
Apr 18, 2023
As the CIO of NOV, my job is to ensure IT infrastructure and security enable our business to power the people who power the world. Over the last several years, I led a secure digital transformation that made NOV more agile and adaptable. Here's how.
As the CIO of NOV, my job is to ensure that IT infrastructure and security enable our business to power the people who power the world. By this, I mean our 27,000 employees across 60 countries working with thousands of partners, suppliers, and customers. They all require secure, reliable technology anytime, anywhere, on almost any device–the same reliability we expect when accessing electricity and water. Over the last several years, I led a secure digital transformation that made NOV more agile and adaptable to challenges.
A transformation to cloud and zero trust
Like many enterprises, we had a legacy IT environment with data centers, hundreds of branch offices, factories, and OT systems, connected via a hub-and-spoke network. We used a castle-and-moat security model with ever-expanding layers of security appliances to address each new threat vector. We relied on multiple VPN technologies for remote access. It was expensive and not flexible enough to support our increasingly mobile and dynamic business.
I needed to reduce costs, improve security, and make life easier for our users and IT administrators. I needed our systems to work all the time, aka gain resiliency. It had to be a win across all these goals, so we set two main priorities.
First, be “cloud smart” and take advantage of where it can help. I had heard way too many horror stories of “cloud first” mass migrations causing extreme cost overruns and business-crippling outages. We had to be smart and determine where the cloud could add value and drive out cost. Our approach had to be evergreen, not replacing one legacy tech debt with new tech debt.
Second, transform our networks and security thinking. Focus on the internet first. Our global MPLS network was excessively expensive, and our old security appliances needed a multimillion-dollar upgrade. Most of our internet traffic was encrypted, which we could not see. The bad guys hid in that traffic, compromising our users and moving laterally to access high-value targets. Next, move toward zero trust. We wanted to follow the maxim “never trust, always verify,” which we later learned was a zero trust architecture. This meant enforcing access policies based on multiple contexts–user's role, location, device posture, and the applications they can access.
As we say in Texas, “We might need a new horse.” Sometimes your old horse can’t adapt, and you need a new one. You love and find comfort in the old steed, but it can’t take you where you need to go next. Our existing technology vendors and channel partners proposed we buy more of what they were already selling us.“Don’t change,” they said. “Double down with what got you into this predicament.” Maybe they could help us win with a couple of goals, but not all. We would need to explore new horizons.
Our phased transformation journey
A successful digital transformation is a journey that doesn’t happen simultaneously. Progress came in increments, with each experience influencing successive phases:
Phase 1 – A collaboration solution
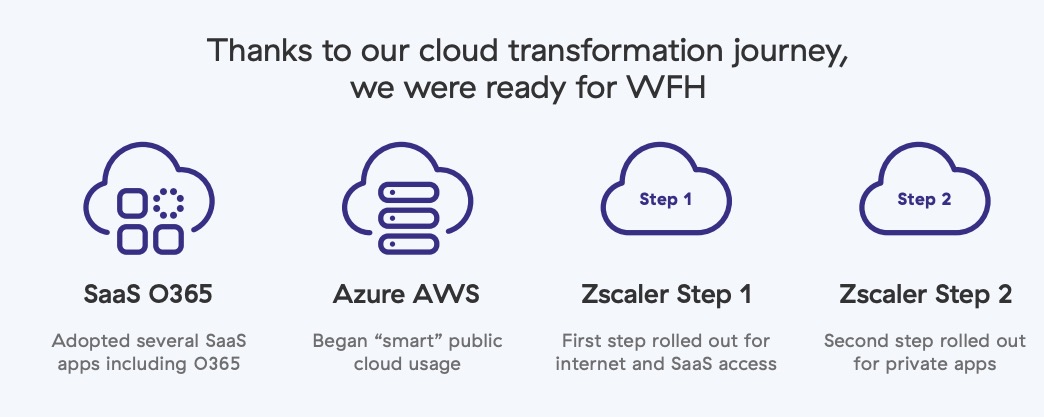
During phase one, we adopted Microsoft Office 365. Collaboration and sharing of large datasets were painful, and we had outgrown our email system. We began rapidly migrating hundreds of terabytes of emails, files, SharePoint data, etc. This delivered immediate productivity value and business flexibility, even with our legacy network and security appliances still in place.
Phase 2 – Secure access to the internet and SaaS from anywhere
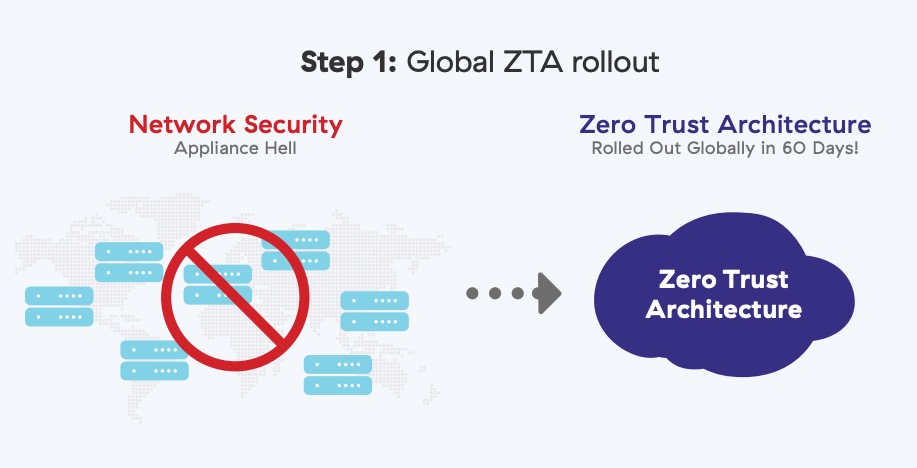
Phase two had three steps. First, we enabled secure access to the internet and SaaS applications through the Zscaler Zero Trust Exchange. This was deployed on our existing legacy MPLS Global Network in 60 days for the entire company while phase one was executing. It immediately gave us resiliency and increased our security posture.
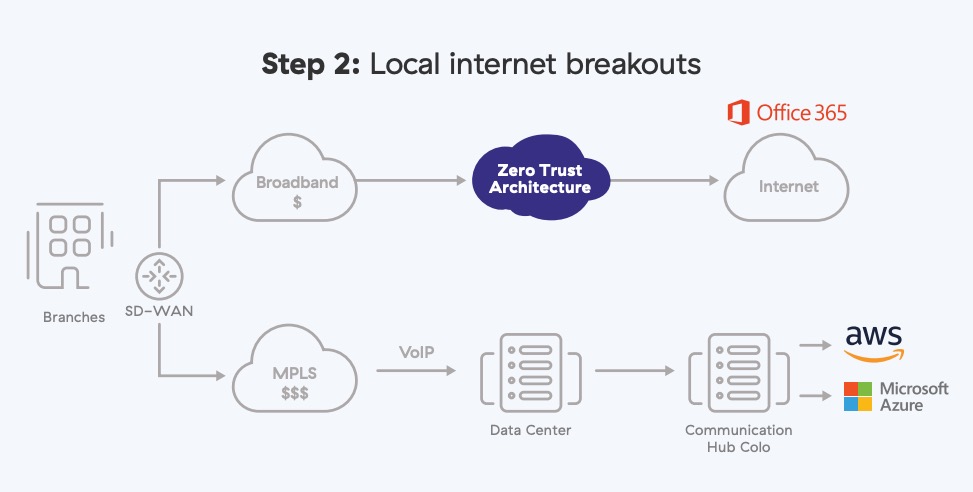
The next step of phase two was to eliminate our MPLS networks and provide local internet breakouts. This resulted in millions of dollars in savings, faster connections, and direct access through SaaS applications such as Office 365 by eliminating traffic through a centralized hub.
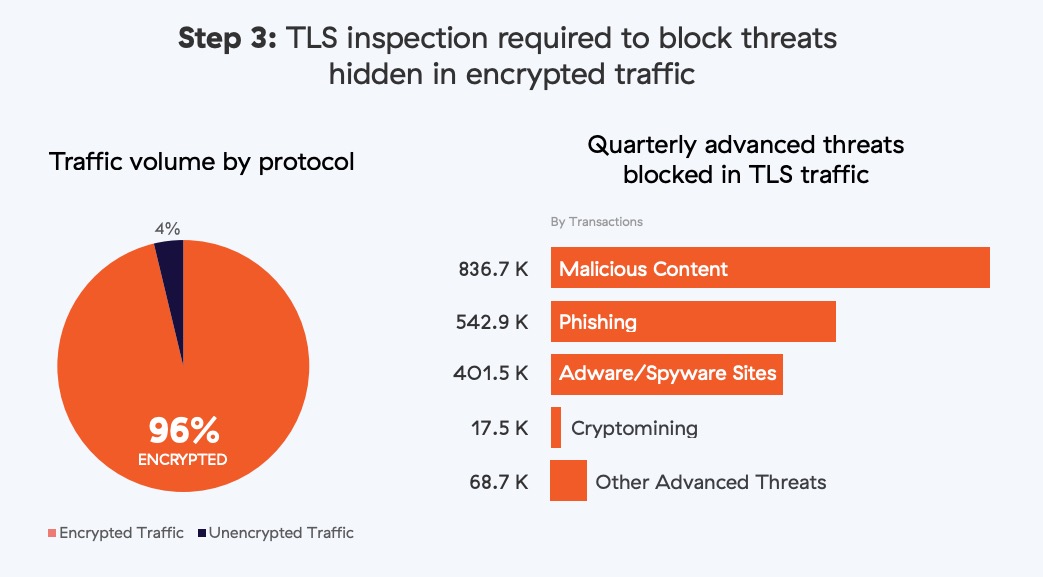
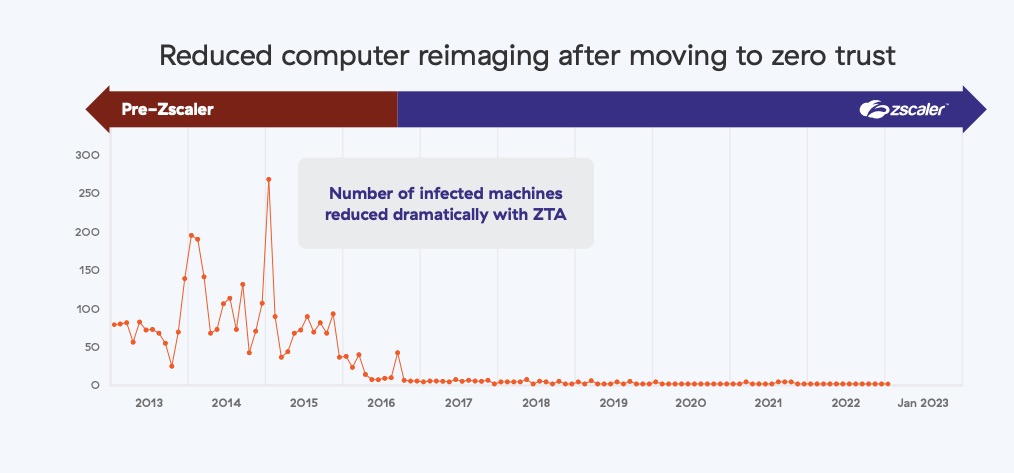
The final step involved turning on TLS inspection capabilities to detect and block threats hidden in encrypted traffic. This significantly improved our risk posture.
Phase 3 – VPN replacement with zero trust security
In phase three, we replaced multiple remote access VPN solutions and provided fast and secure zero trust network access (ZTNA) to private apps using Zscaler Private Access. This allowed NOV employees and our third-party contractors access to 7,500 NOV applications in multiple data centers and public cloud regions directly over the internet. We did this a few years before the COVID-19 lockdown, so we were fully prepared to support our users' need to work from home without interruption.
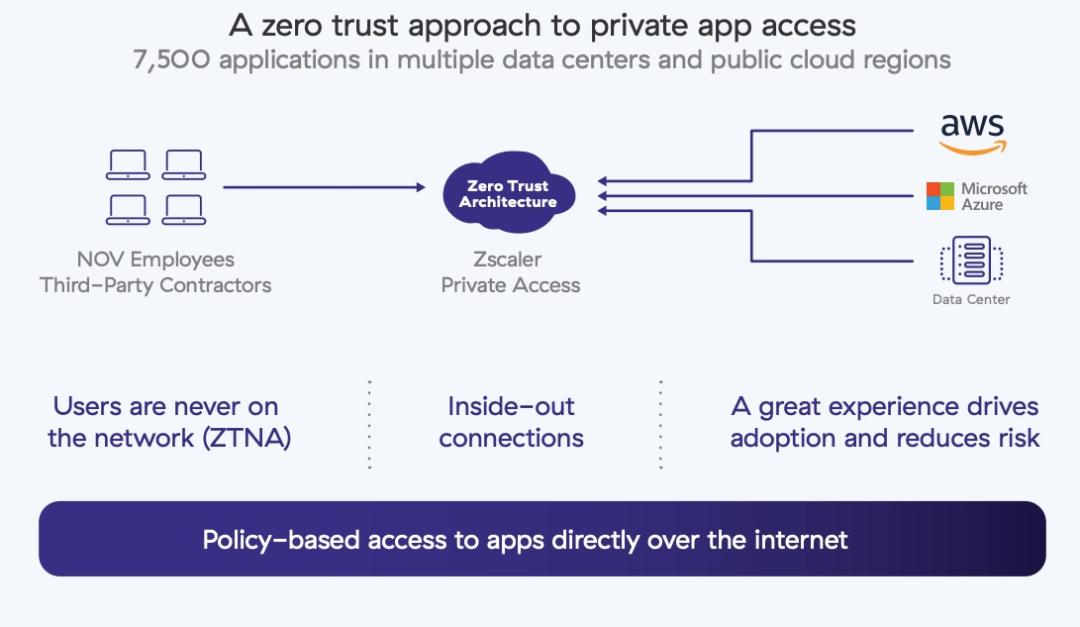
Phase 4 – Move private apps to the cloud and consolidate data centers
Phase four required two steps. First, we moved our critical customer-facing applications into AWS. Then we moved our many regional data centers, which lacked the scale needed to operate efficiently, to Azure.
Phase 5 – Zero trust connectivity for offices
This upcoming phase of our transformation will be the most exciting. Its genesis arose from a question collectively asked by all of our users working remotely from home. If we all can work fine remotely in a zero trust manner, why can’t we do that at our facilities? Do we even need the network? How can we provide ZTNA to devices without identity such as printers, barcode scanner guns, time clocks, IoT, and OT systems? Legacy networks are a security risk due to a lack of identity, and we are going to replace it with zero trust access! With zero trust connectivity, our offices will become like an internet café, and we will no longer extend our corporate network to every office. This step is critical for eliminating lateral threat movement.
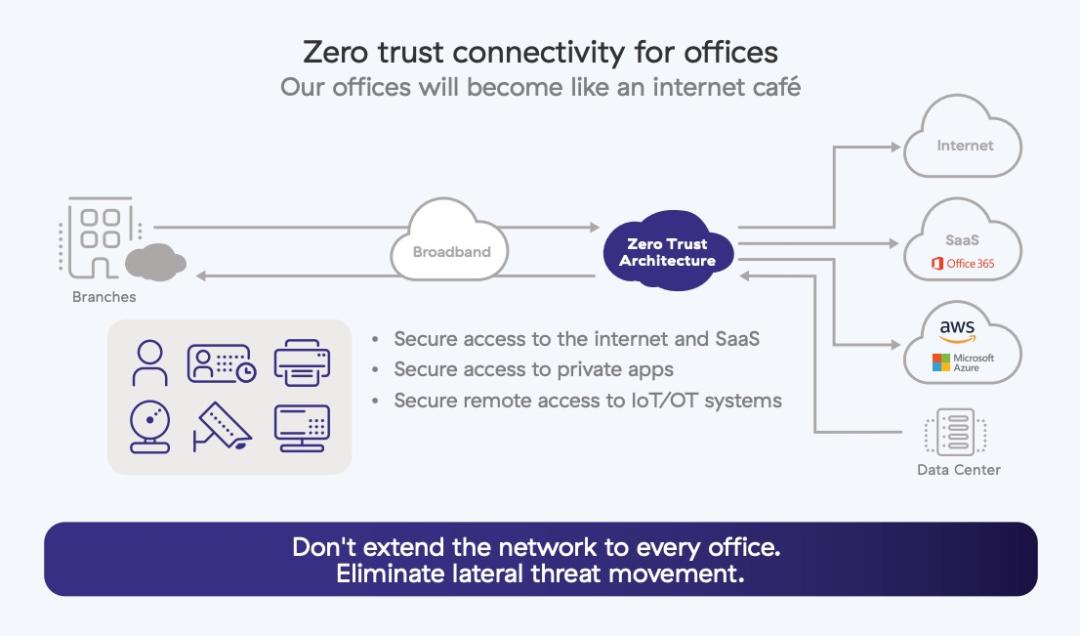
Many of these phases are complete, and some are ongoing due to contractual commitments. Phase five is just getting started. The journey hasn’t always been a straight line, but I can proudly say that we are overachieving our goals.
Here are some of the lessons I learned from our transformation journey:
- Moving from legacy networks and security to zero trust is an architectural change. As it requires cultural and mindset changes, we identified forward-thinking leaders early on in our journey who helped us drive this initiative.
- Choose an integrated platform that secures not only users but also workloads and IoT/OT systems.
- Select a partner who has a highly reliable security cloud. Zscaler’s more than 10 years of operational experience in managing the largest security cloud has delivered us high-performance service without disrupting our business.
- Don’t boil the ocean–just get started. Look for quick, small wins that are easily achieved to drive organizational acceptance of this journey.
Our secure digital transformation has made NOV business a lot more agile. It has saved millions of dollars, improved user productivity, and reduced our cyber risk.
What to read next
Secure digital transformation is business transformation [podcast]
NOV’s digital transformation journey, powered by the Zscaler Zero Trust Exchange [video]
Recommended
