Zscalerのブログ
Zscalerの最新ブログ情報を受信
Secure Developer Workflows with ZIA’s Automated TLS/SSL Inspection and Code Sandboxing
The Developer's Dilemma: Innovate Rapidly without Compromise
Developers use cloud-based code repositories, CI/CD pipelines, and tools to build and deploy applications faster than ever before. While this transformation fuels innovation, it also introduces new attack vectors that can compromise your organization’s infrastructure, valuable data, and intellectual property.
Zscaler Internet Access can now help security and IT teams secure development workflows with two new capabilities: automated TLS/SSL inspection and code sandboxing.
Automate TLS/SSL Inspection for 30+ Popular Developer Tools
Developers rely on dozens of tools and languages like GitHub, Docker, and Python to streamline their workflows and release rapidly. These tools—and the sensitive data transported through them—are frequent targets of attacks hiding in encrypted traffic. To mitigate risk without adding friction, Zscaler can help your security team automate TLS/SSL inspection for encrypted traffic across 30+ popular developer tools and frameworks.
Traditionally, TLS/SSL inspection has been fraught with challenges, including slowing down workflows and frustrating developers. Zscaler changes that narrative by easily integrating its scalable architecture with developer tools and frameworks.
Zscaler Internet Access (ZIA) includes TLS/SSL inspection to identify threats hidden in encrypted traffic without compromising speed or performance—and now, we’re extending this protection to developer environments: whether it’s inspecting upload activity to repositories, monitoring API calls from microservices, or filtering potentially harmful web traffic in third-party tools, Zscaler empowers security teams to safeguard every node in the developer pipeline.
Integration Made Simple
Zscaler TLS/SSL inspection integrates effortlessly into developer workflows, requiring minimal adjustments to existing tools or frameworks. Developers can continue using their preferred platforms while Zscaler handles the heavy lifting in the background. Security teams can even customize policy enforcement based on developer tool usage, ensuring security without introducing inefficiencies. Learn more with the following resources:
- Read this blog to learn the steps to build a custom CA store needed to inspect encrypted traffic with ZIA, and integrate it with various developer tools and frameworks.
- Watch this on-demand webinar for an expert-led discussion of the challenges and methods to inspect encrypted traffic in developer workflows.
For us, Zscaler’s SSL inspection was a big driver. We were worried about the threats we were missing in encrypted traffic.
— Munish Dargan, Lead Enterprise Architect and IT Leader, Genpact
Sandboxing Developer Scripts to Reduce Risk
Threat actors constantly change their attack tactics and strategies, including how they use malicious files with uncommon or new file types. Attackers also attempt to use oversized files to bypass security tool analysis. Zscaler addresses this critical challenge by using advanced sandboxing technology to inspect and analyze scripts before they can be released to customer environments. ZIA’s Cloud Sandbox now supports additional file types in addition to larger files overall based on our signal telemetry from the Zscaler Zero Trust Exchange.
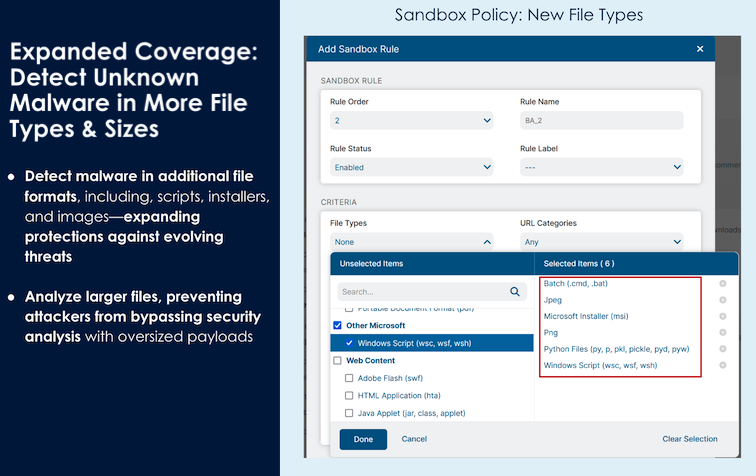
Scripts and Python related files are key in the developer ecosystem as developers often download and use code from online repositories or other external sources. These code libraries and files require examination to ensure no malicious, hidden code can be introduced into production environments.
Malware can also be embedded into images, and in a future release Zscaler will add image file support for ZIA’s Cloud Sandbox. While still a low percentage overall of malicious detections, images with malignant malware are increasing and becoming more commonplace.
Key Benefits of Inspecting Code with Zscaler Cloud Sandbox
- Real-time analysis: Unlike traditional review processes that require manual intervention, Zscaler’s sandboxing happens in real time, inspecting scripts at the speed developers need.
- Deep observability: Zscaler’s architecture analyzes scripts to detect malicious function calls, suspicious outbound communications, or anomalous behavior—without impacting the developer workflow.
- Seamless collaboration: Security teams can share sandbox findings with developers who need to tweak their code, fostering collaboration while maintaining robust protection standards.
Integrating the sandboxing capabilities of Zscaler Internet Access is straightforward thanks to its cloud native scalability and zero trust foundation. Whether securing mid-market organizations or Fortune 500 enterprises, Zscaler adapts to ensure security teams can confidently support their developers at scale.
Secure Developer Workflows Without Compromise or Blocking Innovation
Innovation shouldn’t come at the expense of security, nor should security compromise agility. By automating TLS/SSL inspection across popular developer tools and sandboxing developer scripts, Zscaler ensures continuous protection for your entire development pipeline. These advanced features enable security teams to mitigate risks while developers focus on what they do best: building software that drives your business forward.
Securing your developer workflows at scale while enabling growth is one of several topics we’ll cover during our Zscaler Internet Access Innovations webinar on April 23, 2025. We’ll take a look at the latest ZIA enhancements and show you how they can break silos without compromising on security. RSVP now and take the first step toward secure, scalable developer ecosystems!
このブログは役に立ちましたか?
免責事項:このブログは、Zscalerが情報提供のみを目的として作成したものであり、「現状のまま」提供されています。記載された内容の正確性、完全性、信頼性については一切保証されません。Zscalerは、ブログ内の情報の誤りや欠如、またはその情報に基づいて行われるいかなる行為に関して一切の責任を負いません。また、ブログ内でリンクされているサードパーティーのWebサイトおよびリソースは、利便性のみを目的として提供されており、その内容や運用についても一切の責任を負いません。すべての内容は予告なく変更される場合があります。このブログにアクセスすることで、これらの条件に同意し、情報の確認および使用は自己責任で行うことを理解したものとみなされます。





