/ ¿Qué es DevSecOps?
¿Qué es DevSecOps?
DevOps vs. DevSecOps
Tanto DevOps como DevSecOps utilizan automatización y procesos continuos para establecer ciclos de desarrollo colaborativo. DevSecOps surgió como respuesta a las críticas de que DevOps no enfatizaba adecuadamente la ciberseguridad.
En la metodología DevOps, los desarrolladores y los equipos de operaciones de TI trabajan juntos para crear un marco de implementación ágil y optimizado. DevSecOps tiene como objetivo automatizar tareas de seguridad clave mediante la incorporación de controles y procesos de seguridad en el flujo de trabajo de DevOps. Las prácticas de DevSecOps amplían la cultura DevOps de responsabilidad compartida para incluir prácticas de seguridad.
¿Por qué es importante DevSecOps?
DevSecOps, abreviatura de desarrollo, seguridad y operaciones, ayuda a las empresas a integrar la seguridad en el desarrollo de aplicaciones implementando controles de seguridad en cada etapa del ciclo de vida del desarrollo. Detectar y solucionar problemas de seguridad lo antes posible ayuda a ahorrar costes, evitar repeticiones de trabajos y reducir riesgos al garantizar que las cargas de trabajo en la nube sean seguras antes de implementarlas.
¿Cuál es el propósito de DevSecOps?
DevSecOps ayuda a optimizar los entornos de desarrollo modernos y respalda la transformación digital segura. Las empresas están adoptando servicios nativos de la nube, empleando automatización y perfeccionando procesos de desarrollo iterativos. Los desarrolladores a menudo confían en código reutilizable y componentes de código abierto. Además de eso, los datos confidenciales se han vuelto altamente regulados.
Junto con el cambiante panorama de amenazas, toda esta complejidad ejerce presión sobre los equipos de seguridad, que deben hacer frente a conocimientos, recursos y herramientas limitados.
DevSecOps impulsa prácticas de seguridad más eficientes, ofreciendo una visibilidad profunda enriquecida con contexto completo e integración en las herramientas y procesos de los desarrolladores, junto con seguridad unificada en toda la infraestructura de la nube, datos confidenciales y aplicaciones.
Básicamente, los procesos de DevSecOps ayudan a entregar software seguro, deteniendo los problemas de seguridad antes de que comiencen en el proceso de entrega de software mediante lo siguiente:
- Detectar y solucionar problemas en las primeras etapas del desarrollo para evitar costosas infracciones, vulnerabilidades e infracciones de cumplimiento en el futuro.
- Adoptar un enfoque integrado para la seguridad del ciclo de vida mediante la optimización de procesos entre equipos para evitar fricciones y reducir riesgos.
- Integrar la seguridad en el proceso continuo de integration/entrega (CI/CD) en lugar de dejarla hasta el final.
- Ayudar a los desarrolladores y DevOps a comprender cómo sus versiones y cambios afectan la seguridad para acelerar el desarrollo/la iteración mientras se mantiene seguro.
Además de abordar estos desafíos, DevSecOps ofrece varias ventajas. Veámoslos a continuación.
¿Cuáles son las ventajas de DevSecOps?
1. Desplace la seguridad hacia la izquierda y acelere la innovación
Con controles de seguridad automatizados integrados en IDE y herramientas DevOps populares, los desarrolladores pueden cumplir fácilmente los requisitos de los entornos DevSecOps. Estos controles ayudan a los desarrolladores a identificar, investigar y remediar vulnerabilidades del código en las primeras etapas del desarrollo con las mejores prácticas y una remediación guiada.
2. Reduzca costes y complejidad
Una estrategia DevSecOps eficaz consolida múltiples funciones (como CSPM, CIEM, CWPP, infraestructura como código (IaC) y análisis de vulnerabilidades) en una única solución CNAPP. También ayuda a sus equipos a encontrar y solucionar problemas en una etapa más temprana del proceso de desarrollo, lo que reduce la repetición del trabajo y la aplicación de revisiones, ahorra tiempo y dinero, y reduce el riesgo de una infracción.
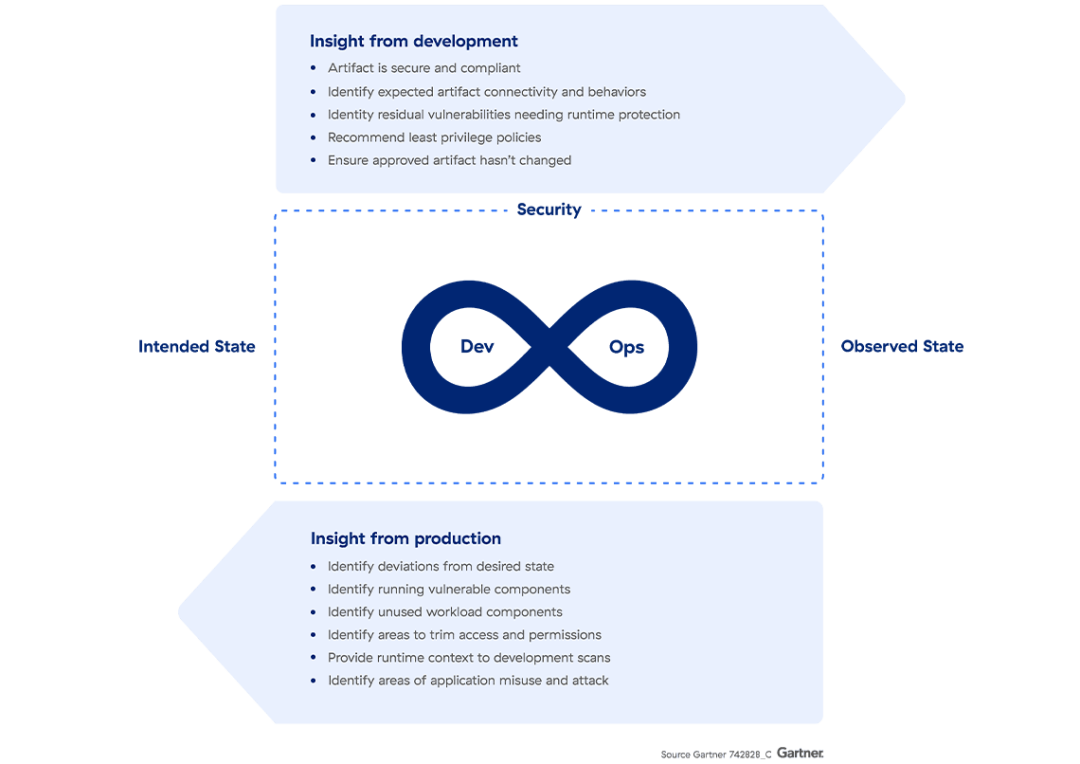
Figura 1: Retroalimentación bidireccional
Fuente: Gartner, Perspectivas de innovación para plataformas de protección de aplicaciones nativas de la nube
Neil MacDonald, Charlie Winckless, 25 de agosto de 2021
3. Obtenga cobertura y control completos
DevSecOps proporciona visibilidad y cobertura completas con controles granulares para ayudar a proteger las aplicaciones nativas, la infraestructura de la nube y los datos confidenciales. Las herramientas DevSecOps eficaces ayudan a identificar y correlacionar problemas, eventos y vectores de ataque ocultos, además de generar alertas, recomendaciones y orientación para su solución en tiempo real.
4. Mejore la colaboración y la comunicación
Los equipos de desarrollo, seguridad y operaciones tienden a trabajar en silos. DevSecOps los reúne en una plataforma para que cada componente y configuración de la pila sea compatible, tenga revisiones y esté configurado de forma segura. Una mejor comunicación y colaboración ayudan a su equipo de seguridad a implementar medidas de seguridad que los desarrolladores pueden incorporar en su trabajo, lo que reduce la fricción entre equipos.
¿Cómo funciona DevSecOps?
Las herramientas CI/CD modernas permiten integrar controles de seguridad en el proceso DevOps en las etapas de codificación, registro, compilación, prueba, implementación y supervisión. Las CNAPP permiten a los equipos de seguridad implementar puertas y protecciones que se pueden integrar en cualquier canalización de DevOps, lo que permite visibilidad para cada ingeniero de software, DevOps y seguridad. Esto se llama canalización DevSecOps.
Su equipo de seguridad puede integrar puertas de seguridad en varias etapas del proceso CI/CD:
- Código: integre aquí capacidades de análisis IaC para brindarles a los desarrolladores visibilidad y orientación sobre cómo seguir estándares de codificación segura.
- Registro: analice cada solicitud de extracción y cambio para detectar vulnerabilidades y filtraciones de datos para garantizar que el código esté limpio y cumpla con las normas antes de ingresar a la compilación y prueba.
- Construir y probar: busque vulnerabilidades y licencias de código abierto, junto con pruebas funcionales y unitarias, para proteger los derechos de propiedad intelectual y evitar vulnerabilidades de día cero.
- Artefactos: una vez que el código se envía al registro central, habilite el análisis de vulnerabilidades, la auditoría y el análisis de acceso para evitar días cero, acceso no autorizado y paquetes fraudulentos o sin firmar.
- Despliegue: una vez que las imágenes certificadas y firmadas del registro se hayan desplegado para realizar pruebas, simule ataques a la aplicación y proyecte los riesgos explotables que pueda contener.
- Supervise: recopile, procese y correlacione continuamente señales de tiempo de ejecución en varios bloques de construcción de la aplicación para desarrollar e implementar medidas de seguridad para evitar problemas futuros.
Lea El rol de la seguridad en la arquitectura DevOps para obtener más información.
¿Cuáles son los desafíos de implementar DevSecOps?
Gestión de las complejidades ambientales
La mayoría de las empresas dependen de múltiples nubes públicas. El uso exclusivo de los controles de seguridad nativos de proveedores individuales genera una visibilidad limitada, silos de seguridad, seguridad inconsistente e informes fragmentados. Mientras tanto, los entornos DevOps combinan varias plataformas, lenguajes de codificación y componentes de código abierto. En estos entornos, las credenciales, los tokens y las claves SSH se comparten abiertamente entre aplicaciones, contenedores y microservicios.
Los equipos de seguridad necesitan controles granulares para abordar entornos complejos sin afectar al rendimiento.
Más allá de las soluciones puntuales
Los equipos de DevOps necesitan una visión integral de su entorno y sus riesgos para resolver problemas y entregar código seguro. Muchos equipos de seguridad utilizan múltiples herramientas de un solo propósito para brindar esa cobertura y luego, en lugar de concentrarse en brindar un excelente software, deben lidiar con la correlación de resultados de estas herramientas dispares, la determinación de prioridades de corrección y el sufrimiento por fatiga de alertas.
Retirar las soluciones puntuales a favor de un enfoque integral significa lograr la aceptación de sus equipos para dar el salto.
Cómo afrontar los desafíos operativos entre equipos
Los ciclos de lanzamiento rápidos pueden provocar errores, como errores de configuración, que pueden convertirse en importantes riesgos de seguridad. En el desarrollo en cascada tradicional, las pruebas de seguridad se realizan después de la etapa de desarrollo, antes de que la aplicación pase a un entorno de producción. Esto puede llevar mucho tiempo y los equipos de seguridad a menudo no pueden mantener el ritmo debido a la experiencia, el presupuesto y los recursos limitados.
Necesitará centrarse en la capacitación y en llenar los vacíos de conocimiento entre sus equipos a medida que avanza hacia DevSecOps.
Fomentar la colaboración y la comunicación
El mayor obstáculo para la cultura DevSecOps es la cultura de seguridad de sus equipos. Los equipos de DevOps tienen la presión para mantener el ritmo y están acostumbrados a que la seguridad los ralentice. A menudo tienen un conocimiento limitado de las mejores prácticas de seguridad y mitigación de riesgos, los requisitos de cumplimiento y las consecuencias de las infracciones. Los equipos de seguridad, por otro lado, se preocupan principalmente de proteger las aplicaciones, el código, la infraestructura y los datos.
En otras palabras, tener objetivos divergentes puede dificultar que los equipos trabajen juntos. Debe unificar sus objetivos y mostrarles los beneficios a largo plazo y entre equipos que aporta DevSecOps.
Lea Los principales desafíos a los que se enfrentan las organizaciones que implementan DevSecOps para obtener más información.
¿Cuáles son los pasos para implementar DevSecOps?
Entonces, en términos prácticos, ¿cómo se hace posible DevSecOps? Comience con estos cinco pasos:
1. Delinee un enfoque unificado
Para mantener los compromisos y lanzamientos según lo previsto sin dejar de lado la seguridad, es necesario que los equipos de seguridad, operaciones y desarrollo conozcan los procesos de los demás, y se necesitan requisitos de seguridad y cumplimiento claramente definidos. Mantener a sus desarrolladores informados sobre las mejores prácticas de seguridad, infracciones, incidentes y orientación ayuda a realizar correcciones oportunas.
2. Adopte una estrategia de “desplazamiento a la izquierda”
La seguridad tiene que empezar temprano en el desarrollo, no añadirse al final. La implementación de políticas de seguridad para el análisis de código ayuda a los desarrolladores a entregar código seguro. Integre una solución de seguridad en los flujos de trabajo existentes de sus desarrolladores que admita diferentes lenguajes e IDE. Esto ayudará al equipo a encontrar y solucionar problemas antes de que lleguen a producción.
3. Evalúe las vulnerabilidades
Los desarrolladores instalan y construyen regularmente sobre dependencias de código de terceros, que pueden provenir de fuentes desconocidas o no confiables. La seguridad debe estar conectada a un sistema CI/CD existente para realizar una revisión crítica, así como analizar de manera temprana y frecuente para detectar vulnerabilidades de seguridad.
4. Gestione amenazas
Los exploits y ataques evolucionan constantemente, y la supervisión continua puede evitar que sufra una vulneración. Su equipo de seguridad debe utilizar controles de seguridad automatizados para analizar y supervisar sus entornos de nube y aplicaciones en busca de ataques o filtraciones, así como para identificar, investigar, priorizar y remediar amenazas o vulnerabilidades.
5. Garantía continua de cumplimiento
Los entornos DevOps cambian constantemente a medida que se crea código nuevo o se modifica el código fuente existente. La validación y los informes de cumplimiento automatizados integrados en todos los procesos de DevOps ayudarán a sus equipos a avanzar más rápido, y los controles confiables garantizarán el cumplimiento y simplificarán las auditorías regulatorias.
Zscaler Posture Control para DevSecOps
Para proteger eficazmente sus aplicaciones y datos en la nube, necesita una evaluación de riesgos automatizada y continua así como una seguridad estrechamente integrada en sus aplicaciones e infraestructura. Un enfoque de seguridad tradicional, con herramientas de seguridad estáticas y aisladas, no puede mantener seguras las aplicaciones críticas, los datos confidenciales y la infraestructura actuales.
Zscaler Posture Control™ ayuda a implementar DevSecOps en la empresa, ofreciendo un enfoque centralizado para proteger la infraestructura en la nube, los datos confidenciales y las aplicaciones nativas implementadas en entornos multinube, al tiempo que reduce la complejidad, la fricción entre equipos y los gastos generales.
Capacidades principales
- Cobertura integral en una sola plataforma: reduzca la complejidad y los gastos generales al reemplazar múltiples productos puntuales con una plataforma unificada que ayuda a su equipo a identificar problemas críticos en los que centrarse primero.
- Correlación avanzada de amenazas y riesgos: mejore la eficiencia de SecOps con políticas y controles inteligentes que detectan configuraciones incorrectas o actividades de riesgo que pueden convertirse en vectores de ataque peligrosos.
- Descubrimiento de estado de la nube, riesgos y cumplimiento: identifique los riesgos y el incumplimiento de manera más temprana en toda su huella de múltiples nubes y sus IDE. Mantenga los flujos de trabajo a través de la integración nativa con IDE y herramientas DevOps populares.
- Implementable en minutos, no requiere agentes: adopte un enfoque basado en API para proteger todas las cargas de trabajo y datos en entornos multinube sin obligar a sus desarrolladores a instalar agentes.
- Seguridad en la nube durante todo el ciclo de vida: detecte y solucione problemas de seguridad en las primeras etapas del desarrollo, antes de que lleguen a producción. Supervise, alerte y bloquee los procesos de implementación cuando se detecten problemas críticos.
- Protección de datos para nubes públicas: identifique y proteja datos confidenciales en reposo o en movimiento con DLP y motores de análisis de amenazas junto con reconocimiento y clasificación de datos avanzados.
- Garantía de cumplimiento continuo: asigne automáticamente la postura de seguridad en la nube a los principales marcos regulatorios e industriales para brindar informes de cumplimiento automatizados y continuos.
Obtenga más información sobre cómo Zscaler Posture Control respalda las iniciativas de DevSecOps de última generación.
Recursos sugeridos
Preguntas frecuentes
Las herramientas de DevSecOps son medios clave para integrar la seguridad en todo el ciclo de vida del desarrollo de software. Al automatizar los procesos de seguridad y respaldar las funciones colaborativas del “equipo DevSecOps”, ayudan a garantizar que la seguridad sea una parte esencial del desarrollo de software. Estos son algunos ejemplos:
— Herramientas de pruebas estáticas de seguridad de aplicaciones (SAST), que analizan el código fuente en busca de vulnerabilidades y errores
— Herramientas de pruebas dinámicas de seguridad de aplicaciones (DAST), que buscan fallas de seguridad en las aplicaciones en tiempo de ejecución
— Herramientas de análisis de composición de software (SCA), que señalan el código fuente abierto en una base de código para garantizar el cumplimiento y la seguridad
— Herramientas de seguridad de contenedores, que examinan las imágenes de contenedores en busca de vulnerabilidades conocidas
— Herramientas de seguridad de infraestructura como código (IaC), que aplican políticas de seguridad para el aprovisionamiento de infraestructuras
— Plataformas CI/CD, que automatizan el proceso de creación, prueba e implementación de código de manera segura
— Herramientas de gestión de eventos e información de seguridad (SIEM), que supervisan y analizan los eventos de seguridad en tiempo real.