Zscaler Blog
Get the latest Zscaler blog updates in your inbox
It's Not Too Late To Ditch Your VPN: Why ZPA Is The Superior Secure Access Solution - Part 1
Introduction
This is the first of the blog series examining the advantages of Zscaler Private Access (ZPA) architecture. In this post, we'll focus specifically on how ZPA addresses the security limitations of traditional Virtual Private Network (VPN) solutions, which have become increasingly inadequate for securing enterprises.
Weaknesses and Limitations of VPNs
Encrypted VPN technology was invented over 30 years ago to help organizations provide remote users access to applications hosted on internal networks. While this model worked for decades, its inherent architectural flaws have made it a liability in today’s threat landscape.
VPNs are fundamentally built on a castle-and-moat security model, where everything inside the network is treated as trusted and secure. Unfortunately, attackers have learned to exploit inherent VPN vulnerabilities, making the technology an urgent security risk for modern businesses.
Below, we’ll explore three primary challenges of VPN and why ZPA solves these problems for enterprise security architects.
1. External Attack Surface and Direct Links to Internal Networks
By design, VPN gateways must be exposed to the public internet to allow remote users to connect. This setup creates a massive external attack surface for cybercriminals to probe for vulnerabilities or exploit stolen credentials. VPN gateways directly link remote users to internal networks, which extends the external threat surface into the core of an organization’s environment.
According to the Zscaler ThreatLabz 2025 VPN Risk Report, a massive 93% of respondents express concerns over backdoor vulnerabilities introduced by external VPN connections. Attackers commonly exploit vulnerabilities found in major VPN vendors' SSL/TLS implementations, making VPN gateways one of the most targeted points of entry.
For example:
- The Colonial Pipeline ransomware attack (2021) exploited weak VPN security, disrupting fuel supplies across the U.S. East Coast.
- In early 2024, CISA issued an emergency directive in response to widespread exploitation of Ivanti VPN vulnerabilities.
These real-world incidents underscore the critical risks of VPN architecture. When a VPN gateway is compromised—whether via zero-day vulnerabilities or unpatched systems—attackers gain direct access to an organization’s internal network. The damage can be immediate, catastrophic, and difficult to contain.
2. Internal Attack Surface Due to Exposed DNS and Server IP Addresses
VPN technology extends the internal network to connected devices, allowing remote users to interact directly with internal resources. This means source and destination IP addresses are exposed, enabling bidirectional communication between endpoints and internal servers. While intended for connectivity, this architecture opens the door for attackers to explore, scan, and navigate the internal network once a VPN breach occurs.
Key risks include:
- Exposed DNS servers: Attackers who gain VPN access can directly interact with internal DNS servers to identify internal services.
- Server discovery via internal IPs: By communicating directly with server IP addresses, threat actors can perform reconnaissance, identify vulnerable systems, and plan broader exploits.
- Lateral movement: Using tools like nmap, attackers can scan network topologies to identify hosts, routers, firewalls, and servers. Leveraging a foothold, they can move laterally to gain access to sensitive systems or data.
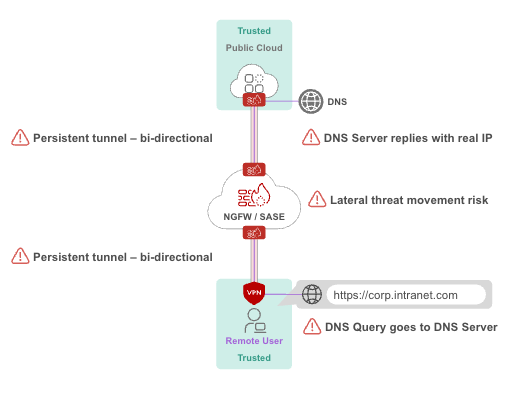
In practice, VPN architecture inadvertently places attackers inside the internal network, giving them the tools and opportunities to compromise other systems. Designed decades ago, VPN technology today is fundamentally attacker-friendly. These attack scenarios aren’t just theoretical—they’ve occurred repeatedly over the years. As per Google Mandiant’s investigation, attackers leveraged the LDAP account that was configured in the vulnerable VPN gateway to create a computer object and request a certificate for a domain administration. Thus, by exploiting the VPN gateway’s vulnerability, the attacker quickly gained access to the Active Directory and moved laterally to establish persistence within the victim’s environment.
3. Routing Complexities, Expensive Infrastructure, and Segmentation Challenges
Providing internal network access for VPN users requires the gateway to connect to every segment of the network. For large enterprises, this often involves costly infrastructure such as MPLS links, IPsec tunnels, or cloud connectivity services like Azure ExpressRoute and AWS Direct Connect. Additionally, operational overhead grows due to high-availability requirements, routing complexities, and troubleshooting challenges inherent to VPN solutions.
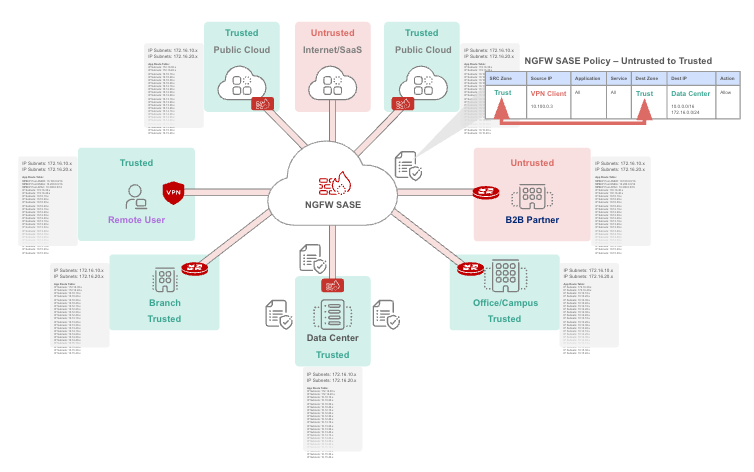
Without proper segmentation, attackers who breach one part of the network can potentially access all connected segments. However, implementing segmentation in a VPN environment is notoriously challenging. Complex firewall rules, evolving applications, and poorly configured access policies all contribute to a fragmented and vulnerable network environment.
Why ZPA's Architecture is Superior
Zscaler Private Access (ZPA) was purpose-built on Zero Trust principles to eliminate the security and operational weaknesses of VPNs, providing a more secure and user-friendly solution for modern enterprises.
Here’s how ZPA addresses the architectural flaws of VPN:
1. No External Attack Surface
Unlike VPN gateways, ZPA’s architecture creates no inbound connections. Instead, ZPA App Connectors in the data center initiate outbound TLS tunnels to the Zero Trust Exchange (ZTE), effectively removing external attack points. Remote users also make outbound TLS connections via Zscaler Client Connector agents installed on their devices.
These inside-out Zero Trust tunnels allow users to connect to applications without exposing any public-facing IPs, drastically reducing the external attack surface and eliminating a key avenue for cyberattacks.
2. Application-Specific Access vs. Network-Level Access
Unlike VPNs, which grant network-level access to remote users, ZPA uses granular application-level access policies. Users are never placed directly on the internal network, and they can only access the specific applications they’re authorized for. And ZPA replaces implicit trust by continuously evaluating each application access request against user identity and device posture.
Further enhancements include synthetic IP addresses—a feature where real server IPs are replaced with ephemeral synthetic IPs. This prevents attackers from performing DNS enumeration - a common reconnaissance technique used after gaining network access - effectively reducing the risk of discovering and targeting internal applications.

By segmenting access at the application level, ZPA prevents threat actors from moving laterally across an organization’s network. Even in a worst-case scenario, attackers are restricted to the limited applications the compromised user is authorized for.
3. Simplified Routing and Facilitated Segmentation
ZPA also reduces operational complexity. Instead of requiring VPN gateways to interconnect with every network segment, organizations can deploy ZPA App Connectors directly where applications are hosted. These connectors facilitate seamless application access without complex routing tables, double NATs, or private MPLS connectivity.

This approach simplifies migration to cloud infrastructure, reduces costs associated with legacy networking solutions, and enables seamless segmentation at scale. Segmentation ensures that even if one part of the network is breached, attackers cannot gain access to other segments.
Summary
VPN technology has long outlived its usefulness as a secure remote-access solution. With its inherent architectural flaws—spanning exposed attack surfaces, internal network vulnerabilities, and segmentation challenges—it has become a liability for organizations navigating modern cybersecurity challenges.
ZPA, built on Zero Trust principles, offers a fundamentally different and superior approach to secure remote access. By eliminating external attack surfaces, restricting access to specific applications, and simplifying segmentation, ZPA empowers organizations to securely connect users to the resources they need while keeping attackers out.
Check out the second blog post in this series as we dive deeper into ZPA’s capabilities and explore why Zero Trust is essential for securing the modern enterprise.
Ready to start a conversation with us? Schedule a demo to see how ZPA can help your organization.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.


