The cloud is a great place to innovate. But managing the security risk, sensitive data, access to data, and compliance of your complex cloud-based environment can be very challenging. Today, many CISOs and IT leaders find themselves grappling with the growing complexity of their increasingly multi-cloud and distributed IT environments and with ever more sophisticated and aggressive cyber attacks. The rising number of cloud data breaches due to simple service misconfigurations and excessive permissions is forcing security practitioners to rethink security and adopt approaches that better address the needs of developers building the dynamic, distributed cloud infrastructure.
Gartner predicts that misconfigurations and privileged entitlements will be the top root causes of successful cloud security breaches for a long time to come.
Security leaders must take proactive steps to increase visibility, control, and secure cloud environments to address cloud security threats. Emerging tools, including Cloud Security Posture Management (CSPM) and Cloud Infrastructure Entitlement Management (CIEM), can help identify and prioritize risks across a multi-cloud environment. Here are five valuable tips for Information security practitioners and security architects to better your Cloud Security Posture.
Tip 1: Prioritize the biggest risks
Organizations need to evolve from reactive and defensive security posture management to being proactive by contextualizing risk intelligence. Risk prioritization is essential, and it covers the broad set of identified risk events, their impact assessments, and their probabilities of occurrences are "processed" to derive a most-to-least-critical rank-order of identified risks. A significant purpose of prioritizing risks is to form a basis for allocating resources.
Information security practitioners are not able to effectively focus and prioritize risk due to:
- Multiple assets, data, and access points
- Visibility gaps
- Dynamic and ever-changing cloud environment
- The time-consuming and cumbersome process of data collation
The best way to manage risk is to monitor and aggressively prioritize risk with CSPM proactively.
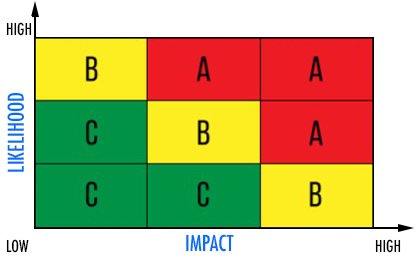
Figure 1: Heat maps communicate risks to business audiences effectively and in a limited time frame.
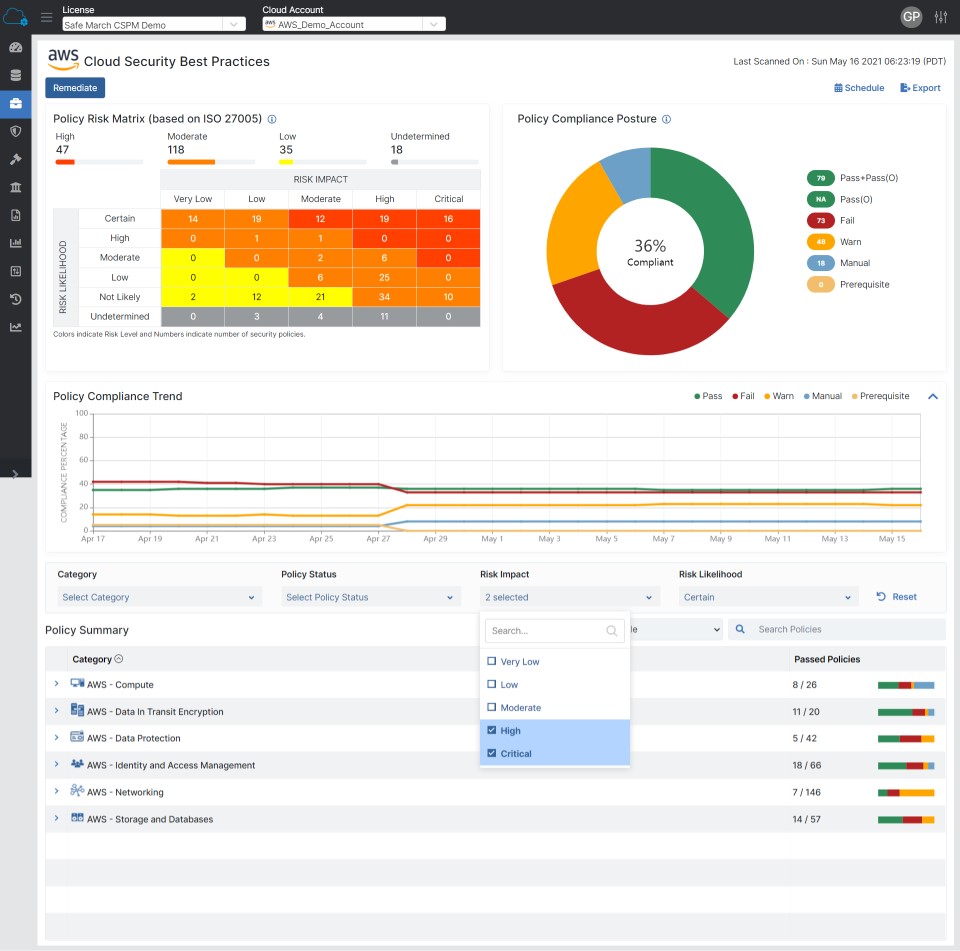
Figure 2: Zscaler Workload Posture Risk Prioritization Matrix
Tip 2: Vary security practices by workload
Cloud workload security best practices vary depending on the type of cloud services, such as IaaS, PaaS, SaaS, and serverless. You have more control over virtual machines, including the operating system, deployed agents and applications, connectivity choices, etc. Whereas Serverless functions are just micro compute instances, your control over it will be when and where they will execute the code you upload. Your level of control, as well as the possible risk exposure will be different for every service and workload type.
CSPM and CIEM will let you distinguish, understand and remediate issues for various types of workloads, including compute, storage, databases, access, networking, serverless, Kubernetes, and PaaS services.
Tip 3: Automate security policy governance
An organization needs to automate and customize its security policies to easily control multi-cloud environments, including policy override, exclusion, cloning, creating baselines, and applying them selectively or holistically across all cloud environments.
CSPM and CIEM help govern cloud security policies, privileged access, create custom and private benchmarks, monitor open violations, enforce least privileges and consistent security policies and track remediation efforts in real-time. It also ensures an agile, secure development environment. The level of automation you employ should be customizable for the specific needs of your organization and your internal processes.
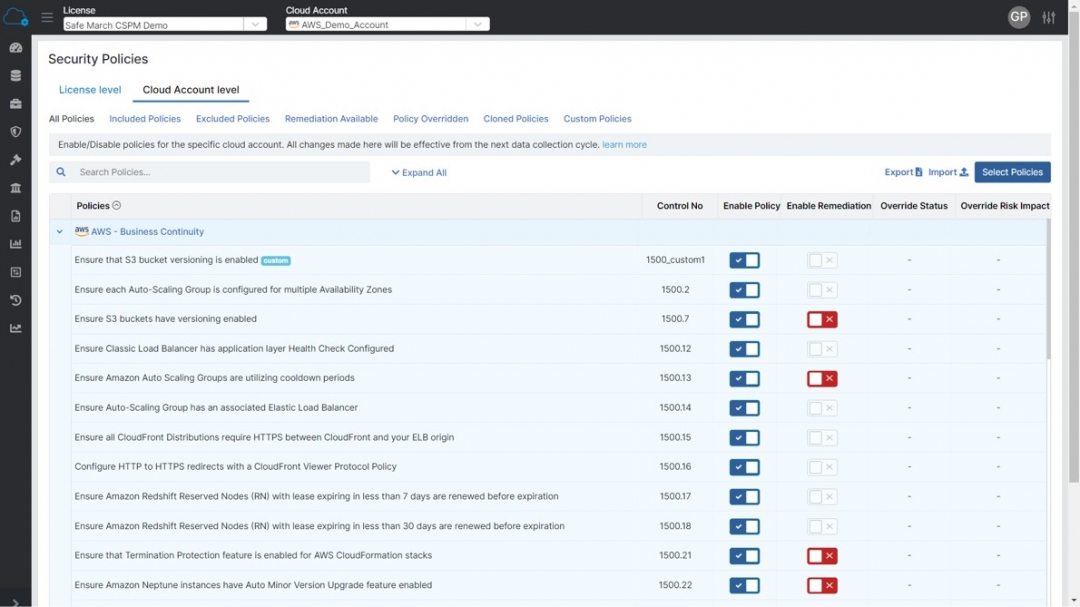
Figure 3: Cloud security policy
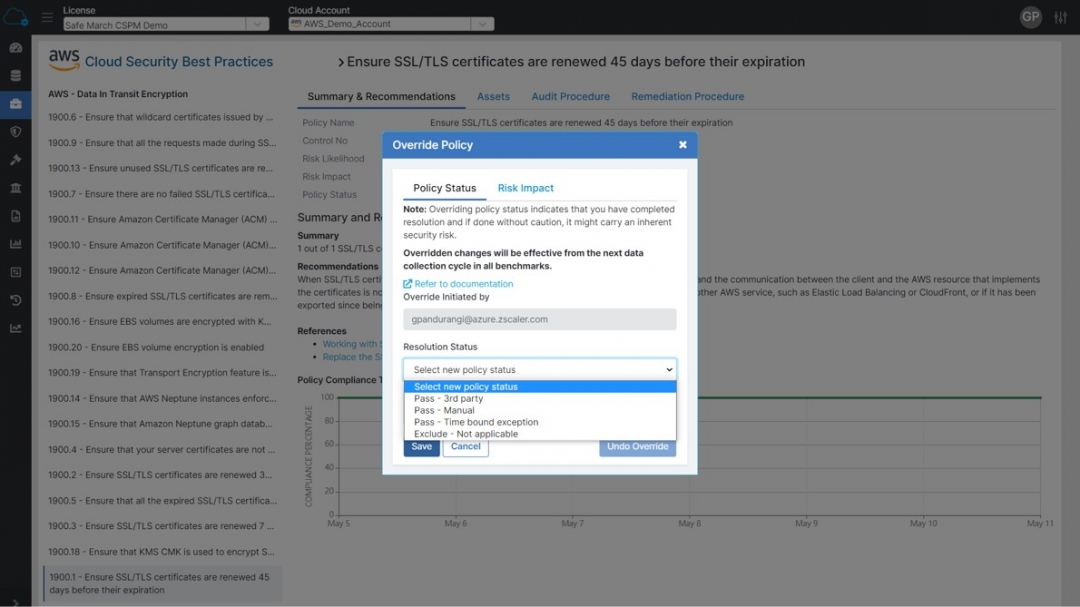
Figure 4: Flexibility to set up custom policies for specific needs of organizations
Tip 4: Enable collaboration across your organization
Typically, InfoSec, Security Operations Center (SOC), and Application Development (AppDev) teams enable and implement cloud security strategies to protect critical information, services and applications. While the InfoSec team is responsible for setting the corporate standard (goal), the application development and infrastructure management teams ultimately implement security and compliance standards.
There are typically three phases of cloud security implementation.
- Phase 1 – InfoSec, Cloud Security Architects, and the CISO/CTO understand the environment, assets deployed and get comprehensive visibility of the current status.
- Phase 2 – GRC, DevOps, SOC, and various teams get involved in the security governance and remediations phase and consider various hardening, policy management, and remediations processes.
- Phase 3 – SOC and GRC teams focus on continuous monitoring and maintaining healthy security posture
Deploying comprehensive CSPM and CIEM improves collaboration between InfoSec, Security Operations Center (SOC), and application development (AppDev) teams.
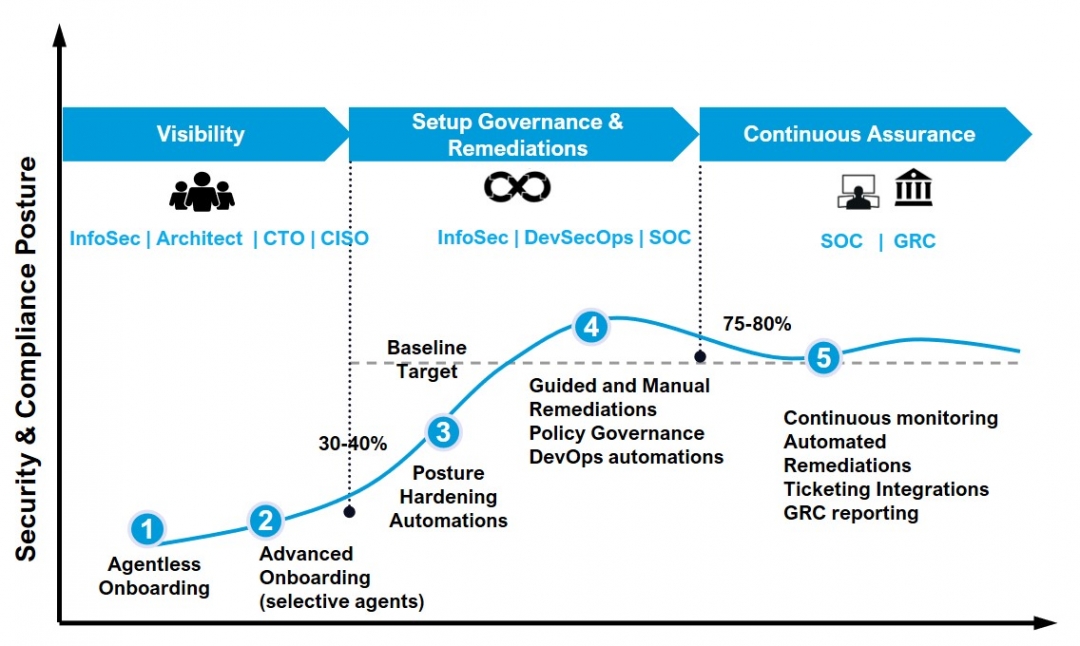
Figure 5: Cloud security deployment and team collaboration
Tip 5: Integrate security guardrails into your DevOps toolchains and IT systems
Security is an integral part of any software, but it’s often neglected during the software development process. Finding and resolving security issues early, before making their way to production, can minimize risk and save valuable time and costs. Automation makes sure security becomes part of SDLC seamlessly.
Embedding security into the software development life cycle (SDLC) through automation is a better approach rather than manual processes because:
- The cost of remediating a security vulnerability post-production is much higher than addressing it in the earlier stages of the SDLC.
- Embedding guardrails enables organizations to mitigate risk and ensure cloud deployments are secure and compliant without impacting development speed. Automation makes sure security becomes part of SDLC seamlessly without impeding innovation.
Tools such as CSPM and CIEM ship with various integration options spanning the SDLC life cycle from automatic provisioning when adding or building new applications to continuous deployment modules. It helps to
- Reduce the risk of misconfigurations, excessive permission, and data exposure
- Unify security and compliance visibility across for DevOps team into every resource deployed
- Seamlessly integrate security and compliance checks at any stage of the development pipeline.
- Data feed and various APIs allow pulling, slicing, and sending the relevant data to appropriate systems.
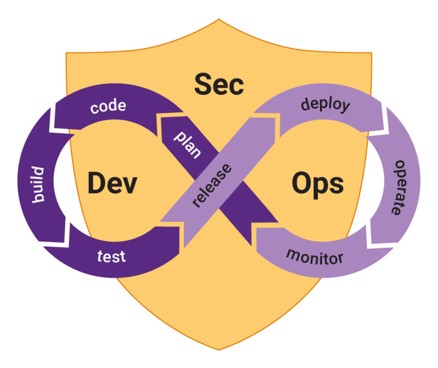
Figure 6: Integrate CSPM into your DevOps toolchains and IT systems
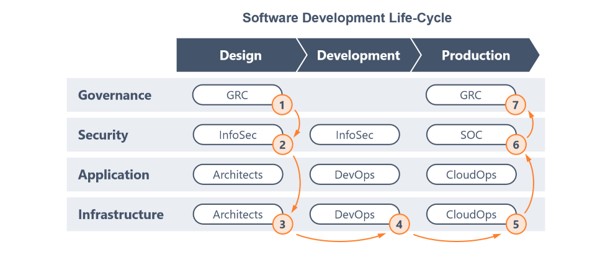
Figure 7: Integrate Security into the development and operations lifecycle
Conclusion
A comprehensive approach towards cloud security with CSPM and CIEM answers the increasing requirements of organizations to address cloud security risks and misconfigured public cloud services. It can help in continuous risk assessment, IAM control and visualization, data protection, incident responses, compliance, and DevOps integration.
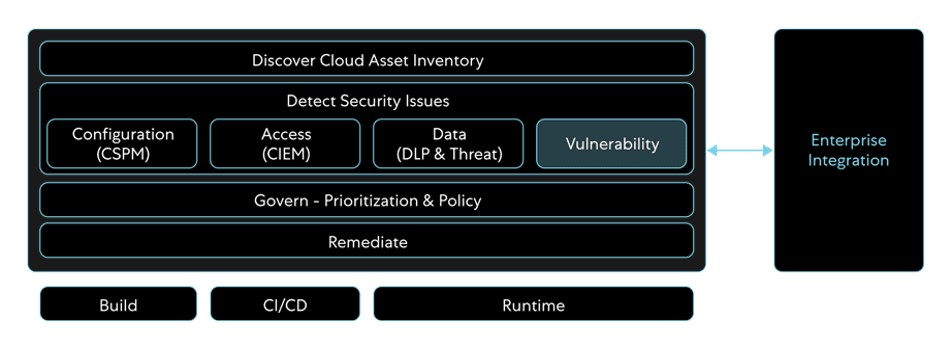
Figure 8: Achieve security posture for cloud workloads across the lifecycle
How does Zscaler Workload Posture help organizations maintain cloud security posture?
Zscaler Workload Posture remediates misconfigurations, secures sensitive data, and enforces least-privileged access across public cloud footprint.
- Cloud administrators can simply connect their cloud accounts across various providers to Zscaler Workload Posture using agentless or API.
- Within minutes, it discovers different types of workloads, clusters, PaaS and Serverless services, asset inventory, and their associated configurations.
- Brings security and compliance visibility across 1000s of security best practices and 16+ compliance frameworks.
- Next, it helps customers wade through the findings with risk-based prioritization views and provides various mechanisms to drive policy-based governance.
- With many integration options available, organizations can roll these out to work with various IT systems across Ticketing, CI/CD, Reporting, IaM, and SIEM systems.
- Lastly, Workload Posture helps to remediate issues either automatically or through guided workflows.
Zscaler Workload Posture delivers tangible benefits:
- Accelerates your cloud adoption by constantly reducing risk
- Enables cloud governance at scale by bringing together multiple teams within your enterprise.
Talk to our experts or schedule a demo to discover how Workload Posture can help reduce the risk of data breaches.
MORE RESOURCES:
Datasheet: Cloud Workload Posture
Blog: How to Find Externally Exposed Cloud Data
Case study: Jefferson Health





