Potencie su organización con una arquitectura Zero Trust
Proteja
Minimice el riesgo empresarial con protección frente a ciberamenazas y pérdida de datos.
Simplifique
Reduzca los costos y la complejidad al eliminar las soluciones puntuales y reducir los gastos generales.
Transforme
Aumente la agilidad empresarial con redes Zero Trust nativas en la nube para usuarios, cargas de trabajo y sucursales.
La arquitectura es importante.
El mundo empresarial ha cambiado
Los modelos tradicionales de red y seguridad fueron diseñados para su uso en épocas anteriores a las tecnologías revolucionarias de hoy. Las siguientes herramientas impulsan la transformación digital y permiten a las organizaciones ser más ágiles y competitivas, pero requieren un nuevo enfoque de las redes y la seguridad.
Movilidad
Nube
IoT/OT
IA/Aprendizaje automático
La transformación digital requiere una arquitectura Zero Trust

Las arquitecturas tradicionales de red y firewall impiden la transformación
Una red de confianza conecta usuarios, sitios y aplicaciones, y está protegida por un perímetro de seguridad. Tratar de incorporar los servicios en la nube y otras tendencias mediante la aplicación del perímetro de la red es arriesgado y costoso, y perjudica las experiencias de los usuarios.
La arquitectura Zero Trust permite la transformación
Zero Trust significa abandonar los enfoques centrados en la red. Una nube especialmente diseñada sirve como una centralita inteligente que utiliza las políticas empresariales para determinar quién puede acceder a qué, en cualquier lugar y a través de cualquier red. Este enfoque es más seguro y económico, y mejora la experiencia del usuario.
El problema
Las arquitecturas de firewall y VPN aumentan el riesgo
Empresas de todo el mundo han gastado miles de millones en firewalls, pero las violaciones van en aumento. El problema es sencillo: tratar de proteger una red radial con herramientas de seguridad basadas en el perímetro no permite detener las violaciones en las cuatro etapas de la cadena de ataque.
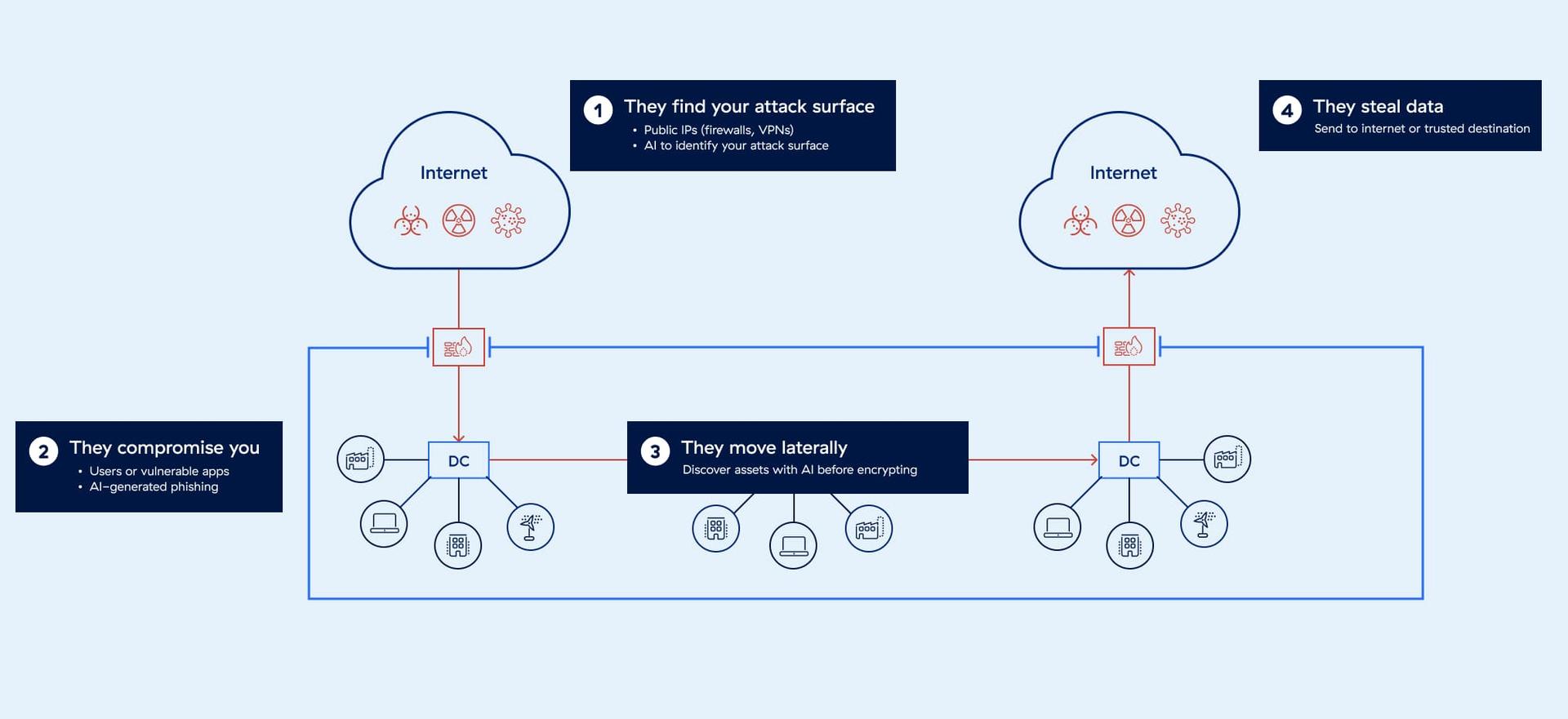
Los atacantes lo encuentran
Todas las IP son vulnerables, incluso las de los firewalls, que se supone que deben brindarle protección.
Lo ponen en peligro
Los atacantes aprovechan las vulnerabilidades para establecer un punto de partida en su red.
Se mueven lateralmente
Una máquina infectada compromete toda su red.
Roban sus datos
Se pierden datos confidenciales en aplicaciones, servidores y redes completas.
Resumen de la plataforma
Zscaler Zero Trust Exchange™ es una plataforma completa e integrada que permite seguridad Zero Trust y transformación de la red para la totalidad de usuarios, cargas de trabajo, IoT/OT y socios B2B.
Basada en el principio Zero Trust de acceso con privilegios mínimos, nuestra arquitectura de proxy única permite una inspección completa de TLS/SSL a escala. Las conexiones individuales se intermedian entre los usuarios y las aplicaciones en función de la identidad, el contexto y las políticas empresariales.
Ventajas
Reduzca el riesgo en las cuatro etapas de la cadena de ataque
Minimizar la superficie de ataque.
Oculte las aplicaciones detrás de Zero Trust Exchange, de manera que no sean visibles en Internet.
Evite el compromiso
Inspeccione todo el tráfico, incluido el tráfico cifrado, y bloquee las amenazas en tiempo real.
Elimine el movimiento lateral
Conecte las entidades autorizadas (como los usuarios) directamente a las aplicaciones, no a la red.
Detenga la pérdida de datos
Identifique y proteja automáticamente los datos confidenciales en movimiento, en reposo y en uso.
Nuestro enfoque Zero Trust
Verifique la identidad
Verifique quién o qué está intentando obtener acceso. La plataforma confirma la identidad del usuario, el dispositivo o la carga de trabajo a través de integraciones con proveedores de identidad de terceros.

Determine el destino
Identifique hacia dónde se dirige la conexión (a una página web, una aplicación SaaS, una aplicación privada o cualquier otro lugar) y asegúrese de que el destino sea conocido y se comprenda.

Evalúe el riesgo
Utilice la IA para determinar el riesgo en función del contexto, teniendo en cuenta factores como el comportamiento del usuario, la postura del dispositivo, el destino y el contenido, información de terceros y más de 500 billones de señales diarias.

Aplique la política
Determine si desea conceder acceso, bloquearlo, aislarlo, engañar o realizar otras acciones. La plataforma aplica la política en tiempo real, por sesión, para cada solicitud.

Serie de seminarios web de tres partes "Zero Trust, de la teoría a la práctica"
Domine el modelo Zero Trusto y conviértase en un embajador de Zero Trust en su organización.
Casos de uso
Asegure cada paso de su proceso de transformación

Proporcione a su personal un acceso rápido, seguro y fiable a Internet, SaaS y aplicaciones privadas.

Asegure las comunicaciones de su carga de trabajo y proteja los datos en reposo dentro de sus aplicaciones en la nube/SaaS.

Obtenga detección de dispositivos IoT, conectividad Zero Trust para IoT/OT y acceso remoto privilegiado a OT.

Amplíe el acceso de privilegio mínimo a SaaS y aplicaciones privadas para sus socios comerciales.

nuestra plataforma
Zscaler Zero Trust Exchange
Comunicación segura entre usuarios, cargas de trabajo y dispositivos
dentro de la sucursal, la nube y el centro de datos.
Zero Trust en todas partes
Detenga los ciberataques
- Vuélvase invisible para los atacantes
- Evite el compromiso
- Evitar el movimiento lateral
Datos protegidos
- Encuentre, clasifique y evalúe la postura de seguridad de los datos
- Prevenga la pérdida de datos en todos los canales
Proteja la IA
- Proteja el uso de la IA pública
- Proteja los modelos y aplicaciones de IA privados
- Proteja las comunicaciones entre agentes
Automatice las operaciones
- Acelere las operaciones de seguridad
- Optimice las experiencias digitales
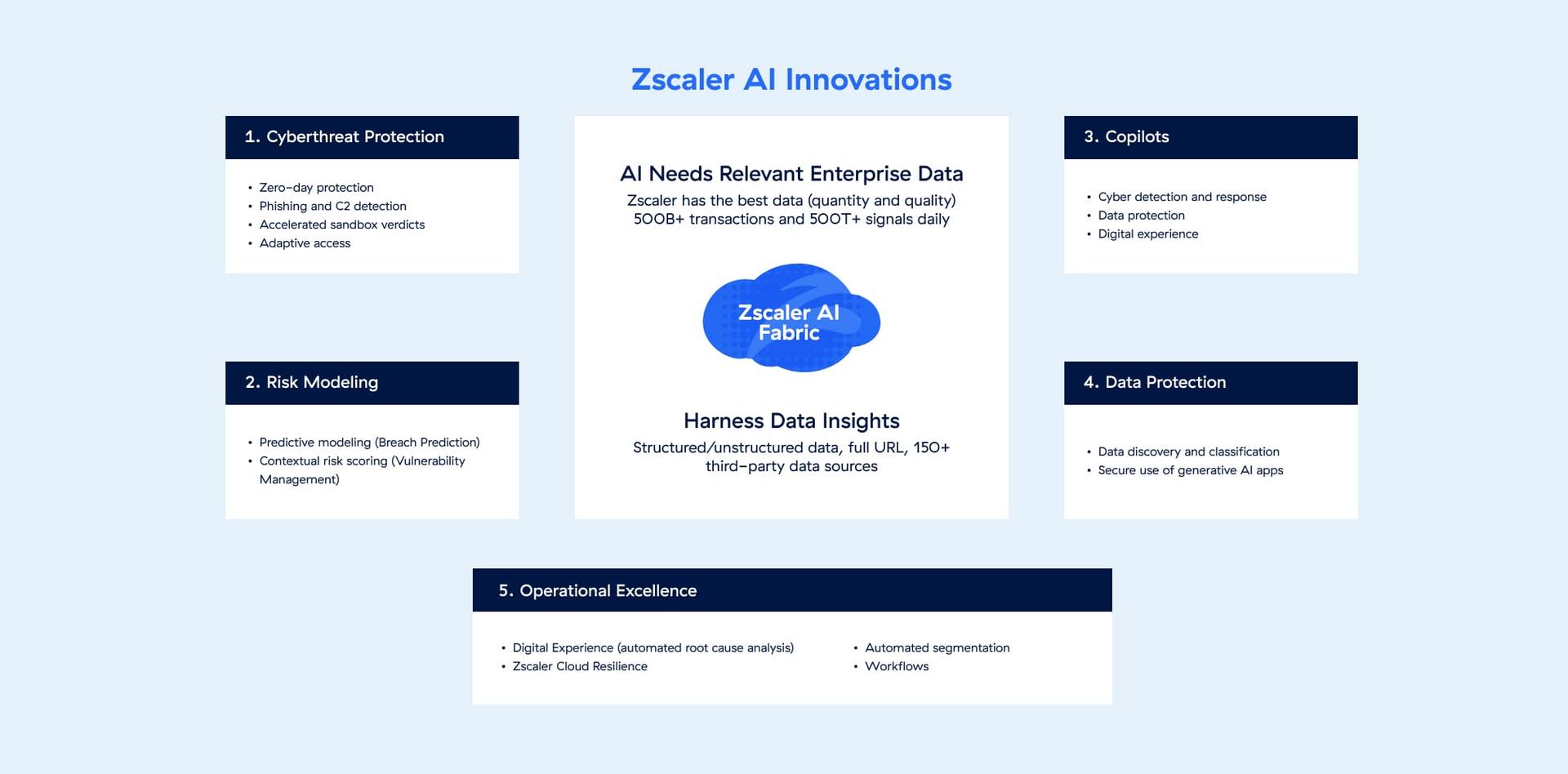
Zero Trust + IA
Liderazgo y ventaja en IA
Zero Trust Exchange utiliza la IA/ML para ofrecer la protección de datos y contra ciberamenazas más eficaz, junto con la automatización y el aumento de la productividad.
Reconocimiento
El líder universalmente reconocido en confianza cero
500 mil millones +
Más de 160 DC
>70 NPS
9+ mil millones
500T+
400+
~45%
Líder
Nasdaq-100
Solicitar una demostración
Permita que nuestros expertos le muestren cómo Zero Trust Exchange puede potenciar su estrategia de seguridad y transformar su manera de hacer negocios.













