Blog da Zscaler
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
CVE-2025-29927: Next.js Middleware Authorization Bypass Flaw
Introduction
On March 21, 2025, a critical vulnerability, CVE-2025-29927, was publicly disclosed with a CVSS score of 9.1, signifying high severity. Discovered by security researcher Rachid Allam, the flaw enables attackers to bypass authorization checks in Next.js Middleware, potentially granting unauthorized access to protected resources. This poses a risk to applications that rely on Middleware to enforce user authorization, validate session data, control route access, handle redirections, and manage UI visibility based on user roles or permissions.
Recommendations
Users whose applications leverage Next.js Middleware for authorization are strongly urged to:
- Update applications: Upgrade to the patched version listed in the affected versions section below.
- Stop header exploits: For applications running version greater than 11.1.4 and less than or equal to 13.5.6, where no secure version is available, configure load balancers or web servers to block external requests containing the
x-middleware-subrequestheader from reaching the Next.js application.
Affected Versions
The following table describes impacted Next.js versions, along with a corresponding patched version.
Impacted Version | Patched Version |
|---|---|
> 11.1.4 | None |
> 12.0 | 12.3.5 |
> 13.0 | 13.5.9 |
> 14.0 | 14.2.25 |
> 15.0 | 15.2.3 |
Table 1: Table of impacted Next.js versions and their corresponding patched versions.
Background
CVE-2025-29927 is an authorization bypass that allows attackers to circumvent Next.js Middleware controls entirely. By including a specially crafted x-middleware-subrequest HTTP header in requests, attackers can bypass authorization checks and gain unauthorized access to protected resources.
Potential impacts of this vulnerability include:
- Unauthorized access: Attackers could gain access to private resources, APIs, or restricted application areas.
- Data exposure: Exploiting this flaw could lead to the theft of sensitive user information.
- Privilege escalation: Attackers might execute malicious actions, such as accessing administrative features or altering server states.
- Content Security Policy (CSP) Bypass: Middleware could be manipulated to modify CSP headers or cookies, potentially compromising application integrity.
- Cache poisoning: In certain configurations, attackers could exploit Middleware to force the caching of 404 responses in applications using a CDN between the Next.js application and the end user. This could render application pages unavailable, impacting their availability and disrupting user experience.
How It Works
The vulnerability stems from how Next.js Middleware handles requests through the runMiddleware function. This function evaluates the x-middleware-subrequest header from incoming requests to decide whether middleware checks should be enforced. The header value is split using a colon (:) as a delimiter and compared against the middlewareInfo.name, which represents the path or location of the middleware component. If the comparison matches, the request bypasses authorization checks and proceeds directly to its destination. The figure below shows a diagram of the attack flow.
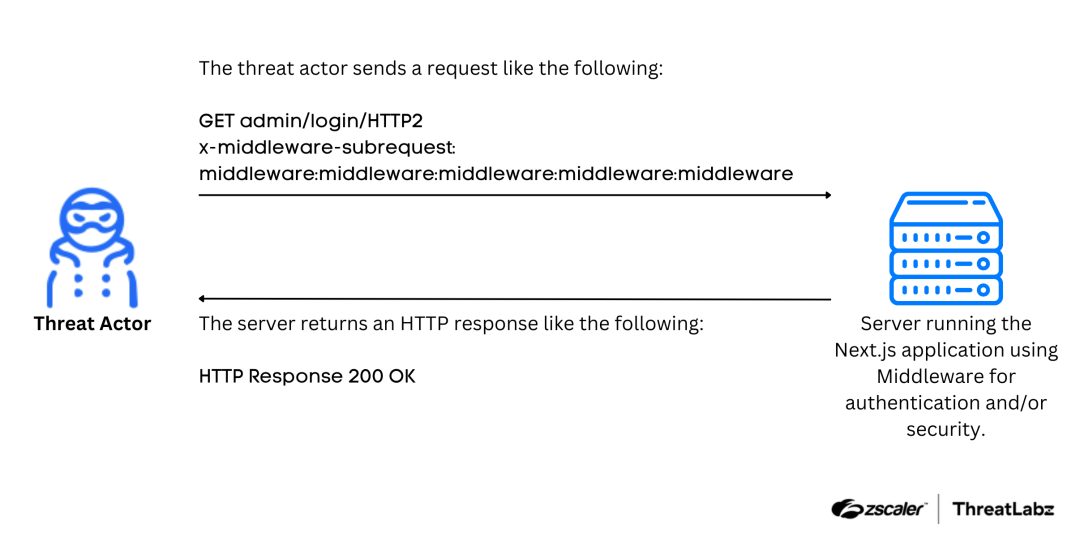
Figure 1: A diagram of the attack flow where an attacker abuses CVE-2025-29927.
Originally designed to prevent infinite loops in recursive requests, this mechanism unintentionally introduced a loophole. Attackers can craft malicious x-middleware-subrequest headers to exploit this flaw, bypassing middleware controls and gaining unauthorized access to protected resources. The code enabling this vulnerability is shown in the figure below:
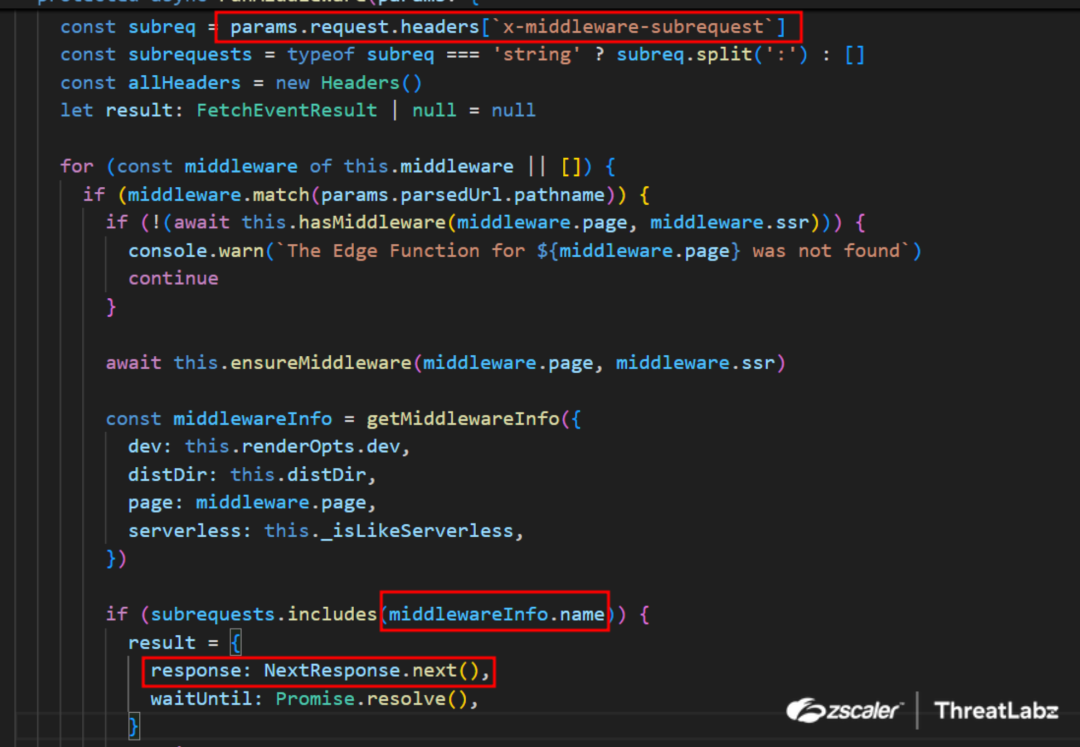
Figure 2: Next.js Middleware code that enables CVE-2025-29927.
Evolution of Middleware file naming and header parsing
- Earlier Versions (Pre 12.2): In early versions of Next.js (prior to 12.2), middleware files were named
_middleware.ts, and only the Pages Router was available. During this period, themiddlewareInfo.namevalue could be determined aspages/_middleware.ts. Attackers could craft a request header like the one below to bypass authorization checks:
x-middleware-subrequest: pages/_middleware
- Next.js 12.2 and later: Starting with version 12.2, Next.js introduced changes to middleware file naming conventions, dropping the underscore (
_) prefix. Middleware files becamemiddleware.tsand could also be placed in a/srcdirectory. ThemiddlewareInfo.namecould now be guessed asmiddlewareorsrc/middleware. The corresponding crafted headers to bypass authorization are the following:
x-middleware-subrequest: middleware
x-middleware-subrequest: src/middleware
- Latest versions: In recent versions of Next.js, the logic for parsing the
x-middleware-subrequestheader evolved. The header value is still split using (:) as a delimiter, but the length of the resulting array (“depth”) is compared to a constant calledMAX_RECURSION_DEPTH(defaulting to 5). This is done to calculate the number of subrequests and avoid an infinite loop condition. Middleware checks are applied only if the depth exceeds this threshold. Attackers exploit this logic by including repeated entries in the header to meet the required depth while bypassing middleware checks. For example:
x-middleware-subrequest: middleware:middleware:middleware:middleware:middleware
x-middleware-subrequest: src/middleware:src/middleware:src/middleware:src/middleware:src/middleware
The patch
The implemented fix addresses the vulnerability through two key components:
- Internal header stripping: All HTTP headers intended for internal use, like
x-middleware-subrequest, are stripped from external requests during processing. - String validation: The
x-middleware-subrequestvalue is now validated against a randomly generated hexadecimal string, ensuring that only legitimate session requests pass authorization checks.
This patch effectively mitigates the authorization bypass and ensures that Middleware components cannot be exploited using tampered request headers. The patched code is shown in the figure below:
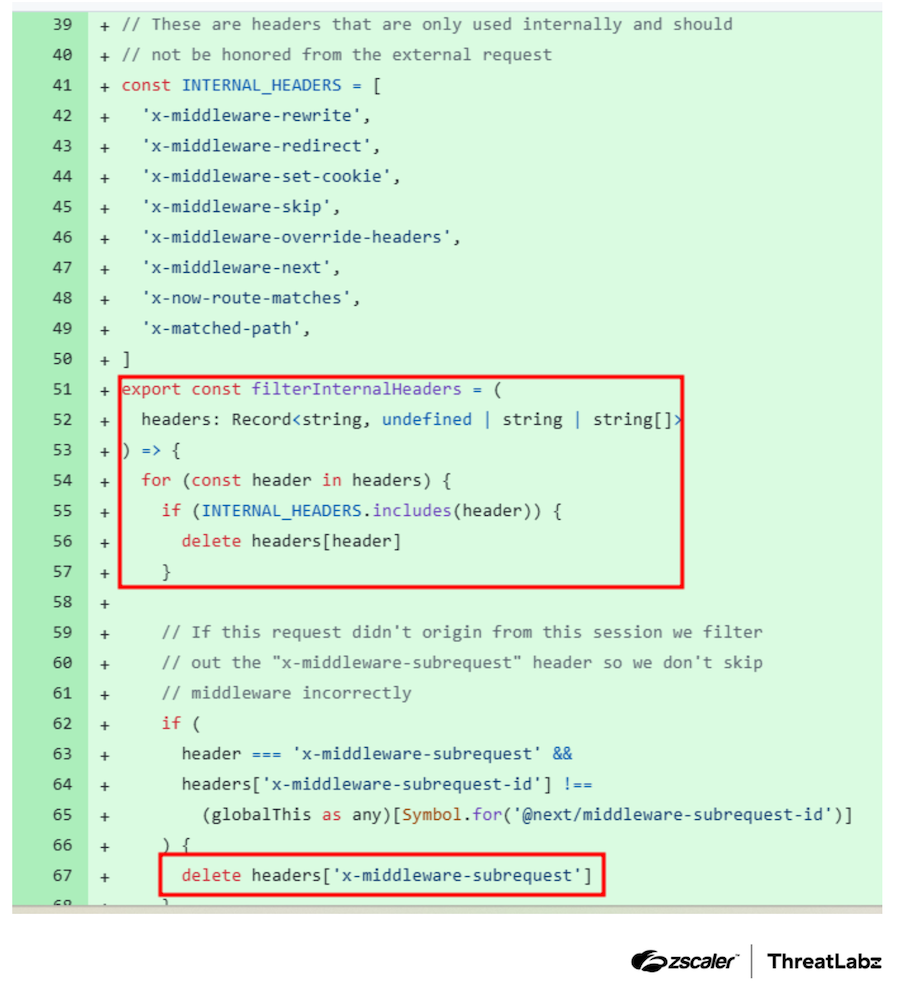
Figure 3: The patched code corresponds to version 15.2.3 of Next.js Middleware.
Conclusion
CVE-2025-29927 poses a risk to applications using Next.js Middleware for authorization, especially self-hosted instances. Middleware should supplement, not replace, robust security measures placed closer to the data source. The impact variation across hosting platforms highlights the need to consider deployment context in security planning.
Zscaler Coverage
The Zscaler ThreatLabz team has deployed protection for CVE-2025-29927.
Zscaler Private Access AppProtection
Esta postagem foi útil??
Aviso legal: este post no blog foi criado pela Zscaler apenas para fins informativos e é fornecido "no estado em que se encontra", sem quaisquer garantias de exatidão, integridade ou confiabilidade. A Zscaler não se responsabiliza por quaisquer erros, omissões ou por quaisquer ações tomadas com base nas informações fornecidas. Quaisquer sites ou recursos de terceiros vinculados neste post são fornecidos apenas para sua conveniência, e a Zscaler não se responsabiliza por seu conteúdo ou práticas. Todo o conteúdo está sujeito a alterações sem aviso prévio. Ao acessar este blog, você concorda com estes termos e reconhece que é de sua exclusiva responsabilidade verificar e utilizar as informações conforme apropriado para suas necessidades.
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Ao enviar o formulário, você concorda com nossa política de privacidade.



