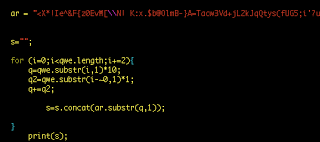
I posted a few of these mal-spam incidents on our Scrapbook blog ... this sort of mal-spam has been on-going, but there has been a recent uptick since early June. The NACHA, Federal Reserve, and now IRS mal-spam sites have all favored the MelbourneIT/Yahoo netblocks/domain services.
I posted a few of these mal-spam incidents on our Scrapbook blog ... this sort of mal-spam has been on-going, but there has been a recent uptick since early June. The NACHA, Federal Reserve, and now IRS mal-spam sites have all favored the MelbourneIT/Yahoo netblocks/domain services.
Blog da Zscaler
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
IRS, NACHA, Etc. Mal-spam
Esta postagem foi útil??
Aviso legal: este post no blog foi criado pela Zscaler apenas para fins informativos e é fornecido "no estado em que se encontra", sem quaisquer garantias de exatidão, integridade ou confiabilidade. A Zscaler não se responsabiliza por quaisquer erros, omissões ou por quaisquer ações tomadas com base nas informações fornecidas. Quaisquer sites ou recursos de terceiros vinculados neste post são fornecidos apenas para sua conveniência, e a Zscaler não se responsabiliza por seu conteúdo ou práticas. Todo o conteúdo está sujeito a alterações sem aviso prévio. Ao acessar este blog, você concorda com estes termos e reconhece que é de sua exclusiva responsabilidade verificar e utilizar as informações conforme apropriado para suas necessidades.
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Ao enviar o formulário, você concorda com nossa política de privacidade.