Some websites make it very hard, or even impossible, to use secure connections to protect their sessions. It has been exactly a month since Firesheep was released to demonstrate the problem of session side-jacking, but these websites are still not willing to do anything about this problem.
Here are some of these sites, all part of the list of domains monitored by Firesheep.
Amazon: no HTTPS for you!
It is just not possible to use https://www.amazon.com/! This address redirect users to http://www.amazon.com/.
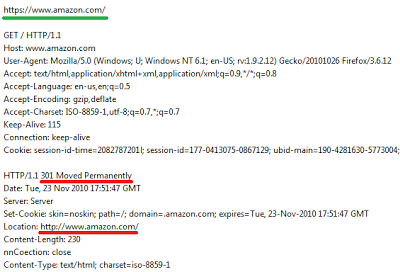 |
| Permanent redirection from HTTPS to HTTP |
To their credit, users must login again over HTTPS to make an order, but Amazon still provides plenty of information about their users: first name, last name, what they're interested in, full access to their shopping cart, etc.
Basecamphq.com: 37signals.com certificate
If you go to https://www.basecamphq.com/, you get a certificate for 37signals.com. This isnt very helpful for users not aware that BaseCamp is a product from the company 37Signals.
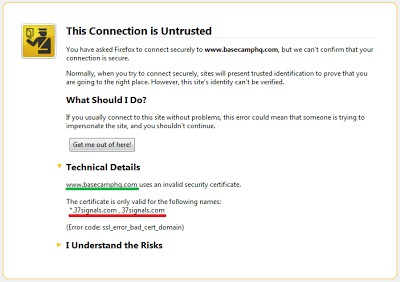 |
| SSL certificate valid for a very different domain name |
Facebook: hidden HTTP connection, HTTPS login fails
I logged into my Facebook account using https://www.facebook.com/. Out of the 10+ requests required to display my home page, one of them is done to http://www.facebook.com/ap.php. This request does carry all the cookie values needed to hijack my account. There is currently no way to surf Facebook safely.
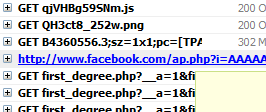 |
| Unsecure HTTP connection |
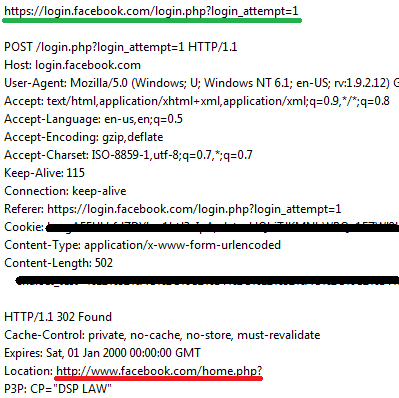 | |||
| Redirection from secure login page to unsecured home page |
Although Firesheep has made a lot of noise, and the issue of session side-jacking has now been widely reported on, even the major sites have not taken the necessary actions to protect their users. It is very sad to see sites such as Facebook, widely used and by a large and diverse audience, are still very insecure.
This was just a quick review of a few sites, I'm sure plenty of other sites have the same weaknesses.
Happy Thanksgiving!
-- Julien




