In our telemetry data from last 3 months we have seen following URL serving the DorkBot installer:
api1[.]wipmania[.]com[.]wipmsc[.]ru/api1[.]gif (Check APPENDIX section for additional info.)
- "-aav_start" - It terminates
- "–shell" - It starts the infection cycle, creates a registry key "Windows Update" to ensure persistence, and creates a mutex named “Windows_Shared_Mutex_231_c000900” to ensure only one copy of Dorkbot is running
- Copy itself as "%APPDATA% \Update\Explorer.exe" on the infected system.
- Creates a Run registry key with the name of "Windows Explorer Manager" for the dropped executable copy.
- It creates a thread that monitors the Run key created in step 2 & recreates it if missing, every 10,000 seconds.
- It also creates a thread that copies the file created in step 1 to file name “\c731200” in the "%APPDATA%” folder.
- It then creates a remote thread in mspaint.exe that tries to resolve a predetermined list of domains as shown in image below:
 |
| DorkBot - Hardcoded Domains |
 |
| DorkBot - memory strings |
- Creates a mutex with the name “c731200”
- Checks for Internet connectivity using API InternetCheckConnection with www.google.com as the URL.
- It then tries to download files from 20 different URLs and saves the downloaded file with random file names in the %Temp% folder. File names are shown in the screenshot below:
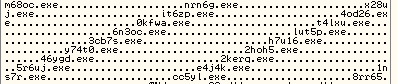 |
| DorkBot- Random file names |
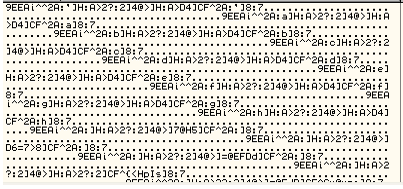 |
| DorkBot - Encrypted URLs |
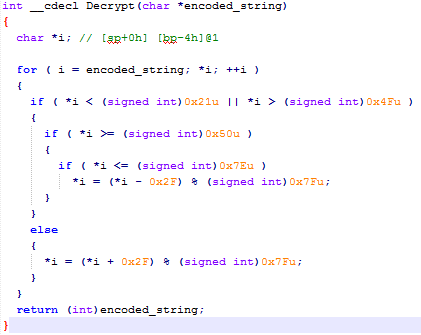 |
| DorkBot - Pseudocode of decryption function |
| URL |
|---|
| http://api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| http://api2[.]wipmania[.]com[.]wipmsc[.]ru/api2.gif |
| http://api3[.]wipmania[.]com[.]wipmsc[.]ru/api3.gif |
| http://api4[.]wipmania[.]com[.]wipmsc[.]ru/api4.gif |
| http://api5[.]wipmania[.]com[.]wipmsc[.]ru/api5.gif |
| http://api6[.]wipmania[.]com[.]wipmsc[.]ru/api6.gif |
| http://api7[.]wipmania[.]com[.]wipmsc[.]ru/api7.gif |
| http://api8[.]wipmania[.]com[.]wipmsc[.]ru/api8.gif |
| http://api9[.]wipmania[.]com[.]wipmsc[.]ru/api9.gif |
| http://api[.]wipmania[.]com[.]fowd[.]ru/api.gif |
| http://api[.]wipmania[.]com[.]selfmg[.]ru/api.gif |
| http://api[.]wipmania[.]com[.]lotus5[.]ru/api.gif |
| http://api[.]wipmania[.]com[.]wipmania[.]ru/lkwaxd.gif |
| http://api[.]wipmania[.]com[.]lotys[.]ru/vjojai.gif |
| http://api[.]wipmania[.]com[.]bwats[.]ru/ofjtme.gif |
| http://api[.]wipmania[.]com[.]stcus[.]ru/apsphv.gif |
| http://api[.]wipmania[.]com[.]cmoen[.]ru/zkmchm.gif |
| http://api[.]wipmania[.]com[.]artbcon3[.]ru/frflec.gif |
| http://api[.]wipmania[.]com[.]yeloto[.]ru/zwfmwd.gif |
| http://update[.]wipmania[.]com[.]raulhost[.]ru/logo.gif |
- Capable of spreading via chat messengers, USB drives, & social networking sites
- Supports multiple Distributed Denial of Service (DDoS) attack types
- Capable of stealing login credentials for multiple HTTP and FTP sites
- Blocks security update related websites to evade detection
- Capable of downloading, installing and uninstalling other malware payloads
|
URL
|
MD5
|
Malware Name
|
|---|---|---|
|
Ernsthaft[.]su/ert[.]exe
|
6C738D0A737D16C87EB40C24C5F594A6
|
IRCBot.HI
|
|
Mslighton[.]net/uploads/io[.]exe
|
C73DBA5827728EEAC59951B14AB329F4
|
RageBot
|
|
Colorfashionbox[.]com/u[.]exe
|
F919C902AC07AF339BBD753E6EFF89C7
|
Phorpiex
|
|
Dumanfun[.]com/t[.]exe
|
DBC477DF90D4ECB37B698C571DE90D11
|
Phorpiex
|
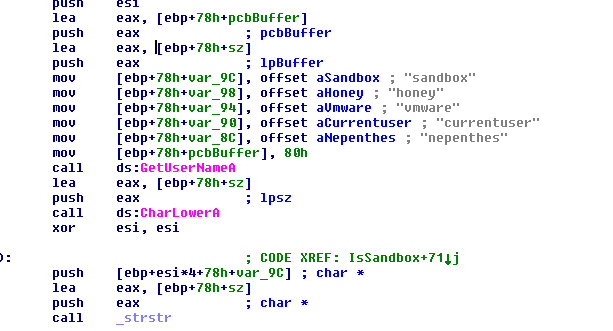 |
| RageBot - Check via Username |
 |
| Phorpiex - Check via DLL name |
 |
| IRCBot.HI - Check via DLL & Product IDs |
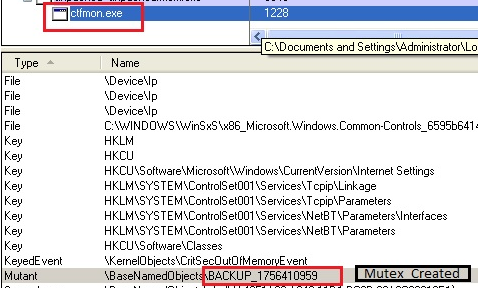
RageBot – It creates a mutex with name “ie”
 |
| RageBot - Mutex |
 |
| Phorpiex - Mutex |
 |
| IRCBot.HI - Mutex |
 |
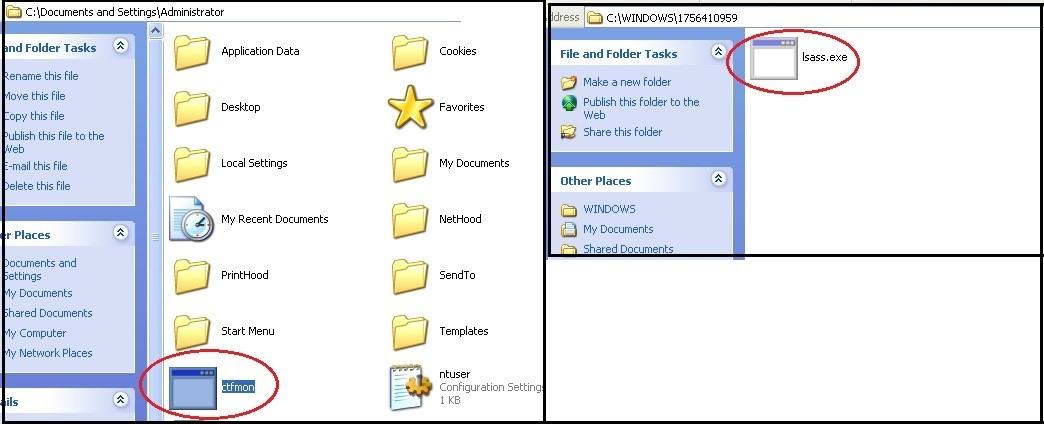
| RageBot – Building installation path |
 |
| Phorpiex – Pseudocode of Installations function |
 |
| IRCBot.HI – Installing in different locations |
 |
| IRCBot.Hi – RunOnce Entry |
"SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List"
- It copies itself to the following P2P & Instant messenger application folders for spreading
- \Program Files\LimeWire\Shared
- \Program Files\eDonkey2000\incoming
- \Program Files\KAZAA
- \Program Files\Morpheus\My Shared Folder\
- \Program Files\BearShare\Shared\
- \Program Files\ICQ\Shared Files\
- \Program Files\Grokster\My Grokster\
- \My Downloads\
- It also searches for RAR files and copies itself inside them.
A. Creates a shortcut in a removable device
- It checks for all removable devices
- Copies itself with a different name
- Creates a shortcut to an already present folder and sets the path of a shortcut to run the malicious file
- Hides the malicious file and folder by setting a hidden attribute for both
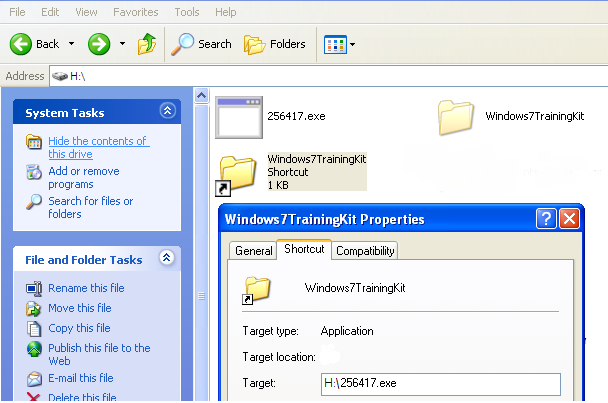 |
| Phorpiex - Creating Shortcuts |
B. Creates an autorun.inf file in removable devices to autorun the malicious file
- Checks for all removable devices.
- Copies itself with a name of windrv.exe
- Creates an autorun.inf file to autorun the malicious file
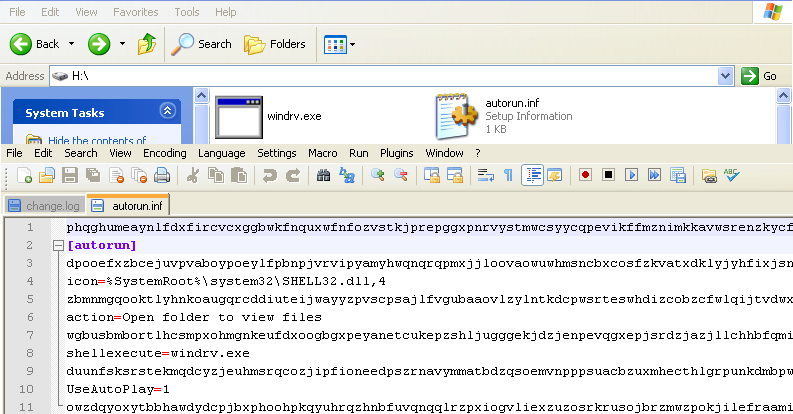 |
| Phorpiex - Creating autorun.inf file |
 |
| IRCBot.HI - Skype inject related string |
 |
| RageBot - C&C Communication |
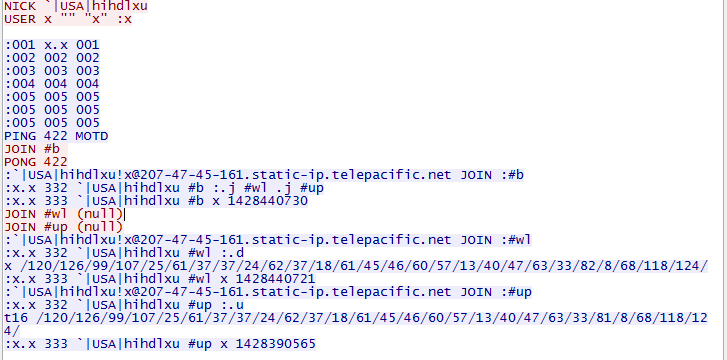 |
| Phorpiex - C&C Communication |
Below is a sample of the C&C communication for this bot:
 |
| IRCBot.HI - C&C Communication |
In this era of sophisticated Botnets with multiple C&C communication channels, custom protocols, and encrypted communication; we continue to see a steady number of new IRC based Botnet payloads being pushed out in the wild on a regular basis. As we saw in our analysis, IRC based Botnet families continue to evolve in terms of sophisticated features incorporated in the bots.
ThreatLabZ is actively monitoring this threat and ensuring signature coverage for Zscaler customers.
Appendix
DorkBot installer URLs and MD5
| TIME | MD5 | URL |
| Jan-15 | E49B3EF80FF4DB4DB1D5220930EC7DAD | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | CC9D72663D2495779B0C81AEE34592E7 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | A98472BCAA010433A80410C3483C90E1 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | EEFC72EFFD96FFD11EC2D69CD6248AC5 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 4E7149C1401F5A0BC34E3AAD6070F4BE | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 5B14C029570F40BDDC73669FE4EFEFB0 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 4C54D366B04F9980F038CB6FC62603D0 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 6E4282023D6A19B27C30DB5D54CEE32C | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | E7B61B2BE23167965079468DF36497EF | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | DC8CBA3F91A34F0D1EFA79BE4495B305 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 8AAD291926335F28B4402830252556F7 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 8036A36C372602CFA049996B9F5BD6AE | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 8036A36C372602CFA049996B9F5BD6AE | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 7257FD6F90B5AA9BB249EA74B764A401 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | B186525826856E881E879C6C44BB2452 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 220188F1BD2E10BA0751383EA0946DBA | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 2DB9BD0ABD99F3285721D358A6816737 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | EBEB072B8336F5FD35328227A60B271C | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 01303BEFE5938C3C748C4E058A8A6AE9 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 82E2CA09BDEB3ABF8B70D848F66793E7 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 0B2E7AE8DF2ADA1E86A3A25FC248C6FE | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 430560EBD3BE6A680BFA6409F332585B | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | F79AF05D9B43F99EB6FC64DA2C129F67 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 384252746FAFF8D264E6A8CA450B6301 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | C9636239ED698834CABA78E1F9F8DB0F | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 9C42746376CC7D265D6BF554B960EDE2 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 67B08BF0F2C89DE4E0D1C36BAF7193B9 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 735B6602B4BD1D71246F43642D6873AA | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 7D9AF61AE962443D586BFC8A86100B5F | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 05ABC48A4BEE624D7952954CF14F699D | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | FF638ACA7D8D10ED8AD2DE1BC333123D | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | AA4085182E8F10FEC8EBC3F6D3612321 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 1A54593E7C82DD1B16B7626FCB211DA1 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Jan-15 | 235E67A88907DA68BFBB9264A00A31E3 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 2CBD9428DEE885C30258BF0C38299138 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | CCDC5EC2085536160813658BE549F0B6 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | CBD732F87901EE03820DBA41D0D2895A | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | BE5E43F2786D628B7AA8689C2108247D | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 5AEC4A3B3E0AEB3B13B98086FC81D797 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 6034814DB1C25A092C39F251F29B2216 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 6CAE0B51E5EAD86EEA47C4068287650A | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 451E324D3CB601E00FA041D6FDE1C4EC | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 9AEB3A097F11887D89EC08D337814B6B | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 8F9F97232DBE283BC5E7B6AB4DD580B8 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | F57A08679380F3FDFD369528FE5CE854 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | F24BC22CFD12E3FDE40D06BF54F35CF1 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 4BB4C19B5FC2401D45845789CC761577 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 583432D95424EC051AFE9E621DC41ACA | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | C5756AC3FE61266D326B43E904BC1A6C | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 44012367D7FFA7845B59462952AB9014 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | FC506F023FF71E3ACDEE4449C43E5F1B | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 322E11B552B897ADBC9ABCE51774988E | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | EC0832E5818E4CD753C4B2675C6179A1 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 63C37B2FEB0C0F71568B9771AC4DACE4 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Feb-15 | 7BE4749D1D1F8950F7288C67A393B7F0 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | ADDF9E2B207AD9E89DB46E81A8121882 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 3E70DB4E5F5F60F2FDE7AEC38F4B30CD | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 268301147BC53722A898E1F38E6F026D | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 309FB15C08861BC063C19C326A29AC98 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 422C1A2BC53F72CAE5435F7F5598BDFD | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 30A6C9DC574075C5EA47F17EA9392C47 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 37A9570400CB0C0CD4E5273AE3232EB5 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | E59BCA5EE865FE5789C96B20A43F9207 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 919C861E6A6ABF88045476D5D92A5DE1 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 5FD98DE177F158C31960BF80272F2535 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 9439AA18598643131B3F8DD9E69AB294 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | F66A06166B73391C4C7A7A58CC6CE66C | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 79589FC33375A63BB44A8DE0B2B5DAF8 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 2C328EF3F2074D68729F329D4B2F8013 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 90E8FF73C7E78B99ABCD1FC22394F22E | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | A3AEC401831AF6EF1C75AFB1C50D96DA | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 42C7C8719D33AFCF36DC7D5D2594EB5B | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 375E51758336183B07CA7DBF771D2EF8 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | FA20E413002E17B938B2451552721027 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 09840FA1887528B20C98C408C8EB6E07 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 6AB2975E77EA4724FADF4CCB7250F0E9 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 51E7E34FFB5EF17FDE5FAFC5DF8F7212 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | F61E3F5ACFE1F861CECEA0A793D4F333 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 229236B39E92E629178419CB8A529E1A | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | D299AD2A61F325F5DA56AE7674D2F77D | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 53CA20232F358A9C256748403451EF14 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 41BE96D1B3BDF9E48D97AE153D6EFD45 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
| Mar-15 | 213E0B42AF7CF1D0DCB75E378CA93512 | api1[.]wipmania[.]com[.]wipmsc[.]ru/api1.gif |
RageBot Commands
| Command | Description |
|---|---|
| PING | Check status |
| 422 | Check status |
| 433 | Redefine nick name |
| -s | Silent mode |
| h 0f6969d7052da9261e31ddb6e88c136e | Uninstall bot. |
| h fd456406745d816a45cae554c788e754 | Download and run file |
| Botinfo | Sends botinfo |
| p2p | Starts p2p spread, Copy itself into following location- \Program Files\LimeWire\Shared \Program Files\eDonkey2000\incoming \Program Files\KAZAA \Program Files\Morpheus\My Shared Folder\ \Program Files\BearShare\Shared\ \Program Files\ICQ\Shared Files\ \Program Files\Grokster\My Grokster\ \My Downloads\ |
| commands | Sends following list of commands commands: botinfo/rarworm/xpl/p2p/vncstop/disconnect/reconnect/nick/restart/part/join/ |
| rarworm | Scan for .rar files and copy itself into .rar archives with name as ?self-installer.exe? |
| disconnect | Disconnect itself |
| b0tk1ller (off) | Starts a thread that scans for the running processes and terminate the process if process name matched with hardcoded process names. If parameter off is provided it stops the bot killer thread. |
| reconnect | Reconnects to the same server |
| reconnect.next | Same as reconnect since there is only one ip hardcoded in the bot. |
| nick (nickname) | Sets nick name if nickname not provided that generates random nickname |
| restart | Restarts itself |
| vncstop | Stop VNC scanning threads. |
| join (channel_name) | Join mentioned channel |
| xpl | Starts vnc and ftp scanning threads. |
Analysis by: Amandeep Kumar, Avinash Kumar, Nirmal Singh & Deepen Desai





