Bangalore's Metro Rail project website (Bangalore Metro Rail Corporation Limited), "bmrc.co.in" is compromised. Malicious obfuscated JavaScript has been injected into several pages. The obfuscated code contains an iFrame, which after execution, redirects users to a malicious website. This is typical behavior for a JavaScript Trojan. More information about this particular Trojan can be found in McAfee's description of threat JS/Exploit-Blacole.em. Lets look at some of the details of this particular infection.
Compromised Pages:
We have seen more than one page on this website that were found to be compromised. All of the compromised pages are infected with the same malicious JavaScript code.
hxxp://bmrc.co.in
hxxp://bmrc.co.in/careers.htm
hxxp://bmrc.co.in/Network.htm
Malicious Code:
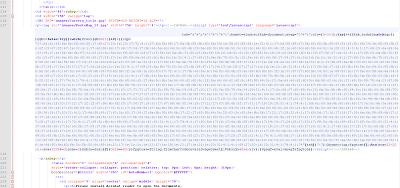
The injected code is obfuscated JavaScript as seen below.
De-obfuscation of the aforementioned JavaScript reveals the browser redirection process.
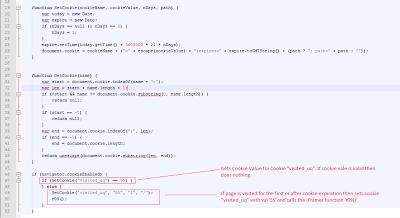
Cookie checking:
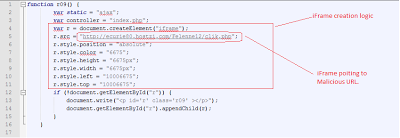
De-obfuscated JS checks a cookie value to determine if the page was loaded in the browser previously. If the code is being loaded for the first time, it then creates a cookie called "visited_uq" which is set with a value of "55" for one day with a path of '/'. It then calls function which creates an iFrame.
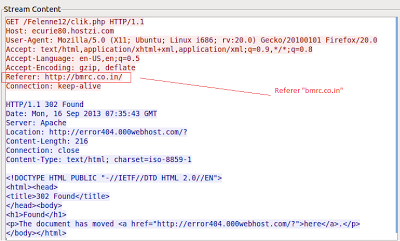
Network Trace
VT Report for "bmrc.co.in/careers.htm":
URL Scan: 8/39
File Scan: 18/47
At the moment, the redirection is no longer serving malicious code. The page ultimately resides at a free hosting service (000webhost.com) but appears to have been taken down. The page could however be revived at some point and the original vulnerability which led to the infection may still exist, so users are advised to avoid the BMRC website until this issue has been addressed. ThreatLabZ has informed BMRC about this infection.
Pradeep