Renversez les rôles et attirez les hackers avancés présents dans votre réseau
Les hackers qui accèdent à votre environnement sans être détectés pensent qu’ils ont déjà gagné. Déployez une technologie de tromperie pour assurer une défense proactive qui attire et révèle les hackers sophistiqués grâce à des leurres réalistes.
Arrêter les déplacements latéraux
en neutralisant les hackers avec des honeypots convaincants
Se protéger contre les attaques de l’IA générative
sur votre infrastructure et vos ensembles de données d’apprentissage
Détecter les utilisateurs compromis
et l’utilisation abusive d’identifiants volés
Problème
Les hackers compromettent les environnements Zero Trust par le biais des utilisateurs et des applications
90 %
80 %
91 %
Présentation du produit
Détectez les menaces avancées qui échappent aux défenses traditionnelles
Zscaler Deception déploie des actifs leurres réalistes dans votre environnement pour attirer, détecter et intercepter les hackers actifs. Lorsqu’un utilisateur compromis interagit avec un leurre, votre équipe reçoit une alerte immédiate et les hackers ne sauront qu’ils ont été détectés jusqu’à ce qu’il soit trop tard.
Composante de la plateforme cloud native Zscaler Zero Trust Exchange™, la solution Deception peut déployer rapidement et de manière homogène une détection des menaces haute fidélité dans l’ensemble de votre entreprise.
Éliminer les risques liés à votre surface d’attaque
Détournez les acteurs malveillants des cibles critiques telles que les terminaux, les systèmes d’identité, les réseaux, les applications et le cloud.
Détecter plus rapidement les menaces les plus importantes
Détectez les utilisateurs compromis, les déplacements latéraux et les ransomwares avec des IOC (indicateurs de compromission) extrêmement fiables et un taux de faux positifs proche de zéro.
Contenir les menaces en temps réel
Exploitez les politiques d’accès Zero Trust pour limiter ou supprimer dynamiquement l’accès aux services SaaS sensibles et aux applications internes.
Avantages
Adoptez une nouvelle approche de la détection ciblée des menaces
Protéger les utilisateurs et les applications avec des leurres
Détectez silencieusement les menaces et l’activité des hackers à l’aide de leurres sur les terminaux ainsi que d’applications, de serveurs, d’utilisateurs et d’autres ressources leurres.
Accélérer la réponse aux incidents et réduire la lassitude à l’égard des alertes
Informez rapidement votre équipe de sécurité des menaces et des violations confirmées, sans faux positifs ni frais opérationnels supplémentaires.
Faire peser la charge de la réussite sur le hacker
Remplacez votre surface d’attaque par de fausses cibles convaincantes auxquelles les hackers ne peuvent pas résister et attrapez-les dès qu’ils mordent à l’appât.
Détails du produit
Plateforme complète de cyber-tromperie
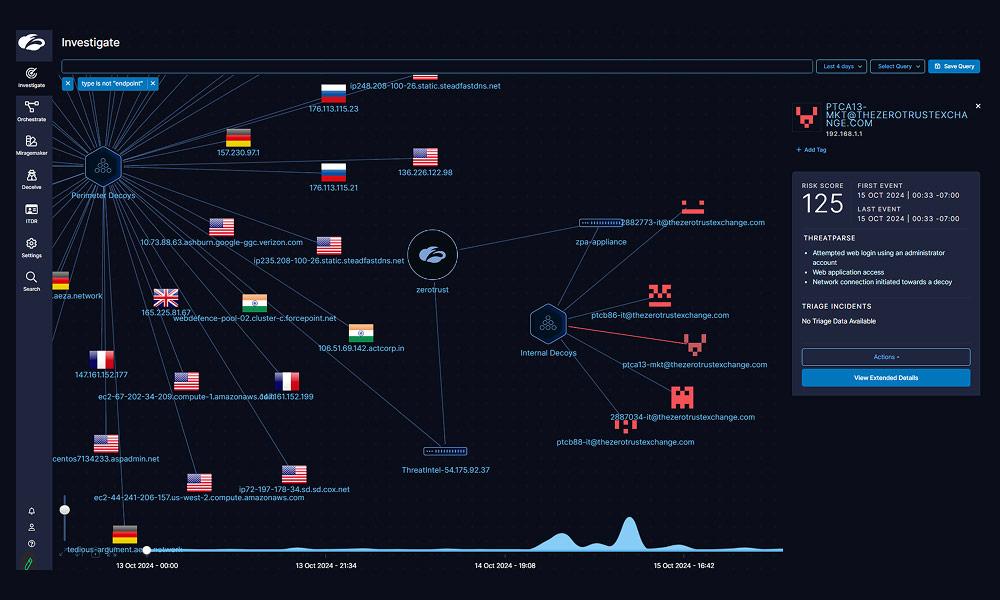
Capacités principales
Utilisez des chatbots leurres, des API LLM leurres, des leurres adaptatifs et des agents leurres pour détecter les hackers qui ciblent l’infrastructure d’IA générative de votre environnement.
Utilisez des leurres accessibles sur Internet pour détecter les menaces précédant une violation qui ciblent spécifiquement votre entreprise.
Aménagez un champ de mines pour protéger vos terminaux à l’aide de fichiers, d’informations d’identification, de processus leurres et bien plus encore.
Détectez les déplacements latéraux dans vos environnements cloud avec à l’aide de serveurs Web et fichiers leurres, des bases de données leurres et bien plus encore.
Extrayez des informations à partir de journaux riches en contexte, et bénéficiez d’analyses détaillées automatisées et d’analyses des causes profondes en deux clics.
Déployez des systèmes de serveurs leurres qui hébergent des services tels que des serveurs SSH, des bases de données, des partages de fichiers, etc.
Détectez l’activité d’énumération et l’accès malveillant avec de faux utilisateurs dans Active Directory.
Bénéficiez d’une visibilité plus approfondie sur les attaques dans des environnements de système d’exploitation leurres réalistes et hautement interactifs.
Cas d’utilisation
Transformez votre réseau en un environnement hostile pour les hackers

Recevez des signaux de mise en garde précoce à partir des leurres basés sur le périmètre lorsque des hackers sophistiqués, tels que des opérateurs de ransomwares ou des groupes d’APT, effectuent une reconnaissance avant l’intrusion.

Déployez des mots de passe, des cookies, des sessions, des signets et des applications leurres pour détecter les utilisateurs compromis lorsqu’un hacker interagit avec l’environnement trompeur.

Utilisez des leurres d’application et des leurres sur les terminaux pour détourner et intercepter les hackers qui tentent de se déplacer latéralement dans votre environnement.

Entourez vos biens les plus précieux de leurres qui détectent et bloquent instantanément même les adversaires les plus furtifs et les plus sophistiqués.

Détectez les ransomwares à chaque étape du cycle de vie de l’attaque grâce à des leurres placés dans votre réseau, vos terminaux, vos clouds et vos environnements Active Directory.

Effectuez une intégration homogène à la plateforme Zscaler et aux outils d’opérations de sécurité tiers tels que SIEM et SOAR pour arrêter les hackers actifs avec une réponse automatisée et rapide.

Interceptez les hackers qui utilisent des identifiants volés pour accéder à des applications Web leurres qui ressemblent à des applications de banc d’essai vulnérables et à des services d’accès distant tels que les VPN.

Détectez l’injection de requête, l’empoisonnement de données et d’autres attaques sérieuses qui ciblent votre infrastructure d’IA générative et vos ensembles de données d’apprentissage.

Notre plateforme
Zscaler Zero Trust Exchange
Sécurisez les communications des utilisateurs, des workloads et des appareils entre
et au sein du site distant, du cloud et du data center.
Zero Trust Everywhere
Arrêter les cyberattaques
- Se rendre invisible aux yeux des hackers
- Empêcher l'intrusion
- Empêcher le mouvement latéral
Sécuriser les données
- Identifier, classer et évaluer la posture de sécurité des données
- Prévenir la perte de données sur tous les canaux
Sécuriser l’IA
- Sécuriser l’utilisation de l’IA publique
- Sécuriser les applications et modèles d’IA privés
- Sécuriser la communication des agents
Automatiser les opérations
- Accélérer les opérations de sécurité
- Optimisez l’expérience numérique
FAQ
FAQ
La technologie Zscaler Deception réinvente les honeypots traditionnels en intégrant la tromperie directement dans les environnements utilisateur sur les terminaux, le réseau, Active Directory, les workloads cloud, les dispositifs IoT/OT, et plus encore, rendant les pièges indiscernables des actifs légitimes. Contrairement aux honeypots statiques, Zscaler utilise des leurres et des fils d’Ariane, de sorte que les hackers se révèlent sans le savoir. Cette stratégie proactive et distribuée détecte les menaces en temps réel et s’intègre parfaitement à la plateforme Zero Trust Exchange de Zscaler.
Zscaler Deception est parfaitement intégré à Zscaler Zero Trust Exchange pour distribuer dynamiquement des actifs leurres légers sur les terminaux, les réseaux, Active Directory, les workloads cloud et les dispositifs IoT/OT de l’entreprise. Ces pièges reproduisent des actifs authentiques, ce qui rend la détection d’activités malveillantes pratiquement instantanée. Cette approche intégrée permet une détection proactive des menaces tout en maintenant une validation continue fidèle à l’approche Zero Trust. Zscaler Deception est également intégré à l’agent sur les terminaux, Zscaler Client Connector, et à Zscaler Private Access pour détecter les déplacements latéraux des terminaux vers les applications.
Zscaler Deception est conçu pour découvrir un large éventail de menaces, notamment les menaces persistantes avancées (APT), les attaques préalables à l’intrusion, la compromission d’identité, l’escalade des privilèges, les déplacements latéraux, les menaces internes et les ransomwares. En attirant les hackers avec des leurres, la solution identifie les comportements suspects à un stade précoce, offrant une protection proactive contre les violations et réduisant considérablement les temps de présence.
Oui, Zscaler Deception prend entièrement en charge les environnements cloud, sur site et hybrides. Sa conception légère garantit un déploiement transparent sur les terminaux, les workloads et les dispositifs IoT, quelle que soit l’infrastructure. En tant que solution fournie dans le cloud, elle s’aligne parfaitement sur les environnements distribués modernes pour fournir une détection des menaces complète et évolutive.
Oui, Zscaler Deception peut détecter des attaques telles que l’injection de requêtes, l’empoisonnement des données, le jailbreaking, les suffixes adverses, l’extraction de données d’entraînement, etc. Zscaler Deception prend en charge la création de chatbots LLM et d’API leurres pour détecter ces attaques.








