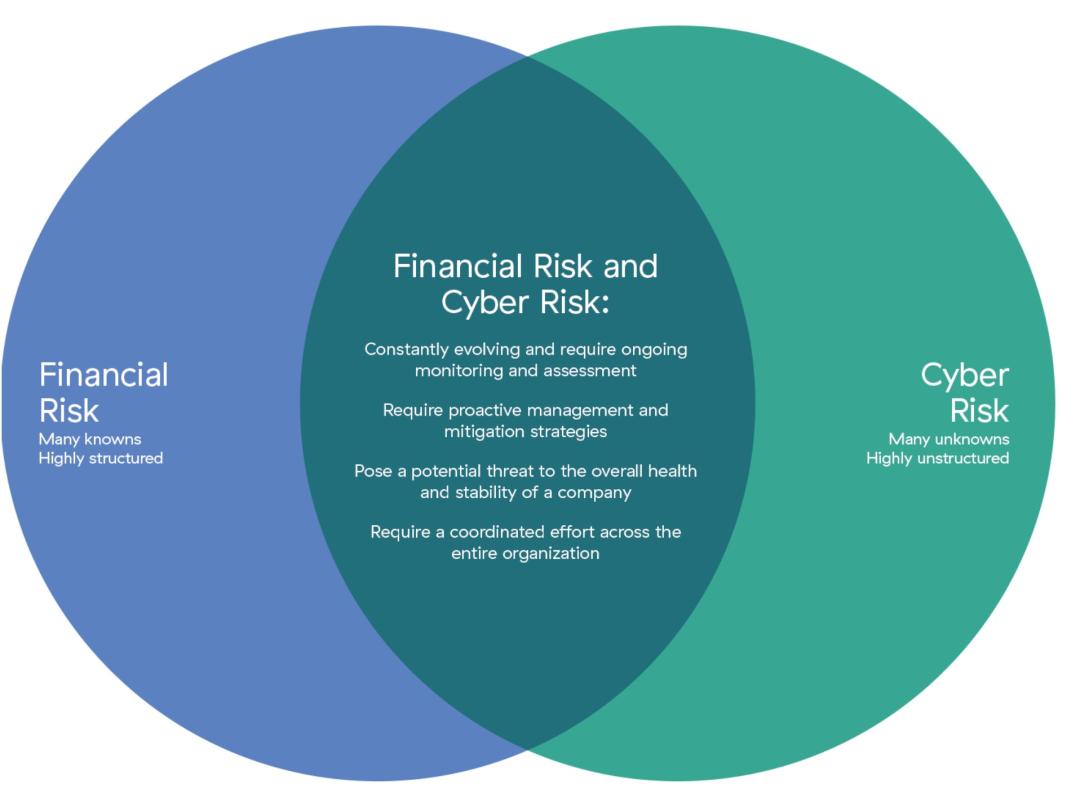
Most boards are already attuned to measuring financial risk as part of their fiduciary responsibility. There are similarities and differences between financial and cyber risk. While financial risk is structured with many knowns, cyber risk entails many unknowns and is highly unstructured, but both require a coordinated effort across the organization.
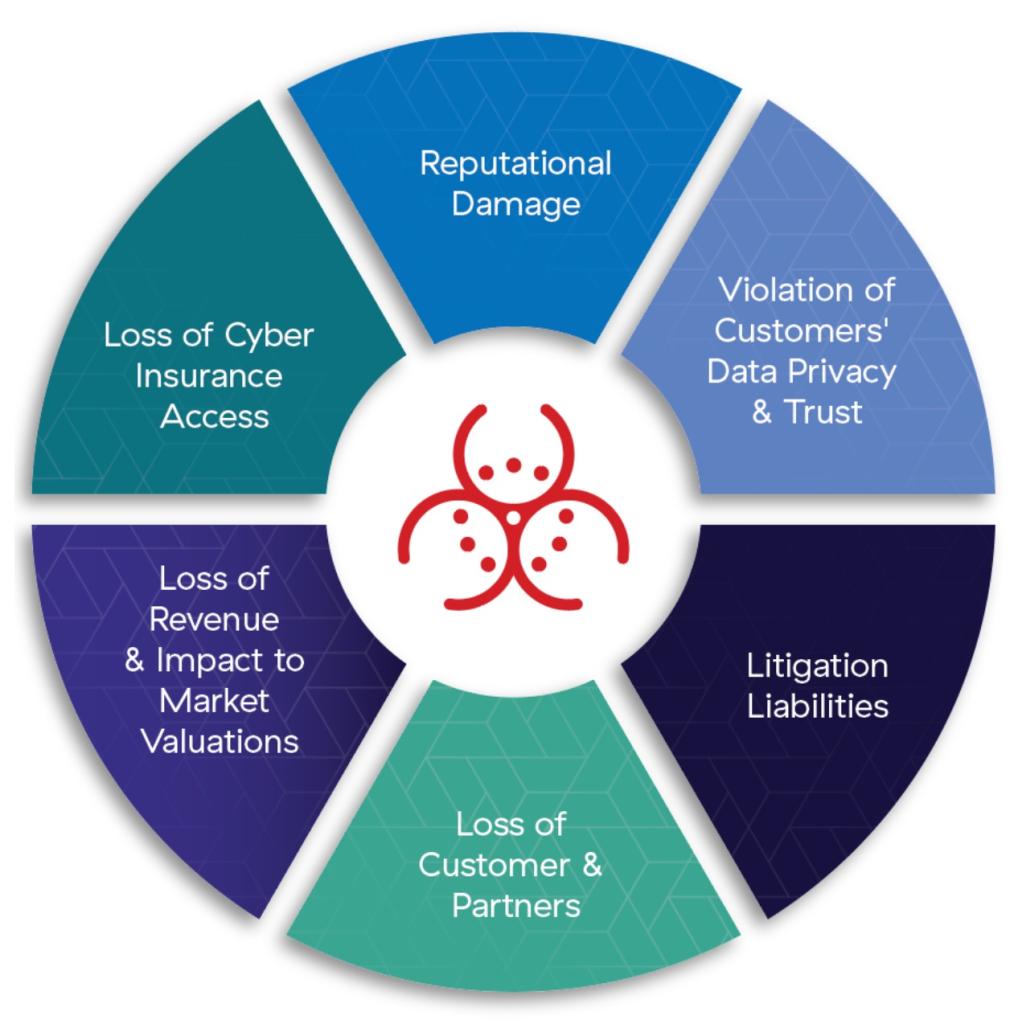
Malicious actions lead to a number of business implications, including unexpected financial losses, operational disruption, and at the very worst case force a company to go out of business.
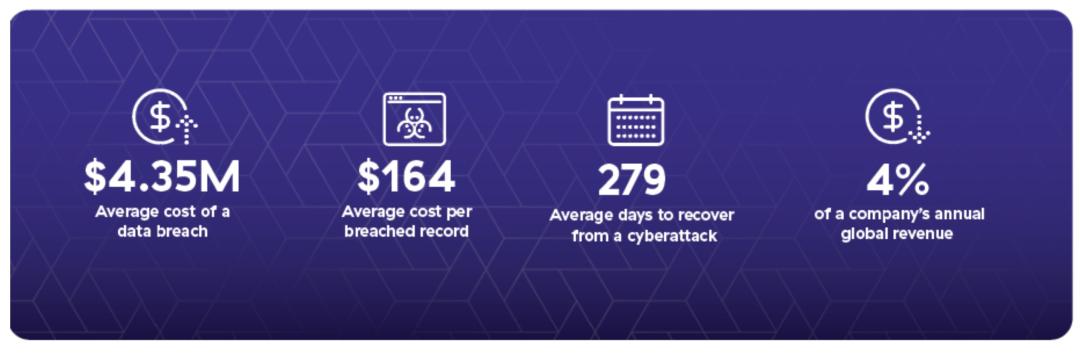
Cyberattacks threaten the financial stability of the company, and this makes them a shared concern and responsibility for all employees and stakeholders. The following sources offer a rough starting point for formulating your cyber breach loss estimations:
- Average cost of a data breach: $4.35 million
- Average cost per breached record: $164
- Average days to recover from cyberattack: 279 days
- Fine for a serious privacy violation: up to 4% of a company’s annual global revenues
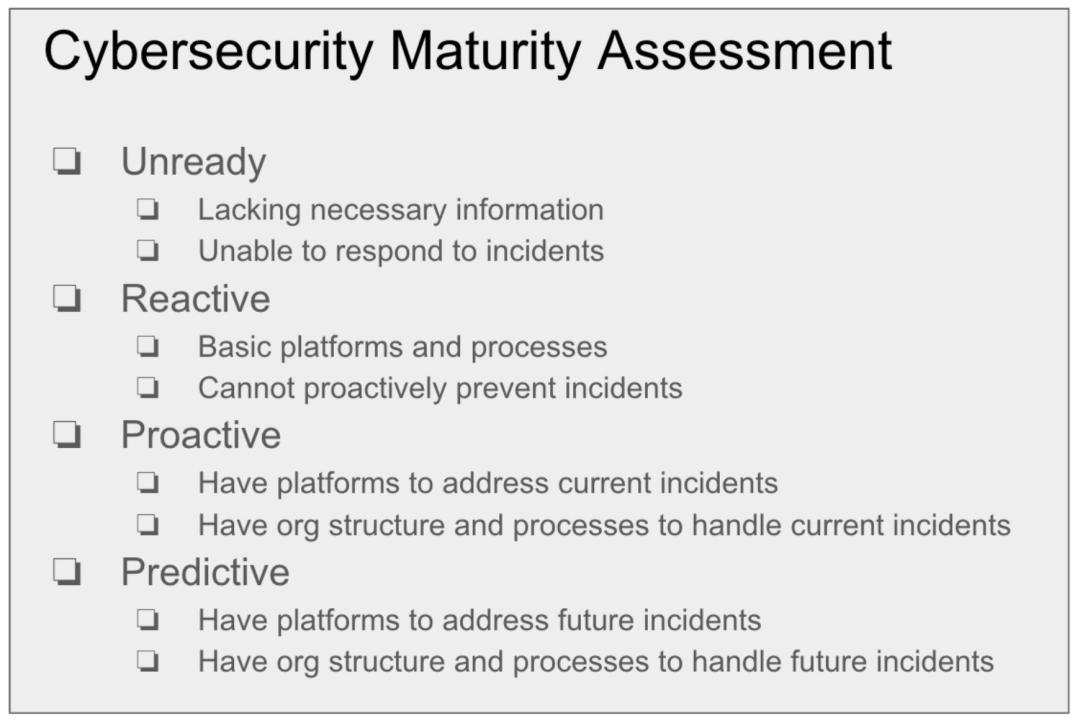
Another important step, in addition to conveying the gravity of cyber risk, is advising on how your organization responds to cyber incidents. Do you have a cyber risk management plan with strategies for preventing, detecting, and responding to cyber threats? You can use a cybersecurity maturity model to rate your current state of affairs as unready, reactive, proactive, or predictive. Note that most organizations today would rate themselves as unready or reactive. Also note that NIST also provides a Cyber Risk Scoring framework.
In summary
- Convey cyber risk posture by describing the exposed attack surface, potential attackers, existing policies/controls, the ability of attackers to move within systems, location/accessibility of sensitive data, and monitoring.
- Third-party audits of external attack surface, internal compromise, lateral propagation, and data loss provide an independent lens.
- Couple cyber risk assessment with financial impact analysis, using the cost of breaches and fines as a starting point.
- Determine cyber incident response maturity using a model like unready, reactive, proactive, or predictive. Most organizations are unready or reactive.
- Cyber risk is a shared concern for all employees and stakeholders given threats to company stability. The board should be provided full and current transparency on cyber risk status and trends.
This is part three of a series of posts dedicated to helping CXOs understand and excel in their board-level interactions. The next installment will cover explaining cyber risk controls to board members.
What to read next
Recommended


