Do you feel like you’ve squeezed a decade's worth of digital transformation into the last three years? I certainly do. As evidence, take a look at the before and after of my home office. It went from a makeshift dining table turned desk to a fully loaded workspace with lights, mics, and cameras - a pandemic innovation!

During this time, zero trust network access, or ZTNA, technology benefited from a “perfect storm” of market conditions that drove a wave of innovation: the mass shift to remote work, the surge in digital tools and apps, and the accelerated cloud push. This rare convergence of events forced many organizations to rethink their access models, many of which relied on traditional remote access VPNs. From that storm, ZTNA emerged as a viable alternative to VPNs.
In a new paper titled “Making Sense of the Quickly Evolving ZTNA Market,” the Enterprise Strategy Group (ESG) examines the trends, challenges, and evolution of the growing and crowded market for ZTNA. According to ESG, ZTNA has become so popular that more than two thirds of companies are replacing their VPNs with ZTNA tools or are interested in doing so.
First-generation ZTNA – Just a VPN replacement?
John Grady, ESG principal analyst and author of the paper, says that while most ZTNA tools provide clear advantages over VPNs, few can effectively address the challenges network security teams face today to protect and secure access to applications. The key issues organizations encounter with first-generation tools are:
1. Inconsistent user experience: While cloud-only tools were ideal for connecting solely on the remote access use case, they introduce a sort of inverse backhauling model when users in offices have to access on-premises resources and are routed through the cloud to do so.
2. Access is still too broad: Most ZTNA tools provide basic separation to reduce the attack surface. However, when legitimate users are compromised, this does not prevent attackers from moving laterally and accessing other resources. ZTNA tools should go further and extend segmentation mechanisms across workloads and devices to more effectively prevent lateral movement inside a cloud or data center environment.
3. Limited security services: ZTNA took a significant step forward in protecting applications when compared to VPN, but most tools fail to address the issue holistically. It is common for ZTNA solutions to establish a connection between a user and application, and then step out of the way rather than continuing to scan the traffic for security threats, leaving the door open to attackers.
According to Grady, secure access and ZTNA should not be operated in a silo and must be part of a larger, integrated platform focused on protecting distributed users and applications. This means being part of a broader secure access service edge (SASE) or security service edge (SSE) platform. For many organizations, ZTNA is not just a part, but a foundational aspect, of these architectures, with 58% of organizations that have begun to implement SASE/SSE citing ZTNA as the starting point for their project.
“Ultimately, tools supporting this broader type of approach require a more substantial set of features and capabilities compared to those focused solely on the remote access use case,” says Grady, which misses the massive shift towards comprehensive zero trust architectures.
ZTNA, evolved - Overcome first-gen hurdles with Zscaler
Zscaler supports broader security transformation initiatives and emerging use cases with its next-generation ZTNA, Zscaler Private Access. It provides any-to-any connectivity, zero trust segmentation, and integrated, continuous security. This combination helps network security teams reduce their attack surface, minimize lateral spread, and ensures a consistent and seamless user experience that just works.
Next-generation ZTNA
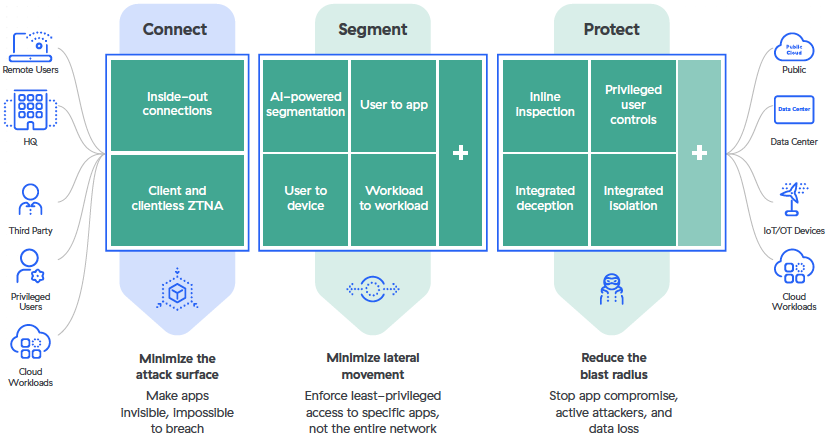
Zscaler Private Access has immediate benefits when replacing current access approaches that are ill-matched for digital transformation. It brings significant advantages to user experience, scalability, and agility, and improves an organization’s overall security posture. As a result of zero trust initiatives, 77% of companies have realized at least one security and one business benefit.¹
To find out how to evolve your secure access strategy, read ESG’s new white paper or register for our webcast with ESG - and get ready to take your zero trust security to the next level.





