CXO REvolutionaries
Amplifying the voices of real-world digital and zero trust pioneers
A Forum for Enterprise Transformation
CXO REvolutionaries
Meet successful cloud-innovators solving difficult enterprise challenges, securely.
Events
Attend invite-only events, roundtables, and panels with CXO pioneers driving secure digital transformation initiatives.
Insights
Access on-point content from innovative leaders with crucial insights into how enterprises achieve agility, resiliency, and security.
Connect
Join a community of C-level executives pushing enterprises into a cloud- and mobile-first world.
Meet REvolutionary CXO Leaders
These IT leaders are bringing a new wave of cloud- and mobile-first technology to major enterprises globally.
Attend CXO-Only Events
Learn from IT revolutionaries, digital transformation pioneers, and thought leaders at
these invitation-only events.
Access Insightful Thought Leadership
An executive-level resource for actionable, practical, and real-world examples for creating enterprise change through digital transformation initiatives.
Don't Miss
In the News...
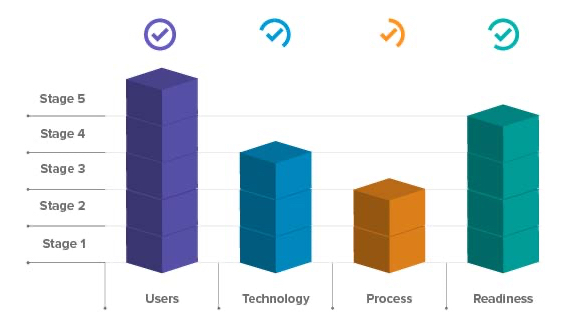
Evaluate your digital transformation progress
This evaluation can steer your organization to the next stage of its digital transformation journey for users, technology, process, and readiness. Find out where your organization needs to go.