The past few weeks I noticed a handful of "free access" / "open for free access" malware binary executables. There was some information in the open source about this, but not much piecing the entire picture together - in fact, it appears that there could be a linkage to the Koobface gang for this. Read on for more details...
Of late the binaries have mostly been named "Open.Me.For.free.Access1.1.exe"
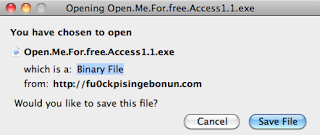
For example, (all live at the moment, not blocked through Google SafeBrowsing)
- fu0ckpisingebonun.com/Open.Me.For.free.Access1.1.exe
- g1rlyuoung.com/Open.Me.For.free.Access1.1.exe
- 1000sweeties.com/Open.Me.For.free.Access1.1.exe
- www.baabbeesss.com/Open.Me.For.free.Access1.1.exe
- 69poses4u.com/Open.Me.For.free.Access1.1.exe
 There have been a number of other domains registered for this campaign. All sites lure the victims through porn, and are advertised via web and email spam. Clicking on any of the links in the page entices the user to download the binary. Fortunately, the binary remains static in each run. In this particular example the binary has ok A/V detection, V/T results 27/42, MD5: 76553a8e67d22c40fabd52cb57d30ea4
There have been a number of other domains registered for this campaign. All sites lure the victims through porn, and are advertised via web and email spam. Clicking on any of the links in the page entices the user to download the binary. Fortunately, the binary remains static in each run. In this particular example the binary has ok A/V detection, V/T results 27/42, MD5: 76553a8e67d22c40fabd52cb57d30ea4
The malware uses a browser helper object (BHO) to automatically access and inject content into the victims browser. The malware accesses and injects content into the victim's browser from adult site affiliates, for example, streamray.com and cams.com.

In a previous blog post, I mention the Partnerka (Russian slang for the affiliate networks). These affiliate programs provide a revenue stream for spammers, SEOers, and malware authors alike based on pay-per-etc.,etc. (traffic volumes, clicks, purchases, installs, credential / sign-up). In other words, the malware from this post is being used to monetize adult site affiliate programs such as the Cams / Streamray affiliate.
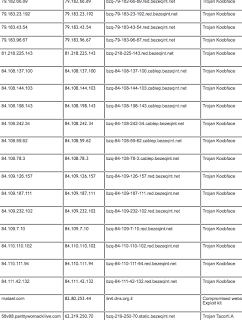
Variants of the malware from this post have been classified as "Trojan Tacorti" by some vendors. Here is an example of a ThreatExpert report from a previous Tacorti run -- the possible country of origin from the artifact is identified as Russia.
The resolving IP for the above Tacorti domains is: 62.219.250.70 with nameservers on the same IP block:
Name Server : NS1.CUM4ME.TV (62.219.250.67)
Name Server : NS2.CUM4ME.TV (62.219.250.67)
All of the Tacorti domains were registered through:
Registrar: GAL COMMUNICATION (COMMUNIGAL) LTD.
With private whois info, contact to unmask:
[email protected]
The nameserver domain was registered through:
Registrar: REGISTER.COM, INC.
With private whois info through Domain Discreet
(I sent notification to the appropriate parties for the nameserver domain)
IP Info:
70.250.219.62.in-addr.arpa. 86400 IN PTR bzq-219-250-70.static.bezeqint.net.
67.250.219.62.in-addr.arpa. 86400 IN PTR bzq-219-250-67.static.bezeqint.net.
inetnum: 62.219.250.64 - 62.219.250.127
netname: WADACH-WATZPI-LTD
person: Zehavit Vigder
address: bezeq-international
address: 40 hashacham
address: petach tikva 49170 Israel
phone: +972 1 800800110
fax-no: +972 3 9203033
e-mail: [email protected]
route: 62.219.224.0/19
descr: BEZEQ-INTERNATIONAL
origin: AS8551
AS8551 is shown to be a fairly "dirty" AS, with a history of hosting Koobface malware, see malwareurl.com report. There is no conclusive evidence at present to link the Trojan Tacorti runs to the Koobface gang, but the modus operandi (MO) is similar to this gang (monetizing affiliate networks through malware infections ... and they have a history of porn / web cam / video as the social engineering lure for victims).