
Oct 28, 2022
Element #7 of the Seven Elements of Highly Successful Zero Trust Architecture explores the enforcement actions that can be taken as a result of data gathered during the first six elements.
Editor’s note: Element #7 of the Seven Elements of Highly Successful Zero Trust Architecture explores the enforcement actions that can be taken as a result of data gathered during the first six elements.
Following the Verify and Control stages, and armed with an understanding of dynamic risk assessments, we arrive at the point of enforcement. Enforcement is not centralized on a network of dedicated equipment, as is often the case with traditional security solutions. Authorization decisions made in Element 1 and the assessments in Element 2 influence enforcement in our current stage.
Policy enforcement must be constantly and uniformly applied. This is only possible when policy remains the same and is applied equally regardless of the location of the enforcement point.
Technology and architecture considerations
Zero trust allows us to start at zero. Access is denied to anyone or anything as an initial condition. This means no services, FQDNs, or IPs are exposed or can be discovered. An initiator can only connect to their requested destination as befitting their access criteria.
This type of invisibility-until-permission is only possible if policy is enforced independent of the network and, most importantly, if the initiator and the destination are abstracted from one another.
Policy enforcement must take into consideration all previously validated qualities:
Reduce visibility, reduce attack surface
Traditional, network-based solutions connect initiators to a shared network, either physically on a local network or logically via a virtual private network (VPN). This extends the network to wherever a user is connected, and control is applied at the network layer.
Anyone on that network can see all other nodes. A control, such as a firewall, can minimize some of the attack surface, but if access is needed to a service, there still needs to be an open path through the controls. This is similar to a figure standing on a street who is able to see each house, approach it, and test if their key works in the door.

A zero trust enforcement policy allows for various controls to be enforced based on the following formula:
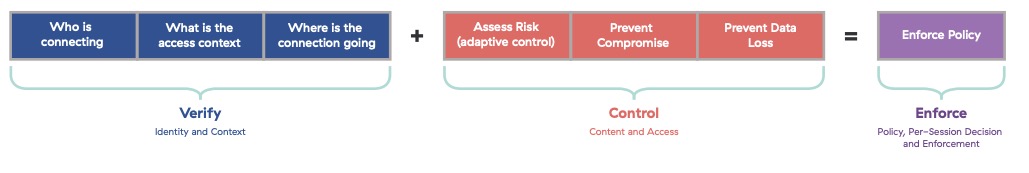
Enforcement in zero trust scenarios is not simply limited to the two options of “conditional allow” or “conditional block.” Its controls are at the application layer, not at the network layer as with legacy network control solutions.

Policy Enforcement Actions
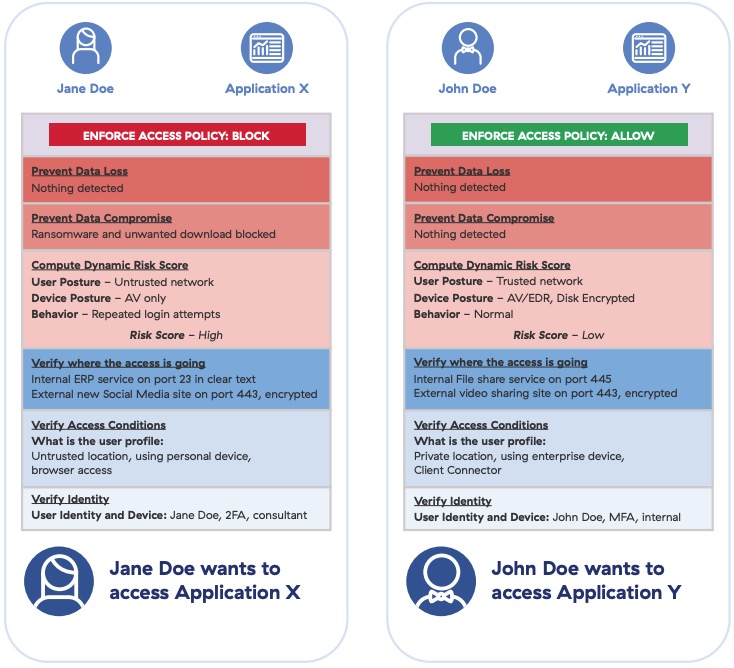
Following any decision, enforcement takes on one of the following actions, either conditional allow or conditional block.
- Conditional Allow – Access is granted to the requested application not as a blind allow-and-connect, but with the ability to deliver additional controls, such as isolation, inspection, and warnings.
- Conditional Block – If conditions of an access request are flagged in Elements 1-6, access is blocked. Block controls can be called at any time during Elements 1-6 if an initiator fails one of the tests. For example, access would be blocked if an authorized user and device are validated, but then malware is downloaded.
Zero trust progress report
Upon the completion of the policy enforcement phase:
- All elements will have been evaluated
- Assessments are completed
- Scores are assigned
- Access has been conditionally allowed or conditionally blocked
Should access be granted, then the last step for access is the ability to get traffic to the correct destination application.
Download the Seven Elements of Highly Successful Zero Trust Architecture eBook and stay tuned for more installments of our accompanying commentary
Recommended

