UPDATE: The botnet which is described here is called 'Asprox'. I've compared research with that seen from
StopMalvertising.
Recent email spam has begun taking advantage of user's need to snail mail something. The attacker will forward a message supposedly from USPS in order to get victim's to click on a link purported to be a shipping receipt, which actually leads to a malicious file. If the user is unfortunate enough to click the link in the spam mail, a zip file containing a variant of Asprox is downloaded.
 |
| At the time of research, the VT score was 4/53 | |
Once the file makes it way onto the desktop, it feigns a document icon in order to trick the user into thinking it is safe to view. This is actually the malicious executable which scored
4/53 on initial VirusTotal scans.
 |
| Never trust an icon! Check the 'Right Click > Properties' to see the true extension |
The file itself creates local copies of itself in the logged-in User's Local Application Data and creates an autostarter to ensure that the victim stays infected after restarting their compromised PC.
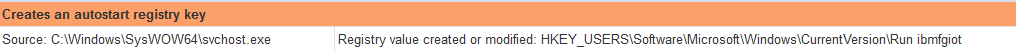 |
| The threat installs a randomly generated Autostarter value |
ThreatLabZ has monitored this infection for a few days and observed several other download locations that kick off this threat.
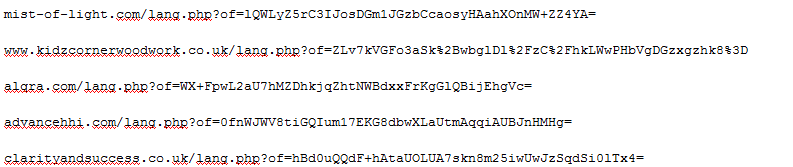
| All links download a similar package. |
|
| |
The common factor across all of these dropped files is that they all POST bzip2 compressed data which is then encrypted with a 16-byte random RC4 key via HTTP as reported by
StopMalvertising. We're seeing a growing number of attacks which utilize this method of phone home activity. The case of this Asprox threat phones home over ports 443 and 8080.
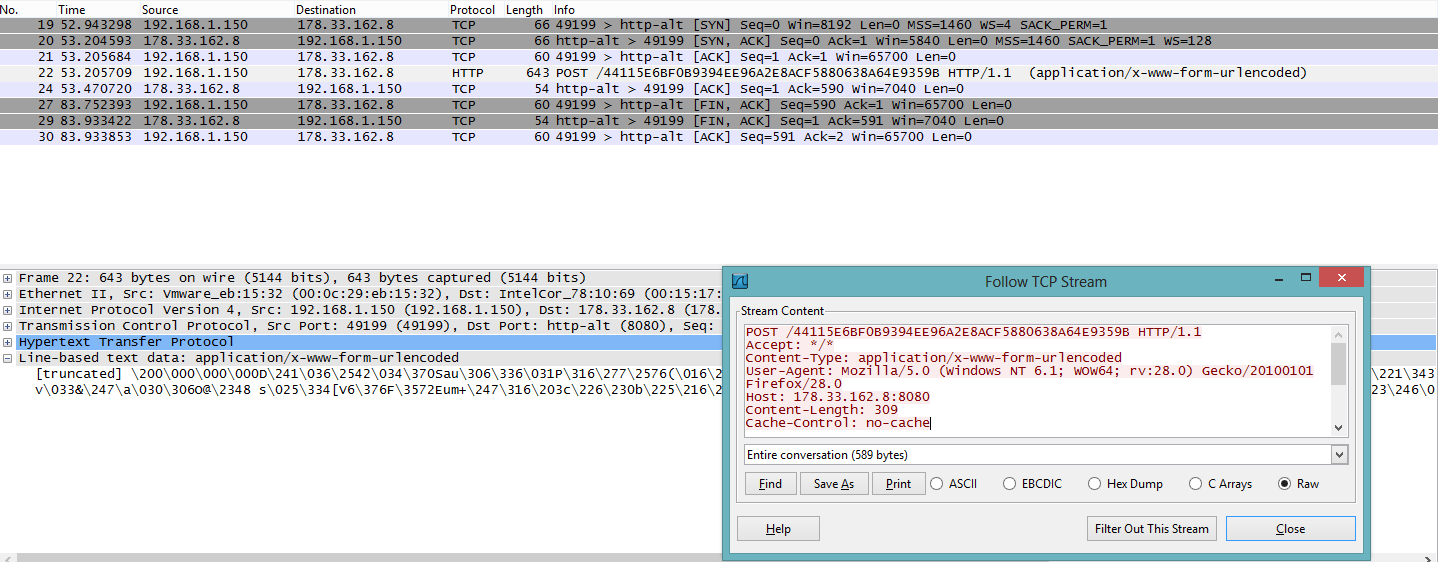 |
| Communication is sent over port 8080 or 443 |
ThreatLabZ collected numerous IPs which were seen to communicate with malicious variants mentioned above.
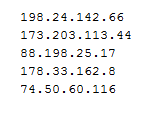 |
| IPs which communicated with Malicious samples. |
Users and Administrators should be cautious of all traffic regardless of the ports it communicates on. Attackers are leveraging nonstandard HTTP ports in order to bypass some security solutions.











