This post also appeared on LinkedIn.
Most IT security professionals would agree that the key ingredient for safeguarding networks is “reducing the attack surface.” Fewer avenues for breaches means reduced risk and fewer incidents for an enterprise: Hackers can’t attack what they can’t see. Reducing attack surface exposure really is the secret to securing your network, applications, and—most importantly—your data.
I embraced the “reduce the attack surface” mantra back in 2015. Five years into my IT security journey, it is still my mission. I am more convinced than ever that it is critical to preventing network breaches—now and for the future. This one principle dramatically reduces the risk of your enterprise succumbing to the next ransomware attack or data exfiltration.
Calling all servers . . .
The “attack surface” comprises the sum of all exposed points through various vectors that an attacker could target to compromise a computing device or network. You can group the attack vectors into three main categories: the channel (a listening TCP/UDP port), assets (which include applications, services, webpages, files, executables, etc.), and access (user credentials). Below is a breakdown of the various attack vector options available to attackers.
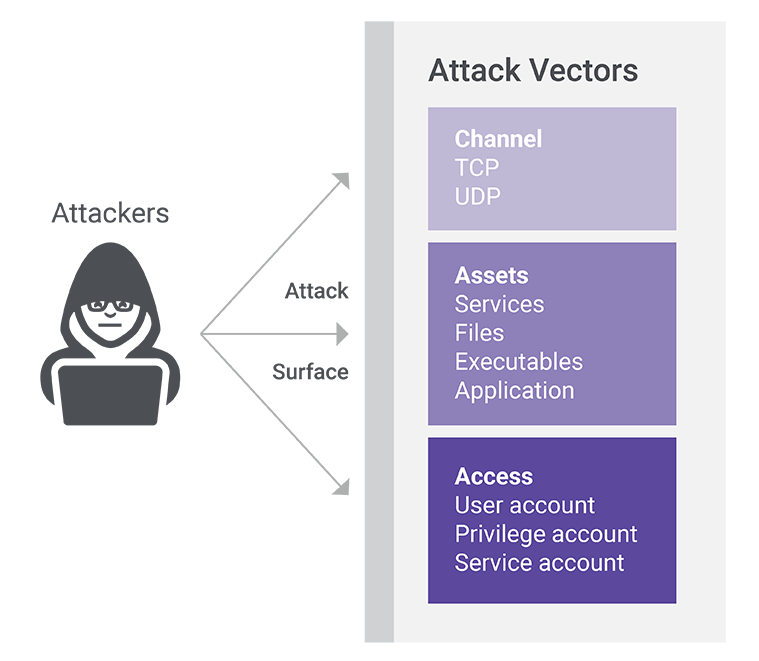
The channel—typically an exposed-to-the-internet communications protocol like TCP or UDP—allows all entities on the internet to communicate with each other. It’s how you gain access to networks, applications, and your data. It’s also what exposes these same assets to attack.
For example, a TCP SYN handshake consists of a SYN request to a web server (on port 443), a server SYN/ACK reply, and a final sender ACK. This establishes a connection and allows data to be sent and received—before any authentication of the source happens. Bad actors use this connection to compromise the web server using a known exploit or zero-day vulnerability: They exploit open TCP or UDP connections and gain access to entities on the network. Once in, hackers can attempt to move “east-west” within the network.
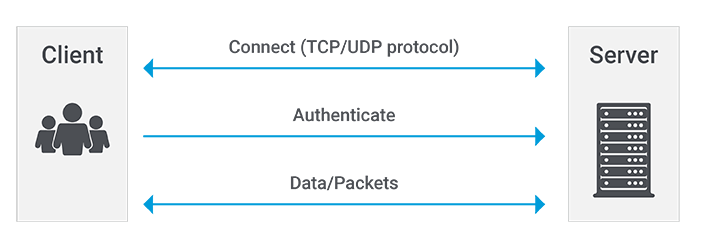
Reducing the attack surface requires making sure a web server does not communicate with unauthorized or unauthenticated entities. In traditional castle-and-moat security architectures, this network connection ensures access to much if not all the network assets. Attackers can compromise access credentials or find open ports to exploit.
Going “dark”: Camouflage for your corporate network
“Going dark” hides the network from the internet at large in order to prevent bad actors from ever accessing the network via a web server (or other network entities).
Think about your physical house security: your doors and windows represent the attack surface. Each door or window is literally a channel attack vector similar to an open TCP port on an IT system waiting for someone to connect. In legacy castle-and-moat security, we allow access to the doors and windows before we establish if the person trying to enter is somebody who should be on the inside at all.
By going dark, you effectively hide all your doors and windows from view. Instead, you create a secure underground tunnel for each individual valuable asset in your house, and you can only enter an asset tunnel if you pass an identity check.
The user and device identity must be authenticated before a TCP channel connection (or in our analogy, an underground tunnel) gets created. With a dark network, we use the peephole to verify identity before we open the door—every time somebody knocks, no matter who is knocking.
Thieves may be able to see your house. But they can’t see any windows or doors. They can’t see the tunnels. And if they somehow stumble onto one, they can’t use it unless they are recognized as somebody allowed inside the house. If they can’t see an opening, they move on to a different house (most likely one with legacy security . . .).
Why not just use a VPN?
First of all, good question! A VPN does reduce the attack surface, but there are several major issues. The VPN concentrator itself becomes a new attack surface: VPNs are like putting a fence around your house to protect all the doors and windows. But it’s a fence with a gate, and that gate is visible and can be breached. If the burglar breaks down the gate, the attacker can see all the doors and windows (which are open because you thought the gate was secure).
Also, VPNs don’t protect against two major security risks: east-west movement and IP visibility.
When a user authenticates with VPN, the user generally gets full network IP protocol access—including the Internet Control Message Protocol (ICMP), which hackers can exploit. Attackers can use ICMP for reconnaissance in the attack phase. This allows an attacker to probe your network and data center, or—even worse—steer ransomware to additional targets.
Users can connect to a network using direct IP communication via an IP address. This exposes the network listening port to attackers. An attacker can use a port scan of various subnets to obtain a full list of services that are open on the server. One method to prevent this is by only allowing connections from an authorized and valid DNS request and port number, which ensures the applications and services can only be seen once the user is authenticated. This remediates risk, and is what the industry has named Zero Trust Network Access (ZTNA).
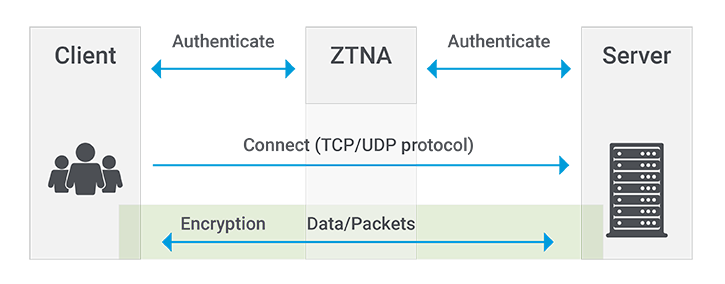
The mechanics of going dark
The beauty of going dark is that hackers can’t attack what they can’t see. Enterprises need to measure their attack surface from their users’ perspective. How do users find and connect to the network?
Try this experiment: Scan your entire enterprise network. You will find that some port numbers (such as 135, 137, 138, 139, 445, 3389) are open. That makes them (dangerously) available as an attack vector. These ports are used for common services such as WMI, SMB, RDP, etc. These common services are exposed by default on Windows systems after joining the domain or for example when file- and print-sharing are enabled.
IT security teams must reduce such open network connections to near zero, which I call “Zero Attack Surface.”
How do you go dark?
Reducing attack surface takes four steps: closing the firewall, eliminating peer-to-peer communication, obscuring the data center, and establishing progress measurement.
Start your zero attack surface journey: Close the local Windows firewall for all incoming services and only allow trusted incoming connections from an authenticated trusted source.
Ransomware like Wannacry and notPetya prove: You can no longer allow peer-to-peer communication between clients. The risk far outweighs any gain. Very rarely does the client require inbound connectivity (nearly 99% is outbound).
How can you reduce the attack surface in the data center? First, ensure users cannot directly connect to the data center. They must connect via a service that renders the network dark. Then reduce peer-to-peer internal data center connections as much as possible using new Zero Trust technologies that microsegments data and applications using their cryptographic identity fingerprint.
How do you measure the progress of your mission? Conduct a port scan of the entire access and data center network segments. Count the number of replies for each host on each port, and make sure that every week this number goes down. The lower the number, the lower the attack surface—and the lower the risk of compromises to your network. Accountability is key: This measure should become a visible KPI for your CISO and security team.
Let’s look at the numbers: Assume in your large enterprise, you have 20K Windows 10 clients. This equates to 100K possible channel attack vectors, assuming each client has the five “standard” Windows ports open (e.g., 135, 445, etc.). Shut down these common inbound listening ports with Windows firewall block rules via a domain group policy and you’ll reduce your attack surface metric by more than 100K ports!
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is a clearly defined way of making your network dark. For today’s enterprises, ZTNA is the present and the future of perimeter-less cloud security. According to Gartner, “ZTNA provides controlled access to resources, reducing the surface area for attack. The isolation afforded by ZTNA improves connectivity, removing the need to directly expose applications to the internet.” *
Zero Trust principles are based on adopting a least-privilege strategy and strictly enforcing access control. Legacy network security relied on packet exchange to negotiate connections, but you can’t trust a packet since it does not contain any identity. Therefore you must first identify packets using ZTNA, establish a connection based on identity and policy, then create secure microtunnels for these packets to flow between users and IT assets.
As enterprises adopt more cloud solutions to achieve business goals faster and with less expense, security remains a big stumbling block. The way forward is abandoning legacy hub-and-spoke networking models and castle-and-moat security strategies that advertise the network in favor of perimeter-less models that let corporate assets and applications go dark to the internet.
Lock down your network doors and windows with ZTNA now. Go dark.
Try Zscaler’s free, private, and safe-to-use Security Assessment Tool today to check your Internet Attack Surface.
* Market Guide for Zero Trust Network Access, Steve Riley, Neil MacDonald, Lawrence Orans, June 2020





