Earlier this year, many organizations were affected by the devastating SolarWinds attack. Thousands of servers and devices were infected when attackers piggy-backed off third-party software to infiltrate corporate networks.
Last week, we saw Microsoft releasing an urgent alert warning customers to immediately patch their on-premises Microsoft Exchange servers due to the recent attacks believed to be led by a Chinese cybercriminal group, HAFNIUM. HAFNIUM has exploited four vulnerabilities in Microsoft's software, allowing hackers to target and gain access to Microsoft Exchange servers which, "enabled access to email accounts, and allowed the installation of additional malware to facilitate long-term access to victim environments."
It's clear that these attacks will continue as cybercriminals become more advanced and continue to find ways to exploit legacy architectures. To stop this continuous cycle of attack, react, and mitigate, IT must drive organizations to adopt the right security strategy with the right technology. It’s encouraging to see that the majority of companies are already doing exactly that.
Zero trust, the most essential security strategy in the modern world.
The large increase in attacks and vulnerabilities in the last year is mainly due to the rise in the remote and mobile workforce during the pandemic. With users distributed globally, network-centric solutions, such as VPN, become a hotspot for attacks and vulnerabilities. In a recent study, 72 percent of IT professionals stated they were concerned that their VPN may jeopardize their ability to secure their environment. This is why many are stepping away from a network-centric approach to security and are adopting a zero trust strategy to meet the needs of today’s modern workforce. Here are three critical reasons why zero trust is necessary moving forward:
1. A mobile workforce
As mentioned before, the increase in mobile users has increased business risk. Users are everywhere, on both known and unknown devices, accessing your private applications. Without the control of having users in the office, the attack surface expands, and the risk of attack or infection drastically increases. It's a sobering reminder that it only takes one infected device to take down the whole network.
Therefore, application access should NOT be granted based on IPs and ports but rather on contextual, identity-aware identifiers. Access is provisioned when zero trust policy is verified based on an individual's identity, device, device posture, location, etc. It's critical as trust must be established before access is granted, allowing the business to control the level of risk they take on.
2. Unnecessarily large network exposure
Another point to consider is that with network-centric technologies, remote users are brought ONTO the network. Traditional technologies like VPN use exposed VPN concentrators to listen for inbound pings on the internet. See the issue? While necessary for employees to access business-critical apps, these exposed VPN concentrators provide a foothold for cybercriminals to locate and exploit the network.
This raises the question: how can we give users access to private applications without exposing our network and servers to the internet? The key to making this possible is to eliminate the listening of inbound pings. If nothing can reach a server or application, it's virtually invisible to bad actors or unauthorized users. In light of this, Gartner recommends adopting zero trust network access technologies to deliver secure access to authorized users, keep unauthorized users off your network, and leave no attack surface exposed to cybercriminals.
3. Lateral Access
Lastly, lateral movement has been a considerable contributor to the severity of these recent attacks. Once on the network, over-privileged access allows cybercriminals to move laterally. Therefore, it's vital in this threat landscape that even authorized users only have access to "need-to-know" applications, NOT the entire, underlying network. That way, if user credentials are stolen, or a device was infected, contamination is contained and not spreading to the corners of your network.
In principle, adopting a zero trust strategy is assuming least-privileged access with users and devices never brought onto the network. Instead, access is brought to the user with zero trust policies that dictate the level of access on an individual application basis. This zero trust approach results in granular application segmentation without undergoing complex network segmentation.
Don't work harder. Play smarter with zero trust.
This war against bad actors isn't going to end any time soon. But, with the right strategy IT security leaders can adapt and use modern zero trust services to protect business data from the cybercriminals that wish to do them harm. Today, 72 percent of companies are looking to adopt zero trust, and 59 percent are accelerating these efforts.
Not sure where to go from here? Take these steps to move forward:
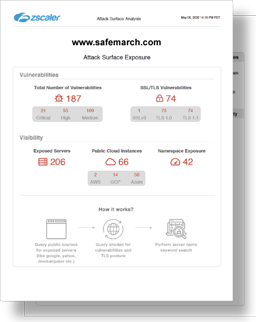
- Identify your attack surface. Free attack surface analysis
- Review your customized results.
- Learn best practices for implementing zero trust.





