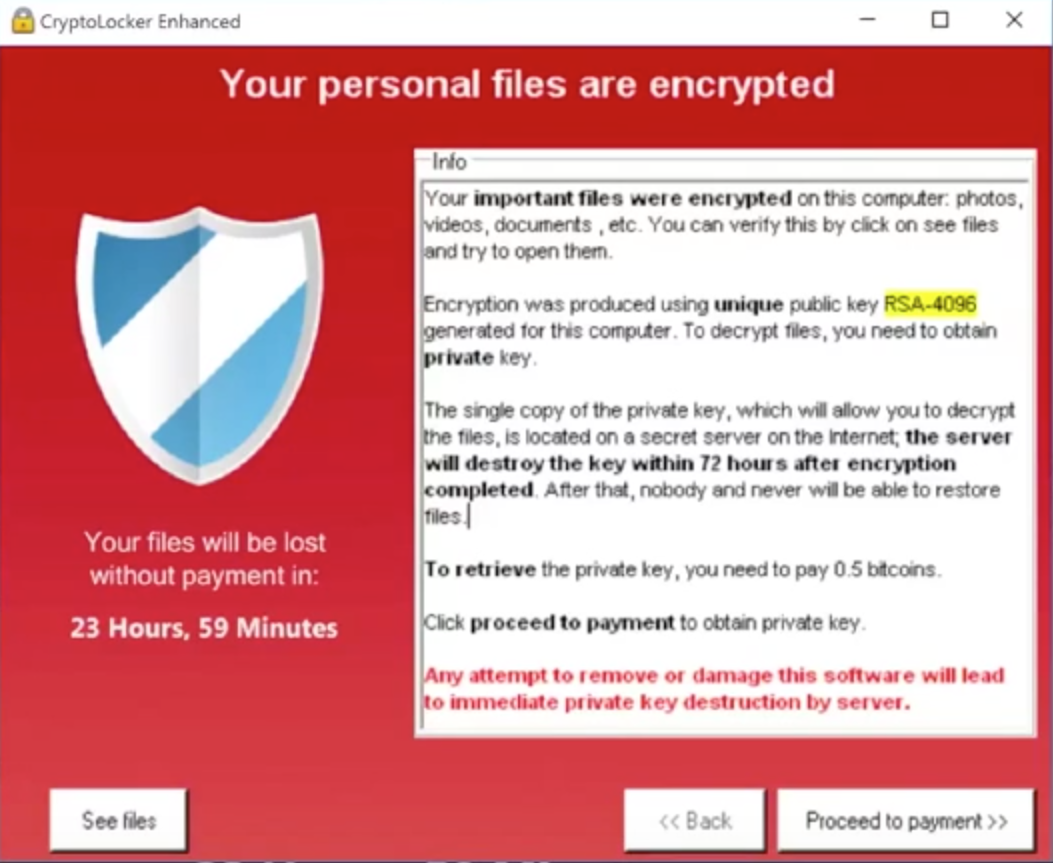
Ransomware has been around for more than 25 years, starting with the AIDS Trojan in 1989 and evolving into more sophisticated trojans, such Gpcode and ROJ.RANSOM.A, in the middle of the last decade. After that, the use of ransomware slowed until 2013, when it made a big comeback as the malware predator of choice with CryptoLocker. In all cases the modus operandi is the same: malware is downloaded onto a computer (desktop or server), after which it restricts access to the machine or encrypts the files on the system’s hard drive and only enables the decryption of these files after the owner has paid a “ransom.” Historically, the perpetrators have demanded a relatively small amount in order to compel people to pay the ransom — quickly.
The cost of infection is at an all-time high
When a formula works, people use it. Because ransomware has been so effective, so it’s no surprise that cybercriminals have expanded its use and broadened their “market” by setting their sights on business. According to the CyberThreat Alliance, a specific strain of ransomware, CryptoWall V3, was responsible for $325 million in damages stemming from almost 407,000 infections involving over 4,000 malware samples. And 2016 is looking even more lucrative for the attackers and dangerous for the rest of us. According to an FBI source reported by CNN, cybercriminals collected $209 million from ransoms in just the first three months of 2016.
The best defense is a strong defense
 At Zscaler, we believe that the best defense is to follow best practices to avoid the threat and deploy strong protection to stop it. Since ransomware is always propagated as an executable file, the best protection is to deploy sandboxing technology. Zscaler’s cloud sandbox was recently tested by AV-TEST and found to detect and protect against 99.91 percent of all malicious threats.
At Zscaler, we believe that the best defense is to follow best practices to avoid the threat and deploy strong protection to stop it. Since ransomware is always propagated as an executable file, the best protection is to deploy sandboxing technology. Zscaler’s cloud sandbox was recently tested by AV-TEST and found to detect and protect against 99.91 percent of all malicious threats.
We’ve put together a set of resources to help you learn about ransomware, take the right precautions, and deploy the best defenses:
- Visit our ransomware section, which gives you access to a variety of resources
- Read our threat research on the various strains of ransomware that we have analyzed in our lab
- Check your security posture to see how well protected you are





