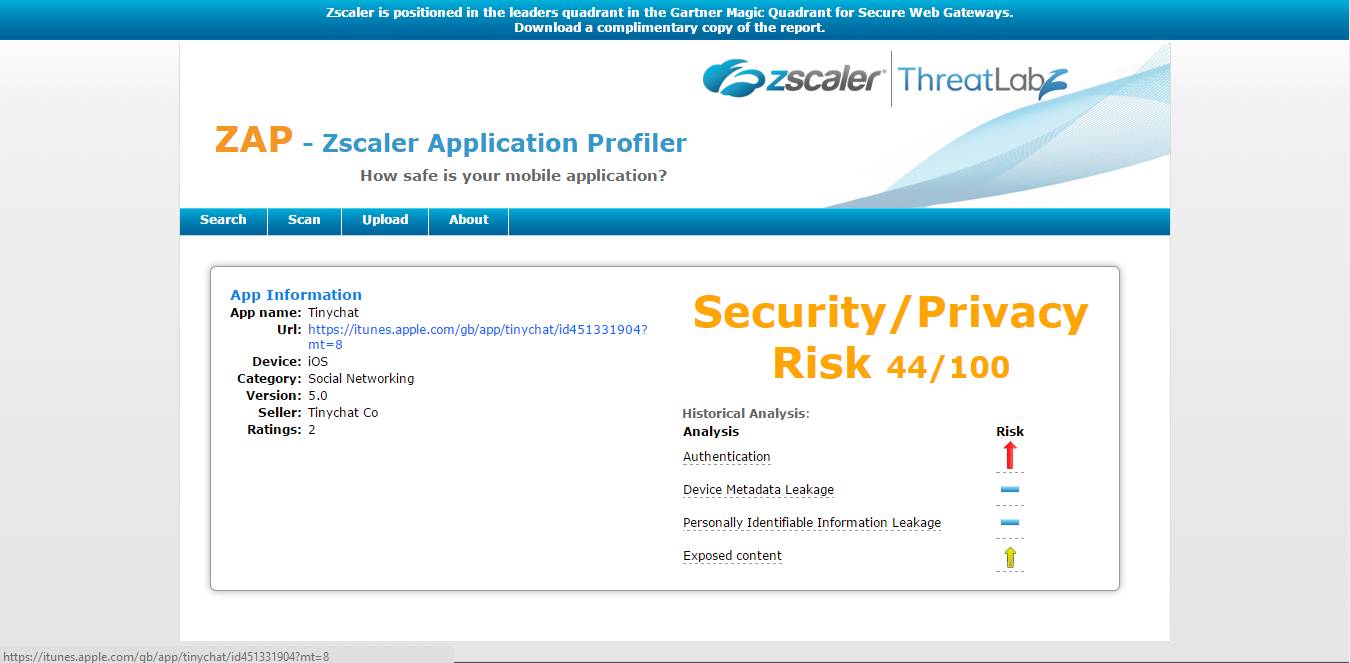
Tinychat
TinychatTinychat is a group video chat application that allows users to chat online and also create their own chart rooms. Currently, this application is ranked among the top 200 apps in the Social Networking category on the iTunes app store. Tinychat claims 5 million minutes of usage per day, making it one of the largest voice and video chat communities on the Internet today.
A user must submit their email address and password in order to create an account. Alternately, a user can also use their Facebook or Twitter account to login to this application.
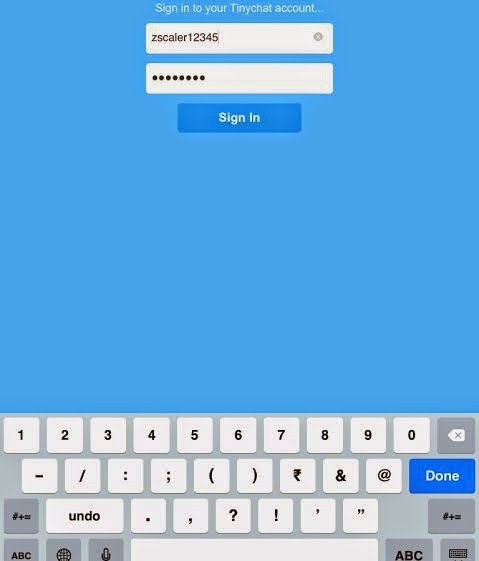 |
| App Login page |
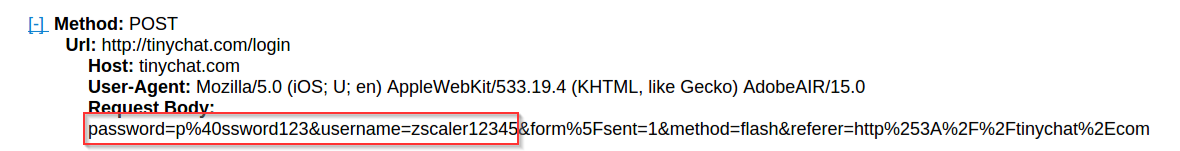 |
| Login Capture |
Account registration:
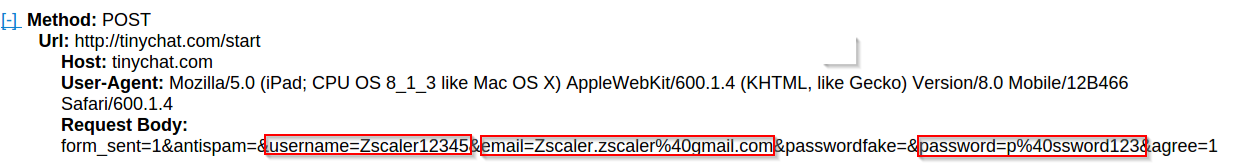 |
| Registration Capture |
An attacker can easily takeover the victim's account by sniffing the vulnerable application's network traffic. This can further lead to more sophisticated attacks and can often lead to the compromise of other applications/services due to password reuse.
Conclusion:
This type of security flaw can be uncovered by simply analyzing the network traffic sent by the application. It is disappointing to see such applications getting uploaded to Apple iTunes store without basic security tests like checking for clear text username/passwords being conducted. This is not the first time we have seen a popular iOS application with this security flaw, but Apple continues to ignore performing a basic security check as part of their vetting process for adding new applications to the app store.
Credit: Analysis by Lakshmi.