
Dec 14, 2023
Managing cyber risk is a continuous journey that requires fine-tuning. Moving towards zero trust is a big step toward the minimization of cyber risk, but it is not a one-and-done process.
Managing cyber risk is a continuous journey that requires fine-tuning as the organization changes, the threat landscape evolves, business needs change, etc. Moving towards zero trust is a big step toward the minimization of cyber risk, but it is not a one-and-done process.
Board members should continuously reassess risk, influence technology and non-technology factors, overcome obstacles and finally, measure the impact of change. And, once your organization has started its zero trust journey, it is time to quantify the benefits you have achieved, specifically around cyber risk mitigation.
The most important metrics will be the ones that your organization can cite to justify launching risk mitigation strategies. Specific goals will vary among businesses, but there are a few common metrics that reliably provide a good starting point. These include measurements related to risk reduction, technology cost reduction, and operational efficiencies.
Measuring risk mitigation gains is accomplished by comparing the effectiveness and coverage of your former security posture to current ones. Look at the in-depth risk assessment created at the beginning of your transformation and evaluate where each item stands now. With the movement toward zero trust, your organization will have robust protections against ransomware, phishing attacks, data loss, and insider threats. Each of these should be examined and quantified when estimating positive returns.
It is important not to overlook the severe costs that are avoided every day the organization remains secure. Consider the non-financial losses borne by institutions that have suffered a public data breach. These include the initial blow to brand reputation, loss of customer trust, impaired productivity, and data-related damages. For example, if important intellectual property is stolen, your organization could completely lose its competitive advantage. If your clientele’s personal data is stolen, your customer base may never recover.
Estimating the costs of avoiding a breach is an imperfect science. However, some factors to consider are the cost-per-hour of malicious cyber events, loss of future business, brand damage, and customer churn. Add this estimate to the known, average costs of successful cyberattacks for an idea of how much you’ve saved by avoiding a breach.
It is also worth noting that successful cyberattacks can result in executives considering leaving their positions (almost a third of all IT cybersecurity leaders, based on research from 2022). For small and mid-sized businesses (SMBs) the effects of a cyberattack are even more devastating. Forbes reports that 60% of small companies go out of business within six months of a successful cyberattack.
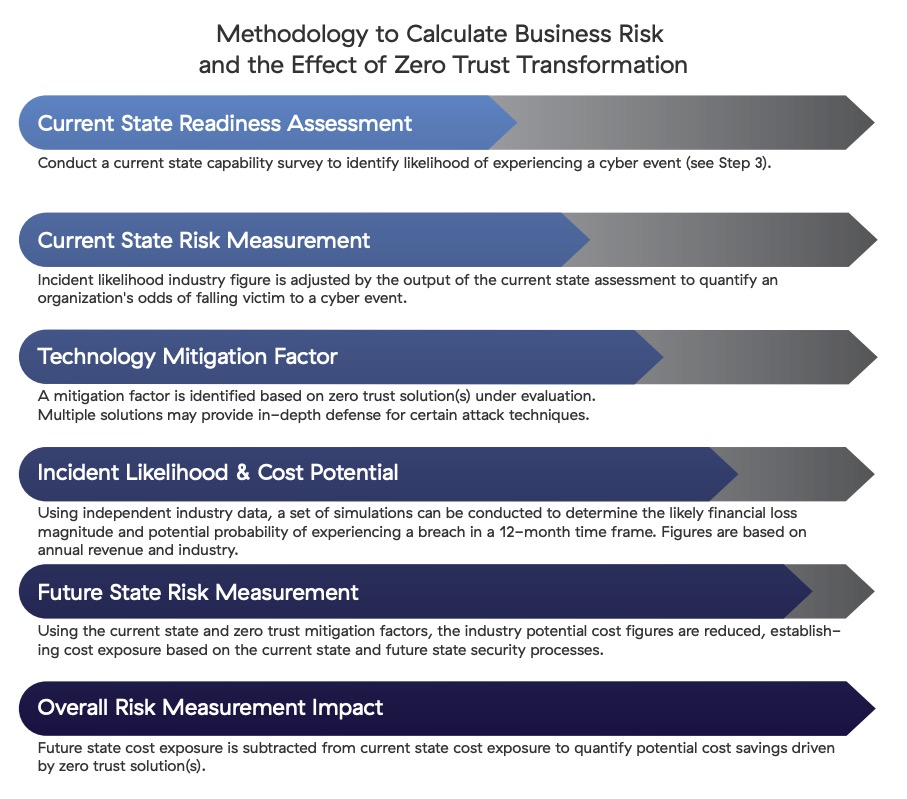
Calculating the financial impact of cyber risk and benefits of zero trust migration
Third parties often use a six-step methodology to calculate business risk and the effect of zero trust transformation:
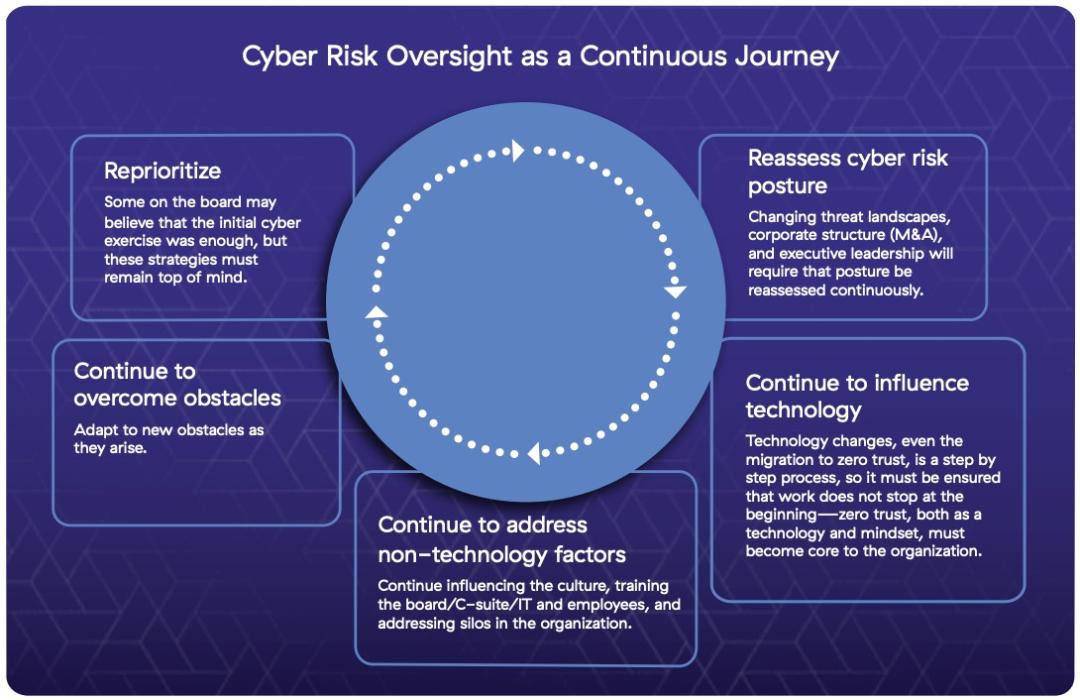
Since the strategies outlined here are not taken in one fell swoop, it is important to view cyber risk mitigation as a continuous journey:
In summary:
- Organizations must conduct continuous risk assessments to identify evolving threats as the organization changes, comparing the risk evolution back to initial assessments.
- Organizations can quantify the benefits of zero trust migration through methods of risk reduction, cost savings, and operational efficiencies. Estimated costs avoided by preventing breaches can be a key metric for boards to understand.
- Boards should seek to have data provided to them that calculates the cyber risk financial impact using simulations based on the likelihood of cyber events, potential losses, and risk mitigation from zero trust.
- Boards should encourage the reprioritization of cyber strategies, the reassessment of risk posture, continually influence cyber importance within technology and overall culture, and encourage the ability to adapt to new obstacles.
- Managing cyber risk is an ongoing process for organizations requiring repetition of assessment, implementation, and measurement of zero trust initiatives.
This is the final installment of a series of posts dedicated to helping CXOs and boards address cyber risk. Download Cybersecurity: Seven Steps for Boards of Directors to read the complete series.
What to read next
Briefing the board on cyber risk maturity
6 common challenges boards face overseeing cybersecurity change
Recommended


