Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Enhanced Threat Detection Using Zscaler and Amazon GuardDuty
As cloud environments grow more complex, security teams need enhanced threat detection capabilities to protect their organizations. Sophisticated attackers are using compromised credentials to move laterally through cloud environments while evading detection. According to IBM’s 2024 Cost of a Data Breach Report, breaches from stolen or compromised credentials are taking the longest to identify and contain, at an average of 292 days, and resulting in the highest costs, at an average of $4.99M.
The Value of AI and Automation in Security
Organizations using AI for security reduced breach costs by $2.2M and shortened their breach lifecycle by 100 days compared to those without these capabilities. In fact, a key finding of the analysis is that the more organizations use security AI and automation, the lower their average breach cost.
Building on these insights about the value of automated, intelligent security approaches, this post demonstrates how to strengthen cloud security by integrating Amazon GuardDuty with Zscaler's security solutions.
Integrating Zscaler and GuardDuty enhances threat detection and response through automated intelligence sharing. Let's examine the key components of this integration:
Zscaler Deception
Zscaler Deception detects threats by placing AI-powered decoys throughout environments. As part of the Zscaler Zero Trust Exchange platform, this technology spots lateral movement and privilege escalation attempts that traditional security tools often miss. The decoys mirror authentic resources to identify credential misuse and attack activity. Machine learning models analyze decoy interactions to detect attack patterns, while the system restricts access to sensitive resources when threats are detected, stopping attackers before they reach critical assets.
Zscaler Internet Access (ZIA)
Zscaler Internet Access (ZIA) is a cloud-delivered secure internet gateway that provides consistent protection regardless of location. Organizations can direct AWS traffic to Zscaler using GRE or IPSec tunnels or Cloud Connector appliances. Positioned between workloads and the internet, ZIA inspects all traffic inline, including SSL, and offers comprehensive security services such as Cloud Firewall, Intrusion Protection Service (IPS), Sandboxing, Data Loss Prevention (DLP), and Isolation.
Amazon GuardDuty
Amazon GuardDuty is a native AWS security service that continuously monitors cloud workloads for malicious activity. Using machine learning and threat intelligence, GuardDuty analyzes multiple AWS resources and generates prioritized security findings. Teams can review these findings in the console or automate responses through AWS Lambda functions and workflow integrations.
This post shows how to detect and block threats in AWS environments by integrating Zscaler's security solutions with GuardDuty. We'll explore two integrations: Zscaler Deception alerts enhancing GuardDuty's threat monitoring, and GuardDuty intelligence powering ZIA's automated blocking capabilities. Through architecture diagrams and step-by-step implementation guidance, we'll show how these integrations work together to strengthen your security operations.
Integration #1: Enhancing GuardDuty with Zscaler Deception Intelligence
By integrating Zscaler's AI-powered Deception technology with GuardDuty's monitoring, organizations can detect lateral movement and privilege escalation attempts across their infrastructure. Zscaler deploys multiple types of decoys that appear identical to authentic resources, identifying when attackers misuse authorized credentials to move through the environment. When Zscaler's decoys detect this attack activity, they generate threat alerts that are ultimately sent to GuardDuty, which processes this data alongside data it has gathered from the AWS infrastructure. An AWS Lambda function fetches the Deception threatfeed from a web endpoint and stores this information as a flat text file in an S3 bucket. GuardDuty retrieves these findings at user-specified intervals, incorporating them with data from the AWS infrastructure. GuardDuty's machine learning models then analyze this combined data to identify threat patterns and potential attack paths. Teams can review GuardDuty's prioritized security findings in the AWS console or trigger automated responses through AWS Lambda functions and workflow integrations to contain threats before they reach critical assets.
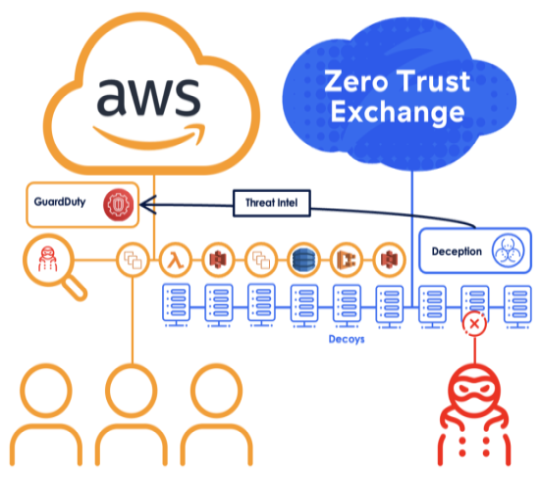
Scenario: Catching Attackers Using Compromised Credentials
An attacker phishes an employee's credentials and begins exploring the network for high-value targets - admin accounts and sensitive data. Their activity looks legitimate to traditional detection methods because they're using real credentials. But when they access one of Zscaler's decoys, they reveal their presence. The integration of Zscaler Deception and GuardDuty turns these deceptive resources into an early warning system, catching attackers during reconnaissance before they reach their targets.
How It Works
- Deceptive Assets: To lure attackers into revealing themselves, Zscaler Deception deploys decoy EC2 instances that mimic high-value database servers and plants fake AWS credentials with apparent elevated permissions. These deception elements serve as traps designed to detect unauthorized access attempts.
- Attack Detection: When attackers interact with these decoys - whether accessing fake servers or attempting to use planted credentials - Zscaler generates an alert.
- Alert Processing: This alert is published to a web endpoint where a Lambda function scrapes it and places it in an S3 bucket for retrieval by GuardDuty.
- Response: Security teams then receive a consolidated alert in the GuardDuty console, showing where attacks originated, what actions were attempted, and which resources were targeted. Teams can then trace the intrusion path and trigger automated response playbooks to contain the threat.
Next Steps: Implementing the Solution
Deploy this integration using the CloudFormation template and detailed instructions available in the Zscaler and Amazon GuardDuty deployment guide.
Integration #2: Automated Zscaler Firewall Updates from GuardDuty Intelligence
By integrating GuardDuty's threat intelligence with Zscaler's Zero Trust Exchange, organizations can automatically block traffic to malicious destinations across their infrastructure. GuardDuty continuously monitors AWS environments using machine learning models to identify suspicious activities and potential threats, generating detailed findings that include malicious domains and IP addresses. In this integration, a Lambda function automatically extracts the suspicious FQDNs and IP addresses from the GuardDuty findings every five minutes, forwarding them to Zscaler Internet Access (ZIA). ZIA then creates or updates its IP and FQDN Destination Groups with this threat intelligence, applying these updates to firewall policies that block and log access to flagged destinations. Each Lambda execution refreshes the Destination Groups with current threat data, while GuardDuty's age-out mechanism ensures that expired threats are automatically removed from the security policies. This automated synchronization between GuardDuty and ZIA creates a self-maintaining security perimeter that continuously adapts to emerging threats without manual intervention.
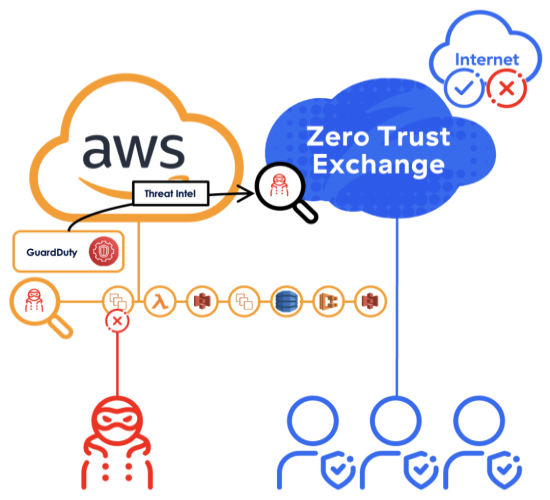
Scenario: Protecting Cloud Resources from Unauthorized Cryptomining
Cloud resources are frequently targeted by attackers who hijack computing power for cryptocurrency mining operations. Their typical approach involves compromising EC2 instances to secretly install mining software, which results in excessive resource consumption, unexpected cost increases, and potential security breaches. The GuardDuty-ZIA integration addresses this threat by automatically detecting and blocking connections to known mining pools and command-and-control servers. This immediate response prevents attackers from establishing mining operations, protecting both cloud resources and business operations from compromise.
How It Works
- GuardDuty Continuous Monitoring: GuardDuty tracks cloud activity patterns using machine learning models to detect anomalies. It analyzes API calls, resource usage, and communication with known mining pools to identify potential cryptomining operations.
- Threat Detection: When GuardDuty spots suspicious activity - like abnormal CPU spikes or connections to mining infrastructure - it generates detailed findings containing malicious domains and IP addresses associated with the mining operation.
- Automated Processing: An AWS Lambda function retrieves these GuardDuty findings and extracts the threat indicators. The function processes this data and prepares it for immediate enforcement action through Zscaler's platform.
- Threat Blocking: The processed threat data is automatically pushed to ZIA, which updates its firewall policies to block all communication with identified mining infrastructure. This prevents compromised resources from connecting to mining pools and command-and-control servers across the organization.
Next Steps: Implementing the Solution
Deploy this integration using the CloudFormation template and detailed instructions available in the Zscaler and Amazon GuardDuty deployment guide.
Combining GuardDuty and Zscaler creates a powerful, automated security solution for cloud environments. This integration combines AI-powered threat detection with automated response - a highly effective approach that, according to IBM's 2024 Cost of a Data Breach Report, reduces compared to organizations without AI security capabilities.
The integration requires minimal setup - just configure the Lambda functions and integration endpoints once, and the system handles threat detection and response automatically. GuardDuty findings trigger immediate Zscaler policy updates, while Zscaler's Deception technology enhances GuardDuty's threat detection capabilities.
Ready to strengthen your cloud security? Enable Amazon GuardDuty in your AWS Console and get started with Zscaler solutions on the AWS Marketplace, or contact your AWS and Zscaler representatives to learn more. For implementation details, refer to the Zscaler and Amazon GuardDuty Deployment Guide, or experience it first-hand with our ZIA demo and Deception demo.
This blog post was co-authored by Aaron Rohyans, Sr. Principal Solutions Architect at Zscaler, Gina McFarland, Partner Solutions Architect at AWS, and Travis Niedens, Sr. Partner Solutions Architect at AWS.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




