In a recent presentation at the Cloud Security Alliance Summit 2017, Frederik Janssen of Siemens made a statement that was bold and yet self-evident: “The internet is the new corporate network.” Janssen is the Global Head of Service Portfolio and Lifecycle Management of IT Infrastructure at Siemens, a global corporation that generates annual revenues of nearly 80 billion euros. The company has more than 350,000 employees in 192 countries.
During a recent webcast with Zscaler, Janssen recounted his company’s journey to the cloud and the strategy that guided it.
“As you move more and more applications to the cloud, you have to deal with a situation where you are not in control of all endpoints, and you cannot physically secure the networks you are using across your entire IT landscape,” said Janssen.
This realization caused Siemens to embark on a journey to provide a fast and secure direct-to-internet experience for all users as their primary “online” experience; this journey proved transformational for the Siemens IT strategy and led the company inevitably to the cloud.
A moat only works when there is a castle
To help illustrate the nature of the change, let's go back to a medieval notion of security when we defended ourselves with castles, moats, and drawbridges. At the time, those were the leading defenses. The nobles and all of their valuables were locked safely behind the massive stone architecture. But as people left the castle in search of new lands and greater opportunities, the walls no longer protected them.
Bringing that analogy forward, corporate networks have been secured from outside threats in much of the same “castle and moat” mentality.
Security gateways, primarily composed of purpose-built security appliances, have served as the drawbridge between the corporate network and internet, with guards protecting the traffic flowing in and out. But as applications have moved to the cloud and users have become mobile, the guards are no longer able to protect them. They’re still standing at the gateways, protecting the valuables inside, but the valuables are long gone.
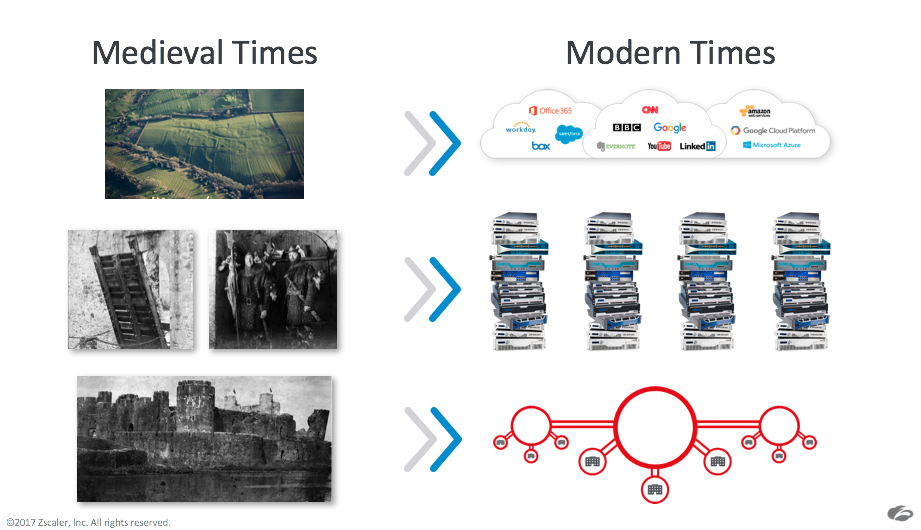
This new reality led Siemens to rethink its approach to security, essentially doing away with the idea of a trusted corporate network — a shift in thinking that has impacted every level of the Siemens IT strategy. With an organization of Siemens’ size, a digitalization of such magnitude puts a significant burden on the IT department as it copes with new requirements and technologies. Janssen and his team had to rethink their approach to network structure and user connectivity.
The Siemens model for transformation
In a recent webcast, Janssen outlined the four-layer model that guides the Siemens network transformation strategy.
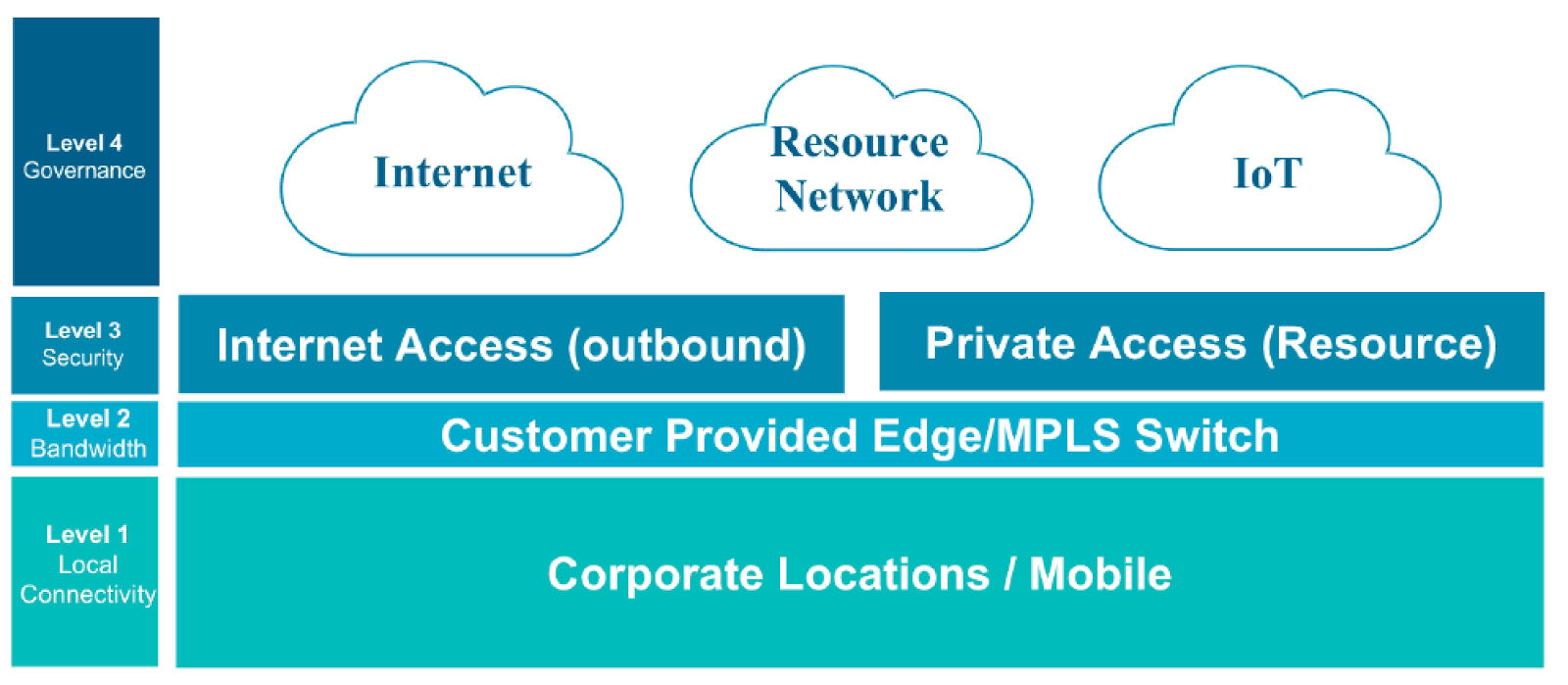
It starts with a simple question: if the end destination is an application accessed over the internet, and thousands of devices and individuals need to connect to that asset from hundreds of locations, wouldn’t the internet be the best connectivity method?
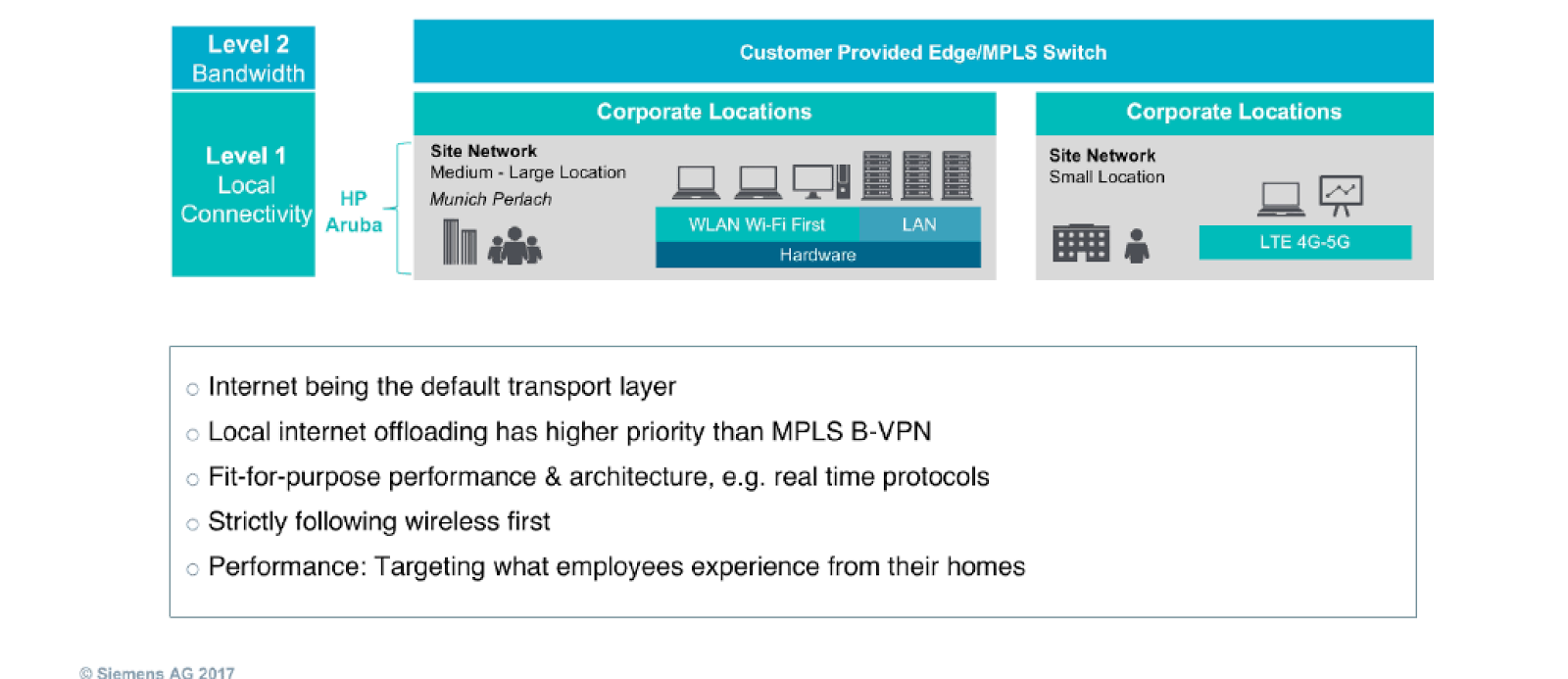
In the Siemens model, level one and two address local connectivity and bandwidth — how do we connect users to the internet? What service providers are involved, and how do we route the user to the internet as quickly as possible?
In this model, the focus is on creating a user-centric experience and scalable architecture with support for real-time protocols. The architecture must be able to perform at a level that users accept, one that enables them to be productive.
At level three, Janssen emphasized the importance of a scalable security architecture that can follow the user and leverage the internet as the corporate network. This is where Siemens turned to Zscaler to help deliver cloud-based security as ubiquitous as the internet itself.
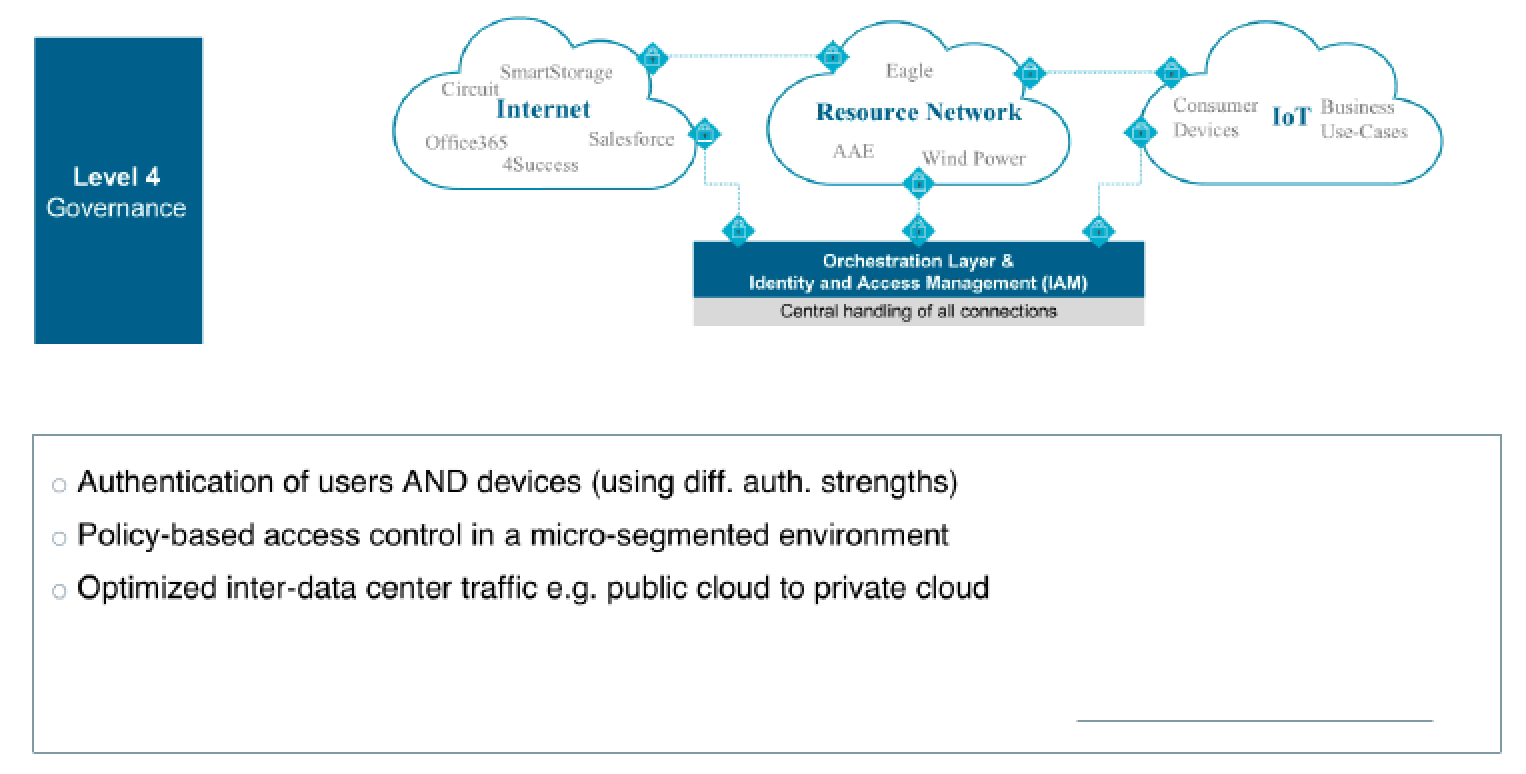
The fourth and final layer is dedicated to governance and orchestration. Here, Siemens needed to make sure that it maintained visibility and control over users, devices, and applications. It was a requirement for Siemens to be able to authenticate not only users, but also different devices, across different regions, using different authentication mechanisms.
Business agility is the goal – security is the enabler
In the past, security and networking teams talked in terms of reducing risk, stopping threats, and protecting critical assets. These abilities remain important, but the conversation has shifted and has become more centered around business agility.
SaaS applications, public cloud, and mobility offer organizations fast access to resources that can help propel a business forward by cutting down development times, making employees more productive, and reducing the cost and complexity of supporting a broad range of applications. However, agility without security presents more risk than an enterprise should be willing to take on.
But rather than simply saying “no” to a cloud-first strategy, forward-looking teams are finding new ways to transform their networks and security to thrive — not just survive — in the cloud.
Today, Siemens has fully deployed Zscaler Internet Access worldwide, covering 350,000 employees and 450,000 workplace systems, and is nearing full deployment of Zscaler Private Access. With the Internet as the company’s default transport, instead of expensive MPLS and business VPNs, the company is seeing dramatic cost reductions and is reducing network complexity.
Ultimately, Siemens was looking for a simpler more flexible way to provide fast, secure access to applications while also adhering to the many different regulations governing access and storage and privacy in all the different countries.
This really is the promise of digital transformation. Moving away from legacy architectures gives you a more agile, future-proof network that enables employees to access the resources they need, securely providing better performance, resiliency, and reliability for the entire organization.





