Rubrik's integration with Zscaler secures sensitive data by combining data-at-rest intelligence with data-in-motion security.
Sensitive data proliferation and exfiltration
More users are storing sensitive data in SaaS applications, data centers, and the cloud, making it vulnerable to ransomware attacks and exfiltration. Bad actors are also using cloud storage, collaboration apps, and personal email apps to exfiltrate data.

BENEFITS
Effective data protection across the enterprise
Secure content management
Gain visibility in the files classified as sensitive by the Rubrik Security Cloud and evaluate the content movement with the industry-leading Zscaler Data Protection.
Prevent data exfiltration
Secure sensitive data across your organization, whether it’s being uploaded to an internet resource, accessed by BYOD, or attached to personal emails, with custom remediation and response policies.
Enhanced compliance
Details
Rubrik Security Cloud and Zscaler Index Document Match (IDM) integration allows you to:

The Rubrik Security Cloud identifies sensitive information in your data and classifies it accordingly. The content is then made available to Zscaler IDM for indexing. Learn more about Zscaler IDM here.

Zscaler Data Protection applies security policies to data moving to and from applications and platforms, preventing sensitive data from being exfiltrated.
OUR PLATFORM
Zscaler DP and Rubrik work together to protect your data
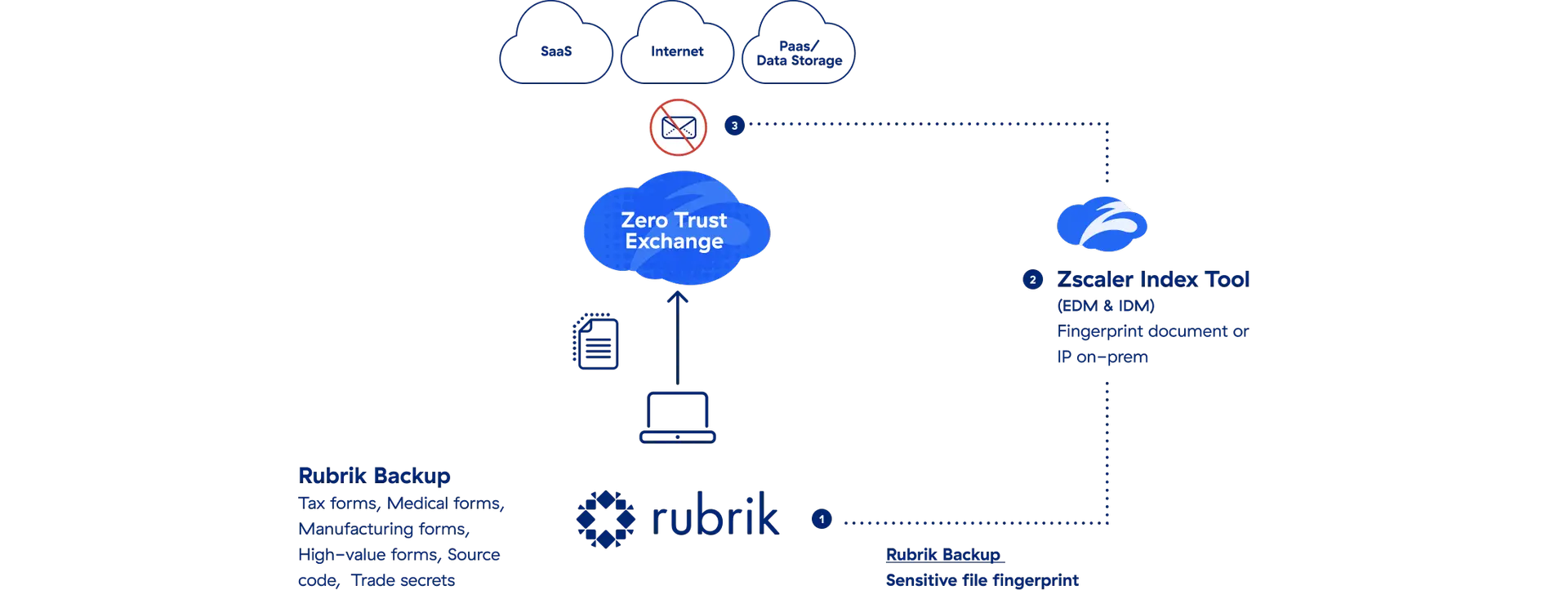
Discover. Rubrik identifies sensitive content and sends it to Zscaler.
Evaluate. Zscaler evaluates the movement of the sensitive data.
Protect. DLP policies are applied to prevent the loss of sensitive data.