Facilitar y agilzar su estrategia de desinversión en TI
70 %
85 %
50 %
El problema
Maximizar el valor mientras desentraña los ecosistemas es un desafío
Las desinversiones son operaciones delicadas y complicadas que pueden tener efectos de gran alcance en el valor de las acciones, la ventaja competitiva y la postura de cumplimiento. Cuando los dominios de bajo valor y de alto esfuerzo, como la red y la seguridad, bloquean su camino, ejercen una gran presión sobre sus cronogramas.

más del 50 % de las sinergias empresariales dependen de la tecnología
PwC

El 51 % de los responsables de las operaciones de fusiones, adquisiciones y desinversiones citan la cibernética como el principal riesgo en las transacciones
McKinsey

La duración promedio de los acuerdos de servicios de transición (TSA) es de 18 meses.
Deloitte
Descripción general de las soluciones
Acelerar la separación para captar valor más rápidamente con Zscaler
Optimizar los procesos de separación con la plataforma Zscaler distribuida en la nube. Separar lógicamente las entidades, reduzca drásticamente el riesgo y ahorre esfuerzos significativos, como la necesidad de determinados servicios de TSA, convirtiéndolos de potenciales sumideros de enorme valor en elegantes facilitadores del negocio.
Eliminar de manera lógica los activos, usuarios y flujos de datos desinvertidos
de su ecosistema de red, de manera rápida, segura y con poca sobrecarga, desde día 1.
Aplicar el acceso Zero Trust a las aplicaciones bajo TSA
para los usuarios cedidos.
Transmitir más controles el día 1
reducir rápidamente su carga de TSA de la entidad recién creada o adquirida.
Proteger sus joyas de la corona de la exfiltración
por un nuevo comprador durante el período del TSA.
Establecer una desinversión sin complicaciones
Ventajas
Únase a más de 350 organizaciones a las que hemos ayudado a realizar integraciones y desinversiones de TI rápidas y seguras.
Simplificar la separación
Administre la seguridad y la conectividad a través de políticas en lugar de controles de acceso a la red y segmentación.
Mitigar el riesgo compartido
Minimice la exposición y conceda acceso zero trust a los recursos retirados o TSA, mientras elimina de su red a los usuarios retirados.
Adaptar los costos a sus necesidades
Aprovechar los precios basados en la demanda, eliminando importantes gastos de capital y costos impredecibles.
Reducir las demandas de soporte
Entregue los controles de seguridad y acceso de los activos retirados para reducir la carga del TSA y facilitar los plazos.
Detalles de la solución
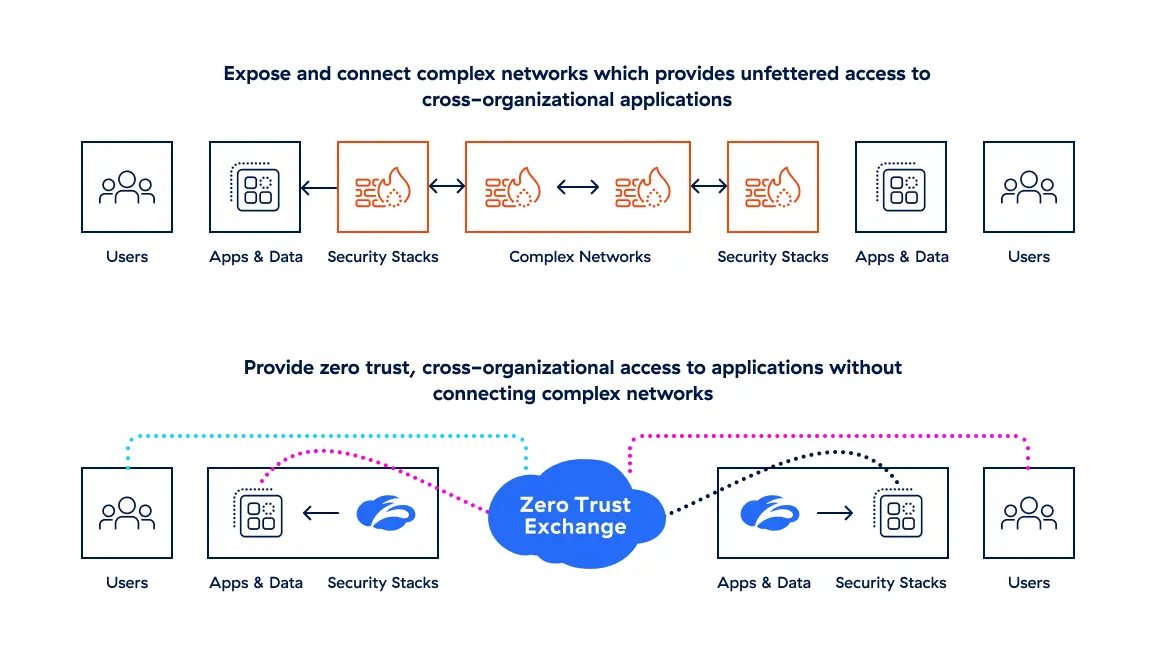
Zero Trust y el ciclo de vida de la separación
Zscaler trabaja con empresas de capital privado para proteger y acelerar sus operaciones con una hoja de ruta probada:
Día 1: Escición parcial
Segmente lógicamente a los usuarios y recursos dentro del ámbito para proteger su posición de seguridad durante el período de TSA.
Traspase el control de la política de seguridad mediante la transmisión del usuario de Zscaler a la entidad escindida
Reduzca la necesidad de ampliar los TSA manteniendo las auditorías y los controles adecuados
Otorgue a los usuarios transferidos acceso Zero Trust a las aplicaciones bajo TSA sin colocarlas en su red ni exponer sus datos
Día 2 y siguientes: Separación/ Puesta en marcha
Ofrezca una experiencia de usuario fluida conectando a los usuarios a cualquier aplicación, en cualquier lugar, para respaldar el realojamiento provisional de aplicaciones.
Salga rápidamente de los TSA basados en seguridad o en red poniéndose en marcha o tomando el control del usuario de Zscaler
Realinee los recursos de red tradicionales con oportunidades más valiosas sin presencia de TI a través de Zscaler
Complete escisiones seguras y eficientes sin preocuparse por el aprovisionamiento de circuitos, el gasto de capital o el suministro.
Cómo optimiza Zscaler las desinversiones
Hoja de ruta de desinversiones
Control
- Cree un usuario de Zscaler para escisiones que permita la separación lógica y de tráfico de red de los activos e interacciones de usuarios, cargas de trabajo y aplicaciones en el ámbito/transferidos.
Segmento
- Implemente conectores de Zscaler para permitir el acceso de usuarios transmitidos a aplicaciones y recursos TSA en una arquitectura Zero Trust.
- Olvídese de la necesidad de una red "clonada y listo" aprovechando Zero Trust Exchange como intermediario para las aplicaciones transferidas
- Traslade a los usuarios transportados a la Wi-Fi pública, eliminándolos eficazmente de la red sin perjudicar la productividad.
Separado
- Integre otras capacidades de perfil de riesgo para proporcionar una política dinámica basada en la postura de seguridad
- Utilice las capacidades zero trust de cargas de trabajo a carga de trabajo para separar aún más el tráfico de aplicaciones transferidas o TSA
Salida del TSA
- Cierre cualquier TSA de red o servicio de seguridad
- Entregue la administración de los inquilinos al proveedor de TI de la entidad separada
- Retire el proveedor de identidad de la entidad retirada si lo hay, de la póliza del arrendatario disociado
- Elimine cualquier acceso VPN heredado o similar a aplicaciones aprobadas por la TSA o transferidas.






